How To Install Docker Desktop on Debian 13

Docker Desktop has revolutionized the way developers work with containers, providing an intuitive graphical interface that simplifies container management and development workflows. Debian 13, known for its stability and robust package management system, serves as an excellent foundation for containerized development environments. This comprehensive guide walks you through every step of installing Docker Desktop on Debian 13, ensuring a smooth setup process that gets you up and running with containerization technology.
Whether you’re a seasoned system administrator, a software developer transitioning to containerized applications, or a Linux enthusiast exploring modern development tools, this guide provides the detailed instructions and troubleshooting tips you need. Docker Desktop transforms complex container operations into user-friendly experiences, making it easier to build, share, and run applications across different environments.
The installation process involves several critical steps, from preparing your system and configuring repositories to post-installation optimization and security considerations. Understanding these components ensures not only a successful installation but also optimal performance and security for your containerized development environment.
Prerequisites and System Requirements
Hardware Requirements
Docker Desktop demands specific hardware capabilities to function effectively on Debian 13. Your system must feature a 64-bit kernel with CPU virtualization support enabled in the BIOS or UEFI settings. Modern processors from Intel (VT-x) and AMD (AMD-V) include these virtualization extensions, but they may require manual activation in system firmware.
Memory requirements are particularly crucial for container operations. While Docker Desktop technically runs with 4 GB of RAM, optimal performance requires at least 8 GB, especially when running multiple containers or resource-intensive applications. Consider that Docker Desktop itself consumes system resources, and containers add additional memory overhead.
Storage considerations extend beyond simple disk space requirements. Docker images and containers can quickly accumulate significant storage, particularly when working with multiple projects or large application stacks. Allocate at least 20 GB of free disk space, though production environments often require substantially more. SSD storage dramatically improves Docker performance compared to traditional hard drives, particularly for image pulls and container startup times.
Virtualization support verification ensures compatibility with Docker’s backend systems. Execute grep -E "(vmx|svm)" /proc/cpuinfo to confirm hardware virtualization capabilities. The presence of “vmx” indicates Intel VT-x support, while “svm” confirms AMD-V functionality. Without these features, Docker Desktop cannot leverage hardware-accelerated virtualization.
Software Prerequisites
Debian 13 compatibility requires specific software configurations beyond basic operating system installation. Docker Desktop integrates tightly with desktop environments, necessitating proper graphical interface support. KDE, GNOME, and MATE desktop environments provide comprehensive Docker Desktop integration, though GNOME users require additional configuration steps.
GNOME desktop environments need specific extensions for complete Docker Desktop functionality. The AppIndicator and KStatusNotifierItem extensions enable system tray integration, allowing Docker Desktop to display status information and provide quick access to common functions. Install these extensions through GNOME Extensions or package management systems before proceeding with Docker Desktop installation.
Non-GNOME desktop environments typically require gnome-terminal installation for optimal Docker Desktop integration. Many Docker Desktop features, including integrated terminal access and container logs, depend on gnome-terminal functionality. Install this package using sudo apt install gnome-terminal even if your primary desktop environment uses different terminal applications.
Package management prerequisites include curl, wget, and GPG tools for secure repository access and package verification. These utilities facilitate secure downloads and repository configuration, ensuring installation integrity and security. Verify their presence using which curl wget gpg commands before proceeding.
User Permissions and Access
Administrative privileges are essential throughout the Docker Desktop installation process. Your user account requires sudo access for package installation, repository configuration, and system service management. Verify sudo privileges by executing sudo -v and entering your password when prompted.
Internet connectivity enables package downloads, repository access, and Docker image pulls during installation verification. Configure network settings appropriately, ensuring DNS resolution functions correctly. Test connectivity using ping 8.8.8.8 and nslookup docker.com commands to verify both network access and domain name resolution.
Docker group membership becomes crucial post-installation for non-root container operations. While not required during initial installation, understanding user group concepts helps prevent common permission issues later. The installation process automatically creates the docker group and provides guidance for user addition.
Pre-Installation System Preparation
System Update and Package Management
Begin Docker Desktop installation by ensuring your Debian 13 system includes the latest security patches and package updates. System currency prevents compatibility issues and ensures access to recent package versions that Docker Desktop requires.
Execute sudo apt update to refresh package repository information, downloading the latest package metadata from configured repositories. This step synchronizes your local package database with upstream repositories, ensuring accurate dependency resolution during subsequent installation steps.
Follow package list updates with sudo apt upgrade to install available security patches and package updates. This comprehensive system update process may require significant time depending on the number of available updates and your internet connection speed. Reboot your system if kernel updates were included in the upgrade process.
Install essential prerequisite packages using sudo apt install apt-transport-https ca-certificates curl gnupg lsb-release. These packages provide secure repository access, certificate validation, download capabilities, and cryptographic verification tools necessary for Docker repository configuration. The apt-transport-https package enables secure HTTPS repository access, while ca-certificates provides trusted certificate authority certificates for SSL/TLS verification.
Verify successful package installation by checking individual package status using dpkg -l | grep -E "(curl|gnupg|ca-certificates)". This command displays installed package versions and confirms successful installation completion.
Removing Previous Docker Installations
Clean removal of existing Docker installations prevents conflicts and ensures proper Docker Desktop integration. Previous installations may include Docker Engine, community Docker packages, or incomplete Docker Desktop installations that interfere with the new setup process.
Identify existing Docker components using dpkg -l | grep docker to display all Docker-related packages installed through package management systems. Remove these packages systematically to prevent conflicts with Docker Desktop installation.
Execute comprehensive Docker removal using:
sudo apt remove docker docker-engine docker.io containerd runc
sudo apt purge docker-ce docker-ce-cli containerd.io docker-compose-plugin
sudo rm -rf /var/lib/docker
sudo rm -rf /var/lib/containerdThese commands remove Docker packages, configuration files, and data directories completely. The purge operation removes configuration files in addition to package binaries, while manual directory removal eliminates persistent data that might interfere with fresh installations.
Verify complete removal by checking for remaining Docker processes using ps aux | grep docker and ensuring no Docker-related systemd services remain active with systemctl list-units | grep docker. Clean removal prevents port conflicts, service conflicts, and configuration interference.
Desktop Environment Configuration
Desktop environment preparation ensures optimal Docker Desktop integration and user experience. GNOME users require specific extension installation and configuration, while other desktop environments need terminal application verification.
Install GNOME Shell extensions for Docker Desktop system tray support:
sudo apt install gnome-shell-extension-appindicator
sudo apt install gnome-shell-extension-top-icons-plusEnable installed extensions using GNOME Tweaks or the Extensions application. These extensions provide system tray functionality that Docker Desktop requires for status display and quick access features. Log out and log back in to activate extension changes completely.
Alternative desktop environments typically work with Docker Desktop without additional configuration, though gnome-terminal installation improves integration. Install gnome-terminal using sudo apt install gnome-terminal regardless of your primary desktop environment choice.
Test system tray functionality by running applications that use system tray integration, ensuring proper display and interaction capabilities before proceeding with Docker Desktop installation.
Docker Repository Setup
Adding Docker’s Official GPG Key
Secure package installation requires Docker’s official GPG key for package verification and authenticity confirmation. This cryptographic verification prevents package tampering and ensures installation integrity throughout the process.
Create a directory for Docker GPG keys and download the official key using secure methods:
sudo mkdir -p /etc/apt/keyrings
curl -fsSL https://download.docker.com/linux/debian/gpg | sudo gpg --dearmor -o /etc/apt/keyrings/docker.gpgThe curl command downloads Docker’s GPG key using secure HTTPS connection, while gpg --dearmor converts the key into the binary format required by APT package management. The /etc/apt/keyrings directory provides a standardized location for package signing keys.
Verify GPG key installation and fingerprint accuracy using:
sudo gpg --show-keys /etc/apt/keyrings/docker.gpgCompare the displayed fingerprint with Docker’s officially published fingerprint to ensure authenticity. This verification step prevents man-in-the-middle attacks and confirms you’re installing legitimate Docker packages.
Set appropriate permissions for the GPG key file:
sudo chmod a+r /etc/apt/keyrings/docker.gpgThese permissions allow APT to read the key file while maintaining security through restricted write access.
Repository Configuration
Docker’s official repository provides the most current and secure Docker Desktop packages for Debian systems. Proper repository configuration ensures access to official packages and automatic updates through standard package management workflows.
Add Docker’s repository to your APT sources list using architecture-specific configuration:
echo "deb [arch=$(dpkg --print-architecture) signed-by=/etc/apt/keyrings/docker.gpg] https://download.docker.com/linux/debian $(lsb_release -cs) stable" | sudo tee /etc/apt/sources.list.d/docker.list > /dev/nullThis command automatically detects your system architecture and Debian version, ensuring correct repository URL configuration. The signed-by parameter associates the repository with Docker’s GPG key for package verification.
Update package lists to include Docker repository packages:
sudo apt updateVerify repository addition by checking available Docker packages:
apt-cache search docker-desktopThis command should display Docker Desktop packages available for installation, confirming successful repository configuration.
Docker Desktop Installation Methods
Method 1: Official DEB Package Installation
Direct DEB package installation provides immediate access to the latest Docker Desktop release without dependency on repository configuration. This method suits environments with restricted internet access or specific version requirements.
Download the latest Docker Desktop DEB package from Docker’s official website or using command-line tools:
wget https://desktop.docker.com/linux/main/amd64/docker-desktop-amd64.debVerify package integrity using checksums provided on Docker’s download page. Compare SHA256 checksums using:
sha256sum docker-desktop-amd64.debInstall the downloaded package using APT package manager:
sudo apt install ./docker-desktop-amd64.debThe ./ prefix instructs APT to install from the local file rather than searching repositories. APT automatically resolves dependencies and installs required packages during this process.
Monitor installation progress and respond to configuration prompts as needed. The installation process may present licensing agreements or configuration options that require user confirmation.
Method 2: Repository-Based Installation
Repository-based installation provides automatic updates and simplified package management through standard APT operations. This method integrates Docker Desktop into your system’s regular update cycle.
Install Docker Desktop directly from the configured repository:
sudo apt install docker-desktopAPT automatically downloads and installs Docker Desktop along with all required dependencies. This method ensures compatibility with your system’s package management and provides automatic security updates.
Verify successful installation by checking package status:
dpkg -l | grep docker-desktopRepository installation creates desktop environment integration automatically, including application menu entries and file associations.
Post-Installation Configuration
Initial Setup and Verification
Docker Desktop requires initial configuration and verification to ensure proper functionality and optimal performance. Launch the application through your desktop environment’s application menu or using command-line execution.
Start Docker Desktop from the terminal:
systemctl --user start docker-desktopThe initial startup process may require several minutes as Docker Desktop initializes its backend services and downloads necessary components. Monitor startup progress through the application interface or system logs.
Configure resource allocation according to your system capabilities and development requirements. Access settings through the Docker Desktop interface and adjust CPU allocation, memory limits, and disk space allocation. Conservative initial settings prevent system performance issues while allowing adjustment based on actual usage patterns.
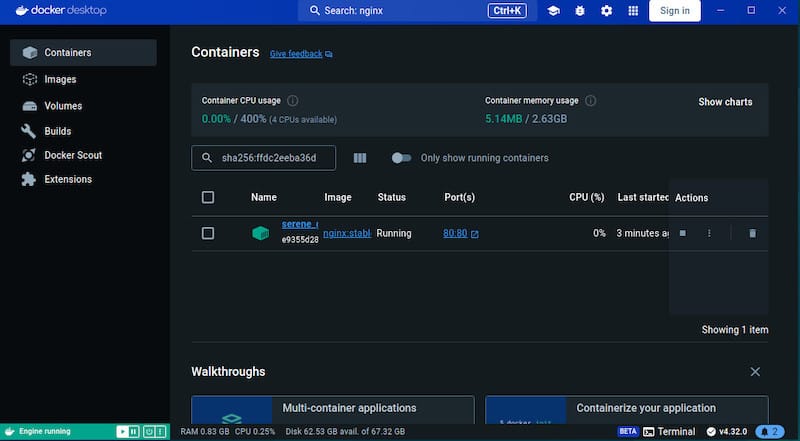
Test basic Docker functionality using the hello-world container:
docker run hello-worldThis command downloads and runs a minimal test container, verifying Docker installation, network connectivity, and basic container operations. Successful execution confirms proper Docker Desktop installation and configuration.
User and Group Management
Docker group membership enables non-root Docker command execution, improving security and user experience. The installation process creates the docker group automatically, but manual user addition is required.
Add your user account to the docker group:
sudo usermod -aG docker $USERLog out and log back in to activate group membership changes. Alternatively, use newgrp docker to activate group membership in the current session without logging out.
Verify group membership using:
groups $USER | grep dockerTest non-root Docker access by running:
docker psThis command should execute successfully without requiring sudo privileges, confirming proper group configuration.
Consider security implications of docker group membership, as it provides root-equivalent access to the Docker daemon. Users in the docker group can potentially escalate privileges through container operations, so limit membership to trusted users only.
System Integration
Complete Docker Desktop integration requires verification of system-level components and configurations. Check Docker CLI installation and functionality through command-line interface testing.
Verify Docker CLI installation:
which docker
docker --versionThese commands confirm Docker CLI availability and display version information, ensuring command-line interface functionality.
Test Docker Compose integration:
docker compose versionDocker Desktop includes Docker Compose automatically, providing multi-container application management capabilities essential for modern development workflows.
Configure Docker Desktop autostart if desired through your desktop environment’s startup applications configuration. This setting automatically launches Docker Desktop during system boot, ensuring containers and services start automatically.
Testing and Verification
Comprehensive testing validates Docker Desktop installation and identifies potential issues before production use. Execute various test scenarios to confirm functionality across different Docker features and capabilities.
Run additional test containers to verify image downloading and container execution:
docker run -it --rm ubuntu:latest bashThis command downloads the Ubuntu image and starts an interactive container, allowing you to test container networking, file system access, and process isolation. Exit the container using the exit command.
Test port mapping functionality:
docker run -d -p 8080:80 nginx:latestThis command starts an Nginx web server container with port mapping, allowing access through http://localhost:8080. Verify web server accessibility using your web browser or curl commands.
Test volume mounting capabilities:
docker run -v /tmp:/app ubuntu:latest ls /appVolume mounting enables file sharing between host systems and containers, essential for development workflows. This test confirms proper file system integration and permission handling.
Clean up test containers:
docker container prune
docker image pruneThese commands remove stopped containers and unused images, maintaining system cleanliness and preventing unnecessary storage consumption.
Troubleshooting Common Issues
Installation Problems
Installation difficulties often stem from repository configuration errors, dependency conflicts, or insufficient system resources. Systematic troubleshooting approaches resolve most common installation issues effectively.
Repository access problems typically manifest as package not found errors or GPG verification failures. Verify repository configuration using:
cat /etc/apt/sources.list.d/docker.listEnsure the repository URL, architecture, and signing key path match expected values. Reconfigure the repository if discrepancies exist.
Dependency conflicts may occur with existing Docker installations or conflicting packages. Remove conflicting packages systematically and retry installation:
sudo apt autoremove
sudo apt autocleanThese commands remove orphaned packages and clean package cache, resolving many dependency-related issues.
Permission errors during installation typically indicate insufficient sudo privileges or file system permission problems. Verify sudo access and ensure adequate disk space for package installation and extraction.
Runtime Issues
Docker Desktop runtime problems often involve service startup failures, resource allocation issues, or desktop environment integration problems. Systematic diagnosis approaches identify root causes effectively.
Docker daemon startup failures typically generate specific error messages in system logs. Check Docker Desktop logs using:
journalctl --user -u docker-desktopCommon startup issues include insufficient system resources, virtualization support problems, or conflicting services. Address identified issues systematically based on log message content.
System tray integration problems particularly affect GNOME users without proper extension configuration. Verify extension installation and activation:
gnome-extensions list | grep -i indicatorReinstall or reconfigure GNOME extensions if system tray functionality remains problematic.
Resource allocation errors occur when Docker Desktop cannot allocate requested CPU, memory, or disk resources. Adjust allocation settings through the Docker Desktop interface, reducing resource requests to match system capabilities.
Performance and Networking
Performance optimization ensures efficient Docker operation and prevents system resource exhaustion. Monitor resource usage and adjust configurations based on actual workload requirements.
Container performance issues often stem from insufficient resource allocation or storage driver inefficiencies. Monitor system resource usage during container operations:
docker statsThis command displays real-time resource consumption for running containers, helping identify resource bottlenecks and optimization opportunities.
Network connectivity problems within containers may indicate DNS configuration issues or firewall interference. Test container network connectivity:
docker run --rm alpine:latest nslookup google.comDNS resolution failures often require Docker daemon configuration adjustments or host system DNS configuration changes.
Storage performance optimization may require storage driver selection based on system characteristics. Docker Desktop typically selects appropriate storage drivers automatically, but manual optimization may benefit specific use cases.
Best Practices and Security Considerations
Docker Desktop security requires ongoing attention to updates, configuration management, and container security practices. Implement comprehensive security measures to protect both Docker installations and containerized applications.
Regular Docker Desktop updates provide security patches and feature improvements essential for secure operation. Enable automatic updates through Docker Desktop settings or monitor release announcements for manual update scheduling.
Container image security scanning identifies vulnerabilities in base images and application dependencies. Use Docker Scout or integrated security scanning features to analyze image security before deployment:
docker scout cves [image-name]Resource monitoring prevents resource exhaustion attacks and ensures system stability. Configure resource limits for containers and monitor consumption patterns regularly.
Network security configurations isolate container networks and prevent unauthorized access. Use custom networks for multi-container applications and avoid exposing unnecessary ports to host systems.
Backup strategies protect Docker data and configurations from loss or corruption. Regular backups of Docker volumes, container configurations, and custom images ensure recovery capabilities during system failures.
Advanced Configuration and Tips
Advanced Docker Desktop configuration optimizes performance and integrates with development workflows effectively. Customize daemon configuration, resource allocation, and integration settings based on specific requirements.
Custom Docker daemon configuration enables fine-tuned performance optimization and security enhancements. Edit daemon configuration through Docker Desktop settings or direct configuration file modification.
Development tool integration streamlines container-based development workflows. Configure IDE integration, Git repository mounting, and automated build processes for efficient development cycles.
Multi-platform development capabilities enable cross-platform application building and testing. Configure BuildKit and multi-architecture image building for comprehensive application compatibility testing.
Resource quota management prevents individual containers from consuming excessive system resources. Implement container resource limits and system-wide quotas for stable multi-user environments.
Logging configuration customization enables effective troubleshooting and monitoring. Configure log drivers, rotation policies, and centralized logging integration for production-ready logging infrastructure.
Congratulations! You have successfully installed Docker Desktop. Thanks for using this tutorial to install the latest version of Docker Desktop on Debian 13 “Trixie“. For additional help or useful information, we recommend you check the official Docker website.