How To Install BleachBit on Debian 13

Maintaining a clean and optimized Linux system requires the right tools and expertise. BleachBit stands out as one of the most effective system cleaning utilities available for Debian 13, offering comprehensive privacy protection and disk space optimization. This detailed guide provides multiple installation methods and essential configuration steps to help users successfully deploy BleachBit on their Debian 13 systems.
What is BleachBit?
Understanding BleachBit’s Purpose
BleachBit represents a powerful, open-source system cleaner designed specifically for Linux environments, including Debian distributions. This cross-platform utility excels at removing unnecessary files, protecting user privacy, and optimizing system performance through intelligent cleaning algorithms . Unlike proprietary alternatives, BleachBit offers complete transparency through its open-source codebase, ensuring users maintain full control over their system cleaning processes.
The application serves multiple critical functions within Linux ecosystems. Primary capabilities include cache removal, temporary file deletion, browser data cleaning, and secure file shredding. Advanced users particularly appreciate BleachBit’s ability to permanently remove sensitive data through multiple overwrite algorithms, making data recovery virtually impossible.
Key Features and Benefits
BleachBit’s comprehensive feature set addresses various system maintenance requirements. The application excels at browser data management, removing cookies, browsing history, cached files, and stored passwords across multiple web browsers . System optimization occurs through systematic removal of temporary files, log entries, and redundant cache data that accumulates during regular computer usage.
Privacy protection represents another cornerstone feature. BleachBit implements secure deletion algorithms that overwrite sensitive files multiple times, preventing potential data recovery attempts . This functionality proves invaluable for users handling confidential information or those concerned about digital privacy. File shredding capabilities extend beyond simple deletion, ensuring complete data destruction when required.
System Requirements and Prerequisites
Debian 13 System Requirements
Before installing BleachBit on Debian 13, understanding system requirements ensures smooth installation and optimal performance. BleachBit version 4, the current release, requires Python 3 and GTK 3 libraries. These dependencies typically come pre-installed with most Debian 13 installations, but verification prevents potential compatibility issues.
Administrative privileges remain essential for certain BleachBit operations, particularly system-wide cleaning tasks. Users should ensure they possess sudo access or administrator credentials before beginning the installation process. Memory requirements remain minimal, with BleachBit operating efficiently on systems with limited resources.
Pre-Installation System Preparation
Preparing the Debian 13 system before BleachBit installation reduces potential complications and ensures optimal results. Updating existing packages and repositories creates a stable foundation for new software installation. Execute system updates using standard package management commands to refresh repository information and upgrade existing software components.
Creating system backups before major software installations represents a prudent security measure. While BleachBit installation rarely causes system issues, maintaining current backups provides recovery options if unexpected problems arise. Consider backing up important user data and system configurations before proceeding with installation procedures.
Installation Method 1: Using APT Package Manager
Step-by-Step APT Installation
The APT package manager provides the most straightforward method for installing BleachBit on Debian 13 systems. This approach leverages Debian’s built-in package management infrastructure, ensuring proper dependency resolution and system integration.
Begin by updating the package repository information to ensure access to the latest software versions:
sudo apt update && sudo apt upgrade -yThis command refreshes repository metadata and upgrades existing packages to their newest versions. The combined operation ensures system consistency before introducing new software components.
Install BleachBit using the standard APT installation command:
sudo apt install bleachbit -yThe installation process automatically resolves dependencies and configures BleachBit for immediate use. The -y flag confirms installation prompts automatically, streamlining the deployment process for experienced users.
Post-Installation Verification
Verifying successful installation ensures BleachBit functions correctly before proceeding with system cleaning operations. Launch BleachBit from the terminal using the simple command:
bleachbitAlternatively, access BleachBit through the graphical application menu by searching for “BleachBit” in the system applications. The application should launch without errors, displaying the main interface with various cleaning categories.
Test basic functionality by exploring the interface and reviewing available cleaning options. The left panel displays cleaning categories including browsers, system components, and installed applications. This initial exploration familiarizes users with BleachBit’s capabilities and interface layout.
Troubleshooting APT Installation Issues
APT installation occasionally encounters problems requiring troubleshooting intervention. “Package not found” errors typically indicate repository configuration issues or outdated package information. Resolve these problems by verifying repository configuration and updating package lists using sudo apt update.
Dependency conflicts may arise during installation, particularly on systems with modified package configurations. Address dependency issues using the automatic fix command:
sudo apt-get install -fThis command identifies and resolves broken dependencies automatically, restoring package management functionality. Repository authentication problems require importing GPG keys or reconfiguring repository sources according to Debian documentation guidelines.
Installation Method 2: Manual .deb Package Installation
Downloading the Official .deb Package
Manual .deb package installation provides access to the latest BleachBit versions that may not appear in standard repositories immediately. This method ensures users obtain current software releases with the newest features and security improvements.
Access the official BleachBit download page to locate Debian-compatible packages. Select the appropriate .deb file matching your system architecture, typically marked for Debian 13 or universal Debian compatibility. Download packages using wget for command-line efficiency:
wget https://www.bleachbit.org/download/file/t?file=bleachbit_5.0.0-0_all_debian12.debVerify package integrity after downloading by checking file size and comparing checksums when available. Official packages include digital signatures ensuring authenticity and preventing tampering during distribution.
Installing via dpkg Command
The dpkg utility handles individual .deb package installation independent of repository management. This approach provides direct control over package deployment while bypassing repository dependencies.
Install the downloaded package using dpkg:
sudo dpkg -i bleachbit_5.0.0-0_all_debian12.debMonitor installation output for dependency warnings or configuration prompts. The dpkg utility may identify missing dependencies that require separate installation through APT before BleachBit functions correctly.
Advantages of Manual Installation
Manual .deb installation offers several advantages over repository-based methods. Users gain access to the latest software versions immediately upon release, without waiting for repository updates. Version control becomes more precise, allowing installation of specific releases for compatibility or testing purposes.
Package authenticity verification provides enhanced security through digital signature checking. Official BleachBit packages include cryptographic signatures ensuring the software hasn’t been modified or corrupted during distribution. This verification process protects against malicious package substitution attempts.
Digital Signature Verification
Verifying package signatures represents a critical security practice for manual installations. Import the BleachBit public key before installation:
wget http://bleachbit.sourceforge.net/bleachbit_public.key -O /tmp/bleachbit_public.key
gpg --import /tmp/bleachbit_public.keyVerify the package signature using GPG tools:
gpg --verify bleachbit_4.6.2-0_all_debian13.deb.sig bleachbit_4.6.2-0_all_debian13.debSuccessful verification confirms package authenticity and integrity. This additional security step prevents installation of compromised or modified software packages.
Installation Method 3: Using Flatpak
Setting Up Flatpak Environment
Flatpak provides a containerized application installation method offering enhanced security and dependency isolation. This approach creates sandboxed environments preventing application conflicts and system interference.
Install Flatpak if not already present on the Debian 13 system:
sudo apt install flatpak -yEnable the Flathub repository to access BleachBit and other Flatpak applications:
sudo flatpak remote-add --if-not-exists flathub https://flathub.org/repo/flathub.flatpakrepoThis command configures Flathub as a trusted application source. Flathub serves as the primary repository for Flatpak applications, hosting thousands of Linux applications including BleachBit.
Installing BleachBit via Flatpak
Install BleachBit through Flatpak using the official application identifier:
flatpak install flathub org.bleachbit.BleachBit -yThe installation process downloads BleachBit and all required dependencies within an isolated container environment. This approach prevents conflicts with existing system packages while ensuring application functionality.
Launch BleachBit installed via Flatpak:
flatpak run org.bleachbit.BleachBitThe Flatpak version operates independently of system-installed packages, providing additional security through application sandboxing.
Flatpak Installation Benefits
Flatpak installation offers multiple advantages for security-conscious users. Sandboxed execution prevents applications from accessing unauthorized system resources or interfering with other software. Automatic dependency management eliminates compatibility concerns while ensuring consistent application behavior across different Linux distributions.
Version management becomes simplified through Flatpak’s update mechanisms. Applications update independently of system packages, allowing users to maintain current software versions without affecting system stability. Security updates deploy automatically, ensuring applications remain protected against known vulnerabilities.
Installation Method 4: Third-Party Repository
OpenSUSE Build Service Repository
The OpenSUSE Build Service provides an alternative repository containing current BleachBit packages for Debian 13. This method offers repository-based installation while accessing packages newer than those in standard Debian repositories.
Add the repository configuration for Debian 13:
echo 'deb http://download.opensuse.org/repositories/home:/andrew_z/Debian_13/ /' | sudo tee /etc/apt/sources.list.d/home:andrew_z.listImport the repository GPG key to verify package authenticity:
curl -fsSL https://download.opensuse.org/repositories/home:andrew_z/Debian_13/Release.key | gpg --dearmor | sudo tee /etc/apt/trusted.gpg.d/home_andrew_z.gpg > /dev/nullRepository Installation Commands
Update package information and install BleachBit from the third-party repository:
sudo apt update
sudo apt install bleachbitThis approach combines repository convenience with access to updated packages. The installation process follows standard APT procedures while utilizing alternative package sources for enhanced software availability.
Monitor repository updates regularly to maintain current BleachBit versions. Third-party repositories may update packages more frequently than official Debian repositories, providing access to bug fixes and feature enhancements sooner.
Initial Configuration and Setup
First Launch Configuration
BleachBit’s initial launch presents configuration options affecting cleaning behavior and system interaction. The preferences dialog appears during first startup, allowing users to customize default behaviors according to their requirements.
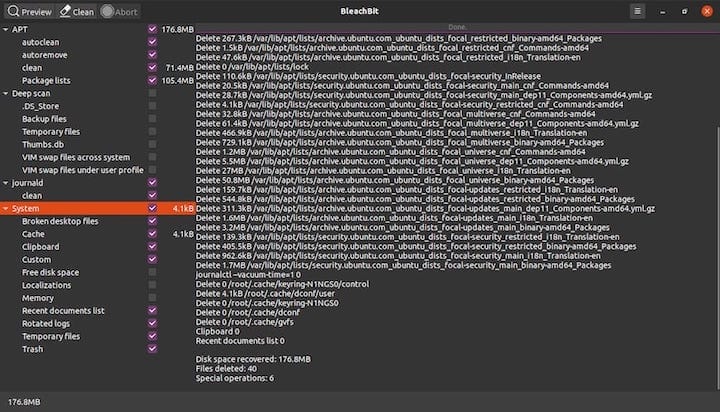
Configure preview settings to review cleaning operations before execution. Enable preview mode to examine which files BleachBit will remove, providing safety verification before permanent deletion. This setting proves particularly valuable for new users learning application behavior.
User Interface Overview
BleachBit’s interface divides into distinct functional areas optimizing user workflow. The left panel displays cleaning categories organized by application type and system component. Categories include web browsers, system files, application caches, and privacy-sensitive data types.
Checkbox functionality enables selective cleaning operations. Users choose specific items for cleaning while preserving others requiring retention. The top menu contains primary action buttons: Preview, Clean, and Shred Files/Folders, each serving distinct cleaning purposes.
Understanding interface organization improves cleaning efficiency and reduces accidental data removal. Spend time exploring categories and understanding cleaning implications before performing system-wide operations.
Administrator vs. User Mode
BleachBit operates in different modes depending on execution privileges. Regular user mode cleans user-specific files and applications without affecting system-wide components. Administrator mode, accessed through sudo bleachbit, enables system-wide cleaning including shared caches and system logs.
Choose execution mode based on cleaning requirements and security considerations. User mode provides sufficient functionality for personal file cleaning while maintaining system integrity. Administrator mode offers comprehensive cleaning capabilities but requires careful consideration of cleaning selections to avoid system damage.
Basic Usage and Features
Understanding Cleaning Categories
BleachBit organizes cleaning options into logical categories facilitating efficient system maintenance. Browser categories include options for removing cookies, browsing history, cached files, and stored passwords across multiple web browsers . Each browser maintains separate cleaning options allowing selective data removal.
System categories encompass temporary files, log entries, package caches, and application-specific data. These options target system-wide files accumulating during regular operation. Application categories provide cleaning options for specific installed software, removing caches and temporary files created during application usage.
Review category descriptions and file types before enabling cleaning options. Understanding cleaning implications prevents accidental removal of important data while maximizing system optimization benefits.
Preview Functionality
The Preview function represents BleachBit’s most important safety feature, allowing users to examine cleaning operations before execution. Click the Preview button to generate a detailed report showing files scheduled for removal and space recovery estimates.
Preview results display file paths, sizes, and cleaning categories for comprehensive review. This information enables informed decision-making regarding cleaning operations while providing space recovery projections. Large file discoveries may indicate system issues or applications creating excessive temporary data.
Always use Preview before executing cleaning operations, particularly when trying new cleaning categories or running administrator mode. Preview functionality prevents accidental deletion of important files while building confidence in BleachBit’s cleaning algorithms.
Secure File Deletion
BleachBit implements multiple secure deletion algorithms ensuring permanent data removal when required. Standard file deletion leaves data recoverable through specialized recovery tools, while secure deletion overwrites file contents multiple times making recovery virtually impossible.
Access secure deletion through the “Shred Files/Folders” function for individual files requiring permanent removal. This feature proves valuable for confidential documents, personal information, or sensitive data requiring complete destruction. Multiple overwrite algorithms provide varying security levels based on data sensitivity requirements.
Consider secure deletion requirements before enabling this functionality. Secure deletion takes significantly longer than standard cleaning operations due to multiple overwrite cycles. Reserve secure deletion for truly sensitive data requiring maximum protection.
Advanced Features and Security Considerations
Privacy Enhancement Features
BleachBit provides comprehensive privacy protection through systematic removal of user activity traces. Browser cleaning eliminates browsing history, saved passwords, download records, and session data that could reveal user behavior patterns. System cleaning removes log files containing user activity information and application usage data.
Free space wiping represents an advanced privacy feature overwriting unused disk space containing deleted file remnants. This process ensures previously deleted files cannot be recovered through forensic analysis techniques. Free space wiping requires significant time but provides maximum privacy protection for security-sensitive environments.
Configure privacy cleaning based on threat models and security requirements. Home users may require basic browser cleaning while business environments might necessitate comprehensive data wiping procedures.
Deep Cleaning Options
Administrator mode enables deep system cleaning affecting shared system components and root-owned files. System-wide cache removal, log file deletion, and package manager cleanup require administrator privileges for complete execution.
Advanced users can create custom cleaning configurations targeting specific file types or directories. Custom cleaners enable automated removal of application-specific data not covered by standard cleaning categories. This functionality requires understanding of file system structure and application behavior.
Exercise caution when performing deep cleaning operations. System-wide cleaning can affect application functionality or system performance if essential files are removed accidentally. Always test deep cleaning procedures on non-production systems before deployment.
Security Best Practices
Implement security best practices when using BleachBit to maximize benefits while minimizing risks. Run regular backups before performing extensive cleaning operations, particularly when using administrator mode or custom cleaning configurations.
Understand file recovery implications when using secure deletion features. Securely deleted files cannot be recovered through standard methods, making this operation irreversible. Reserve secure deletion for data requiring permanent destruction while maintaining standard deletion for recoverable files.
Regular cleaning schedules optimize system performance while maintaining security. Weekly browser cleaning and monthly system cleaning provide good maintenance balance without excessive time investment. Adjust cleaning frequency based on system usage patterns and security requirements.
Troubleshooting Common Issues
Permission and Access Errors
Permission errors frequently occur when BleachBit attempts to access protected system files or directories. These errors typically indicate insufficient privileges for requested cleaning operations. Resolve permission issues by running BleachBit with administrator privileges using sudo bleachbit.
Wayland display server compatibility may cause application launch issues on some Debian 13 installations. Address Wayland-related problems by setting the GDK_BACKEND environment variable:
GDK_BACKEND=x11 bleachbitThis workaround forces BleachBit to use X11 display protocols instead of Wayland, resolving compatibility issues with older application frameworks.
Database and Application Errors
Browser database cleaning occasionally encounters locked database files preventing successful operation. Close all browser instances before running BleachBit to release database locks and enable proper cleaning. Firefox and Chrome maintain multiple processes that may lock databases even after window closure.
SQLite database corruption requires manual intervention using database repair tools. Identify corrupted databases through BleachBit error messages and repair using sqlite3 command-line tools:
sqlite3 database_file.sqlite "PRAGMA integrity_check;"Application-specific cleaning failures may indicate missing application components or modified file locations. Update BleachBit to the latest version to ensure compatibility with current application versions and file structures.
Installation and Launch Problems
Package dependency resolution issues prevent successful BleachBit installation on some systems. Resolve dependency conflicts by updating system packages and installing missing dependencies manually:
sudo apt update
sudo apt install python3-gi python3-gi-cairo gir1.2-gtk-3.0These packages provide essential Python and GTK libraries required for BleachBit operation. Installing dependencies separately resolves conflicts preventing automatic installation.
GTK theme compatibility may cause interface display problems on customized desktop environments. Reset GTK themes to default values or install missing theme components to resolve display issues. Test BleachBit with different themes to identify compatibility problems.
Performance and System Issues
System slowdown after cleaning operations typically indicates removal of essential cache files or application data. Allow time for applications to rebuild caches and restore normal performance. Most performance impacts resolve automatically as applications recreate necessary cache files.
Prevent over-cleaning by understanding cleaning category implications before enabling options. System and application caches provide performance benefits that require rebuilding after removal. Balance cleaning benefits against temporary performance impacts when selecting cleaning options.
Recovery options for excessive cleaning include restoring from backups or reinstalling affected applications. Maintain current system backups before extensive cleaning operations to provide recovery options if problems arise.
Best Practices and Safety Guidelines
Safe Cleaning Recommendations
Develop safe cleaning practices to maximize BleachBit benefits while minimizing system risks. Start with browser cleaning and user-specific temporary files before progressing to system-wide operations. This gradual approach builds experience while limiting potential damage from cleaning mistakes.
Regularly clean browser data, temporary files, and application caches to maintain system performance. These cleaning categories provide significant benefits with minimal risk to system functionality. Reserve system-wide cleaning for periodic maintenance rather than daily operations.
Regular Maintenance Schedule
Establish regular cleaning schedules based on system usage patterns and performance requirements. Weekly browser cleaning removes accumulated web data while monthly system cleaning addresses temporary file accumulation. Adjust cleaning frequency based on disk space constraints and performance needs.
Monitor system performance improvements after cleaning operations to validate cleaning effectiveness. Measure disk space recovery and application response times to quantify BleachBit benefits. Document cleaning results to optimize future maintenance schedules.
Security Considerations
Balance system optimization with security requirements when configuring BleachBit cleaning options. Privacy-sensitive environments may require comprehensive data wiping while performance-focused users might emphasize cache and temporary file removal.
Understand data recovery implications before enabling secure deletion features. Securely deleted files cannot be recovered through standard methods, making this operation permanent. Reserve secure deletion for truly sensitive data requiring complete destruction.
Regular security assessments help determine appropriate cleaning configurations for specific environments. Business networks may require different cleaning approaches compared to home systems based on compliance requirements and threat models.
Congratulations! You have successfully installed BleachBit. Thanks for using this tutorial for installing the latest version of BleachBit on Debian 13 “Trixie”. For additional help or useful information, we recommend you check the official BleachBit website.