How To Install Gitea on Fedora 43

Gitea offers a lightweight, self-hosted alternative to commercial Git services, giving you complete control over your source code repositories. This powerful open-source platform combines the familiar features of GitHub with the flexibility of running on your own infrastructure, making it ideal for development teams, organizations, and individual developers who prioritize data sovereignty and customization.
Installing Gitea on Fedora 43 provides an excellent foundation for hosting unlimited repositories, managing collaborative development workflows, and maintaining full ownership of your code. This comprehensive guide walks you through every step of the installation process, from initial system preparation to advanced configuration with SSL encryption and reverse proxy setup.
What is Gitea?
Gitea is a painless, self-hosted Git service written in Go that provides a complete code hosting solution. As a fork of Gogs, Gitea has evolved into a mature platform that delivers enterprise-grade features while maintaining remarkably low resource requirements.
The platform supports repository management, issue tracking, pull requests, code review, wikis, and project boards. Gitea also includes built-in CI/CD capabilities through Gitea Actions, which offers GitHub Actions compatibility. Additional features include support for over 20 package registry types, making it a comprehensive artifact repository solution.
Organizations choose Gitea for several compelling reasons. The application requires minimal system resources—running smoothly on just 1GB of RAM—while supporting thousands of repositories. Unlike heavier alternatives such as GitLab, Gitea maintains a small footprint without sacrificing essential functionality. The single-binary deployment model simplifies installation, updates, and maintenance significantly.
Gitea excels in environments ranging from small development teams to large enterprises. Personal developers appreciate the straightforward setup and low operating costs. Companies benefit from complete data control, customizable branding, and the ability to integrate with existing infrastructure seamlessly.
System Requirements and Prerequisites
Hardware Requirements
Your Fedora 43 server should meet minimum specifications to ensure smooth operation. A single CPU core and 1GB of RAM provide adequate performance for small teams with up to 10 active users. Disk space requirements start at 1GB for the application and database, though you’ll need additional storage for repositories.
Recommended specifications include 2 CPU cores, 2GB of RAM, and at least 10GB of disk space. These specifications comfortably support teams with 50-100 users and hundreds of repositories. Larger deployments scale linearly with user count and repository size.
Software Prerequisites
Fedora 43 must be fully installed and updated before beginning the Gitea installation. The system requires Git version 2.0.0 or later for repository operations. You’ll need a database server—MariaDB, PostgreSQL, or SQLite—to store application data and metadata.
Optional components enhance functionality and security. A reverse proxy such as Nginx or Apache enables domain-based access and SSL termination. Valid SSL/TLS certificates from Let’s Encrypt or a commercial certificate authority provide encrypted connections.
Access Requirements
Root or sudo privileges are essential for installing packages and configuring system services. SSH access to your Fedora 43 server allows remote administration. Basic command-line proficiency helps you follow the installation steps confidently. You’ll also need the ability to modify firewall rules for network access configuration.
Step 1: Update System and Install Dependencies
Begin by connecting to your Fedora 43 server via SSH. Updating the system ensures you have the latest security patches and package versions.
sudo dnf update -yThis command refreshes package metadata and upgrades all installed packages to their newest versions. The process typically takes several minutes depending on your server’s internet connection and the number of updates available.
Next, install the required dependencies for Gitea operation:
sudo dnf install git wget tar -yGit provides version control functionality that Gitea uses internally. The wget utility downloads files from remote servers. The tar package handles compressed archives during installation and backup operations.
Verify Git installation successfully completed:
git --versionThe command should display Git version 2.43 or newer. Fedora 43 repositories include recent Git versions that meet all Gitea requirements.
Step 2: Install and Configure Database Server
Installing MariaDB
MariaDB provides a robust, open-source relational database that handles Gitea’s data storage needs efficiently. Install MariaDB server and client packages:
sudo dnf install mariadb mariadb-server -yConfigure MariaDB to start automatically at system boot:
sudo systemctl enable mariadbStart the MariaDB service immediately:
sudo systemctl start mariadbVerify the database server is running correctly:
sudo systemctl status mariadbThe output should show “active (running)” in green text, indicating successful startup.
Securing MariaDB
Run the security configuration script to harden your database installation:
sudo mysql_secure_installationThe interactive script prompts you through several security options. When asked about the current root password, press Enter since none exists on fresh installations. Choose to set a root password and enter a strong passphrase that you’ll remember.
Answer “Y” to remove anonymous users, which prevents unauthorized database access. Disallow root login remotely by answering “Y” to enhance security. Remove the test database and access privileges by selecting “Y”. Finally, reload privilege tables immediately by answering “Y”.
Creating Gitea Database
Log into the MariaDB console as the root user:
sudo mysql -u root -pEnter the root password you configured during the security setup. The MariaDB prompt appears, ready for SQL commands.
Create a dedicated database for Gitea with proper character encoding:
CREATE DATABASE gitea CHARACTER SET utf8mb4 COLLATE utf8mb4_unicode_ci;The utf8mb4 character set supports all Unicode characters, including emojis and special symbols in repository content.
Create a dedicated database user with appropriate permissions:
CREATE USER 'gitea'@'localhost' IDENTIFIED BY 'Your_Secure_Password_Here';Replace “Your_Secure_Password_Here” with a strong password combining uppercase letters, lowercase letters, numbers, and special characters. Avoid common words or predictable patterns.
Grant the Gitea user full privileges on the database:
GRANT ALL PRIVILEGES ON gitea.* TO 'gitea'@'localhost';Apply the privilege changes immediately:
FLUSH PRIVILEGES;Exit the MariaDB console:
EXIT;Your database is now prepared to store Gitea application data, user accounts, repository metadata, and operational information.
Step 3: Create Dedicated System User for Gitea
Running services as dedicated system users follows security best practices by limiting potential damage from security vulnerabilities. Create a system account specifically for Gitea:
sudo useradd --system --shell /bin/bash --comment 'Git Version Control' --create-home --home /home/git gitThe --system flag creates a system account with a UID below 1000. The --shell /bin/bash parameter allows the user to execute shell commands. The --create-home and --home /home/git options establish the user’s home directory where repositories will be stored.
Verify the account was created successfully:
id gitThe output displays the user ID, group ID, and group memberships for the git user.
Step 4: Download and Install Gitea Binary
Downloading Gitea
Navigate to the temporary directory:
cd /tmpDownload the latest stable Gitea binary for Linux AMD64 architecture. Visit the official Gitea downloads page to identify the current stable version, then download it:
wget -O gitea https://dl.gitea.io/gitea/1.22/gitea-1.22-linux-amd64Replace “1.22” with the latest stable version number available at the time of your installation. Gitea regularly releases updates with bug fixes, security patches, and new features.
Installing Binary
Move the downloaded binary to the system binary directory:
sudo mv gitea /usr/local/bin/giteaThe /usr/local/bin directory contains locally-installed executables that aren’t managed by the package manager.
Make the binary executable:
sudo chmod +x /usr/local/bin/giteaSet proper ownership for the binary:
sudo chown git:git /usr/local/bin/giteaThis ensures the git user owns the executable, following the principle of least privilege.
Verify the installation completed successfully:
gitea --versionThe command outputs version information, confirming Gitea is properly installed and executable.
Understanding Binary Installation Benefits
Single-binary deployment offers significant advantages over traditional package installations. Updates require simply downloading a new binary and restarting the service. Rollbacks happen instantly by reverting to the previous binary file. Dependency conflicts never occur since Gitea bundles all requirements.
Step 5: Create Required Directory Structure
Creating Directories
Gitea requires several directories for configuration, data storage, and logging. Create the complete directory structure:
sudo mkdir -p /var/lib/gitea/{custom,data,log}The -p flag creates parent directories as needed. The brace expansion creates three subdirectories simultaneously.
Create the configuration directory:
sudo mkdir -p /etc/giteaEach directory serves a specific purpose. The /var/lib/gitea/custom directory holds customized templates, themes, and configurations. The /var/lib/gitea/data directory stores repositories, attachments, avatars, and application data. Logs accumulate in /var/lib/gitea/log for troubleshooting and monitoring.
Setting Permissions
Set appropriate ownership for the data directories:
sudo chown -R git:git /var/lib/gitea/The -R flag applies ownership recursively to all subdirectories and files.
Configure directory permissions to prevent unauthorized access:
sudo chmod -R 750 /var/lib/gitea/These permissions allow the git user full access while restricting others.
Configure the configuration directory with special permissions:
sudo chown root:git /etc/gitea
sudo chmod 770 /etc/giteaDuring installation, the web interface needs write access to create the configuration file. After installation, you’ll tighten these permissions for security.
Step 6: Configure Systemd Service
Creating Service File
Systemd manages services on Fedora 43, handling automatic startup, restart, and monitoring. Create a systemd service file for Gitea:
sudo nano /etc/systemd/system/gitea.serviceAdd the following service configuration:
[Unit]
Description=Gitea (Git with a cup of tea)
After=network.target mariadb.service
[Service]
RestartSec=2s
Type=simple
User=git
Group=git
WorkingDirectory=/var/lib/gitea/
ExecStart=/usr/local/bin/gitea web --config /etc/gitea/app.ini
Restart=always
Environment=USER=git HOME=/home/git GITEA_WORK_DIR=/var/lib/gitea
[Install]
WantedBy=multi-user.targetSave the file by pressing Ctrl+O, then exit with Ctrl+X.
Service Configuration Explanation
The [Unit] section defines service metadata and dependencies. The After= directive ensures Gitea starts only after network and database services are available.
The [Service] section specifies execution parameters. Running as the git user maintains security isolation. The WorkingDirectory parameter sets the context for relative paths. The Restart=always policy automatically recovers from crashes.
Environment variables configure Gitea’s runtime environment. The GITEA_WORK_DIR variable tells Gitea where to find data and configuration files.
Enabling and Starting Service
Reload systemd to recognize the new service file:
sudo systemctl daemon-reloadEnable the Gitea service to start automatically at boot:
sudo systemctl enable giteaStart the Gitea service immediately:
sudo systemctl start giteaCheck the service status to confirm it’s running:
sudo systemctl status giteaThe output should display “active (running)” in green. If the service fails to start, examine the logs for error messages.
Step 7: Configure Firewall
Fedora 43 includes firewalld, a dynamic firewall management tool. Check the firewall status:
sudo firewall-cmd --stateOpen port 3000 to allow access to the Gitea web interface:
sudo firewall-cmd --permanent --add-port=3000/tcpThe --permanent flag makes the rule persistent across reboots.
Reload the firewall to apply changes:
sudo firewall-cmd --reloadVerify the port was added successfully:
sudo firewall-cmd --list-portsThe output should include “3000/tcp” among the open ports.
If you plan to use SSH for Git operations on a non-standard port, open that port similarly. For HTTPS access through a reverse proxy, open port 443.
SELinux Considerations
Fedora 43 runs SELinux in enforcing mode by default. SELinux may block Gitea from binding to ports or accessing files. If you encounter permission denied errors, temporarily set SELinux to permissive mode for troubleshooting:
sudo setenforce 0Check if this resolves the issue. If so, create appropriate SELinux policies rather than disabling SELinux permanently.
Step 8: Initial Gitea Configuration via Web Interface
Accessing Web Installer
Open a web browser and navigate to your server’s IP address on port 3000:
http://your-server-ip:3000Replace “your-server-ip” with your actual server IP address. The Gitea installation wizard appears, presenting configuration options.
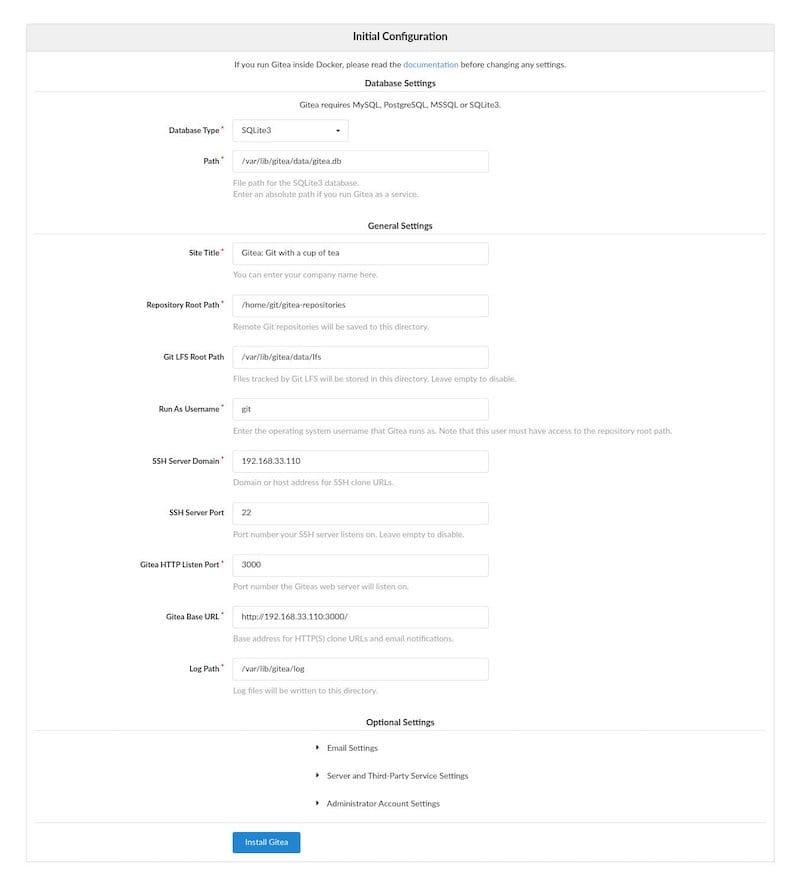
Database Configuration
Select “MySQL” as the database type since MariaDB uses MySQL protocol. Enter the following connection settings:
- Host: 127.0.0.1:3306
- Username: gitea
- Password: Your_Secure_Password_Here
- Database Name: gitea
Use the same password you created during the MariaDB setup. Click “Test Connection” if available to verify the database configuration before proceeding.
General Settings
Configure the basic application settings:
- Site Title: Choose a descriptive name for your Gitea instance
- Repository Root Path:
/home/git/gitea-repositories - Git LFS Root Path:
/var/lib/gitea/data/lfs - Run As Username: git
The repository root path stores all Git repositories. Ensure this location has sufficient disk space for your anticipated repository sizes.
Server and URL Settings
Configure network and access parameters:
- SSH Server Domain: your-domain.com or your server IP
- SSH Server Port: 22
- Gitea HTTP Listen Port: 3000
- Gitea Base URL:
http://your-server-ip:3000/
The base URL tells Gitea how users access the service. Update this later if you configure a domain name or reverse proxy.
Optional Service Settings
Review additional configuration options:
- Email Settings: Configure SMTP if you want Gitea to send notification emails
- Server and Third-Party Service Settings: Enable or disable various features
- Administrator Account Settings: Create the initial admin user
Administrator Account
Create the first administrator account with these fields:
- Administrator Username: Choose a secure username
- Password: Use a strong, unique password
- Email Address: Provide a valid email address
This account has full administrative privileges over the Gitea instance. Store the credentials securely.
Completing Installation
Review all settings carefully, then click “Install Gitea” at the bottom of the page. The installation process creates the configuration file and initializes the database schema. After a few seconds, Gitea redirects you to the login page.
Step 9: Post-Installation Configuration
Securing Configuration File
After the web installation completes, secure the configuration directory to prevent unauthorized modifications. Change the directory permissions:
sudo chmod 750 /etc/giteaSecure the configuration file specifically:
sudo chmod 640 /etc/gitea/app.iniThese restricted permissions prevent the web interface from modifying settings after installation, protecting against potential security vulnerabilities.
Essential Configuration Adjustments
Edit the Gitea configuration file to customize settings:
sudo nano /etc/gitea/app.iniReview and modify key settings:
[server]
DOMAIN = your-domain.com
ROOT_URL = http://your-domain.com:3000/
DISABLE_SSH = false
SSH_PORT = 22
[service]
DISABLE_REGISTRATION = true
REQUIRE_SIGNIN_VIEW = false
[security]
INSTALL_LOCK = trueThe DISABLE_REGISTRATION setting prevents anonymous users from creating accounts. Set this to true for private instances where you’ll manually create user accounts.
Performance Optimizations
Adjust database and cache settings for better performance:
[database]
MAX_IDLE_CONNS = 10
MAX_OPEN_CONNS = 100
[cache]
ENABLED = true
ADAPTER = memory
[indexer]
ISSUE_INDEXER_TYPE = bleve
REPO_INDEXER_ENABLED = trueThese settings optimize database connection pooling and enable content indexing for faster searches.
Restart Service
Apply configuration changes by restarting Gitea:
sudo systemctl restart giteaVerify the service started successfully:
sudo systemctl status giteaStep 10: Configure Nginx Reverse Proxy
Installing Nginx
A reverse proxy provides domain-based access, SSL termination, and additional security layers. Install Nginx on Fedora 43:
sudo dnf install nginx -yEnable Nginx to start at boot:
sudo systemctl enable nginxStart the Nginx service:
sudo systemctl start nginxCreating Nginx Configuration
Create a dedicated configuration file for Gitea:
sudo nano /etc/nginx/conf.d/gitea.confAdd the following reverse proxy configuration:
server {
listen 80;
server_name git.yourdomain.com;
client_max_body_size 512M;
location / {
proxy_pass http://127.0.0.1:3000;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_http_version 1.1;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection "upgrade";
}
}Replace “git.yourdomain.com” with your actual domain name. The client_max_body_size setting allows large file uploads.
Testing and Applying
Test the Nginx configuration syntax:
sudo nginx -tThe output should indicate the configuration is valid with no errors.
Reload Nginx to apply the new configuration:
sudo systemctl reload nginxOpen port 80 in the firewall:
sudo firewall-cmd --permanent --add-port=80/tcp
sudo firewall-cmd --reloadUpdate the Gitea configuration to reflect the new URL:
sudo nano /etc/gitea/app.iniModify the ROOT_URL:
[server]
ROOT_URL = http://git.yourdomain.com/Restart Gitea:
sudo systemctl restart giteaAccess Gitea through your domain name to verify the reverse proxy works correctly.
Step 11: Enable HTTPS with SSL/TLS
Obtaining SSL Certificate
Secure your Gitea instance with HTTPS using Let’s Encrypt certificates. Install Certbot with the Nginx plugin:
sudo dnf install certbot python3-certbot-nginx -yObtain and install an SSL certificate automatically:
sudo certbot --nginx -d git.yourdomain.comCertbot prompts for an email address for renewal notifications. Agree to the terms of service. Choose whether to redirect HTTP traffic to HTTPS (recommended).
The tool automatically modifies your Nginx configuration to enable HTTPS, configures certificate paths, and sets up automatic renewal.
Updating Gitea Configuration
Modify the Gitea configuration to use HTTPS:
sudo nano /etc/gitea/app.iniUpdate the protocol and URL:
[server]
PROTOCOL = https
ROOT_URL = https://git.yourdomain.com/Restart the Gitea service:
sudo systemctl restart giteaTesting SSL Configuration
Access Gitea using the HTTPS URL in your browser. Verify the padlock icon appears in the address bar, indicating a secure connection. Click the padlock to view certificate details and confirm it was issued by Let’s Encrypt.
Test HTTP to HTTPS redirect by accessing the HTTP version of your URL. The browser should automatically redirect to HTTPS.
Testing Your Gitea Installation
Creating First Repository
Log into Gitea with your administrator credentials. Click the “+” icon in the upper right corner and select “New Repository.” Enter a repository name and description. Choose whether the repository should be public or private. Initialize the repository with a README file for convenience.
Click “Create Repository” to complete the process. Gitea displays the new repository page with clone URLs and instructions.
Testing Git Operations
Test repository operations from your local machine. Clone the repository via HTTPS:
git clone https://git.yourdomain.com/username/repository.gitEnter your Gitea username and password when prompted. Navigate into the cloned directory, make changes to a file, commit the changes, and push them back to Gitea:
cd repository
echo "Test content" >> test.txt
git add test.txt
git commit -m "Add test file"
git push origin mainRefresh the Gitea web interface to verify your changes appear in the repository.
Testing Core Features
Create an issue by clicking the “Issues” tab and selecting “New Issue.” Enter a title and description, then submit. Test the pull request workflow by creating a new branch, making changes, and opening a pull request through the web interface.
Add a collaborator by navigating to repository settings and clicking “Collaborators.” Enter a username and select their permission level. Test the wiki functionality by clicking the “Wiki” tab and creating a new page.
Performance Verification
Monitor system resources during operation:
htopGitea should consume minimal resources during idle periods, typically under 100MB of RAM. Check the service logs for errors or warnings:
sudo journalctl -u gitea -fThe logs display startup messages, web requests, and any error conditions. Healthy operation shows successful request handling with 200 status codes.
Common Issues and Troubleshooting
Service Won’t Start
If Gitea fails to start, examine the logs for detailed error messages:
sudo journalctl -u gitea -xeCommon causes include incorrect file permissions, database connection failures, or port conflicts. Verify the git user owns all required directories:
ls -la /var/lib/gitea/Ensure MariaDB is running:
sudo systemctl status mariadbCan’t Access Web Interface
Verify the Gitea service is running and listening on the correct port:
sudo netstat -tlnp | grep 3000The output should show Gitea listening on 0.0.0.0:3000 or 127.0.0.1:3000. Check firewall rules to confirm port 3000 is open:
sudo firewall-cmd --list-portsSELinux may block network access. Check for denial messages:
sudo ausearch -c gitea --rawDatabase Connection Errors
Test database connectivity manually:
mysql -u gitea -p -h 127.0.0.1 giteaEnter the Gitea database password. If connection fails, verify the credentials in /etc/gitea/app.ini match those configured in MariaDB. Ensure MariaDB is accepting local connections.
SSH Clone Not Working
Configure SSH access by adding your public key to your Gitea profile. Navigate to “Settings” → “SSH / GPG Keys” → “Add Key.” Paste your public SSH key and save.
Verify the SSH port is open in the firewall:
sudo firewall-cmd --list-portsCheck the authorized_keys file permissions:
ls -la /home/git/.ssh/Slow Performance
Enable caching in the configuration file:
[cache]
ENABLED = true
ADAPTER = memoryIncrease the database connection pool:
[database]
MAX_IDLE_CONNS = 25
MAX_OPEN_CONNS = 150Monitor disk I/O with iostat to identify bottlenecks. Enable the repository indexer for faster searches.
Security Best Practices
Disable self-registration to prevent unauthorized account creation:
[service]
DISABLE_REGISTRATION = trueEnable two-factor authentication for administrator accounts through the user settings page. Implement a regular backup strategy covering database dumps, repository data, and configuration files.
Keep Gitea updated by periodically checking for new releases and following the upgrade procedure. Use strong passwords for all accounts and enforce password policies through the configuration file.
Consider implementing fail2ban to protect against brute-force login attempts. Create a filter for Gitea login failures and configure automatic IP blocking after repeated failures.
Configure rate limiting to prevent abuse:
[service]
ENABLE_RATE_LIMIT = true
RATE_LIMIT_REQUESTS = 100
RATE_LIMIT_PERIOD = 1mMonitor access logs regularly for suspicious activity. Review active sessions and revoke any unrecognized connections.
Maintenance and Backup
Regular Maintenance Tasks
Check for Gitea updates monthly by visiting the releases page. Download the new binary, stop the service, replace the binary, and restart:
sudo systemctl stop gitea
sudo wget -O /usr/local/bin/gitea https://dl.gitea.io/gitea/1.23/gitea-1.23-linux-amd64
sudo chmod +x /usr/local/bin/gitea
sudo systemctl start giteaOptimize the database quarterly:
mysqlcheck -o gitea -u root -pConfigure log rotation to prevent logs from consuming excessive disk space. Clean up old data and archives periodically.
Backup Procedures
Create database backups regularly:
mysqldump -u gitea -p gitea > gitea_backup_$(date +%Y%m%d).sqlBackup repository data:
sudo tar -czf gitea_repos_$(date +%Y%m%d).tar.gz /home/git/gitea-repositoriesBackup the configuration file:
sudo cp /etc/gitea/app.ini /backup/gitea_config_$(date +%Y%m%d).iniAutomate backups with a cron job that runs nightly:
sudo crontab -eAdd a backup script entry:
0 2 * * * /usr/local/bin/backup-gitea.shTest restore procedures regularly to ensure backups work correctly when needed.
Congratulations! You have successfully installed Gitea. Thanks for using this tutorial for installing Gitea self-hostable web service for managing Git repositories on your Fedora 43 Linux system. For additional or useful information, we recommend you check the official Gitea website.