How To Install Cockpit on Fedora 42

Managing Linux servers traditionally requires extensive command-line knowledge and SSH access, but Cockpit transforms this experience into an intuitive, browser-based administration interface. This powerful web console allows system administrators to monitor performance, manage services, configure networks, and handle storage devices from any device with a web browser. Fedora 42 users running Workstation, KDE, or other non-Server editions can easily install and configure Cockpit to gain comprehensive server management capabilities without leaving their browser. This guide walks through every step of the installation process, from updating system packages to accessing the web interface and exploring advanced configuration options.
What is Cockpit?
Cockpit represents a free, open-source web-based administration tool designed specifically for Linux servers and workstations. Developed with simplicity and efficiency in mind, this lightweight management interface provides real-time system monitoring and administrative control through any modern web browser. The software architecture leverages the same system APIs that command-line tools use, ensuring complete consistency between web console operations and terminal commands.
Changes made through the Cockpit interface directly modify system configuration files, making the tool transparent and predictable for experienced administrators. This design philosophy means administrators can seamlessly switch between the web console and SSH terminal without conflicts or unexpected behavior. The interface requires minimal system resources and only activates when accessed, making it ideal for servers with limited hardware capabilities.
Whether managing a single home server or coordinating multiple production systems, Cockpit streamlines administrative tasks that traditionally required memorizing complex command sequences. Both beginners and seasoned system administrators benefit from the visual dashboard that presents critical system metrics at a glance.
Key Features and Benefits
Cockpit delivers an extensive feature set that covers virtually every aspect of Linux system administration. The dashboard provides real-time monitoring of CPU utilization, memory consumption, disk I/O operations, and network traffic with interactive graphs that update continuously. System administrators can start, stop, enable, and disable systemd services through an intuitive interface that eliminates the need to remember service names or command syntax.
User account administration becomes straightforward with tools for creating accounts, modifying permissions, setting passwords, and managing SSH keys. Storage management capabilities include partition creation, filesystem formatting, RAID configuration, and LVM volume management through visual workflows. Network configuration tools allow administrators to modify interface settings, create bonds and bridges, and adjust firewall rules without editing configuration files manually.
The integrated log viewer provides powerful filtering and search capabilities for troubleshooting system issues quickly. Virtual machine management features enable administrators to create, configure, and monitor VMs directly from the web interface when the appropriate modules are installed. Software package management includes one-click system updates and package installation through a clean, organized interface.
SELinux management tools help administrators monitor security alerts, adjust policies, and troubleshoot permission issues. The built-in terminal provides full SSH access within the browser, eliminating the need for separate terminal applications. Plugin architecture allows extending functionality through additional modules that integrate seamlessly with the core interface.
Remote access from mobile devices, tablets, and desktop computers makes Cockpit particularly valuable for administrators who need flexibility. No graphical desktop environment needs to be installed on the server itself, conserving resources for production workloads. Cross-platform compatibility ensures consistent administration experiences across different Linux distributions.
Prerequisites
Before beginning the Cockpit installation process on Fedora 42, ensure the system meets several important requirements. A fresh or existing Fedora 42 installation running Workstation, KDE, XFCE, or another variant provides the foundation—note that Fedora Server editions include Cockpit pre-installed and configured automatically.
Root access or sudo privileges are essential for installing packages and modifying system configurations. An active internet connection enables downloading Cockpit packages and dependencies from Fedora’s official repositories. Basic familiarity with terminal commands and Linux system concepts helps navigate the installation steps smoothly.
The firewalld service should be running, as it comes enabled by default on Fedora installations. Minimum hardware specifications include 512MB of RAM and 1GB of free disk space, though these modest requirements suit even older hardware. Verify that port 9090 remains available and not in use by other services, as Cockpit binds to this port for web console access.
Having the server’s IP address or hostname ready facilitates remote access configuration. If planning to manage the system remotely, ensure network connectivity exists between the client device and the Fedora 42 machine.
Step 1: Update System Packages
Maintaining current system packages establishes a secure foundation before installing new software. Updated packages contain the latest security patches, bug fixes, and compatibility improvements that prevent installation conflicts. Open a terminal window and execute the following command with sudo privileges:
sudo dnf update -yThis command instructs DNF, Fedora’s package manager, to download and install all available updates for currently installed packages. The -y flag automatically confirms the update operation without prompting for manual approval, streamlining the process. DNF displays detailed progress information including package names, download sizes, and installation status as it works through the update queue.
The update process typically completes within minutes depending on internet connection speed and the number of packages requiring updates. Pay attention to any messages indicating kernel updates, as these require a system reboot to take effect. If kernel updates were installed, restart the system with:
sudo rebootAfter the system restarts, log back in and verify that all packages updated successfully. This preparation step ensures Cockpit installs against the most current system libraries and dependencies, preventing compatibility issues down the road.
Step 2: Install Cockpit Package
Fedora 42 includes Cockpit packages in its default repositories, simplifying the installation process considerably. The base Cockpit package contains the core web console functionality needed for basic system administration tasks. Install Cockpit by executing this straightforward command:
sudo dnf install cockpit -yDNF resolves dependencies automatically, downloading the Cockpit package along with any required supporting libraries. The installation process displays detailed information about packages being installed, their sizes, and total download requirements. Watch for any error messages during installation, though issues rarely occur when installing from official repositories.
The base Cockpit installation provides essential functionality, but additional modules extend capabilities significantly. Consider installing these popular optional packages based on your administration needs:
sudo dnf install cockpit-packagekit cockpit-storaged cockpit-pcp -yThe cockpit-packagekit module enables graphical software package management and system updates through the web interface. Installing cockpit-storaged provides enhanced storage management features including advanced disk operations. The cockpit-pcp package integrates Performance Co-Pilot for detailed system performance metrics and historical data analysis.
For virtual machine management capabilities, install the cockpit-machines module:
sudo dnf install cockpit-machines -yContainer enthusiasts benefit from cockpit-podman, which provides graphical Podman container management. Verify successful installation by checking the installed Cockpit version:
rpm -q cockpitThis command displays the exact version number of the installed Cockpit package, confirming the installation completed successfully.
Step 3: Start and Enable Cockpit Service
Installing Cockpit packages doesn’t automatically activate the service—explicit commands start and enable the web console. Understanding the difference between starting and enabling services proves important for proper system administration. Starting a service activates it immediately for the current session, while enabling ensures automatic startup after system reboots.
Cockpit uses socket activation, a systemd feature that conserves resources by only launching the full service when connections arrive. Start the Cockpit socket with:
sudo systemctl start cockpit.socketThe socket begins listening on port 9090, ready to launch the full Cockpit service when browsers connect. Enable automatic startup at boot time by executing:
sudo systemctl enable cockpit.socketAlternatively, combine both operations into a single efficient command:
sudo systemctl enable --now cockpit.socketThe --now flag instructs systemd to enable and start the service simultaneously. Verify proper service activation by checking the status:
sudo systemctl status cockpit.socketThe output should indicate “active (listening)” status, confirming the socket awaits incoming connections. Green text and “active” status indicate successful configuration. Look for the line showing “Listen: [::]:9090” which confirms the socket binds to the correct port.
The cockpit.service itself remains inactive until someone accesses the web interface, at which point socket activation triggers the full service automatically. This intelligent design minimizes resource consumption on systems where Cockpit isn’t accessed constantly.
Step 4: Configure Firewall Settings
Firewall configuration represents a critical step for enabling remote access to the Cockpit web console. Fedora 42 employs firewalld as its default firewall management solution, providing zone-based security policies. Without proper firewall rules, connection attempts to the web console will timeout even though Cockpit itself runs correctly.
Add the Cockpit service to the firewall’s allowed services list with this command:
sudo firewall-cmd --add-service=cockpit --permanentThe --permanent flag ensures this rule persists across system reboots and firewall reloads. Reload the firewall configuration to activate the new rule immediately:
sudo firewall-cmd --reloadSome administrators prefer executing both commands in sequence:
sudo firewall-cmd --add-service=cockpit
sudo firewall-cmd --add-service=cockpit --permanentThis approach applies the rule immediately with the first command, then makes it permanent with the second. Verify the firewall rule added successfully by listing active services:
sudo firewall-cmd --list-servicesThe output should include “cockpit” among the allowed services. Cockpit uses TCP port 9090 by default, which the firewall service name encompasses.
Alternatively, configure the firewall using explicit port numbers instead of service names:
sudo firewall-cmd --add-port=9090/tcp --permanent
sudo firewall-cmd --reloadBoth methods achieve identical results—service names often prove more readable and maintainable. For enhanced security in production environments, restrict access to specific IP address ranges:
sudo firewall-cmd --permanent --add-rich-rule='rule family="ipv4" source address="192.168.1.0/24" service name="cockpit" accept'
sudo firewall-cmd --reloadThis rich rule permits Cockpit access only from the specified network subnet, blocking connections from other sources.
Step 5: Access Cockpit Web Console
With installation and configuration complete, accessing the Cockpit web console becomes straightforward. Open any modern web browser—Chrome, Firefox, Safari, or Edge all work excellently. For local access on the Fedora 42 machine itself, navigate to:
https://localhost:9090Remote access from other computers on the network requires using the server’s IP address:
https://192.168.1.100:9090Replace the example IP with your Fedora 42 system’s actual address. Alternatively, use the hostname if DNS resolution works properly on your network:
https://fedora-server:9090The browser displays a security warning about the SSL certificate upon first connection. This warning appears because Cockpit automatically generates a self-signed certificate that browsers don’t recognize as trusted. Click “Advanced” or similar options and proceed to the website—this is safe when connecting to your own server.
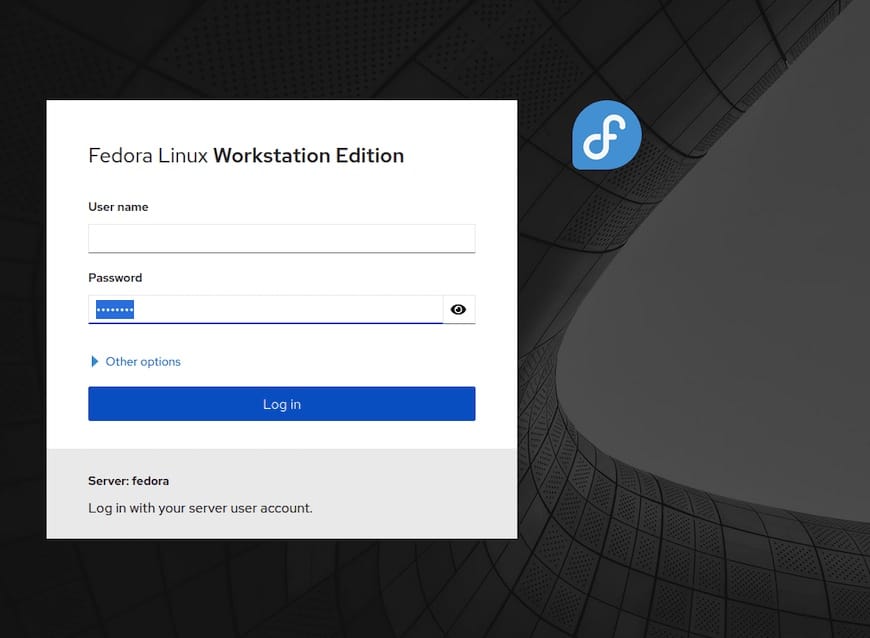
The login screen presents a clean interface requesting username and password credentials. Any local system user account works for authentication, not just administrative accounts. Enter valid credentials and notice the “Reuse my password for privileged tasks” checkbox. Enabling this option allows Cockpit to automatically execute sudo operations without repeatedly prompting for passwords, convenient for administrative sessions.
Root login remains disabled by default, following security best practices. Use a regular user account with sudo privileges for administrative access instead. After successful authentication, the main dashboard appears, displaying system information and real-time performance metrics.
The overview page shows current CPU and memory utilization through interactive graphs. Storage utilization, network traffic statistics, and system information populate the interface immediately. The left navigation menu provides access to all available management sections organized logically.
Understanding the Cockpit Dashboard
The Cockpit interface organizes functionality into clearly defined sections accessible through the left navigation menu. Understanding each section’s purpose maximizes efficiency when performing administrative tasks.
The Overview section displays system health at a glance, including hardware specifications, operating system version, hostname, and system time. Interactive performance graphs show CPU usage, memory consumption, disk I/O, and network activity with updates every second. Clicking graphs expands detailed views with historical data when Performance Co-Pilot is installed.
Logs provides comprehensive access to the systemd journal with powerful filtering capabilities. Search for specific terms, filter by severity level, or narrow results to particular time ranges. Log entries display with context, making troubleshooting significantly faster than parsing raw journal files.
Storage management tools present all connected disks, partitions, and filesystems in visual layouts. Create partitions, format filesystems, mount volumes, and manage RAID arrays through guided workflows. LVM operations including volume group creation and logical volume management become accessible to administrators unfamiliar with command syntax.
Networking configuration includes interface management, network bond creation, bridge setup, and VLAN configuration. Firewall rule management provides graphical zone configuration and service management. Network statistics graphs show traffic patterns for each interface.
Accounts administration centralizes user and group management operations. Create accounts, modify passwords, configure password expiration policies, and manage SSH authorized keys. User session information shows currently logged-in accounts and their activities.
Services lists all systemd units with their current states. Start, stop, restart, enable, and disable services with single clicks. View service logs, configuration files, and dependency relationships directly from the interface.
Applications appears when cockpit-packagekit is installed, enabling package installation and removal through search functionality. Browse available software by category or search for specific packages.
Software Updates shows available system updates with detailed package lists and changelogs. Apply updates with automatic reboot scheduling when necessary.
Terminal provides embedded SSH access within the browser, eliminating the need for separate terminal applications. Full shell access with command history and tab completion functions identically to standard SSH sessions.
SELinux management tools display security alerts, policy status, and troubleshooting recommendations. Adjust enforcement modes and view detailed access denial logs.
Each section integrates directly with underlying system APIs and configuration files, ensuring changes persist correctly and remain compatible with command-line administration.
Installing Additional Cockpit Modules
Cockpit’s modular architecture allows administrators to install only needed functionality, keeping the base system lightweight. Additional modules extend capabilities for specialized tasks without bloating the core installation.
Install modules using DNF from the command line:
sudo dnf install cockpit-machines -yThe cockpit-machines package enables complete virtual machine management including VM creation, configuration, storage management, and console access. This module integrates with libvirt, providing graphical control over KVM virtualization.
Container management becomes available through cockpit-podman:
sudo dnf install cockpit-podman -yThis module allows administrators to manage Podman containers, images, volumes, and pods through the Cockpit interface. Pull container images, create new containers, and monitor resource usage visually.
Advanced performance monitoring requires cockpit-pcp:
sudo dnf install cockpit-pcp -yPerformance Co-Pilot integration provides historical performance data, detailed metrics, and customizable dashboards. This proves valuable for capacity planning and performance troubleshooting.
Additional useful modules include cockpit-storaged for enhanced disk management and cockpit-sosreport for generating diagnostic reports. Third-party repositories like 45Drives provide specialized modules for file sharing, ZFS management, and enterprise storage features.
After installing new modules, they appear automatically in the Cockpit navigation menu without requiring service restarts. Remove unwanted modules with standard DNF commands:
sudo dnf remove cockpit-podman -yBrowse available Cockpit modules by searching the repository:
dnf search cockpit-This command lists all packages matching “cockpit-” prefix, revealing available extensions.
Configuring Cockpit Settings
Cockpit’s default configuration suits most use cases, but customization options exist for specific requirements. The main configuration file resides at /etc/cockpit/cockpit.conf which administrators can edit to modify behavior.
Create or edit the configuration file:
sudo nano /etc/cockpit/cockpit.confCommon configuration options include customizing the login page title:
[WebService]
LoginTitle=Fedora 42 Production ServerThis title appears on the login screen, helping distinguish between multiple managed systems. Configure allowed origins for cross-origin requests when accessing Cockpit through reverse proxies:
[WebService]
Origins = https://example.com:9090 https://192.168.1.100:9090Security-conscious administrators might restrict maximum session duration:
[WebService]
MaxSessionIdleTime=15This setting automatically logs out users after 15 minutes of inactivity. Root login can be enabled, though this practice contradicts security recommendations:
[WebService]
AllowUnencrypted=falseAfter modifying configuration files, restart Cockpit to apply changes:
sudo systemctl restart cockpit.socketCertificate management deserves attention for production deployments. Cockpit automatically generates self-signed certificates stored in /etc/cockpit/ws-certs.d/. Replace these with proper certificates from Let’s Encrypt or internal certificate authorities for production use.
Copy certificate files to the appropriate directory:
sudo cp server.cert /etc/cockpit/ws-certs.d/
sudo cp server.key /etc/cockpit/ws-certs.d/Cockpit automatically loads certificates from this directory without additional configuration.
Managing Remote Servers with Cockpit
Cockpit excels at managing multiple servers from a single interface, streamlining administration across infrastructure. The dashboard button in the top-left corner provides access to the server selection menu.
Click the hostname dropdown and select “Add new host” to configure remote management. Enter the target server’s hostname or IP address in the dialog box. Cockpit attempts SSH connection using the current user’s credentials.
SSH key-based authentication works seamlessly for passwordless connections. Configure SSH keys beforehand for optimal security:
ssh-copy-id username@remote-serverThis command copies the local public key to the remote server’s authorized_keys file. Password authentication functions but requires entering credentials for each connection.
An interesting capability allows managing systems without Cockpit installed on them. The Cockpit Client Flatpak application runs on the administrator’s workstation and connects to remote servers via SSH, displaying management interfaces without requiring Cockpit installation on targets.
Switch between managed servers using the hostname dropdown menu. All administrative functions work identically whether managing local or remote systems. Version compatibility should be considered when managing servers running different Fedora releases.
Security Best Practices
Implementing proper security measures protects Cockpit installations from unauthorized access and potential vulnerabilities. Strong passwords for all system accounts represent the first line of defense. Enforce password policies requiring complexity and regular rotation.
SSH key-based authentication eliminates password exposure over networks. Generate strong SSH keys with:
ssh-keygen -t ed25519 -C "cockpit-access"Deploy keys to authorized systems while restricting password authentication entirely. Regular security updates close vulnerabilities promptly:
sudo dnf update cockpitEnable automatic security updates for critical patches. Limit administrative access to trusted personnel only, avoiding shared credentials. Use dedicated accounts for Cockpit administration rather than personal user accounts.
HTTPS-only access prevents credential interception. Never enable the AllowUnencrypted option in production environments. Replace self-signed certificates with proper SSL certificates from trusted authorities.
Firewall rules should restrict Cockpit access to specific networks when possible:
sudo firewall-cmd --permanent --add-rich-rule='rule family="ipv4" source address="10.0.0.0/8" service name="cockpit" accept'
sudo firewall-cmd --reloadThis configuration permits access only from the 10.0.0.0/8 network range. Monitor authentication attempts and access patterns through system logs:
sudo journalctl -u cockpit.serviceReview logs regularly for suspicious activity patterns. Maintain the default configuration that prevents direct root login, relying instead on regular accounts with sudo privileges.
SELinux provides additional security layers—never disable it permanently. Address policy violations by adjusting permissions rather than disabling enforcement. Regular security audits identify misconfigurations before exploitation occurs.
Troubleshooting Common Issues
Despite straightforward installation procedures, occasional issues may arise requiring systematic troubleshooting. Understanding common problems and their solutions minimizes downtime and frustration.
Cannot access Cockpit web interface: Verify the service runs correctly:
sudo systemctl status cockpit.socketInactive or failed status indicates service problems. Check service logs for error messages:
sudo journalctl -xeu cockpit.socketConfirm firewall rules allow connections:
sudo firewall-cmd --list-allThe output should show cockpit among allowed services. Test local connectivity before troubleshooting remote access issues.
Browser security warnings: Self-signed certificates trigger warnings in all modern browsers. This behavior is expected and safe when connecting to known servers. Proceed through the warning or install proper certificates to eliminate messages permanently.
Authentication failures: Verify the account exists and has correct permissions:
id usernameCheck PAM configuration in /etc/pam.d/cockpit for policy issues. Password complexity requirements might prevent authentication with weak credentials.
Software updates showing “OSTree” errors: This problem occurs on systems using traditional package management but having cockpit-ostree installed unnecessarily. Remove the conflicting package:
sudo dnf remove cockpit-ostree -yInstall the correct package manager module:
sudo dnf install cockpit-packagekit -yRefresh the browser to see updates appear correctly.
Virtual machines not appearing: Ensure hardware virtualization is enabled in BIOS/UEFI settings. Verify cockpit-machines installation:
rpm -q cockpit-machinesCheck libvirt service status:
sudo systemctl status libvirtdStart and enable libvirt if inactive:
sudo systemctl enable --now libvirtdPerformance issues or sluggishness: Monitor system resources to identify bottlenecks. Install cockpit-pcp for detailed performance analysis. Restart the Cockpit service if experiencing temporary issues:
sudo systemctl restart cockpit.socketCannot connect to remote hosts: Test SSH connectivity manually first:
ssh username@remote-serverVerify network routing and firewall rules on both systems. Ensure Cockpit socket runs on the remote server if managing Cockpit-to-Cockpit connections.
Congratulations! You have successfully installed Cockpit. Thanks for using this tutorial for installing Cockpit web-based graphical interface for managing Linux servers on Fedora 42 Linux system. For additional help or useful information, we recommend you check the official Cockpit website.