How To Install ISPConfig on Debian 13

ISPConfig is a powerful open-source hosting control panel that simplifies server management for system administrators and hosting providers. This comprehensive guide walks through the complete installation process of ISPConfig on Debian 13 (Trixie), covering everything from initial server preparation to post-installation configuration. Whether managing a single server or multiple hosting environments, ISPConfig provides an intuitive web-based interface for controlling web servers, email systems, DNS zones, FTP accounts, and databases.
Released in August 2025, Debian 13 “Trixie” represents the latest stable version of this renowned Linux distribution, bringing enhanced security features, updated packages, and improved hardware support. Installing ISPConfig on this cutting-edge platform ensures access to modern software stacks while maintaining the stability Debian is famous for.
This tutorial employs the automated installation method, which streamlines the setup process by automatically configuring Apache, MariaDB, Postfix, Dovecot, BIND, and PureFTPD. The entire installation typically completes within 30-60 minutes, depending on server specifications and internet connection speed.
What is ISPConfig?
ISPConfig serves as a comprehensive web-based hosting control panel designed for Linux servers running Apache or Nginx web servers. System administrators rely on this software to manage multiple websites, email accounts, DNS records, FTP users, and MySQL databases from a single unified interface.
The control panel features four distinct access levels: Administrator, Reseller, Client, and Email User. Administrators possess full system control. Resellers can create and manage client accounts. Clients manage their own websites and email addresses. Email users access only their mailbox settings.
Released under a BSD license, ISPConfig remains completely free and open-source. This makes it an attractive alternative to commercial control panels like cPanel or Plesk, especially for budget-conscious hosting providers and small businesses.
The software manages critical server components including web servers (Apache2 or Nginx), mail transfer agents (Postfix), IMAP/POP3 servers (Dovecot), DNS nameservers (BIND or PowerDNS), FTP servers (PureFTPD), and database systems (MariaDB or MySQL). Additional integrated services include Rspamd for spam filtering, ClamAV for virus scanning, and Redis for caching.
ISPConfig’s multi-server architecture supports distributed hosting environments where services span multiple physical or virtual servers. This scalability makes it suitable for both small single-server setups and large enterprise hosting infrastructures.
Prerequisites and System Requirements
Operating System Requirements
A fresh installation of Debian 13 (Trixie) provides the foundation for this setup. The server should run the x86_64 (AMD64) architecture, though Debian 13 now officially supports RISC-V 64-bit systems as well.
Avoid installing ISPConfig on systems with pre-configured web servers, mail servers, or DNS servers, as conflicts may arise during installation. A clean Debian 13 minimal installation ensures the smoothest setup experience.
Minimum Hardware Specifications
The server requires at least 2 CPU cores (vCores) to handle ISPConfig and its associated services efficiently. While ISPConfig can technically run on 1 GB of RAM, 2 GB represents the practical minimum for comfortable operation with all services enabled.
Storage demands vary based on usage, but start with at least 20 GB of free disk space. This accommodates the operating system, ISPConfig, all server software, and initial website/email data. Plan for additional storage based on anticipated hosting needs.
A stable internet connection is essential for downloading packages and updates throughout the installation process.
Access Requirements
Root access or sudo privileges are mandatory for installing and configuring system services. SSH access allows remote server management, though local console access works equally well.
Having a registered domain name with proper DNS configuration enhances functionality, especially for email services and SSL certificates. The server needs a fully qualified domain name (FQDN) configured before beginning installation.
What is Debian 13 (Trixie)?
Debian 13 “Trixie” launched in August 2025 as the project’s thirteenth major release. This version ships with Linux Kernel 6.12, providing enhanced hardware compatibility and performance improvements.
Desktop users benefit from updated environments including GNOME 48, KDE Plasma 6.3, XFCE 4.20, and LXQt 2.1. Server administrators appreciate the inclusion of modern server software packages and security enhancements.
One notable architectural change involves the /tmp directory, which now uses tmpfs by default for improved performance and security. The APT 3.0 package manager debuts in this release, offering faster package operations and improved dependency resolution.
Debian 13 introduces official support for RISC-V 64-bit architecture, expanding deployment options beyond traditional x86 and ARM systems. HTTP Boot support facilitates network-based installations in modern UEFI environments.
The distribution contains 69,830 packages maintained by the Debian community. Like all Debian stable releases, Trixie receives five years of full support, including security updates and critical bug fixes.
Preparing Your Debian 13 Server
Step 1: Configure Hostname
The server requires a properly configured fully qualified domain name (FQDN). Log into the server via SSH or console as root.
Edit the hostname file:
nano /etc/hostnameReplace the contents with your desired hostname, such as server1.example.com. Save and close the file.
Next, edit the hosts file:
nano /etc/hostsAdd or modify the entry to match this format:
127.0.0.1 localhost
YOUR_SERVER_IP server1.example.com server1Replace YOUR_SERVER_IP with the actual server IP address. Save and close the file.
Verify the configuration:
hostname
hostname -fThe first command displays the short hostname. The second shows the FQDN.
Step 2: Update System Packages
Before installing ISPConfig, update all system packages to their latest versions.
apt update
apt upgrade -yThis process may take several minutes depending on the number of updates available. If the kernel receives updates, reboot the server:
rebootWait for the server to restart, then reconnect via SSH.
Step 3: Synchronize System Clock
Accurate time synchronization prevents issues with SSL certificates and email delivery. Debian 13 uses systemd-timesyncd by default.
Check the current time status:
timedatectl statusIf necessary, set the correct timezone:
timedatectl set-timezone Asia/JakartaReplace Asia/Jakarta with your appropriate timezone. Verify synchronization is active by checking the status output shows “System clock synchronized: yes”.
Step 4: Install Required Dependencies
Install wget and essential utilities needed for the automated installer:
apt install wget curl gnupg2 ca-certificates lsb-release -yThese tools enable secure downloads and system detection during the installation process.
Understanding ISPConfig Installation Methods
ISPConfig offers two installation approaches: automated and manual. The automated installer script handles the entire setup process, downloading and configuring all necessary components without manual intervention.
This automated method installs and configures Apache2 (or Nginx as an alternative), multiple PHP versions, MariaDB database server, Postfix mail transfer agent, Dovecot IMAP/POP3 server, BIND DNS server, PureFTPD FTP server, and ISPConfig itself. The script also sets up Rspamd for spam filtering, ClamAV for antivirus protection, and configures firewall rules automatically.
Manual installation provides granular control over every configuration detail but requires extensive Linux system administration knowledge. This approach takes significantly longer and introduces more opportunities for configuration errors.
For most administrators, the automated installer represents the optimal choice, balancing ease of use with comprehensive functionality. The script incorporates best practices developed by the ISPConfig community over many years.
Installing ISPConfig on Debian 13 Using Automated Installer
Step 1: Download and Run the Autoinstaller
The installation command depends on the preferred web server. For Apache2, execute:
wget -O - https://get.ispconfig.org | sh -s -- --use-ftp-ports=40110-40210 --unattended-upgradesFor Nginx as the web server alternative, use:
wget -O - https://get.ispconfig.org | sh -s -- --use-nginx --use-ftp-ports=40110-40210 --unattended-upgradesThe --use-ftp-ports=40110-40210 parameter configures the passive FTP port range. This range must be open in the firewall for FTP to function correctly.
The --unattended-upgrades flag enables automatic security updates for the system. This maintains server security without manual intervention.
Step 2: Confirm Installation Warning
The installer displays a warning message explaining that it will install and reconfigure multiple system services. This warning emphasizes the importance of running the installer on a fresh system without existing service configurations.
Type yes and press Enter to proceed with the installation. Typing anything else aborts the process.
Step 3: Monitor Installation Progress
The automated installer progresses through multiple stages. Initial phases update package repositories and install required dependencies. Subsequent stages install and configure each service component.
Watch for any error messages during installation, though the script handles most situations automatically. The entire process typically completes in 30-60 minutes, varying based on server performance and internet speed.
The installer configures the web server with virtual host templates, sets up the mail server with proper authentication mechanisms, initializes the DNS server with default zones, configures the FTP server with secure settings, and creates the ISPConfig database schema.
Step 4: Save Important Credentials
Near the end of the installation, the script displays critical information. Record the following credentials immediately:
- ISPConfig admin password
- MySQL root password
- Database information
Copy these credentials to a secure password manager or encrypted file. Losing the admin password requires database manipulation to reset.
The installer also displays the ISPConfig access URL, typically https://your-server-ip:8080 or https://your-hostname:8080.
Post-Installation Configuration
Verifying Services Status
After installation completes, verify all services are running correctly. Check MariaDB status:
systemctl status mariadbVerify the web server (Apache or Nginx):
systemctl status apache2
# OR
systemctl status nginxConfirm Postfix mail server operation:
systemctl status postfixCheck Dovecot IMAP/POP3 service:
systemctl status dovecotVerify BIND DNS server:
systemctl status bind9Confirm PureFTPD status:
systemctl status pure-ftpd-mysqlCheck additional services including Rspamd (spam filter), ClamAV (antivirus), and Redis (cache):
systemctl status rspamd
systemctl status clamav-daemon
systemctl status redis-serverAll services should display “active (running)” status. If any service shows errors, review the installation logs.
Cleaning Temporary Files
The installer creates temporary log files during setup. Remove these to free disk space:
rm -rf /tmp/ispconfig-ai/var/log/setup-*This cleanup step is optional but recommended for maintaining a tidy server environment.
Accessing the ISPConfig Control Panel
Open a web browser and navigate to the ISPConfig control panel using the URL provided during installation. The standard format is:
https://your-server-hostname:8080Replace your-server-hostname with the actual server hostname or IP address. Some configurations use port 8081 instead.
The browser displays a security warning about an untrusted SSL certificate. This occurs because ISPConfig initially uses a self-signed certificate. Click “Advanced” or “Proceed Anyway” to continue to the login page.
Enter admin as the username. Use the password displayed during installation. Click the login button to access the ISPConfig dashboard.
The dashboard presents an overview of system status, server resources, and quick access links to common tasks. The left sidebar contains the main navigation menu with sections for Sites, DNS, Mail, Clients, Tools, Monitor, Help, and System.
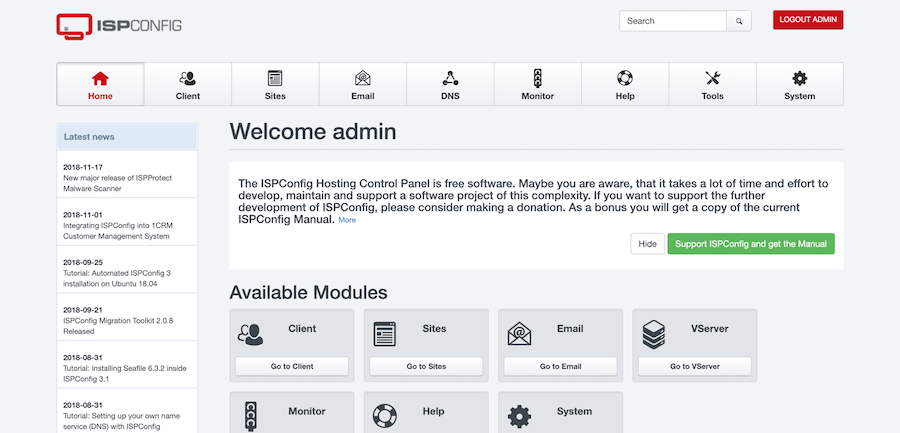
Changing Default ISPConfig Admin Password
Security best practices mandate changing the default administrator password immediately after first login. Navigate to Tools → User Settings in the ISPConfig interface.
Click the “Generate Password” button to create a strong random password. Alternatively, enter a custom password meeting complexity requirements (minimum length, mixed case, numbers, special characters).
Enter the new password twice to confirm. Click “Save” to update the credentials.
Store the new password securely in a password manager. Avoid writing passwords on paper or storing them in plain text files.
Configuring Firewall Rules
The automated installer configures UFW (Uncomplicated Firewall) with necessary rules for ISPConfig operation. Essential ports are automatically opened:
- Port 21: FTP
- Port 22: SSH
- Port 25: SMTP (email sending)
- Port 80: HTTP (web traffic)
- Port 443: HTTPS (secure web traffic)
- Port 110: POP3 (email retrieval)
- Port 143: IMAP (email access)
- Port 465: SMTPS (secure SMTP)
- Port 587: Submission (email submission)
- Port 993: IMAPS (secure IMAP)
- Port 995: POP3S (secure POP3)
- Port 53: DNS queries (TCP/UDP)
- Port 8080: ISPConfig control panel
- Port 8081: ISPConfig alternative port
- Ports 40110-40210: FTP passive mode range
Verify firewall status:
ufw status verboseAdditional firewall rules can be managed through the ISPConfig interface. Navigate to System → Firewall to add custom rules. This provides a graphical interface for managing iptables rules without direct command-line manipulation.
Understanding ISPConfig Services and Components
Web Server Management
ISPConfig supports both Apache2 and Nginx web servers. Apache offers broader compatibility with legacy applications, while Nginx excels at serving static content and handling high concurrent connections.
The control panel manages multiple PHP versions simultaneously, allowing different websites to use PHP 7.4, 8.0, 8.1, or 8.2 as needed. This flexibility accommodates diverse application requirements on a single server.
Virtual host configuration occurs through the Sites section, where administrators define website settings, SSL certificates, PHP options, and directory security. ISPConfig generates appropriate Apache or Nginx configuration files automatically.
Let’s Encrypt integration enables free SSL certificate generation and automatic renewal. This simplifies HTTPS implementation for all hosted domains.
Mail Server Components
Postfix serves as the mail transfer agent (MTA), handling email sending and receiving. ISPConfig configures Postfix with proper authentication, spam filtering, and virus scanning integration.
Dovecot provides IMAP and POP3 services for email retrieval. Users access mailboxes through email clients like Outlook, Thunderbird, or mobile applications.
Rspamd analyzes incoming email for spam characteristics, assigning spam scores and filtering unwanted messages. Administrators adjust spam sensitivity through ISPConfig settings.
ClamAV scans all email attachments for viruses and malware. Infected messages are quarantined or rejected based on policy settings.
Database Management
MariaDB (a MySQL fork) provides database services for websites and applications. ISPConfig creates and manages database users, assigns privileges, and monitors database sizes.
PHPMyAdmin integration offers a web-based interface for direct database administration. Advanced users can execute SQL queries, import/export data, and manage database structures.
Database quotas prevent individual clients from consuming excessive storage. Administrators set limits per client or database.
DNS Server
BIND nameserver management enables hosting authoritative DNS zones for client domains. ISPConfig simplifies DNS record creation with forms for A, AAAA, MX, CNAME, TXT, SRV, and other record types.
PowerDNS serves as an alternative DNS server option. This provides better performance for very high query volumes.
Zone templates accelerate new domain setup by providing pre-configured record sets. Administrators create templates matching common hosting scenarios.
FTP Server
PureFTPD handles file transfer services with support for FTP, FTPS (FTP over SSL), and SFTP protocols. Each FTP account corresponds to a specific website or client.
ISPConfig manages FTP user credentials, home directories, and access permissions. Quotas limit storage consumption per FTP account.
The passive port range (40110-40210) configured during installation enables FTP operation through firewalls and NAT routers.
ISPConfig Dashboard Overview
The main dashboard displays system health indicators including CPU usage, memory consumption, disk space utilization, and network statistics. Real-time monitoring helps identify performance issues before they affect users.
Quick access widgets provide shortcuts to frequently used functions like creating websites, adding email addresses, and managing DNS records. Customizable dashboard layouts adapt to individual administrator workflows.
The navigation sidebar organizes functions into logical categories. Sites manages websites and FTP. DNS controls nameserver zones. Mail handles email domains and mailboxes. Clients manages customer accounts. Tools provides utilities and settings. Monitor displays service status and logs. System contains server configuration.
Multi-server installations display a server selector, allowing administrators to manage services across multiple physical servers from a single interface. This centralized management simplifies large hosting environments.
Basic ISPConfig Configuration Tasks
Creating the first website begins in Sites → Website. Click “Add new website” and complete the form with the domain name, client owner, IP address selection, and web server settings. Enable SSL if desired, selecting Let’s Encrypt for automatic certificate provisioning.
Email account setup starts in Mail → Email Mailbox. Add new mailboxes by specifying the email address, password, mailbox quota, and optional spam filter settings. ISPConfig automatically configures Postfix and Dovecot for new addresses.
DNS zone configuration occurs in DNS → Zones. Create new zones by entering the domain name and selecting the DNS template. Add individual DNS records as needed for mail servers, subdomains, and verification records.
FTP user creation happens in Sites → FTP Accounts. New FTP accounts link to specific websites, inheriting the website’s document root as the FTP home directory. Set quotas to limit storage consumption.
Database creation uses Sites → Database. Specify the database name, associated website, and database user credentials. ISPConfig creates the database and assigns appropriate privileges automatically.
SSL certificate installation leverages the Let’s Encrypt integration in website settings. Enable SSL, select Let’s Encrypt, and click Save. ISPConfig requests and installs the certificate automatically.
Backup configuration resides in System → Backup. Define backup schedules, retention periods, and storage locations. Regular backups protect against data loss from hardware failure, software bugs, or security incidents.
Troubleshooting Common Installation Issues
Issue 1: Installation Script Fails to Download
When the wget command cannot download the autoinstaller, verify internet connectivity:
ping -c 4 google.comIf ping fails, check network configuration in /etc/network/interfaces or NetworkManager settings.
Ensure wget is installed correctly:
apt install wget -yDNS resolution problems prevent hostname lookups. Test with:
nslookup get.ispconfig.orgIf resolution fails, edit /etc/resolv.conf and add working nameservers like 8.8.8.8 or 1.1.1.1.
Issue 2: Service Failed to Start
When a service fails during installation, check its status immediately:
systemctl status service-nameReview detailed error messages in system logs:
journalctl -xe -u service-namePort conflicts occur when another service uses required ports. Identify port usage:
netstat -tulpn | grep :80Stop conflicting services before retrying ISPConfig installation.
Issue 3: Cannot Access ISPConfig Panel
Firewall misconfigurations block access to port 8080. Verify the port is open:
ufw status | grep 8080If missing, open the port manually:
ufw allow 8080/tcpConfirm Apache or Nginx is running and listening on port 8080:
netstat -tulpn | grep 8080SSL certificate warnings are normal for new installations using self-signed certificates. Click through the browser warning to proceed.
Issue 4: Debian 13 Compatibility
ISPConfig may not officially support Debian 13 immediately upon release. The development team typically adds support for new Debian versions within weeks or months.
Check the ISPConfig forum for Debian 13 compatibility discussions. Community members often share workarounds and manual configuration steps for new distributions.
The automated installer may work despite official support being pending. Test in a virtual machine or development environment before production deployment.
Security Best Practices for ISPConfig
Change all default passwords immediately after installation, including the ISPConfig admin password and MySQL root password. Use strong passwords with 16+ characters, mixing uppercase, lowercase, numbers, and special characters.
Keep system packages updated regularly:
apt update && apt upgrade -yEnable automatic security updates using unattended-upgrades:
dpkg-reconfigure --priority=low unattended-upgradesInstall and configure fail2ban for automated brute force protection:
apt install fail2ban -y
systemctl enable fail2ban
systemctl start fail2banDeploy proper SSL certificates from Let’s Encrypt for all hosted websites. Avoid self-signed certificates in production environments.
Implement regular backup schedules through ISPConfig’s backup system. Test restoration procedures periodically to ensure backups are functional.
Restrict SSH access by disabling root login and using SSH keys instead of passwords. Edit /etc/ssh/sshd_config and set PermitRootLogin no and PasswordAuthentication no.
Monitor log files regularly for suspicious activity. ISPConfig’s Monitor section provides centralized log viewing. Watch for repeated failed login attempts, unusual traffic patterns, or unexpected service restarts.
Maintaining Your ISPConfig Server
Schedule regular system updates to receive security patches and bug fixes. Execute updates during low-traffic periods to minimize disruption:
apt update
apt upgrade -yISPConfig releases updates periodically with new features and security improvements. Update ISPConfig through the command line:
ispconfig_update.shDatabase optimization prevents performance degradation over time. Run optimization commands monthly:
mysqlcheck -o --all-databasesLog file rotation prevents logs from consuming excessive disk space. The automated installer configures logrotate for ISPConfig and all services. Verify rotation settings in /etc/logrotate.d/.
Backup verification ensures data recoverability when needed. Periodically test backup restoration in isolated environments. Automated backups are worthless if restoration procedures fail.
Monitor disk space, CPU usage, and memory consumption through ISPConfig’s monitoring tools. Set up alerts for threshold violations to receive proactive warnings before resources are exhausted.
Security patch management requires vigilance. Subscribe to Debian security announcements and ISPConfig security mailing lists. Apply critical patches immediately upon release.
Congratulations! You have successfully installed ISPConfig. Thanks for using this tutorial to install the latest version of ISPConfig open source hosting control panel on Debian 13 “Trixie” system. For additional help or useful information, we recommend you check the official ISPConfig website.