How To Install Jira on Fedora 42

Installing Jira on Fedora 42 transforms your server into a powerful project management hub capable of handling complex agile workflows and issue tracking. This comprehensive guide walks you through every step of the installation process, from initial system preparation to post-installation optimization. Jira Software, developed by Atlassian, has evolved from a simple bug tracking tool into the industry standard for project management, supporting Scrum, Kanban, and hybrid methodologies.
Fedora 42 provides an excellent foundation for hosting Jira due to its cutting-edge kernel, robust security features, and excellent package management system. Unlike cloud-hosted solutions, self-hosting Jira on Fedora 42 gives you complete control over your data, customization options, and integration capabilities. This installation method is particularly valuable for organizations requiring strict data governance, custom integrations, or enhanced performance optimization.
Whether you’re a system administrator deploying Jira for a development team, an IT professional setting up project tracking infrastructure, or a DevOps engineer building comprehensive toolchains, this guide provides the expertise needed for a successful implementation. The following instructions assume basic Linux knowledge and will result in a production-ready Jira installation optimized for performance and security.
Prerequisites and System Requirements
Before beginning the Jira installation on Fedora 42, ensuring your system meets all hardware and software requirements is crucial for optimal performance and stability.
Hardware Requirements
Jira’s hardware requirements depend heavily on your expected user load and project complexity. For a minimum installation supporting up to 100 users, allocate at least 4GB of RAM, though 8GB or more is strongly recommended for production environments. The CPU requirements include a dual-core processor running at 2GHz or faster, with quad-core processors providing significantly better performance for larger teams.
Storage considerations extend beyond the initial 15GB installation footprint. Plan for substantial growth as Jira databases expand with project data, attachments, and historical information. A minimum of 50GB free space is recommended for production deployments, with SSD storage providing optimal performance for database operations and search indexing.
Network requirements include stable internet connectivity for downloading packages and accessing Atlassian’s licensing servers. Bandwidth requirements scale with team size and integration complexity, but a reliable connection is essential for initial setup and ongoing operations.
Software Prerequisites
A fresh Fedora 42 installation provides the cleanest foundation for Jira deployment. Ensure your system includes the latest kernel updates and security patches before proceeding. Root access or sudo privileges are mandatory for installing system packages and modifying configuration files.
Updated package repositories are essential for accessing the latest versions of dependencies. Fedora’s DNF package manager should be configured with official repositories and any additional repositories required for enterprise software installations.
Basic Linux command line proficiency is assumed throughout this guide. Familiarity with text editors like nano or vim, file permissions, and service management will significantly streamline the installation process.
Domain and Network Configuration
Production Jira installations require careful network planning. Configure DNS records to point your chosen domain to the server’s IP address, enabling users to access Jira through a memorable URL rather than IP addresses.
Firewall configuration must accommodate Jira’s default port 8080, though production deployments typically use standard HTTP (80) and HTTPS (443) ports behind a reverse proxy. Database connectivity requires additional ports: MySQL/MariaDB uses port 3306, while PostgreSQL operates on port 5432.
SSL certificate planning ensures secure communications from day one. Whether using Let’s Encrypt, commercial certificates, or self-signed certificates for testing, having SSL strategy prepared prevents security vulnerabilities and simplifies initial configuration.
System Preparation and Environment Setup
Proper system preparation lays the foundation for a stable and secure Jira installation. This phase involves updating the system, installing essential utilities, and configuring the environment for optimal performance.
System Updates and Essential Packages
Begin by updating your Fedora 42 system to ensure all packages reflect the latest security patches and feature updates. Execute the following commands to clean package caches and perform a comprehensive system update:
sudo dnf clean all
sudo dnf update -yInstall essential utilities that support Jira installation and ongoing maintenance. These packages provide crucial functionality for downloading files, managing archives, and monitoring system performance:
sudo dnf install -y wget curl unzip fontconfig htop vim nanoConfigure the system timezone to match your organization’s primary location or UTC for global teams. Proper timezone configuration ensures accurate timestamps in Jira issues and audit logs:
sudo timedatectl set-timezone UTCSystem reboots after major kernel updates ensure all changes take effect and provide a clean starting point for the Jira installation process.
Directory Structure and Permissions
Create dedicated directories for Jira installation and data storage. This separation enhances security, simplifies backups, and follows Linux filesystem hierarchy standards:
sudo mkdir -p /opt/atlassian/jira
sudo mkdir -p /var/atlassian/application-data/jiraConfigure system limits to accommodate Jira’s resource requirements. Edit /etc/security/limits.conf to increase file descriptor limits, preventing resource exhaustion under heavy load:
echo "jira soft nofile 4096" | sudo tee -a /etc/security/limits.conf
echo "jira hard nofile 65536" | sudo tee -a /etc/security/limits.confCreate a dedicated system user for running Jira services. This isolation improves security by limiting the privileges available to the Jira process:
sudo useradd --system --home-dir /var/atlassian/application-data/jira --shell /bin/bash jira
sudo chown -R jira:jira /var/atlassian/application-data/jiraJava Installation and Configuration
Jira requires Java 11 or later for optimal performance and compatibility. OpenJDK provides an excellent open-source alternative to Oracle JDK, offering full compatibility with Jira while avoiding licensing complexities.
OpenJDK 11 Installation
Install OpenJDK 11 development package using Fedora’s DNF package manager. The development package includes both runtime and development tools, ensuring compatibility with Jira’s requirements:
sudo dnf install -y java-11-openjdk-develVerify the Java installation by checking the version and ensuring the correct JVM is active:
java -version
javac -versionThe output should display OpenJDK version 11.x.x, confirming successful installation. If multiple Java versions exist on the system, use alternatives to configure the default version:
sudo alternatives --config javaMultiple Java versions can coexist on Fedora systems, but Jira requires consistent configuration to function properly. Document the Java version used for future maintenance and upgrade planning.
Environment Variable Configuration
Configure the JAVA_HOME environment variable to point to the OpenJDK installation directory. This variable enables Jira to locate the Java runtime and development tools:
export JAVA_HOME=/usr/lib/jvm/java-11-openjdkMake this configuration persistent across system reboots by adding it to the system-wide environment file:
echo "JAVA_HOME=/usr/lib/jvm/java-11-openjdk" | sudo tee -a /etc/environmentVerify the environment variable configuration by opening a new terminal session and checking the variable:
echo $JAVA_HOMETroubleshoot Java configuration issues by checking file permissions, path accuracy, and system logs. Common problems include incorrect paths, missing packages, or conflicting Java installations that require resolution before proceeding.
Database Setup and Configuration
Jira requires an external database for storing application data, user information, and project configurations. PostgreSQL and MySQL/MariaDB represent the most popular choices, each offering distinct advantages for different deployment scenarios.
Database Selection and Installation
PostgreSQL provides excellent performance, advanced features, and strong consistency guarantees that make it ideal for enterprise Jira deployments. Install PostgreSQL server and initialize the database cluster:
sudo dnf install -y postgresql-server postgresql-contrib
sudo /usr/bin/postgresql-setup --initdb
sudo systemctl enable postgresql
sudo systemctl start postgresqlMariaDB offers a lightweight alternative with excellent compatibility and straightforward configuration. Install and configure MariaDB for organizations preferring MySQL-compatible databases:
sudo dnf install -y mariadb-server mariadb
sudo systemctl enable mariadb
sudo systemctl start mariadb
sudo mysql_secure_installationThe secure installation script configures root passwords, removes test databases, and implements security best practices. Follow the prompts to strengthen database security before creating Jira-specific configurations.
Database service startup and enabling ensures automatic startup during system boots. Monitor service status using systemctl status commands to verify proper operation before proceeding with database configuration.
Database and User Creation
Create a dedicated database user with appropriate permissions for Jira operations. This approach follows security best practices by limiting database access to only necessary operations:
For PostgreSQL:
sudo -u postgres createuser -P jirauser
sudo -u postgres createdb -O jirauser jiradbFor MariaDB/MySQL:
sudo mysql -u root -p
CREATE DATABASE jiradb CHARACTER SET utf8mb4 COLLATE utf8mb4_bin;
CREATE USER 'jirauser'@'localhost' IDENTIFIED BY 'secure_password';
GRANT ALL PRIVILEGES ON jiradb.* TO 'jirauser'@'localhost';
FLUSH PRIVILEGES;
EXIT;Database password security requires strong, unique passwords that resist brute-force attacks. Consider using password managers or automated password generation tools to create robust credentials.
Test database connectivity before proceeding with Jira installation. Connection testing identifies configuration issues early, preventing installation failures:
# For PostgreSQL
psql -h localhost -U jirauser -d jiradb
# For MariaDB/MySQL
mysql -h localhost -u jirauser -p jiradbBackup considerations for production environments include automated backup scripts, retention policies, and recovery testing procedures. Implement database backup strategies before deploying Jira in production environments.
Downloading and Installing Jira
The Jira installation process involves downloading the official installer from Atlassian, configuring installation parameters, and establishing the application as a system service.
Jira Download and Preparation
Navigate to Atlassian’s official download page to obtain the latest Jira Software installer compatible with Linux systems. Always download from official sources to ensure authenticity and security:
cd /tmp
wget https://www.atlassian.com/software/jira/downloads/binary/atlassian-jira-software-9.12.0-x64.binVersion selection considerations include long-term support releases, feature requirements, and compatibility with existing integrations. LTS versions provide stability for production environments, while latest versions offer cutting-edge features.
Verify the downloaded file integrity using checksums provided on Atlassian’s download page. File verification prevents installation of corrupted or tampered installers:
sha256sum atlassian-jira-software-9.12.0-x64.binModify file permissions to make the installer executable:
chmod +x atlassian-jira-software-9.12.0-x64.binInstallation Process
Execute the Jira installer with appropriate privileges. The interactive installer guides you through configuration options and system integration:
sudo ./atlassian-jira-software-9.12.0-x64.binInstallation type selection offers Express Install for default configurations or Custom Install for advanced customization. Express Install suits most deployments, while Custom Install enables specific directory choices and port configurations.
Configure installation directories during the setup process:
- Installation directory:
/opt/atlassian/jira(recommended) - Home directory:
/var/atlassian/application-data/jira(recommended) - TCP port: 8080 (default) or custom port for your environment
- RMI port: 8005 (default) for internal communication
Directory customization should consider filesystem layout, backup strategies, and security requirements. Standard locations simplify administration and follow Linux conventions.
Port configuration affects firewall rules, reverse proxy setup, and user access methods. Document port choices for network configuration and troubleshooting purposes.
Service Configuration
Configure Jira as a system service for automatic startup and management. Service integration enables standard systemctl commands for starting, stopping, and monitoring Jira:
sudo systemctl enable jira
sudo systemctl start jiraService management provides centralized control over Jira operations. Monitor service status to ensure proper startup:
sudo systemctl status jiraUser permissions for service directories must allow the Jira service account to read, write, and execute files within the installation and home directories:
sudo chown -R jira:jira /opt/atlassian/jira
sudo chown -R jira:jira /var/atlassian/application-data/jiraFirewall and SELinux Configuration
Fedora’s security frameworks require specific configuration to allow Jira network access while maintaining system security. Proper firewall and SELinux configuration balances accessibility with protection.
Firewall Rules Configuration
Configure firewall rules to allow access to Jira’s web interface. Open the necessary ports using firewall-cmd with permanent rules that persist across reboots:
sudo firewall-cmd --permanent --add-port=8080/tcp
sudo firewall-cmd --permanent --add-service=http
sudo firewall-cmd --permanent --add-service=https
sudo firewall-cmd --reloadProduction deployments typically use reverse proxies to handle SSL termination and load balancing. Configure additional ports if your architecture requires database access from external systems:
sudo firewall-cmd --permanent --add-port=5432/tcp # PostgreSQL
sudo firewall-cmd --permanent --add-port=3306/tcp # MySQL/MariaDBTest firewall rules effectiveness using port scanning tools or network connectivity tests. Verify that required ports are accessible while unnecessary ports remain blocked.
Security considerations for production environments include restricting database access to localhost, implementing intrusion detection, and regular security audits of firewall configurations.
SELinux Configuration
SELinux (Security-Enhanced Linux) provides mandatory access controls that may interfere with Jira operations. Configure SELinux contexts to allow Jira while maintaining security benefits:
sudo setsebool -P httpd_can_network_connect 1
sudo semanage fcontext -a -t bin_t "/opt/atlassian/jira/bin(/.*)?"
sudo restorecon -R /opt/atlassian/jiraSELinux context configuration ensures Jira processes have appropriate permissions for file access, network operations, and system interactions. Monitor SELinux audit logs for access denials:
sudo ausearch -m avc -ts recentTroubleshoot SELinux-related issues by examining audit logs, adjusting file contexts, or creating custom policies for specific requirements. Balance security with functionality by making minimal necessary changes to SELinux configuration.
Production environments should maintain SELinux in enforcing mode while creating appropriate policies for Jira operations. Avoid disabling SELinux entirely, as this significantly reduces system security.
Initial Configuration and Setup Wizard
Once Jira installation completes, the web-based setup wizard guides you through initial configuration, database connection, and administrator account creation.
Web Interface Access
Access Jira through your web browser using the configured hostname and port. The initial setup wizard appears when accessing Jira for the first time:
http://your-server-hostname:8080Setup wizard navigation begins with language selection and basic configuration options. Choose your preferred language and proceed through configuration steps systematically.
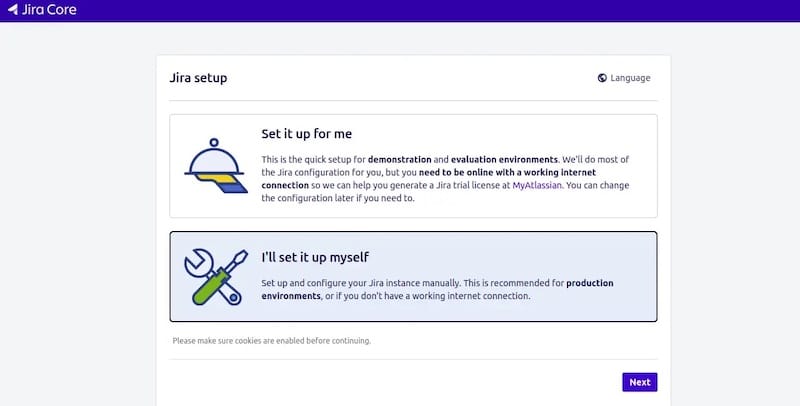
Application title and branding configuration personalizes your Jira instance. Select meaningful titles that reflect your organization and project requirements.
Load balancer considerations apply to production deployments using multiple Jira nodes. Configure session affinity and health checks for optimal performance.
Database Connection and License
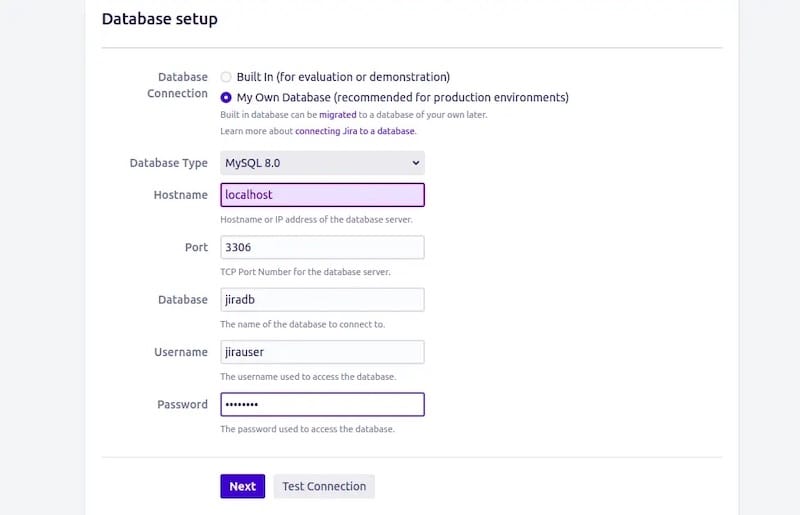
Database configuration in the setup wizard requires the connection details configured earlier. Choose “My own database” and select your database type (PostgreSQL or MySQL):
- Database type: PostgreSQL or MySQL
- Hostname: localhost (typically)
- Port: 5432 (PostgreSQL) or 3306 (MySQL)
- Database: jiradb
- Username: jirauser
- Password: (configured password)
License installation requires a valid Atlassian license key. Evaluate Jira using a trial license or install a purchased license for production deployments. License management affects user limits, feature availability, and support options.
Administrator account creation establishes the primary administrative user. Choose strong credentials and document them securely for future reference:
- Username: admin (or custom administrator name)
- Password: (strong, unique password)
- Email: (valid administrative email address)
Email configuration enables notifications, user registration, and system alerts. Configure SMTP settings using your organization’s email infrastructure or external email services.
Post-Installation Optimization and Security
Optimizing Jira performance and implementing security best practices ensures reliable operation and protects sensitive project data.
Performance Tuning
JVM memory allocation optimization significantly impacts Jira performance. Edit the setenv.sh script to configure heap memory based on your system resources:
sudo nano /opt/atlassian/jira/bin/setenv.shAdd or modify JVM parameters:
JVM_MINIMUM_MEMORY="2048m"
JVM_MAXIMUM_MEMORY="4096m"System resource monitoring helps identify performance bottlenecks and capacity planning requirements. Install monitoring tools to track CPU usage, memory consumption, and disk I/O:
sudo dnf install -y htop iotopLog rotation configuration prevents disk space exhaustion from growing log files. Configure logrotate for Jira logs:
sudo nano /etc/logrotate.d/jiraBackup strategy implementation protects against data loss and enables disaster recovery. Implement automated backups for both the database and Jira home directory using scripts or enterprise backup solutions.
Security Hardening
SSL certificate installation enables HTTPS communication and protects data in transit. Configure SSL certificates using Let’s Encrypt, commercial certificates, or enterprise certificate authorities:
sudo dnf install -y certbot
sudo certbot certonly --standalone -d your-jira-domain.comUser management best practices include strong password policies, multi-factor authentication, and regular access reviews. Configure LDAP integration for enterprise environments requiring centralized authentication.
Regular update procedures maintain security and functionality. Establish schedules for applying security patches, upgrading Jira versions, and updating system packages:
sudo dnf update -yMonitoring and maintenance schedules ensure ongoing system health. Implement automated monitoring for service availability, resource utilization, and security events.
Troubleshooting Common Issues
Understanding common installation and operational issues enables quick resolution and minimizes downtime during Jira deployment and maintenance.
Installation Problems
Java version compatibility issues manifest as startup failures or classpath errors. Verify Java installation and version compatibility with your Jira version. Update or reinstall Java if necessary.
Permission-related errors prevent Jira from accessing files or directories. Check file ownership and permissions for installation and home directories:
sudo chown -R jira:jira /opt/atlassian/jira
sudo chmod -R 755 /opt/atlassian/jiraPort conflicts occur when other services use Jira’s configured ports. Identify conflicting services and either stop them or reconfigure Jira to use alternative ports:
sudo netstat -tulpn | grep :8080Service startup failures often relate to configuration errors, resource constraints, or dependency issues. Examine service logs for detailed error messages:
sudo journalctl -u jira -fPerformance and Connectivity Issues
Memory allocation problems cause slow performance or out-of-memory errors. Monitor JVM memory usage and adjust heap settings based on actual requirements and available system resources.
Database connection errors prevent Jira startup or cause data access failures. Verify database service status, connection parameters, and network connectivity:
sudo systemctl status postgresql
psql -h localhost -U jirauser -d jiradbFirewall and network troubleshooting addresses connectivity issues from client browsers or integrated systems. Test network connectivity and verify firewall rules:
sudo firewall-cmd --list-all
telnet your-server-hostname 8080Log file analysis provides detailed information about errors and performance issues. Key log files include:
/opt/atlassian/jira/logs/atlassian-jira.log/var/log/messages- Database logs (PostgreSQL:
/var/lib/pgsql/data/log/)
Congratulations! You have successfully installed Jira. Thanks for using this tutorial for installing the Jira project management tool on your Fedora 42 Linux system. For additional or useful information, we recommend you check the official Jira website.