How To Install KDE ISO Image Writer on Linux Mint 22

Creating bootable USB drives is essential for any Linux enthusiast. Whether you’re deploying new systems, testing distributions, or preparing recovery media, having a reliable USB creation tool makes all the difference. KDE ISO Image Writer stands out as one of the most secure and user-friendly options available for Linux Mint 22 users. This comprehensive guide walks through everything needed to install and use this powerful application on your system.
What is KDE ISO Image Writer?
KDE ISO Image Writer represents a sophisticated yet straightforward solution for writing ISO image files to USB drives and SD cards. Developed by the KDE community, this open-source application emerged from the ROSA Image Writer project and has evolved into a robust tool that prioritizes both security and usability. Unlike many alternatives that require root privileges, this image writer leverages modern Linux technologies to provide safe, efficient USB creation without unnecessary elevated permissions.
The application supports multiple installation formats including Flatpak, Snap, AppImage, and native packages across various Linux distributions. Its cross-platform capabilities extend beyond Linux to Windows, making it versatile for users managing multiple operating systems. The current stable version 1.0.0, released in May 2023, incorporates years of community feedback and development refinement.
What truly distinguishes this tool is its intelligent design philosophy. The developers implemented features that prevent common user errors, such as accidentally selecting internal hard drives for formatting. Through integration with udisks2 and KAuth, the application requests administrative privileges only when absolutely necessary, maintaining system security throughout the USB creation process.
Key Features and Benefits
Security Features
Security remains paramount in KDE ISO Image Writer’s design architecture. The KAuth integration framework ensures the application never runs with root privileges unnecessarily, minimizing potential security vulnerabilities. This approach contrasts sharply with older tools that demanded full root access for simple USB writing operations.
The safe device selection mechanism automatically filters internal drives from the available target list. Users only see removable media options, virtually eliminating the catastrophic mistake of overwriting system drives. Confirmation dialogs appear before any destructive operations begin, providing a final checkpoint before data modification occurs.
Verification Capabilities
Built-in ISO verification sets this tool apart from simpler alternatives. The application automatically validates ISO files for several major distributions including KDE Neon, Kubuntu, Arch Linux, and Netrunner. Checksum validation ensures ISO integrity before and after the writing process, catching corrupted downloads before they become problematic bootable media.
The threaded verification system prevents interface blocking during lengthy validation procedures. Users can monitor progress without experiencing application freezes, maintaining a responsive experience even when processing large distribution images.
User Experience Excellence
Simplicity defines the user interface philosophy. New users grasp the workflow within seconds—select an ISO file, choose a USB drive, and click create. Clear success and failure messages eliminate ambiguity about operation status. The minimalist design removes unnecessary complexity while retaining all essential functionality.
The application incorporates intelligent “idiot-proofing” measures that guide users toward correct choices and away from potentially destructive actions. Error prevention mechanisms work silently in the background, making the tool remarkably forgiving for less experienced users while remaining efficient for power users.
Cross-Platform Support
Installation flexibility accommodates diverse user preferences and system configurations. Flatpak packages provide distribution-agnostic installation through Flathub, while Snap packages serve Ubuntu-centric ecosystems. AppImage files offer portable solutions requiring no installation, and native packages integrate seamlessly with package managers across different distributions.
Prerequisites and System Requirements
Linux Mint 22 System Requirements
Linux Mint 22 maintains reasonable hardware requirements that most modern computers easily satisfy. The absolute minimum configuration includes 2GB RAM, 20GB disk space, and 1024×768 screen resolution. However, optimal performance requires 4GB RAM, 100GB disk space, and 1440×900 or higher resolution displays. All Linux Mint 22 editions demand 64-bit processors, abandoning legacy 32-bit architecture support.
These requirements extend to KDE ISO Image Writer operation, though the application itself consumes minimal system resources. The primary consideration involves having sufficient free disk space for storing ISO files, which often exceed 2-4GB for modern distributions.
Flatpak Requirements
Linux Mint 22 ships with Flatpak support pre-configured, eliminating manual setup for most users. Flatpak functionality arrived in Linux Mint 18.3 and has remained a core component through all subsequent releases. Flathub repository access provides the gateway to thousands of applications, including KDE ISO Image Writer.
Users need active internet connections for initial application downloads. Subsequent offline usage remains fully functional once installation completes. The Flatpak runtime environment handles all dependency management automatically, simplifying the installation experience considerably.
Additional Prerequisites
Preparation ensures smooth installation and usage. Obtain a USB drive with 4GB minimum capacity, though 8GB or larger proves more versatile for modern distribution images. Verify adequate storage space exists for downloading ISO files from official distribution sources.
Administrative privileges remain necessary for installation procedures and USB writing operations. Standard user accounts with sudo access satisfy this requirement. Basic command line familiarity helps troubleshoot potential issues, though graphical methods handle most installation scenarios without terminal interaction.
Method 1: Install KDE ISO Image Writer via Flatpak (Recommended)
Step 1: Verify Flatpak Installation
Begin by confirming Flatpak exists on your system. Open the terminal application from the application menu or press Ctrl+Alt+T. Execute the following command to check the installed version:
flatpak --versionThe system displays the current Flatpak version number if properly installed. Linux Mint 22 includes Flatpak by default, so most users see immediate version information. Should the system report “command not found,” installation becomes necessary through the following command:
sudo apt install flatpakThis command retrieves Flatpak from official repositories and configures the basic infrastructure. The installation process takes just moments on modern internet connections.
Step 2: Add Flathub Repository
Flathub serves as the primary application repository for Flatpak packages. While Linux Mint 22 typically includes Flathub configuration, verification prevents installation failures. Execute this command to add or verify Flathub repository access:
sudo flatpak remote-add --if-not-exists flathub https://flathub.org/repo/flathub.flatpakrepoThe --if-not-exists flag intelligently checks for existing Flathub configuration before adding duplicate entries. No error messages appear if Flathub already exists in your system configuration. This command establishes the connection to thousands of available Flatpak applications, dramatically expanding software availability beyond traditional repositories.
Confirm successful repository addition by listing configured remotes:
flatpak remotesThe output displays all configured repositories, with Flathub appearing in the list.
Step 3: Install KDE ISO Image Writer
Execute the primary installation command to retrieve KDE ISO Image Writer from Flathub:
sudo flatpak install flathub org.kde.isoimagewriterAlternatively, users preferring per-user installation rather than system-wide deployment can omit sudo:
flatpak install flathub org.kde.isoimagewriterThe installation wizard displays package information including download size and required dependencies. Press Y or Enter to proceed with installation. Flatpak automatically resolves dependencies, downloading required runtime environments if not already present.
Typical installation requires 50-100MB depending on existing Flatpak runtimes. Modern connections complete downloads within 1-2 minutes. Progress indicators display download and installation status throughout the process.
Upon completion, the system confirms successful installation with a summary message listing installed components.
Step 4: Launch the Application
Start KDE ISO Image Writer through multiple methods. Command line users execute:
flatpak run org.kde.isoimagewriterGraphical interface users locate the application through the Linux Mint menu system. Click the Menu button, then navigate to Accessories category or utilize the search function. Type “ISO Image Writer” in the search field to quickly locate the newly installed application.
The application window appears within seconds, displaying the clean, intuitive interface. Success at this stage confirms proper installation and system integration.
Method 2: Install via Software Manager (GUI Method)
Linux Mint Software Manager provides user-friendly application installation for those preferring graphical interfaces over command line operations. Launch Software Manager from the Menu under Administration or through the application search function.
Click the search icon or field in the Software Manager toolbar. Type “ISO Image Writer” or “isoimagewriter” into the search box. The results display available packages matching your query. Locate the entry labeled “ISO Image Writer” with the KDE logo and Flatpak source indication.
Select the application entry to view detailed information including description, screenshots, reviews, and version details. The interface clearly identifies the package source as Flathub/Flatpak. Click the green Install button to initiate the installation process.
The system prompts for your administrative password to authorize installation. Enter your credentials and wait while Software Manager handles dependency resolution and package retrieval automatically. Progress indicators display download and installation status throughout the operation.
Installation completion generates a notification. The application immediately becomes available through the Menu system in the Accessories category. This graphical method proves ideal for users uncomfortable with command line operations, providing identical functionality through an accessible interface.
Method 3: Install from Command Line (APT Package)
Alternative installation through native APT packages suits users preferring distribution-provided packages over Flatpak. Begin by refreshing package repository metadata:
sudo apt updateThis command synchronizes local package indexes with remote repository servers, ensuring access to the latest available versions. Following the update, install the application:
sudo apt install isoimagewriterThe APT package manager resolves dependencies automatically, displaying required packages before installation. Confirm the installation by pressing Y when prompted.
Native packages integrate more tightly with system configurations compared to sandboxed Flatpak applications. However, Flatpak versions often receive updates more quickly as they bypass distribution packaging cycles. Choose the installation method aligning with your preferences regarding update frequency versus system integration depth.
Verify successful installation by checking the installed binary location:
which isoimagewriterThe system displays the executable path if installation succeeded.
How to Use KDE ISO Image Writer on Linux Mint 22
Preparing Your ISO File
ISO file acquisition represents the first critical step. Download desired Linux distribution ISO images exclusively from official sources to ensure authenticity and security. Popular distributions maintain dedicated download pages with direct links and torrent options.
Verify ISO integrity immediately after downloading. Most distribution websites provide SHA256 checksum values alongside download links. Generate the checksum for your downloaded file:
sha256sum /path/to/downloaded.isoCompare the output against the official checksum value published on the distribution website. Matching values confirm file integrity; mismatches indicate corrupted downloads requiring re-acquisition.
Store ISO files in organized directories for future reference. Consider creating a dedicated folder structure like ~/Downloads/ISO/ for easy management of multiple distribution images.
Step-by-Step Usage Guide
Step 1: Launch ISO Image Writer
Open the application through your preferred method—Menu navigation or command line execution. The main window displays a clean interface with clear sections for ISO file selection and USB device targeting.
Step 2: Select Your ISO File
Click the “Path to ISO image” field or Browse button. The file browser appears, allowing navigation to your stored ISO files. Browse to your Downloads folder or wherever you saved the distribution image. Select the desired ISO file and click Open.
The application displays the selected file path, confirming your choice. Supported formats include standard .iso files from virtually any Linux distribution or bootable utility.
Step 3: Insert USB Drive
Connect your USB drive to any available USB port. The system automatically detects the removable media within seconds. Wait for the device recognition process to complete before proceeding.
Backup any important data from the USB drive before continuing. The writing process completely erases all existing content, making data recovery impossible without specialized tools.
Step 4: Select Target USB Device
The Target Device dropdown menu displays detected removable media. Internal hard drives never appear in this list, thanks to built-in safety mechanisms. Carefully verify the correct device selection by examining capacity and device identifiers.
USB device naming conventions follow patterns like /dev/sdb or /dev/sdc. Double-check capacity values match your physical USB drive to prevent selecting wrong devices in multi-USB scenarios.
Step 5: Create Bootable USB
Click the “Create” or “Write” button to initiate the process. A warning dialog appears, explicitly stating that all data on the selected USB drive will be permanently erased. Read the warning carefully and confirm your understanding.
The application requests your administrative password through a secure authentication dialog. Enter your credentials to authorize the operation. This represents the only moment requiring elevated privileges during the entire workflow.
Progress bars display writing status with percentage completion and estimated time remaining. Modern USB 3.0 drives complete typical 2-4GB ISO files within 5-10 minutes. Older USB 2.0 devices require longer durations.
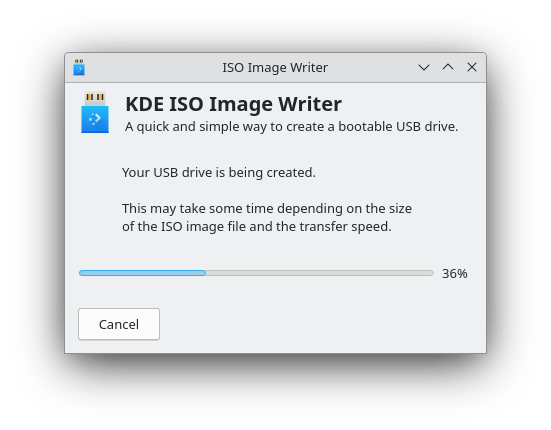
Step 6: Verify Completion
Upon successful completion, a confirmation message appears indicating the bootable USB creation succeeded. For supported distributions, automatic verification runs to ensure data integrity. This validation compares written data against the source ISO file, catching potential errors.
Safely eject the USB drive through the system file manager before physical removal. Right-click the USB drive icon and select “Safely Remove” or “Eject” to flush cached data and unmount the filesystem properly.
Important Warnings and Best Practices
All data on the target USB drive undergoes complete erasure during the writing process. Recovery becomes extremely difficult or impossible after overwriting. Always backup critical files before beginning USB creation procedures.
Never disconnect the USB drive while writing operations are in progress. Premature removal corrupts both the USB drive and leaves it in an unusable state requiring reformatting. Power interruptions during writing also cause similar corruption issues.
Verify ISO checksums before writing to prevent creating bootable media from corrupted source files. Corrupted ISOs produce non-functional bootable USBs that fail during boot attempts or installation procedures.
Troubleshooting Common Issues
Issue 1: Application Won’t Launch
Application launch failures typically stem from incomplete installations or corrupted Flatpak metadata. Verify installation status by listing installed Flatpak applications:
flatpak list --appIf KDE ISO Image Writer appears in the list, attempt repair through reinstallation. Uninstall the application first:
flatpak uninstall org.kde.isoimagewriterThen reinstall following the installation instructions in Method 1. Check system logs for specific error messages providing diagnostic clues:
journalctl -xeReview recent log entries for application-related errors or dependency issues.
Issue 2: USB Drive Not Detected
USB detection problems arise from hardware issues, driver problems, or device formatting complications. Verify physical USB drive functionality by testing on different computers or USB ports. Bad USB ports fail to provide power or data connectivity.
Check kernel device recognition through dmesg logs:
dmesg | tail -20Recently connected USB devices appear in these kernel messages with assigned device names. Missing entries indicate hardware detection failures requiring troubleshooting at the system level.
Format-related problems occasionally prevent proper USB recognition. Try reformatting the USB drive through the Disks utility before attempting ISO writing procedures.
Issue 3: Writing Process Stuck at 0%
Progress indicators freezing at 0% suggest corrupted ISO files, defective USB drives, or permission issues. Test alternative ISO files first to isolate the problem source. Download fresh ISO copies if checksums reveal corruption.
Defective USB drives exhibit inconsistent behavior including write failures and stalled operations. Test suspected defective drives with different applications or systems to confirm hardware failure. Replace failing drives immediately as they provide unreliable data storage.
Permission problems manifest when PolicyKit configurations prevent proper privilege elevation. Verify your user account belongs to required system groups for device access.
Issue 4: Authentication Errors
PolicyKit authentication failures indicate misconfigured privilege systems or account limitations. Confirm your user account possesses sudo privileges by testing a simple sudo command:
sudo echo "test"Successful execution confirms sudo access. Failures require administrator assistance to grant appropriate privileges.
Try launching the application through terminal with verbose output to capture detailed error messages:
flatpak run --verbose org.kde.isoimagewriterError messages provide specific clues about permission or configuration problems.
Issue 5: ISO Verification Fails
Verification failures occur when written data doesn’t match source ISO files or when working with unsupported distributions. KDE ISO Image Writer automatically verifies specific distributions including KDE Neon, Kubuntu, Arch Linux, and Netrunner. Other distributions may not support automatic verification.
Manually verify ISO integrity before writing using checksum validation:
sha256sum /path/to/iso/file.isoCompare results against official distribution checksums. Mismatches require re-downloading the ISO file from official sources.
Re-download suspected corrupted files using different download methods. Torrent downloads often provide more reliable transfers through automatic error checking and corruption detection.
Updating and Maintaining KDE ISO Image Writer
Updating Flatpak Applications
Flatpak applications receive updates independently from system package updates. Manually update all installed Flatpak applications through a single command:
flatpak updateThe system checks for available updates across all installed applications and runtimes. Confirm updates when prompted to download and install new versions.
Update specific applications individually by specifying the application identifier:
flatpak update org.kde.isoimagewriterThis targeted approach updates only KDE ISO Image Writer, leaving other applications at current versions.
Automatic Updates via Software Manager
Linux Mint Software Manager handles Flatpak updates through its unified interface. Launch Software Manager and navigate to the Updates section. The interface displays available updates for all package types including Flatpak applications.
Select KDE ISO Image Writer from the update list and click Install Updates. The system handles download and installation automatically. Configure automatic update checks in Software Manager preferences to receive notifications when updates become available.
Checking Current Version
Display installed Flatpak applications with version information:
flatpak list --app --columns=name,application,versionLocate KDE ISO Image Writer in the output to verify the installed version number. Compare against the latest release information on the official KDE Apps website or Flathub page.
Future Updates and Features
KDE ISO Image Writer continues active development with exciting improvements on the horizon. The upcoming UI redesign utilizing Kirigami frameworks promises enhanced mobile and touch device compatibility. Direct ISO download capabilities will eliminate separate browser downloads, streamlining the workflow significantly.
Pre-authentication features under development will request permissions once rather than repeatedly during multiple USB creation sessions. These enhancements maintain the tool’s position as a premier choice for Linux bootable media creation.
Uninstalling KDE ISO Image Writer
Removing Flatpak Version
Uninstall KDE ISO Image Writer through Flatpak commands when no longer needed:
flatpak uninstall org.kde.isoimagewriterThe system confirms the uninstallation request and removes the application along with its specific data. Remove unused runtime dependencies to reclaim additional disk space:
flatpak uninstall --unusedThis command identifies and removes orphaned runtimes no longer required by any installed applications.
Removing via Software Manager
Software Manager provides graphical uninstallation for users preferring point-and-click interfaces. Launch Software Manager and search for KDE ISO Image Writer. Select the installed application from search results. The interface displays a Remove or Uninstall button replacing the Install button for installed applications.
Click Remove and authenticate with your administrative password. The system handles removal automatically, displaying progress indicators during the process.
Removing APT Package
Users who installed through APT repositories uninstall using traditional apt commands:
sudo apt remove isoimagewriterThis command removes the application while preserving configuration files. Completely purge all traces including configurations:
sudo apt purge isoimagewriterClean residual package files and dependencies:
sudo apt autoremoveVerifying Complete Removal
Confirm successful removal by checking for remaining files or executable paths:
which isoimagewriter
flatpak list | grep isoimagewriterEmpty results indicate complete removal. Manually inspect configuration directories if concerns about leftover files persist.
Security and Privacy Considerations
Why KDE ISO Image Writer is Secure
Security architecture distinguishes KDE ISO Image Writer from less sophisticated alternatives. KAuth integration restricts privilege escalation to specific operations requiring elevated permissions. The application never runs entirely as root, limiting potential security vulnerabilities from code exploits.
Udisks2 framework handles low-level device operations through secure system services. This abstraction layer prevents direct device manipulation requiring dangerous root access. Modern privilege separation principles guide the entire implementation, aligning with contemporary Linux security best practices.
Open-source transparency enables community security audits. The GPL-3.0 license grants full source code access to anyone interested in reviewing implementation details. Security researchers regularly examine popular open-source projects, reporting and fixing vulnerabilities collaboratively.
Best Practices for Safe USB Creation
Download ISO files exclusively from official distribution websites or verified mirrors. Third-party download sites occasionally distribute modified images containing malware or unwanted software. Bookmark official distribution websites to ensure consistent access to legitimate download sources.
Verify checksums religiously before writing any ISO file. This simple verification step catches corrupted downloads before they become problematic bootable media. Automated checksum verification takes seconds but prevents hours of frustration troubleshooting mysteriously failing installations.
Dedicate specific USB drives to bootable media rather than mixing purposes. Frequent reformatting reduces USB drive lifespan. Keeping separate drives for data storage and bootable media extends hardware longevity while maintaining clear organizational separation.
Data Privacy
KDE ISO Image Writer implements zero telemetry or data collection. The application operates entirely locally without sending usage statistics, file information, or personal data to external servers. Internet connectivity serves solely for initial installation; all subsequent operations function completely offline.
Local file operations maintain complete privacy. Your ISO files and USB devices remain under exclusive control without external monitoring or tracking. This privacy-respecting approach aligns with broader KDE community values emphasizing user autonomy and data protection.
Permission Management
PolicyKit prompts represent security checkpoints preventing unauthorized device access. Understand these authentication requests as legitimate security measures rather than annoying obstacles. Administrative privileges become necessary for low-level device operations including disk writing and partition manipulation.
Review requested permissions carefully before approving authentication dialogs. Legitimate applications clearly explain why privileges are needed. Suspicious or unexplained permission requests warrant investigation before approval.
Advanced Tips and Use Cases
Creating Multi-Distribution Testing Environment
Maintain multiple USB drives containing different Linux distributions for comprehensive testing environments. Label each USB drive clearly with permanent markers indicating distribution contents. This organization prevents confusion when working with multiple bootable media simultaneously.
Establish systematic ISO file organization. Create distribution-specific subdirectories under a main ISO folder. Name files consistently including distribution name, version, and architecture. Proper file management simplifies locating correct ISOs when creating bootable USBs.
Enterprise and Educational Use
System administrators deploying Linux across multiple machines benefit significantly from standardized installation media. Create bootable USBs from customized distribution images containing preconfigured settings and applications. This standardization reduces deployment time and ensures consistency across organizational infrastructure.
Educational institutions teaching Linux administration find KDE ISO Image Writer ideal for student USB creation projects. The safe interface prevents catastrophic mistakes while teaching proper bootable media creation procedures. Students gain practical experience without risking institutional hardware.
System Recovery Scenarios
Maintain dedicated rescue USB drives containing live Linux distributions specialized for system recovery. Distributions like SystemRescue or GParted Live provide powerful troubleshooting tools for repairing damaged installations. Store these emergency USB drives safely alongside important recovery documentation.
Periodically refresh rescue USB drives with updated distribution versions. Recovery tools improve continuously, and updated utilities better support recent hardware. Annual updates maintain rescue media effectiveness for emergency situations.
Testing New Linux Distributions
Safe distribution evaluation requires live USB testing before commitment. KDE ISO Image Writer facilitates risk-free exploration of unfamiliar distributions. Boot computers from live USBs to evaluate desktop environments, application selections, and hardware compatibility without modifying existing installations.
Create notes documenting testing experiences for future reference. Maintain comparison spreadsheets tracking distribution features, performance characteristics, and hardware compatibility results. Systematic testing produces valuable decision-making data for migration planning.
Command Line Integration
Advanced users integrate KDE ISO Image Writer into automated workflows through command line invocation. Scripts can launch the application programmatically for repetitive USB creation tasks. While full automation requires direct dd usage, GUI launch automation streamlines manual workflows.
Performance Optimization
USB 3.0 or USB 3.1 drives dramatically reduce writing times compared to legacy USB 2.0 devices. Modern high-speed drives complete 4GB ISO writes in under 5 minutes. Investment in quality USB drives pays dividends through time savings over multiple uses.
Select USB drives from reputable manufacturers ensuring consistent performance and longevity. Cheap, no-name USB drives often fail prematurely or exhibit frustratingly slow write speeds. Quality hardware maintains reliability across hundreds of write cycles.
Congratulations! You have successfully installed ISO Image Writer. Thanks for using this tutorial for installing KDE ISO Image Writer on your Linux Mint 22 system. For additional help or useful information, we recommend you check the official ISO Image Writer website.