How To Install GlassFish on Debian 13

GlassFish stands as one of the most robust open-source application servers for deploying Java-based web applications and enterprise services. This powerful platform supports Jakarta EE (formerly Java EE) specifications, making it an ideal choice for hosting enterprise-scale applications, RESTful APIs, and microservices architectures. Whether you’re a seasoned system administrator or a developer looking to deploy Java applications, understanding how to properly install and configure GlassFish on Debian 13 is essential for creating a stable production environment.
This comprehensive guide walks you through every step of the GlassFish installation process on Debian 13. You’ll learn how to set up the necessary prerequisites, download and configure the application server, secure the admin console, and implement best practices for production deployments. By the end of this tutorial, you’ll have a fully functional GlassFish server ready to host your Java applications with confidence.
Prerequisites
Before diving into the GlassFish installation process, ensure your Debian 13 system meets the following requirements. A fresh installation of Debian 13 is recommended to avoid potential conflicts with existing software packages. You’ll need root or sudo privileges to execute system-level commands throughout this tutorial.
Your server should have at least 2GB of RAM for basic operations, though 4GB or more is recommended for production environments. Adequate disk space is crucial—allocate at least 1GB for the GlassFish installation itself, plus additional space for your applications and log files. A stable internet connection is necessary for downloading packages and the GlassFish server archive.
SSH access to your server is essential for remote administration. Basic familiarity with Linux command-line operations will help you navigate through the installation steps more efficiently. If you plan to make your GlassFish server publicly accessible, having a domain name pointed to your server’s IP address is beneficial, though not strictly required for initial setup and testing.
Understanding basic firewall configuration concepts will help you properly secure your installation. The ability to use text editors like vi, vim, or nano is also important for editing configuration files throughout this process.
Step 1: Update Debian 13 System
Keeping your Debian 13 system up-to-date is a critical first step before installing any new software. This ensures you have the latest security patches and dependency packages available. System updates prevent compatibility issues and reduce potential vulnerabilities in your server environment.
Open your terminal and execute the following command to update the package index:
sudo apt updateThis command refreshes your system’s package database, pulling the latest information about available packages from Debian repositories. Next, upgrade all installed packages to their newest versions:
sudo apt upgrade -yThe -y flag automatically confirms the upgrade process without requiring manual intervention. This step may take several minutes depending on how many packages need updating and your internet connection speed. Once completed, your system is ready for the GlassFish installation process with all dependencies current and secure.
Step 2: Install Java on Debian 13
GlassFish is a Java-based application server, making Java installation an absolute prerequisite. The server requires Java Development Kit (JDK) version 8 or higher to function properly. GlassFish 7.x, the latest version, works optimally with Java 11 or Java 17, providing enhanced performance and security features.
Install the default OpenJDK package using the following command:
sudo apt install default-jdk -yThis command installs the Java Development Kit along with all necessary runtime dependencies. The installation process typically takes a few minutes as it downloads and configures multiple Java-related packages. The default-jdk package provides a complete Java development environment suitable for running GlassFish server.
After installation completes, verify that Java is properly installed by checking the version:
java --versionYou should see output displaying the OpenJDK version number, build information, and JVM details. The version information confirms that Java is correctly installed and accessible from your command line. This verification step is crucial before proceeding with the GlassFish download.
If you need a specific Java version for compatibility reasons, you can install targeted versions like openjdk-11-jdk or openjdk-17-jdk. Setting the JAVA_HOME environment variable may be necessary for some configurations, though it’s typically not required for basic GlassFish installations on Debian systems.
Step 3: Download GlassFish on Debian 13
GlassFish is not available in the default Debian package repositories, requiring manual download from the official Eclipse Foundation website. This approach ensures you always get the latest stable version with all current features and security updates. The recommended installation location is the /opt directory, which Linux systems reserve for third-party software packages.
Navigate to the /opt directory where you’ll download and extract GlassFish:
cd /optDownload the latest GlassFish 7.x release using wget:
sudo wget https://download.eclipse.org/ee4j/glassfish/glassfish-7.0.24.zipThis command downloads the GlassFish ZIP archive directly to your current directory. The file size is approximately 120-150MB, so download time varies based on your internet connection speed. Always verify you’re downloading from the official Eclipse GlassFish repository to ensure authenticity and security.
Before extracting the archive, ensure the unzip utility is installed:
sudo apt install unzip -yExtract the downloaded GlassFish archive:
sudo unzip glassfish-7.0.24.zipThe extraction process creates a glassfish7 directory containing all necessary server files, including the bin directory with administrative tools, the glassfish directory with domains and configurations, and various supporting libraries. This directory structure organizes all GlassFish components logically for easy management.
Verify the extraction by listing the directory contents:
ls -la /opt/glassfish7/You should see directories like bin, glassfish, mq, and various configuration files. The bin directory contains the asadmin utility, which you’ll use extensively for server management. Understanding this directory structure helps when troubleshooting issues or customizing your installation.
Step 4: Create GlassFish Systemd Service File
Creating a systemd service file allows you to manage GlassFish like any other system service on Debian 13. This integration enables automatic startup on system boot, simplified service management, and consistent server operations. Systemd provides robust process management and logging capabilities that enhance server reliability.
Create a new systemd service file using your preferred text editor:
sudo nano /etc/systemd/system/glassfish.serviceAdd the following configuration to the file:
[Unit]
Description=GlassFish Server v7.0
After=syslog.target network.target
[Service]
ExecStart=/opt/glassfish7/bin/asadmin start-domain
ExecReload=/opt/glassfish7/bin/asadmin restart-domain
ExecStop=/opt/glassfish7/bin/asadmin stop-domain
Type=forking
[Install]
WantedBy=multi-user.targetLet’s break down each section of this configuration. The [Unit] section defines service metadata and dependencies. The Description provides a human-readable name for the service. The After directive ensures GlassFish starts only after the system logging and network services are available, preventing startup failures.
The [Service] section contains the actual service commands. ExecStart specifies the command to start the GlassFish domain. ExecReload allows graceful restarts without stopping the service entirely. ExecStop defines how to properly shut down the server. The Type=forking setting tells systemd that GlassFish spawns child processes and continues running in the background.
The [Install] section determines when the service should start. WantedBy=multi-user.target ensures GlassFish starts in normal multi-user system mode. This configuration creates a production-ready service that integrates seamlessly with Debian’s system management.
Save and close the file. If using nano, press Ctrl+X, then Y, and Enter to confirm. Your GlassFish service file is now ready for activation.
Step 5: Start and Enable GlassFish Service
With the systemd service file created, you can now start managing GlassFish through standard systemd commands. This approach provides consistent service management across your entire Debian system. First, reload the systemd daemon to recognize your new service file:
sudo systemctl daemon-reloadThis command refreshes systemd’s configuration, making it aware of the newly created GlassFish service. Now start the GlassFish service:
sudo systemctl start glassfishThe start command initializes the GlassFish domain and launches all associated processes. This typically takes 10-30 seconds depending on your system resources. Enable GlassFish to start automatically on system boot:
sudo systemctl enable glassfishEnabling the service creates the necessary symbolic links in systemd’s configuration directories, ensuring GlassFish launches whenever your server restarts. This is crucial for production environments where automatic recovery from system reboots is essential.
Check the service status to verify successful startup:
sudo systemctl status glassfishYou should see output indicating the service is “active (running)” with a green status indicator. The output displays recent log entries showing domain startup messages. If the status shows “failed” or “inactive,” review the error messages for troubleshooting clues.
GlassFish runs on two primary ports by default. Port 4848 serves the administrative console, while port 8080 handles HTTP application requests. Port 8181 is available for HTTPS traffic when SSL is configured. Understanding these ports is essential for firewall configuration and troubleshooting connectivity issues.
You can manage the GlassFish service using standard systemctl commands: sudo systemctl start glassfish, sudo systemctl stop glassfish, sudo systemctl restart glassfish, and sudo systemctl reload glassfish. These commands provide complete control over your server’s lifecycle.
Step 6: Configure Firewall for GlassFish
Proper firewall configuration is essential for both security and accessibility of your GlassFish server. Debian 13 typically uses UFW (Uncomplicated Firewall) as its front-end for iptables management. Opening only necessary ports reduces your attack surface while maintaining required functionality.
Allow HTTP traffic on port 8080 for application access:
sudo ufw allow 8080/tcpThis port serves your deployed Java applications to end users. If you plan to use HTTPS with SSL certificates, also open port 8181:
sudo ufw allow 8181/tcpThe admin console port (4848) requires special consideration. For security best practices, you should restrict admin console access to localhost or specific IP addresses rather than opening it to the public internet. However, for initial setup and testing, you may temporarily allow it:
sudo ufw allow 4848/tcpAfter initial configuration, consider restricting this port using IP-specific rules or SSH tunneling for remote access. If you’re configuring Nginx as a reverse proxy, also allow standard web ports:
sudo ufw allow 80/tcp
sudo ufw allow 443/tcpReload the firewall to apply new rules:
sudo ufw reloadVerify your firewall rules are correctly configured:
sudo ufw statusThe output displays all active firewall rules and their current status. This verification step ensures your GlassFish server is both accessible and protected. For production environments, implement additional security measures like fail2ban for brute-force protection and regular security audits.
Step 7: Access GlassFish Admin Console
The GlassFish Administration Console provides a powerful web-based interface for managing your application server. This graphical interface simplifies domain management, application deployment, resource configuration, and performance monitoring. Understanding how to access and navigate the admin console is fundamental to effective GlassFish administration.
Access the default GlassFish application page by opening your web browser and navigating to:
http://your-server-IP:8080Replace your-server-IP with your actual server’s IP address. You should see the GlassFish welcome page, confirming that the server is running and accepting connections. This page indicates your basic installation is successful and the HTTP listener is functioning properly.
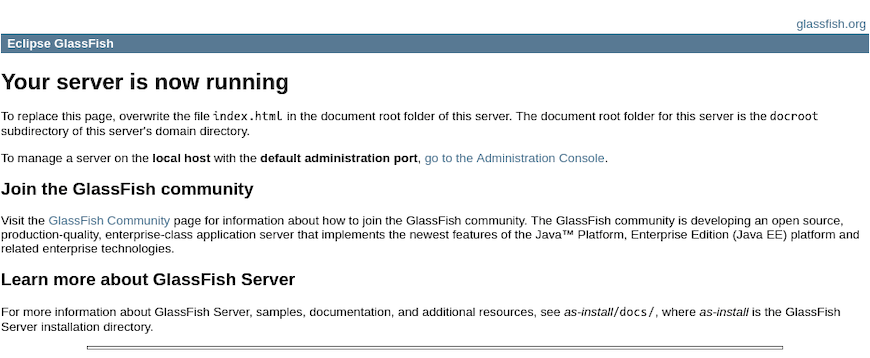
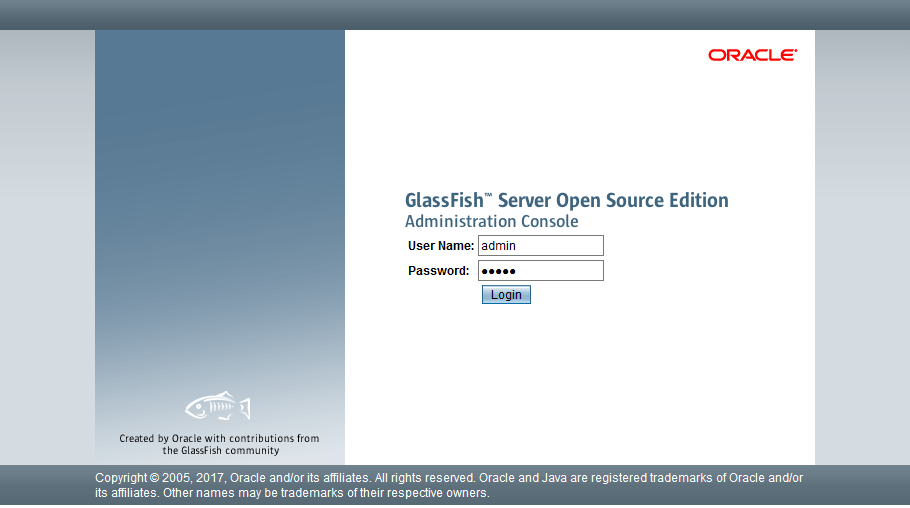
Access the administration console by navigating to:
http://your-server-IP:4848The admin console login screen appears, requesting credentials. By default, GlassFish uses “admin” as the username with a blank password. This default configuration is insecure and must be changed before deploying to production environments.
For remote administration from your local machine, SSH tunneling provides secure access without exposing the admin console to the internet. Create an SSH tunnel using this command from your local terminal:
ssh -L 4848:localhost:4848 user@your-server-IPThis command forwards your local port 4848 to the remote server’s localhost port 4848 through an encrypted SSH connection. Once the tunnel is established, access the admin console by navigating to http://localhost:4848 in your local browser. This method ensures admin traffic remains encrypted and protected from potential attackers.
The admin console interface organizes features into logical sections: Common Tasks for frequent operations, Domain for server-wide settings, Applications for deployment management, Resources for JDBC and JMS configuration, Configurations for detailed server settings, and Monitoring for performance tracking. Familiarizing yourself with this layout improves administrative efficiency.
Step 8: Secure GlassFish Admin Console
Default security settings make GlassFish vulnerable to unauthorized access. Implementing proper security measures is non-negotiable before deploying applications or exposing your server to network traffic. The first and most critical step is changing the default admin password.
Make the asadmin utility available in your PATH:
sudo export PATH=/opt/glassfish7/bin:$PATHThis command temporarily adds the GlassFish bin directory to your system PATH, allowing direct execution of asadmin commands. For permanent access, add this export command to your ~/.bashrc or ~/.bash_profile file.
Change the admin password using asadmin:
sudo asadmin --port 4848 change-admin-passwordThe command prompts you to enter the current password (press Enter for blank default) and then your new password twice for confirmation. Choose a strong password combining uppercase and lowercase letters, numbers, and special characters. Strong passwords are at least 12 characters long and avoid dictionary words or predictable patterns.
Enable secure admin to require authentication for all administrative operations:
sudo asadmin --port 4848 enable-secure-adminYou’ll be prompted to enter the admin username and your newly set password. Secure admin enforces HTTPS for admin console access and requires authentication for asadmin commands. This feature significantly enhances security by preventing anonymous administrative access.
Restart GlassFish to apply security changes:
sudo systemctl restart glassfishAfter restart, the admin console requires HTTPS access. Navigate to https://your-server-IP:4848 (note the https protocol). Your browser may display a security warning about the self-signed certificate. For production environments, replace the self-signed certificate with a properly signed certificate from a trusted Certificate Authority.
Additional security hardening includes changing default ports to non-standard values, restricting admin console access by IP address, implementing network segmentation, regularly updating GlassFish to patch security vulnerabilities, and reviewing access logs for suspicious activity. These measures create defense-in-depth protecting your application server from various attack vectors.
Step 9: Verify GlassFish Installation
Thorough verification ensures your GlassFish installation is functioning correctly before deploying applications. Testing multiple aspects of the server confirms all components are properly configured and communicating. Start by accessing the default application page at http://your-server-IP:8080 to verify HTTP listener functionality.
Check the admin console accessibility at https://your-server-IP:4848 and log in with your admin credentials. Successful login confirms authentication is working correctly. Navigate through various admin console sections to verify the interface loads properly without errors.
Verify domain status using asadmin commands:
sudo /opt/glassfish7/bin/asadmin list-domainsThis command displays all configured domains and their current status. The default domain domain1 should show as “running.” Check detailed domain information:
sudo /opt/glassfish7/bin/asadmin --port 4848 list-applicationsThis lists all deployed applications. A fresh installation shows no applications deployed, which is expected. Review GlassFish server logs for any errors or warnings:
sudo tail -f /opt/glassfish7/glassfish/domains/domain1/logs/server.logThe log file contains detailed information about server operations, startup sequences, and any errors encountered. Press Ctrl+C to exit the log viewer. Look for any ERROR or WARNING messages that might indicate configuration issues.
Test basic application deployment by deploying a sample WAR file if available. Monitor resource usage using system tools:
sudo systemctl status glassfishThis shows memory usage, CPU consumption, and process information. Verify that Java processes are running and consuming reasonable resources for your server’s specifications.
Optional: Configure Nginx as Reverse Proxy
Using Nginx as a reverse proxy in front of GlassFish provides numerous benefits including load balancing, SSL termination, enhanced security, improved caching, and the ability to serve applications on standard ports 80 and 443. This configuration is highly recommended for production deployments.
Install Nginx on Debian 13:
sudo apt install nginx -yThe installation configures Nginx to start automatically and begins listening on port 80. Create a new Nginx configuration file for GlassFish:
sudo nano /etc/nginx/conf.d/glassfish.confAdd the following reverse proxy configuration:
upstream glassfish {
server 127.0.0.1:8080 weight=100 max_fails=5 fail_timeout=5;
}
server {
listen 80;
server_name your-domain.com;
location / {
proxy_pass http://glassfish;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
}
}Replace your-domain.com with your actual domain name. This configuration creates an upstream block defining the GlassFish backend server and a server block handling incoming HTTP requests. The proxy headers preserve client information for GlassFish applications to access.
Test the Nginx configuration for syntax errors:
sudo nginx -tSuccessful output indicates your configuration is valid. Restart Nginx to apply changes:
sudo systemctl restart nginxVerify Nginx is running:
sudo systemctl status nginxNow access your GlassFish applications using your domain name on port 80: http://your-domain.com. Nginx receives the request and forwards it to GlassFish on port 8080, returning the response to the client. This architecture hides the application server from direct internet exposure.
For SSL/TLS encryption, install Certbot and obtain Let’s Encrypt certificates:
sudo apt install certbot python3-certbot-nginx -y
sudo certbot --nginx -d your-domain.comCertbot automatically configures Nginx for HTTPS and sets up automatic certificate renewal. This provides free, trusted SSL certificates for secure client connections.
Common GlassFish Commands
Mastering essential asadmin commands streamlines daily GlassFish administration tasks. These commands provide powerful control over server operations, application management, and configuration adjustments. Always execute these commands from the GlassFish bin directory or ensure it’s in your system PATH.
Start the default domain:
sudo asadmin start-domain domain1Stop the default domain:
sudo asadmin stop-domain domain1Restart the domain:
sudo asadmin restart-domain domain1List all domains and their status:
sudo asadmin list-domainsDeploy an application:
sudo asadmin deploy /path/to/application.warUndeploy an application:
sudo asadmin undeploy application-nameList all deployed applications:
sudo asadmin list-applicationsView server logs in real-time:
sudo asadmin view-log --followGenerate JVM report for troubleshooting:
sudo asadmin generate-jvm-reportCreate a new domain:
sudo asadmin create-domain --portbase 5000 newdomainThese commands form the foundation of effective GlassFish server management. Combining them with systemd service commands provides comprehensive control over your application server environment.
Troubleshooting Common Issues
Even with careful installation, you may encounter issues requiring troubleshooting. Understanding common problems and their solutions minimizes downtime and frustration. Port conflicts are among the most frequent issues, occurring when another process occupies GlassFish’s default ports.
If GlassFish fails to start due to port conflicts, identify the conflicting process:
sudo netstat -tulpn | grep :8080Either stop the conflicting service or configure GlassFish to use alternative ports through domain configuration.
Admin console loading issues often stem from browser cache problems or certificate issues with secure admin. Clear your browser cache, try a different browser, or access via incognito mode. For HTTPS certificate warnings, either accept the self-signed certificate temporarily or install a proper certificate.
Service startup failures require log examination:
sudo journalctl -u glassfish -n 50This displays the last 50 lines of GlassFish service logs, revealing startup errors or configuration problems. Common causes include incorrect Java paths in service files, insufficient permissions, or corrupted domain configurations.
Java version compatibility issues arise when applications require specific Java versions. Verify your Java version matches GlassFish requirements. Install multiple Java versions if needed and configure GlassFish to use the appropriate one through JAVA_HOME settings.
Memory and JVM configuration problems manifest as OutOfMemoryError exceptions or performance degradation. Adjust JVM settings in domain.xml or through asadmin commands:
sudo asadmin create-jvm-options "-Xmx2048m"Permission-related errors occur when GlassFish files have incorrect ownership or permissions. Ensure the user running GlassFish has read, write, and execute permissions on the installation directory:
sudo chmod -R 755 /opt/glassfish7Firewall blocking connections prevents external access to GlassFish. Verify firewall rules allow traffic on necessary ports and check that your cloud provider’s security groups permit inbound connections if using cloud infrastructure.
Domain.xml configuration problems can corrupt your domain. GlassFish maintains backup copies of domain.xml. Restore from backup if corruption occurs:
sudo cp /opt/glassfish7/glassfish/domains/domain1/config/domain.xml.bak /opt/glassfish7/glassfish/domains/domain1/config/domain.xmlCongratulations! You have successfully installed GlassFish. Thanks for using this tutorial to install the latest version of GlassFish on Debian 13 “Trixie” system. For additional help or useful information, we recommend you check the official GlassFish website.