How To Install BleachBit on Rocky Linux 10

System maintenance and privacy protection have become essential priorities for Linux administrators and security-conscious users alike. Rocky Linux 10 systems accumulate temporary files, cached data, browser histories, and other digital clutter that can compromise both performance and privacy over time. Enter BleachBit – a powerful, open-source system cleaning solution that addresses these critical concerns comprehensively.
This detailed guide walks you through multiple installation methods for BleachBit on Rocky Linux 10, from simple package manager installations to advanced source code compilation. Whether you’re a system administrator managing enterprise servers or a privacy-focused user seeking to optimize your desktop environment, you’ll discover the most suitable installation approach for your specific needs and technical requirements.
By following this comprehensive tutorial, you’ll gain complete mastery over BleachBit installation, configuration, and usage on Rocky Linux 10. The guide covers everything from basic prerequisites through advanced automation techniques, ensuring you can implement effective system cleaning and privacy protection strategies immediately after installation.
What is BleachBit?
BleachBit stands as one of the most trusted open-source system cleaning and privacy protection tools available for Linux distributions. This GPL-3.0 licensed software provides comprehensive disk space cleaning, privacy protection, and system optimization capabilities that rival commercial alternatives while maintaining complete transparency through its open-source nature.
The software excels at secure deletion of sensitive data including browsing histories, cache files, cookies, temporary documents, and system logs. Unlike simple file deletion, BleachBit employs advanced overwriting techniques that prevent data recovery attempts, making it particularly valuable for users handling confidential information or operating in security-sensitive environments.
BleachBit’s cross-platform compatibility extends beyond Linux to include Windows systems, though its integration with Linux distributions like Rocky Linux 10 provides superior performance and deeper system access. The software supports thousands of applications through its extensive cleaner database, automatically detecting installed programs and offering appropriate cleaning options for each detected application.
Key advantages include zero telemetry or advertising, lightweight resource consumption, and active community-driven development. The software maintains backwards compatibility with older Linux distributions while continuously adding support for newer applications and system components, ensuring long-term viability for Rocky Linux 10 installations.
Advanced users particularly appreciate BleachBit’s customization capabilities through CleanerML files and custom cleaner creation, allowing integration of organization-specific cleaning requirements and third-party application support that extends beyond the default cleaner database.
Prerequisites and System Requirements
Rocky Linux 10 compatibility with BleachBit requires specific system components and user privileges to ensure successful installation and optimal performance. Understanding these requirements prevents installation failures and ensures all features function correctly after deployment.
Operating System Requirements:
- Rocky Linux 10 (64-bit architecture recommended for optimal performance)
- Kernel version 4.18 or higher (standard with Rocky Linux 10)
- Minimum 512MB RAM (1GB recommended for GUI usage)
- 50MB free disk space for complete installation including dependencies
Software Dependencies:
- Python 3.6 or higher (pre-installed on Rocky Linux 10)
- GTK 3.22 or higher for graphical interface functionality
- GLib 2.50 or higher for core system integration
- Cairo graphics library for rendering operations
Network and Security Requirements:
- Active internet connection for package downloads and repository access
- Root or sudo privileges for system-wide installation and cleaning operations
- Current system updates applied through DNF package manager
- EPEL repository access for extended package availability
Pre-installation Checklist:
Before proceeding with BleachBit installation, verify system update status using sudo dnf update -y and confirm user account privileges through sudo -v command execution. Create backup copies of critical system configurations and personal data, particularly if planning to use advanced cleaning features immediately after installation.
Consider disk space requirements for both installation and operation, as BleachBit may temporarily require additional space during deep cleaning operations depending on the volume of data being processed and removed from the system.
Installation Methods
Installing via DNF Package Manager
The DNF package manager represents the most straightforward and reliable method for installing BleachBit on Rocky Linux 10 systems. This approach leverages Rocky Linux’s integrated package management system to handle dependency resolution, security verification, and future update management automatically.
Step 1: Update System Packages
sudo dnf update -y
sudo dnf upgrade -yThis ensures your Rocky Linux 10 system contains the latest security patches and package definitions before attempting BleachBit installation.
Step 2: Enable EPEL Repository
sudo dnf install epel-release -y
sudo dnf config-manager --set-enabled epelThe Extra Packages for Enterprise Linux (EPEL) repository provides additional software packages not included in Rocky Linux’s default repositories, including BleachBit and various dependencies.
Step 3: Install BleachBit Package
sudo dnf install bleachbit -yDNF automatically resolves and installs required dependencies including Python libraries, GTK components, and associated system tools necessary for BleachBit operation.
Step 4: Verify Installation Success
bleachbit --version
which bleachbitThese commands confirm successful installation and display the installed version information along with the executable file location.
Advantages of DNF Installation:
- Automatic dependency management eliminates manual library installation
- Integrated security verification through package signing
- Simplified future updates using standard system update procedures
- Official repository integration ensures compatibility with Rocky Linux 10
Potential Limitations:
Repository versions may lag behind the latest BleachBit releases, though this trade-off typically favors stability over cutting-edge features for production environments.
Installing via RPM Package
Direct RPM installation provides access to specific BleachBit versions or unofficial builds while maintaining package management integration. This method suits users requiring particular versions or those experiencing repository access issues.
Step 1: Download Official RPM Package
Visit the official BleachBit website and download the appropriate RPM package for Rocky Linux 10. Verify the package integrity using provided checksums or GPG signatures.
Step 2: Install Required Dependencies
sudo dnf install python3 python3-tkinter gtk3 -y
sudo dnf install python3-chardet python3-gobject -yManual dependency installation ensures all required components are available before BleachBit installation.
Step 3: Import GPG Security Key
wget -O- https://www.bleachbit.org/download/linux | sudo rpm --importThis step verifies package authenticity and prevents installation of potentially modified or malicious packages.
Step 4: Install RPM Package
sudo rpm -Uvh bleachbit-*.rpmThe -U flag upgrades existing installations, while -v provides verbose output and -h displays progress indicators during installation.
Verification Commands:
rpm -qa | grep bleachbit
bleachbit --helpWhen to Choose RPM Installation:
- Specific version requirements not available in repositories
- Custom builds or beta versions for testing purposes
- Offline installation scenarios without repository access
- Integration with existing RPM-based deployment systems
Installing from Source Code
Source code installation offers maximum flexibility and access to the latest development features while providing complete control over the compilation and installation process. This method appeals to developers and advanced users requiring customization capabilities.
Step 1: Install Development Dependencies
sudo dnf groupinstall "Development Tools" -y
sudo dnf install git python3 python3-pip python3-devel -y
sudo dnf install gtk3-devel cairo-devel gobject-introspection-devel -yDevelopment tools provide compilation utilities, while Python development packages enable proper integration with system libraries.
Step 2: Clone Official Repository
git clone https://github.com/bleachbit/bleachbit.git
cd bleachbitCloning the official repository ensures access to the complete source code tree including documentation, test suites, and build scripts.
Step 3: Verify Python Dependencies
python3 -m pip install --user pygobject PyGObject
python3 -c "import gi; gi.require_version('Gtk', '3.0'); from gi.repository import Gtk"These commands verify that Python can properly interface with GTK libraries required for BleachBit’s graphical interface.
Step 4: Run from Source Directory
python3 bleachbit.pySource-based execution doesn’t require system-wide installation, allowing testing and evaluation before committing to permanent installation.
Optional System-Wide Installation:
sudo python3 setup.py install
sudo desktop-file-install bleachbit.desktopAdvantages of Source Installation:
- Access to latest development features and bug fixes
- Complete customization through source code modification
- No dependency on package repository availability
- Educational value for understanding software architecture
Considerations:
Manual update management requires periodic repository synchronization, and compilation may require additional development packages depending on system configuration.
Installing via Snap Package
Snap package installation provides containerized deployment with automatic dependency management and security isolation. This method suits users preferring self-contained applications with minimal system integration.
Step 1: Install Snapd Service
sudo dnf install snapd -y
sudo systemctl enable --now snapd.socketSnapd provides the runtime environment for snap package management and execution.
Step 2: Create Symbolic Link
sudo ln -s /var/lib/snapd/snap /snapThis ensures compatibility with snap package expectations for file system layout.
Step 3: Install Core Snap
sudo snap install core
sudo snap refresh coreThe core snap provides essential runtime components for all snap applications.
Step 4: Install BleachBit Snap
sudo snap install bleachbit
snap list | grep bleachbitSnap-Specific Considerations:
Snap packages operate within confined environments that may limit access to certain system areas compared to traditional installations. This security feature may affect cleaning capabilities for some system locations while providing enhanced application isolation.
Initial Setup and Configuration
Proper initial configuration ensures BleachBit operates safely and effectively within your Rocky Linux 10 environment. The configuration process involves security settings, user preferences, and operational parameters that govern cleaning behavior and system interaction.
First Launch Options:
BleachBit supports both graphical and command-line interfaces. Launch the GUI application using bleachbit from the terminal or access it through the system menu under System Tools. Command-line users can explore available options using bleachbit --help to understand parameter usage and automation possibilities.
Essential Preference Configuration:
Navigate to Edit → Preferences to access critical configuration options:
- Language Settings: Configure interface language and locale preferences
- Security Options: Enable preview mode by default to prevent accidental deletions
- Update Preferences: Configure automatic update checking and cleaner database updates
- Debug Options: Enable logging for troubleshooting and performance monitoring
User vs Administrator Modes:
Understanding the distinction between user-level and system-wide cleaning proves crucial for effective BleachBit utilization. Regular user mode restricts cleaning operations to user-accessible files and directories, while administrator mode (sudo bleachbit) provides access to system-wide temporary files, logs, and shared cached data.
Safety Configuration Best Practices:
Enable preview mode for all initial cleaning operations to review selected files before permanent deletion. Configure warning dialogs for destructive operations including file shredding and free space wiping to prevent accidental data loss during routine maintenance operations.
Custom Cleaner Integration:
Advanced users can integrate custom cleaners through CleanerML files placed in the ~/.config/bleachbit/cleaners/ directory. These custom definitions extend BleachBit’s capabilities to handle organization-specific applications and cleaning requirements beyond the default cleaner database.
Using BleachBit GUI Interface
The graphical user interface provides intuitive access to BleachBit’s comprehensive cleaning capabilities through a well-organized, user-friendly design that accommodates both novice and experienced users effectively.
Interface Layout Overview:
The main window features a three-panel design with cleaner categories in the left panel, file preview and results in the center area, and action buttons prominently displayed in the toolbar. This layout facilitates quick navigation between different cleaning categories while maintaining clear visibility of selected operations and their potential impact.
Cleaner Category Navigation:
The left panel organizes cleaners into logical categories including:
- Firefox/Chrome/Edge: Browser-specific cache, cookies, history, and download records
- System: Temporary files, log files, thumbnail caches, and system-wide cached data
- LibreOffice/GIMP: Application-specific temporary files and recent document lists
- Deep Scan: Comprehensive analysis for additional recoverable space
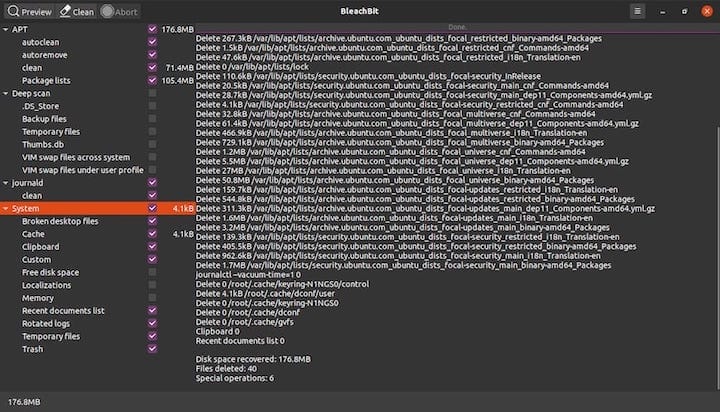
Preview Mode Operation:
The Preview button serves as the primary safety mechanism, analyzing selected cleaners and displaying detailed information about files scheduled for deletion without performing actual removal operations. Preview results include file paths, sizes, and categories, enabling informed decisions about cleaning scope and potential impact.
Selective Cleaning Strategy:
Checkbox-based selection allows granular control over cleaning operations. Start with conservative selections focusing on obviously safe categories like browser caches and temporary files before expanding to more comprehensive system cleaning operations based on experience and confidence levels.
Progress Monitoring:
During cleaning operations, the status bar displays real-time progress information including the number of files processed, space recovered, and estimated completion time. This feedback helps users understand the scope of cleaning operations and identify potential performance bottlenecks.
Results Interpretation:
Post-cleaning summaries provide detailed statistics about space recovered, files removed, and time required for operation completion. These metrics help evaluate cleaning effectiveness and guide future maintenance scheduling decisions.
Command Line Usage and Automation
Command-line operation enables powerful automation capabilities and scripting integration that extend BleachBit’s utility for system administrators and power users managing multiple systems or implementing automated maintenance routines.
Essential Command Syntax:
Basic BleachBit command structure follows the pattern: bleachbit [options] [cleaners]. Options modify behavior while cleaners specify target categories for operations.
Fundamental Commands:
# List all available cleaners
bleachbit --list-cleaners
# Preview specific cleaner operations
bleachbit --preview firefox.cache system.tmp
# Execute cleaning operations
bleachbit --clean firefox.cache system.tmp
# Display system information
bleachbit --sysinfoAdvanced Command Options:
# Clean all Firefox-related data
bleachbit --clean firefox.*
# Preview all system cleaners
bleachbit --preview system.*
# Enable debug mode for troubleshooting
bleachbit --debug --clean system.tmp
# Display version and build information
bleachbit --versionAutomation and Scripting:
Create automated cleaning scripts for regular maintenance:
#!/bin/bash
# Daily maintenance script
echo "Starting daily system cleanup..."
bleachbit --clean system.tmp system.cache system.logs
echo "Cleanup completed. Space recovered:"
df -h /Cron Job Integration:
Schedule automated cleaning using cron for hands-free maintenance:
# Edit crontab
crontab -e
# Add weekly cleaning job (Sundays at 2 AM)
0 2 * * 0 /usr/bin/bleachbit --clean system.tmp firefox.cache >/dev/null 2>&1Root Privilege Considerations:
System-wide cleaning requires root privileges: sudo bleachbit --clean system.*. Exercise caution with automated root-level cleaning scripts and thoroughly test operations in preview mode before implementing automated execution.
Output Redirection and Logging:
Capture cleaning results for monitoring and audit purposes:
bleachbit --clean system.tmp > cleanup.log 2>&1
bleachbit --preview firefox.* | grep "Delete" > preview_report.txtAdvanced Features and Security Options
Advanced security features distinguish BleachBit from basic system cleaning utilities by providing military-grade data destruction capabilities and comprehensive privacy protection mechanisms suitable for high-security environments and confidential data handling.
Secure File Shredding:
The file shredding feature employs multiple-pass overwriting algorithms that prevent data recovery through conventional and advanced forensic techniques:
# Shred specific files
bleachbit --shred /path/to/sensitive/file.txt
# Shred entire directories
bleachbit --shred /path/to/sensitive/directory/Shredding operations use configurable overwrite patterns including random data, zeros, and government-standard algorithms. The process may require significant time for large files due to multiple write operations ensuring complete data destruction.
Free Space Wiping:
Free space wiping prevents recovery of previously deleted files by overwriting unused disk sectors:
# Wipe free space on root partition
sudo bleachbit --wipe-free-space /
# Wipe free space on specific mount point
sudo bleachbit --wipe-free-space /homeThis operation can require substantial time and may impact system performance during execution. Plan free space wiping operations during low-usage periods or maintenance windows.
Database Optimization:
BleachBit includes specialized database cleaning and optimization for common applications:
- Firefox: SQLite database vacuuming improves browser performance
- Chrome/Chromium: Database optimization reduces memory usage
- System databases: Cleanup of package manager and application databases
Custom Cleaner Development:
Advanced users can create custom cleaners using CleanerML format:
<?xml version="1.0" encoding="UTF-8"?>
<cleaner id="custom.application">
<label>Custom Application</label>
<description>Clean custom application data</description>
<option id="cache">
<label>Cache</label>
<description>Delete application cache files</description>
<action command="delete" search="glob" path="~/.custom-app/cache/*"/>
</option>
</cleaner>Save custom cleaners in ~/.config/bleachbit/cleaners/ for automatic recognition and integration.
Troubleshooting Common Issues
Installation and Runtime Problems can occur due to dependency conflicts, permission issues, or system configuration variations. Understanding common scenarios and their solutions enables quick resolution and maintains system stability.
Permission and Access Errors:
# Error: Permission denied when cleaning system files
# Solution: Use sudo for system-wide operations
sudo bleachbit --clean system.tmp
# Error: Cannot access display
# Solution: Verify X11 forwarding for remote sessions
echo $DISPLAY
xhost +local:Dependency and Library Issues:
# Error: ImportError: No module named 'gi'
# Solution: Install PyGObject and GTK development packages
sudo dnf install python3-gobject gtk3-devel
# Error: Cannot load GTK
# Solution: Verify GTK installation and environment
python3 -c "import gi; gi.require_version('Gtk', '3.0')"Performance and Resource Problems:
When BleachBit operates slowly or consumes excessive resources:
- Large file handling: Break cleaning operations into smaller chunks
- Memory limitations: Close unnecessary applications during cleaning
- Disk I/O bottlenecks: Schedule cleaning during low-activity periods
- Network timeouts: Verify repository connectivity for updates
Configuration and Behavior Issues:
# Reset to default configuration
rm -rf ~/.config/bleachbit/
bleachbit --clean system.tmp
# Rebuild cleaner database
bleachbit --update-cleaners
# Verify installation integrity
bleachbit --sysinfoDebug Mode Operation:
Enable debug mode for detailed troubleshooting information:
bleachbit --debug --preview system.tmp > debug.log 2>&1Debug output includes detailed operation logs, error messages, and system interaction information valuable for identifying specific problems and their root causes.
Common Resolution Strategies:
- Verify system updates: Ensure Rocky Linux 10 packages are current
- Check disk space: Confirm adequate space for temporary operations
- Review user permissions: Validate access rights for target directories
- Test minimal operations: Start with simple cleaners before complex operations
- Consult log files: Review system logs for related error messages
Performance Optimization and Best Practices
Optimal BleachBit usage requires understanding system resources, timing considerations, and strategic cleaning approaches that maximize effectiveness while minimizing system impact and user disruption.
Scheduling Strategy:
Implement regular cleaning schedules based on system usage patterns:
- Daily: Browser cache and temporary files for heavy internet users
- Weekly: System logs and application caches for general desktop usage
- Monthly: Deep scans and database optimization for comprehensive maintenance
- Quarterly: Free space wiping and security-focused cleaning for sensitive environments
Resource Management:
Monitor system resources during cleaning operations to prevent performance degradation:
# Monitor disk I/O during cleaning
iostat -x 1 &
bleachbit --clean firefox.cache
pkill iostat
# Check memory usage
free -h
bleachbit --preview system.*
free -hIncremental Cleaning Approach:
Avoid overwhelming system resources by implementing incremental cleaning strategies:
- Start conservatively: Begin with obviously safe cleaners like browser cache
- Expand gradually: Add system temporary files and logs after gaining confidence
- Monitor results: Track space recovered and system performance impact
- Adjust frequency: Modify cleaning schedules based on actual space accumulation rates
Integration with System Maintenance:
Coordinate BleachBit operations with other maintenance activities:
- Before system backups: Clean unnecessary files to reduce backup size
- After software updates: Remove obsolete cached data and temporary files
- During maintenance windows: Perform intensive operations like free space wiping
- Before disk space alerts: Implement automated cleaning triggers
Security Considerations and Privacy Protection
Privacy protection through BleachBit requires understanding data destruction principles, threat models, and appropriate security measures for different sensitivity levels and regulatory requirements.
Data Classification Strategy:
Categorize data based on sensitivity levels:
- Public data: Standard deletion sufficient
- Internal data: Secure deletion recommended
- Confidential data: Multi-pass shredding required
- Regulated data: Compliance-specific destruction methods
Threat Model Assessment:
Consider potential adversaries and their capabilities:
- Casual access: Basic file deletion provides adequate protection
- Deliberate investigation: Secure deletion and overwriting necessary
- Forensic analysis: Multi-pass shredding and free space wiping essential
- Advanced persistent threats: Comprehensive security protocols required
Compliance Integration:
Many organizations must comply with data protection regulations:
- GDPR: Right to erasure requirements for personal data
- HIPAA: Secure disposal of protected health information
- SOX: Financial record destruction protocols
- PCI DSS: Credit card data security requirements
Implementation Best Practices:
# Comprehensive privacy cleaning
sudo bleachbit --clean firefox.* system.cache system.logs
bleachbit --shred ~/.bash_history
sudo bleachbit --wipe-free-space /home
# Automated privacy maintenance
#!/bin/bash
# Daily privacy routine
bleachbit --clean firefox.cookies firefox.history
bleachbit --clean system.recent_documents
bleachbit --shred ~/.recently-used.xbelCongratulations! You have successfully installed BleachBit. Thanks for using this tutorial for installing the BleachBit open-source system cleaner and privacy tool on Rocky Linux 10 system. For additional or useful information, we recommend you check the official BleachBit website.