How To Install Apache on Rocky Linux 10

In this tutorial, we will show you how to install Apache on Rocky Linux 10. Apache HTTP Server remains the backbone of modern web infrastructure, powering over 35% of all websites globally. Rocky Linux, as an enterprise-grade operating system and direct successor to CentOS, provides the perfect foundation for hosting robust web applications. This comprehensive guide walks you through every step of installing and configuring Apache on Rocky Linux, from initial system preparation to advanced security hardening.
Whether you’re a system administrator deploying production servers or a developer setting up a local testing environment, this tutorial provides the technical depth and practical insights needed for a successful Apache installation. We’ll cover everything from basic installation commands to advanced configuration techniques that ensure optimal performance and security.
Prerequisites and System Requirements
Before beginning the Apache installation process, ensure your system meets the necessary requirements. Rocky Linux 10 serves as the recommended platform for this installation, offering long-term support and enterprise-grade stability. Your system should have at least 1GB of RAM and 10GB of available disk space for a basic Apache installation, though production environments typically require significantly more resources.
Administrative privileges are essential for this installation process. You must have either root access or sudo privileges to install packages, modify system configurations, and manage services. Network connectivity is required to download packages from Rocky Linux repositories and apply system updates.
Essential System Requirements:
- Rocky Linux 10 (recommended) or compatible RHEL-based distribution
- Minimum 1GB RAM (2GB+ recommended for production)
- 10GB available disk space
- Root or sudo access
- Active internet connection
- Basic command-line knowledge
Pre-Installation System Preparation
System preparation forms the foundation of a successful Apache installation. Begin by updating your Rocky Linux system to ensure all packages and security patches are current. This step prevents compatibility issues and ensures you’re working with the latest software versions.
Execute the following command to update your system:
sudo dnf update -yThe DNF package manager fetches updates from both AppStream and BaseOS repositories. This process may take several minutes depending on your system’s current state and available updates. The -y flag automatically confirms all prompts during the update process.
Verify your system’s repository configuration to ensure proper package sources:
sudo dnf repolistThis command displays active repositories, confirming that AppStream and BaseOS repositories are properly configured and accessible. Rocky Linux’s repository structure mirrors Red Hat Enterprise Linux, providing enterprise-grade package management and security updates.
Consider creating a system backup before proceeding with the installation, especially in production environments. While Apache installation is typically safe, having a recovery point ensures business continuity in case of unexpected issues.
Apache Installation Process
Apache installation on Rocky Linux utilizes the DNF package manager, which provides dependency resolution and secure package installation from official repositories. The Apache web server package is called httpd in Red Hat-based distributions, maintaining consistency with enterprise Linux standards.
Install Apache using the following command:
sudo dnf install httpd -yThe installation process downloads the Apache HTTP Server package and its dependencies. Rocky Linux typically installs Apache version 2.4.53 or newer, which includes modern security features and performance improvements. The installation includes the main server binary, configuration files, and essential modules.
Verify the installation by checking the Apache version:
httpd -vThis command displays the installed Apache version and build information. A successful installation shows output similar to:
Server version: Apache/2.4.53 (Rocky Linux)
Server built: Jan 31 2023 00:00:00The installation creates several important directories:
/etc/httpd/– Main configuration directory/var/www/html/– Default document root/var/log/httpd/– Log file directory/etc/httpd/conf.d/– Additional configuration files
Apache Service Management
Proper service management ensures Apache starts automatically and runs reliably. Rocky Linux uses systemd for service management, providing robust process control and monitoring capabilities.
Start the Apache service immediately after installation:
sudo systemctl start httpdThis command initializes the Apache daemon and begins listening for web requests. The service starts in the background without producing output unless errors occur.
Enable Apache to start automatically during system boot:
sudo systemctl enable httpdThis configuration ensures Apache launches automatically after system restarts, maintaining service availability without manual intervention. The enable command creates the necessary systemd links for automatic startup.
Verify the service status to confirm proper operation:
sudo systemctl status httpdA successful configuration displays output indicating the service is “active (running)” with recent startup information. The status command provides detailed information about service health, including recent log entries and process details.
Essential Service Management Commands:
sudo systemctl start httpd– Start Apache servicesudo systemctl stop httpd– Stop Apache servicesudo systemctl restart httpd– Restart Apache servicesudo systemctl reload httpd– Reload configuration without restartsudo systemctl status httpd– Check service status
Firewall Configuration and Security
Rocky Linux implements firewalld as the default firewall solution, providing zone-based network security management. Apache requires specific port configurations to serve web content to users.
Open the HTTP port (80) for web traffic:
sudo firewall-cmd --permanent --add-port=80/tcpConfigure HTTPS port (443) for secure connections:
sudo firewall-cmd --permanent --add-port=443/tcpThe --permanent flag ensures these rules persist after system reboots. Without this flag, firewall rules only apply to the current session.
Reload the firewall configuration to activate the new rules:
sudo firewall-cmd --reloadAlternatively, use predefined service definitions for cleaner configuration:
sudo firewall-cmd --permanent --zone=public --add-service=http
sudo firewall-cmd --permanent --zone=public --add-service=https
sudo firewall-cmd --reloadVerify the firewall configuration:
sudo firewall-cmd --list-allThis command displays all active firewall rules, confirming that HTTP and HTTPS services are properly allowed. The output should show both ports 80 and 443 in the allowed ports or services list.
Testing Apache Installation
Thorough testing confirms Apache is functioning correctly and serving web content. Multiple testing methods ensure comprehensive verification of the installation.
Open a web browser and navigate to your server’s IP address:
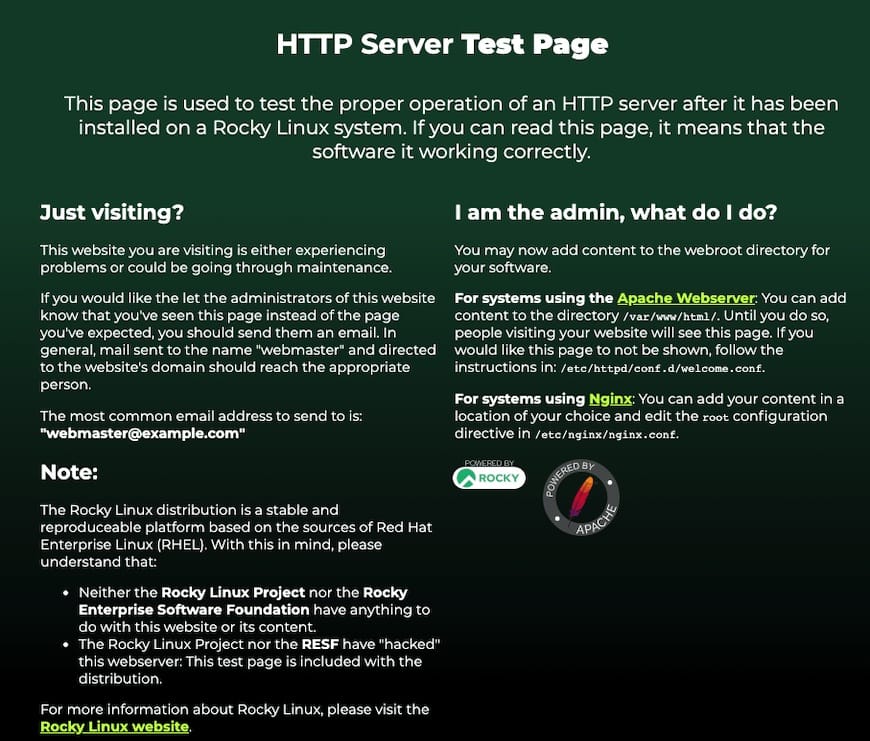
http://YOUR_SERVER_IPReplace YOUR_SERVER_IP with your actual server IP address. A successful installation displays the Rocky Linux Apache Test Page, confirming the web server is operational and serving content.
For command-line testing, use curl to verify Apache responses:
curl http://localhostThis command retrieves the default Apache test page content directly from the command line. The output should include HTML content from the default Rocky Linux Apache welcome page.
Test external connectivity from another system:
curl http://YOUR_SERVER_IPExternal testing confirms that firewall configurations are correct and Apache is accessible from remote systems. This test simulates actual user access patterns.
Testing Checklist:
- Local browser access to server IP
- Command-line curl testing
- External system access verification
- Port connectivity confirmation
- Service status validation
Basic Apache Configuration
Apache’s modular configuration system provides extensive customization options while maintaining security and performance. The main configuration file resides at /etc/httpd/conf/httpd.conf, with additional configurations in /etc/httpd/conf.d/.
Edit the main configuration file:
sudo nano /etc/httpd/conf/httpd.confConfigure essential server parameters:
ServerAdmin webmaster@example.com
ServerName www.example.com:80Replace webmaster@example.com with your administrative email address and www.example.com with your domain name. The ServerAdmin directive specifies the contact email for server-related issues, while ServerName defines the server’s primary hostname.
Configure the document root directory:
DocumentRoot "/var/www/html"The DocumentRoot directive specifies where Apache serves files from. The default /var/www/html directory provides appropriate permissions and security settings for web content.
Set directory permissions and options:
<Directory "/var/www/html">
Options Indexes FollowSymLinks
AllowOverride None
Require all granted
</Directory>This configuration allows directory listings and symbolic links while maintaining security by preventing .htaccess overrides. Adjust these settings based on your specific security requirements.
Test configuration syntax before applying changes:
sudo httpd -tThis command validates Apache configuration files for syntax errors. Always run this test before restarting Apache to prevent service disruption from configuration mistakes.
Reload Apache configuration:
sudo systemctl reload httpdThe reload command applies configuration changes without interrupting active connections, ensuring continuous service availability during updates.
Virtual Hosts Setup
Virtual hosts enable Apache to serve multiple websites from a single server, maximizing resource utilization and simplifying management. This advanced configuration technique supports both name-based and IP-based virtual hosting.
Create a virtual host configuration file:
sudo nano /etc/httpd/conf.d/example.com.confConfigure a basic virtual host:
<VirtualHost *:80>
ServerName example.com
ServerAlias www.example.com
DocumentRoot /var/www/html/example.com
ErrorLog /var/log/httpd/example.com_error.log
CustomLog /var/log/httpd/example.com_access.log combined
</VirtualHost>This configuration creates a virtual host for example.com with dedicated document root and log files. The ServerAlias directive allows multiple domain names to resolve to the same virtual host.
Create the document root directory:
sudo mkdir -p /var/www/html/example.com
sudo chown apache:apache /var/www/html/example.com
sudo chmod 755 /var/www/html/example.comProper directory permissions ensure Apache can serve files while maintaining system security. The apache user and group provide appropriate ownership for web content.
Create a simple test page:
sudo echo "<h1>Welcome to example.com</h1>" > /var/www/html/example.com/index.html
sudo chown apache:apache /var/www/html/example.com/index.htmlTest the virtual host configuration:
sudo httpd -t
sudo systemctl reload httpdVirtual hosts require proper DNS configuration to function correctly. Ensure your domain names resolve to the server’s IP address through DNS A records.
Performance Optimization and Advanced Topics
Apache performance tuning involves configuring modules, adjusting worker processes, and optimizing resource utilization for your specific workload requirements.
Enable essential Apache modules:
sudo httpd -M | grep -E "(rewrite|ssl|headers)"This command lists currently loaded modules. Enable additional modules by editing /etc/httpd/conf.modules.d/ configuration files as needed.
Configure worker process limits in /etc/httpd/conf/httpd.conf:
<IfModule mpm_prefork_module>
StartServers 8
MinSpareServers 5
MaxSpareServers 20
ServerLimit 256
MaxRequestWorkers 256
MaxConnectionsPerChild 4000
</IfModule>These settings control Apache’s process management and resource utilization. Adjust values based on your server’s hardware specifications and expected traffic patterns.
Configure log rotation to manage disk space:
sudo nano /etc/logrotate.d/httpdProper log management prevents disk space exhaustion while maintaining adequate logging for troubleshooting and monitoring purposes.
Troubleshooting Common Issues
Apache installation and configuration can encounter various issues requiring systematic troubleshooting approaches. Understanding common problems and their solutions ensures quick resolution of service disruptions.
Check Apache error logs for detailed problem information:
sudo journalctl -u httpd
sudo tail -f /var/log/httpd/error_logThese commands provide real-time access to Apache error messages and system logs. Error logs contain detailed information about configuration problems, permission issues, and service failures.
Resolve port binding conflicts:
sudo netstat -tulpn | grep :80
sudo lsof -i :80These commands identify processes using port 80, helping resolve conflicts that prevent Apache from starting. Kill conflicting processes or reconfigure Apache to use alternative ports.
Address SELinux-related issues:
sudo setsebool -P httpd_can_network_connect 1
sudo restorecon -R /var/www/html/SELinux security policies can prevent Apache from functioning correctly. These commands adjust SELinux settings for proper Apache operation while maintaining system security.
Common Issue Resolution:
- Service startup failures: Check error logs and configuration syntax
- Port conflicts: Identify and resolve competing processes
- Permission errors: Verify file ownership and directory permissions
- SELinux denials: Adjust security contexts and boolean settings
- Configuration errors: Validate syntax with
httpd -t
Security Hardening and Best Practices
Apache security hardening involves multiple layers of protection, from basic configuration adjustments to advanced security measures that protect against common web vulnerabilities.
Hide Apache version information:
ServerTokens Prod
ServerSignature OffAdd these directives to /etc/httpd/conf/httpd.conf to prevent Apache from revealing version information to potential attackers. This security-through-obscurity measure reduces information available to reconnaissance attempts.
Configure security headers:
Header always set X-Content-Type-Options nosniff
Header always set X-Frame-Options DENY
Header always set X-XSS-Protection "1; mode=block"
Header always set Strict-Transport-Security "max-age=31536000; includeSubDomains"These headers provide protection against common web vulnerabilities including cross-site scripting, clickjacking, and content-type confusion attacks.
Disable unnecessary modules:
sudo nano /etc/httpd/conf.modules.d/00-base.confComment out modules not required for your specific use case. Fewer loaded modules reduce attack surface and improve performance.
Implement regular security updates:
sudo dnf update httpd
sudo systemctl reload httpdEstablish a regular update schedule for Apache and system packages. Security patches address newly discovered vulnerabilities and maintain system integrity.
Configure SSL/TLS for encrypted connections:
sudo dnf install mod_sslSSL/TLS encryption protects data transmission between clients and servers. Modern web applications should enforce HTTPS for all connections to protect user privacy and data integrity.
Monitoring and Maintenance
Ongoing monitoring and maintenance ensure Apache continues operating optimally and securely. Implement comprehensive monitoring solutions to track performance metrics and identify potential issues before they impact users.
Monitor Apache status and performance:
sudo systemctl status httpd
sudo httpd -SRegular status checks verify service health and configuration validity. The -S flag displays virtual host configurations and helps identify configuration issues.
Set up log monitoring:
sudo tail -f /var/log/httpd/access_log
sudo tail -f /var/log/httpd/error_logReal-time log monitoring provides insights into traffic patterns, errors, and security events. Consider implementing automated log analysis tools for production environments.
Establish backup procedures:
sudo tar -czf apache-backup-$(date +%Y%m%d).tar.gz /etc/httpd/ /var/www/html/Regular backups of configuration files and web content ensure quick recovery from system failures or security incidents.
Congratulations! You have successfully installed Apache web server. Thanks for using this tutorial for installing the Apache HTTP server on your Rocky Linux 10 system. For additional help or useful information, we recommend you check the official Apache website.