How To Install KRdp on Manjaro

Remote desktop access has become essential for modern computing workflows. Whether you’re managing multiple systems, working remotely, or providing technical support, having reliable remote desktop protocol (RDP) functionality on your Manjaro Linux system can significantly enhance productivity and flexibility.
KRdp represents KDE’s native approach to remote desktop sharing, offering seamless integration with the Plasma desktop environment. Unlike traditional remote desktop solutions that often feel clunky or resource-intensive, KRdp provides a streamlined experience specifically designed for KDE users. This comprehensive guide will walk you through every aspect of installing, configuring, and optimizing KRdp on Manjaro Linux.
The installation process involves several components working together harmoniously. From initial system preparation to advanced security configurations, each step plays a crucial role in establishing a robust remote desktop infrastructure. By the end of this guide, you’ll have a fully functional KRdp server capable of handling multiple concurrent connections while maintaining optimal security standards.
Understanding KRdp Architecture and System Requirements
Technical Architecture Overview
KRdp operates as an integrated component within the KDE Plasma desktop environment, leveraging the existing desktop sharing framework that KDE has refined over years of development. The system builds upon FreeRDP libraries while maintaining native integration with plasma-krdp_server.service, creating a cohesive remote desktop experience that feels natural to KDE users.
The architecture differs significantly from standalone RDP solutions like xRDP. KRdp utilizes Plasma’s built-in screen sharing capabilities, which means it can take advantage of modern display protocols including Wayland support. This integration allows for features like seamless clipboard sharing, audio redirection, and native window management that external solutions often struggle to implement effectively.
When a client connects to your KRdp server, the system establishes a secure channel using industry-standard encryption protocols. The server can operate in two distinct modes: session sharing, where remote users see and interact with your current desktop session, or new session mode, where each connection receives an independent desktop environment. Understanding these operational modes helps determine the most appropriate configuration for your specific use case.
System Requirements and Compatibility Matrix
Manjaro Linux compatibility with KRdp depends on several factors, with the most critical being your KDE Plasma version. Modern Manjaro installations typically ship with Plasma 5.24 or newer, which includes comprehensive KRdp support. However, users running older installations may need to perform system updates before proceeding.
Hardware requirements remain modest for basic remote desktop functionality. A dual-core processor with 4GB RAM can handle single remote sessions effectively, while systems supporting multiple concurrent connections should have at least 8GB RAM and a quad-core processor. Graphics performance impacts remote desktop quality significantly, especially when sharing media-rich content or running graphics-intensive applications.
Network infrastructure plays an equally important role in KRdp performance. Bandwidth requirements vary based on screen resolution, color depth, and activity level. Standard office productivity tasks require approximately 1-2 Mbps per connection, while media streaming or graphical applications may demand 5-10 Mbps or more. Latency becomes particularly noticeable above 100ms, affecting user experience during interactive tasks.
Port configuration requires careful planning, especially in enterprise environments. KRdp uses port 53731 by default, but this can be customized during configuration. Firewall rules must accommodate both incoming connections and any required port forwarding for external access.
Pre-Installation System Preparation
Comprehensive System Updates
Before installing KRdp, ensuring your Manjaro system runs the latest packages prevents compatibility issues and security vulnerabilities. Begin by refreshing package databases and performing a full system upgrade:
sudo pacman -SyuThis command synchronizes package databases with remote repositories and upgrades all installed packages to their latest versions. The process may take several minutes depending on the number of pending updates and your internet connection speed.
After completing system updates, verify your current KDE Plasma version to ensure compatibility:
plasmashell --versionMost KRdp features require Plasma 5.20 or newer. If you’re running an older version, consider whether upgrading to a more recent Manjaro release would be beneficial for your remote desktop requirements.
Package management configuration should include AUR (Arch User Repository) support, as some KRdp-related packages may only be available through community repositories. Enable AUR support through Pamac or install an AUR helper like yay:
sudo pacman -S yayNetwork and Security Infrastructure Setup
Network configuration forms the foundation of reliable remote desktop access. Start by establishing a static IP address for your Manjaro system, particularly important for consistent remote connections. Edit the network configuration through NetworkManager or systemd-networkd depending on your system setup.
For NetworkManager-based systems, use nmcli to configure static addressing:
sudo nmcli connection modify "connection-name" ipv4.addresses 192.168.1.100/24
sudo nmcli connection modify "connection-name" ipv4.gateway 192.168.1.1
sudo nmcli connection modify "connection-name" ipv4.dns 192.168.1.1
sudo nmcli connection modify "connection-name" ipv4.method manualReplace “connection-name” with your actual network connection identifier, which you can discover using:
nmcli connection showFirewall configuration requires opening the appropriate ports while maintaining security. Manjaro typically includes UFW (Uncomplicated Firewall) for simplified firewall management:
sudo ufw enable
sudo ufw allow 53731/tcpFor more granular control, specify source IP ranges to restrict access:
sudo ufw allow from 192.168.1.0/24 to any port 53731User account preparation involves creating dedicated accounts for remote access, avoiding the use of administrative accounts for routine remote desktop sessions. Create a standard user account with appropriate group memberships:
sudo useradd -m -G users,wheel remote-user
sudo passwd remote-userInstalling KRdp on Manjaro Linux
Method 1: Official Repository Installation
Most modern Manjaro installations include KRdp components as part of the standard KDE Plasma package collection. However, you may need to install additional packages to ensure complete functionality.
Start by installing the core FreeRDP packages that provide the underlying remote desktop protocol implementation:
sudo pacman -S freerdpNext, install plasma-desktop components if they’re not already present:
sudo pacman -S plasma-desktopThe plasma-krdp_server service should be included with standard Plasma installations, but verify its presence:
systemctl list-unit-files | grep krdpIf the service doesn’t appear, you may need to install additional KDE components:
sudo pacman -S kde-system-metaThis meta-package includes various KDE system components that ensure complete desktop sharing functionality.
Method 2: AUR Installation for Advanced Features
Some users prefer AUR packages that provide additional features or more recent versions of KRdp components. Exercise caution when installing AUR packages, as they’re community-maintained and may not receive the same testing as official repository packages.
Install an AUR helper if you haven’t already:
sudo pacman -S base-devel git
git clone https://aur.archlinux.org/yay.git
cd yay
makepkg -siSearch for available KRdp-related AUR packages:
yay -Ss krdpInstall any desired additional packages, being mindful of dependency conflicts with officially installed packages.
Installation Verification and Testing
After completing the installation process, verify that all components are properly installed and functional. Check for the presence of required packages:
pacman -Q | grep -E "(freerdp|plasma)"Verify that the plasma-krdp_server service exists and can be managed:
systemctl status plasma-krdp_server.serviceAt this point, the service will likely be inactive, which is expected behavior before configuration. Test basic FreeRDP functionality by attempting to connect to another RDP server (if available) to ensure client components work correctly.
Configuring KRdp Server Settings
Initial Configuration Through System Settings
KDE System Settings provides the primary interface for configuring KRdp server functionality. Access the desktop sharing settings through the system menu:
- Open System Settings from the application launcher
- Navigate to Sharing in the left sidebar
- Select Desktop Sharing from the available options
The Desktop Sharing interface presents several configuration options. Enable remote desktop access by checking the “Activate RDP server” checkbox. This action initializes the plasma-krdp_server service and begins listening for incoming connections on the default port.
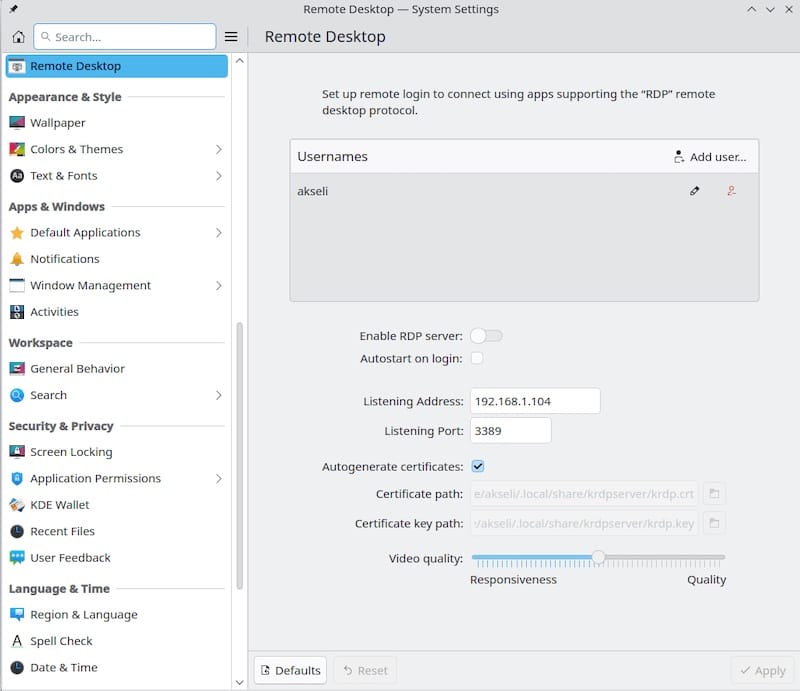
Authentication settings determine how remote clients connect to your system. The simplest approach uses standard user account credentials, requiring remote users to provide valid username and password combinations for system accounts. More advanced configurations can integrate with network authentication systems or implement additional security layers.
Connection settings allow customization of network parameters including port numbers and network interface bindings. The default port 53731 works well for most installations, but you might need to change this value to avoid conflicts with other services or comply with organizational network policies.
Session sharing behavior significantly affects the remote desktop experience. Choose between sharing your current desktop session or creating new sessions for each connection. Session sharing allows multiple users to collaborate on the same desktop, while new sessions provide isolated environments for each user.
Advanced Configuration Options
Advanced users often require more granular control over KRdp behavior than the graphical interface provides. Configuration files located in /etc/ and user-specific directories allow detailed customization of server behavior.
Performance optimization involves balancing image quality against bandwidth consumption and system resources. Higher quality settings provide better visual fidelity but require more network bandwidth and processing power. Experiment with different settings to find the optimal balance for your specific environment and use cases.
Security protocol configuration determines encryption levels and authentication methods. Modern KRdp implementations support TLS encryption for data transmission, providing strong protection against network eavesdropping. Enable the highest security levels your client software supports while maintaining compatibility requirements.
Network interface binding becomes important in multi-homed systems where you want to restrict KRdp access to specific network segments. Configure the server to listen only on internal network interfaces to prevent external access attempts, or bind to specific IP addresses for granular control.
Systemd Service Management
The plasma-krdp_server systemd service manages the KRdp server process lifecycle. Understanding service management commands helps troubleshoot issues and maintain reliable operation.
Start the service manually for testing:
sudo systemctl start plasma-krdp_server.serviceCheck service status and recent log entries:
systemctl status plasma-krdp_server.serviceEnable automatic startup so the service begins during system boot:
sudo systemctl enable plasma-krdp_server.serviceMonitor service logs in real-time during troubleshooting:
journalctl -u plasma-krdp_server.service -fService dependencies ensure that required components start before KRdp attempts initialization. Review dependency relationships to understand startup order and troubleshoot service failures:
systemctl list-dependencies plasma-krdp_server.serviceSecurity Configuration and Best Practices
User Authentication and Access Control
Implementing robust authentication mechanisms protects your system from unauthorized access while maintaining usability for legitimate users. Start by creating dedicated user accounts specifically for remote desktop access, avoiding the use of administrative accounts for routine remote sessions.
Strong password policies form the foundation of authentication security. Enforce minimum password lengths, complexity requirements, and regular password changes. Configure PAM (Pluggable Authentication Modules) to implement these policies system-wide:
Edit /etc/security/pwquality.conf to set password requirements:
minlen = 12
minclass = 3
maxrepeat = 2Consider implementing account lockout policies to prevent brute-force attacks:
# Edit /etc/security/faillock.conf
deny = 5
unlock_time = 900For enhanced security environments, explore two-factor authentication integration. While KRdp doesn’t natively support 2FA, you can implement it at the system level using PAM modules like Google Authenticator or hardware tokens.
Firewall and Network Security Implementation
Network-level security controls provide the first line of defense against unauthorized access attempts. Configure your firewall to implement defense-in-depth strategies that protect your KRdp server while maintaining necessary functionality.
UFW provides simplified firewall management suitable for most installations:
# Allow RDP access from specific network segments
sudo ufw allow from 192.168.1.0/24 to any port 53731
# Allow RDP access from specific IP addresses
sudo ufw allow from 10.0.0.100 to any port 53731
# Deny all other access attempts
sudo ufw default deny incomingMore complex network environments may require advanced firewall configurations using iptables directly:
# Allow established connections
iptables -A INPUT -m state --state ESTABLISHED,RELATED -j ACCEPT
# Allow RDP from trusted networks
iptables -A INPUT -s 192.168.1.0/24 -p tcp --dport 53731 -j ACCEPT
# Log and drop other attempts
iptables -A INPUT -p tcp --dport 53731 -j LOG --log-prefix "RDP-REJECT: "
iptables -A INPUT -p tcp --dport 53731 -j REJECTVPN integration provides additional security layers by encrypting all network traffic between remote clients and your Manjaro system. Consider implementing site-to-site VPN connections or requiring remote users to establish VPN connections before accessing RDP services.
Encryption and Protocol Security
Modern KRdp implementations support multiple encryption standards to protect data transmission. Configure the highest encryption levels compatible with your client software and network infrastructure.
TLS encryption provides strong protection against network interception. Enable TLS for all RDP connections and configure certificate validation to prevent man-in-the-middle attacks. Generate SSL certificates using Let’s Encrypt or your organization’s certificate authority:
# Install certbot for Let's Encrypt certificates
sudo pacman -S certbot
# Generate certificates (adjust domain name)
sudo certbot certonly --standalone -d your-manjaro-system.domain.comNetwork Level Authentication (NLA) adds an additional security layer by requiring authentication before establishing full RDP sessions. This prevents unauthorized users from accessing login screens and reduces attack surface area.
Regular security updates maintain protection against newly discovered vulnerabilities. Establish automated update procedures while testing updates in non-production environments first:
# Create automated update script
#!/bin/bash
pacman -Syu --noconfirm
systemctl restart plasma-krdp_server.serviceClient Connection Setup and Testing
Linux Client Configuration
KRDC (KDE Remote Desktop Client) provides native integration with KRdp servers, offering the best user experience for KDE-based client systems. Install KRDC through your distribution’s package manager:
sudo pacman -S krdcConfigure KRDC connections by creating new connection profiles:
- Launch KRDC from the application menu
- Select “New Connection” from the File menu
- Choose RDP as the connection protocol
- Enter your Manjaro system’s IP address and port
- Configure authentication credentials and connection options
Save connection profiles for quick access to frequently used systems. KRDC supports various connection parameters including screen resolution, color depth, and resource sharing options.
Remmina offers an alternative RDP client with extensive configuration options and support for multiple protocols. Install Remmina for environments requiring more advanced client features:
sudo pacman -S remmina freerdpCreate Remmina connection profiles with optimized settings for your network environment and usage patterns. Experiment with compression levels and color depth settings to find the optimal balance between performance and quality.
Command-line RDP clients provide scripting capabilities and automated connection options. FreeRDP includes command-line tools for advanced users:
xfreerdp /v:192.168.1.100:53731 /u:username /p:password /w:1920 /h:1080Windows and Cross-Platform Clients
Windows Remote Desktop Connection provides built-in RDP client functionality with broad compatibility across KRdp implementations. Configure Windows clients by accessing “Remote Desktop Connection” through the Start menu or running mstsc.
Connection settings should specify your Manjaro system’s IP address and custom port if you’ve changed from the default. Use the format 192.168.1.100:53731 in the Computer field to specify non-standard ports.
Advanced settings allow optimization for different network conditions and security requirements. Enable clipboard sharing, drive redirection, and audio forwarding based on your needs while considering security implications of each feature.
macOS clients can use Microsoft Remote Desktop from the App Store or third-party applications like Royal TSX. Configuration procedures remain similar to Windows clients, with some interface differences.
Mobile clients extend remote desktop access to smartphones and tablets. Applications like RD Client for iOS and Android provide touch-optimized interfaces for managing remote Manjaro systems from mobile devices.
Troubleshooting Common Issues and Solutions
Service Startup and Configuration Problems
Service startup failures often result from dependency issues or configuration conflicts. Begin troubleshooting by examining systemd service logs for specific error messages:
journalctl -u plasma-krdp_server.service --since "1 hour ago"Common error patterns include missing dependencies, port conflicts, and permission issues. Address dependency problems by installing missing packages or updating existing components:
# Reinstall plasma-desktop components
sudo pacman -S plasma-desktop --force
# Verify FreeRDP installation
sudo pacman -S freerdp --forcePort conflicts occur when other services use the same network port as KRdp. Identify conflicting services using netstat or ss:
ss -tlnp | grep 53731If conflicts exist, either change the KRdp port configuration or stop conflicting services. Update firewall rules accordingly when changing port numbers.
Permission issues may prevent the service from accessing required system resources. Verify that the plasma-krdp_server service runs with appropriate privileges and can access necessary files and directories.
Connection and Authentication Failures
Client connection failures often stem from network connectivity issues, authentication problems, or configuration mismatches. Systematic troubleshooting helps identify and resolve these issues quickly.
Test basic network connectivity using ping and telnet:
# Test basic connectivity
ping 192.168.1.100
# Test port accessibility
telnet 192.168.1.100 53731If telnet connections fail, verify firewall configurations on both client and server systems. Ensure that intermediary network equipment (routers, switches, firewalls) allows traffic on the required ports.
Authentication failures require verification of user account settings and password accuracy. Test authentication using standard login methods before attempting remote desktop connections:
# Test user account functionality
su - remote-userAccount lockout policies may prevent connections after multiple failed attempts. Check account status and unlock accounts if necessary:
# Check account lock status
faillock --user remote-user
# Reset failed login attempts
sudo faillock --user remote-user --resetPerformance Optimization and Quality Issues
Remote desktop performance depends on multiple factors including network bandwidth, server resources, client capabilities, and configuration settings. Systematic optimization addresses each component for optimal user experience.
Network performance analysis helps identify bandwidth limitations and latency issues. Use tools like iperf3 to measure available bandwidth between client and server:
# On server
iperf3 -s
# On client
iperf3 -c 192.168.1.100Reduce bandwidth requirements by adjusting color depth and compression settings. Lower color depths and higher compression levels decrease bandwidth usage at the cost of visual quality.
Server resource monitoring identifies performance bottlenecks during remote desktop sessions. Monitor CPU usage, memory consumption, and disk I/O during typical workloads:
# Monitor system resources
htop
# Monitor disk I/O
iotop
# Check memory usage
free -hGraphics performance affects remote desktop responsiveness, particularly during media playback or graphics-intensive applications. Consider upgrading graphics drivers or hardware for demanding use cases.
Advanced Configuration and Enterprise Integration
Performance Tuning and Optimization
Advanced performance optimization requires understanding the relationship between various configuration parameters and their impact on user experience. Video codec settings significantly affect both bandwidth consumption and visual quality.
Configure codec preferences based on your specific use case requirements:
# Edit RDP server configuration
# /etc/xrdp/xrdp.ini (if using hybrid setup)
[Globals]
bitmap_cache=yes
bitmap_compression=yesBandwidth limiting prevents remote desktop sessions from consuming excessive network resources, particularly important in shared network environments:
# Configure traffic shaping with tc
tc qdisc add dev eth0 root handle 1: htb default 30
tc class add dev eth0 parent 1: classid 1:1 htb rate 100mbit
tc class add dev eth0 parent 1:1 classid 1:10 htb rate 10mbit ceil 20mbit
tc filter add dev eth0 protocol ip parent 1:0 prio 1 u32 match ip dport 53731 0xffff flowid 1:10Load balancing across multiple servers provides scalability for environments supporting many concurrent users. Implement load balancing using tools like HAProxy or nginx:
upstream krdp_servers {
server 192.168.1.100:53731;
server 192.168.1.101:53731;
server 192.168.1.102:53731;
}
server {
listen 53731;
proxy_pass krdp_servers;
}Enterprise Integration and Management
Active Directory integration enables centralized user management and single sign-on capabilities. Configure PAM modules to authenticate against Active Directory domain controllers:
# Install required packages
sudo pacman -S samba krb5
# Configure Kerberos authentication
# Edit /etc/krb5.conf
[realms]
DOMAIN.COM = {
kdc = dc1.domain.com
admin_server = dc1.domain.com
}Centralized configuration management becomes essential when managing multiple Manjaro systems with KRdp. Use configuration management tools like Ansible or Puppet to maintain consistent configurations:
# Ansible playbook example
- name: Configure KRdp on Manjaro systems
hosts: manjaro_servers
tasks:
- name: Install KRdp packages
pacman:
name:
- freerdp
- plasma-desktop
state: present
- name: Configure KRdp service
systemd:
name: plasma-krdp_server.service
enabled: yes
state: startedMonitoring and logging solutions provide visibility into remote desktop usage and performance. Implement log aggregation using tools like ELK stack or simple log forwarding to central servers:
# Configure rsyslog forwarding
echo "*.* @@log-server:514" >> /etc/rsyslog.conf
systemctl restart rsyslogSystem Maintenance and Long-term Management
Regular Maintenance Procedures
Establishing regular maintenance schedules ensures continued reliability and security of your KRdp installation. Weekly maintenance tasks should include monitoring log files for errors, checking service status, and verifying that remote connections function correctly.
Update procedures require careful planning to minimize service disruptions while maintaining security. Create maintenance windows for applying system updates and testing KRdp functionality afterward:
#!/bin/bash
# Maintenance script
echo "Starting weekly KRdp maintenance..."
# Stop KRdp service
systemctl stop plasma-krdp_server.service
# Update system packages
pacman -Syu --noconfirm
# Restart KRdp service
systemctl start plasma-krdp_server.service
# Test basic functionality
sleep 5
systemctl status plasma-krdp_server.service
echo "Maintenance completed"Security patch monitoring becomes critical for maintaining protection against emerging threats. Subscribe to Manjaro security announcements and KDE security bulletins to stay informed about important updates.
Backup and Recovery Planning
Configuration backup procedures should capture all customizations and settings required to restore KRdp functionality after system failures or migrations. Key files to backup include:
- System configuration files in
/etc/ - User-specific configurations in home directories
- Service configuration files
- Custom scripts and automation tools
#!/bin/bash
# KRdp backup script
BACKUP_DIR="/backup/krdp-$(date +%Y%m%d)"
mkdir -p "$BACKUP_DIR"
# Backup system configurations
cp -r /etc/systemd/system/plasma-krdp* "$BACKUP_DIR/"
# Backup user configurations
tar -czf "$BACKUP_DIR/user-configs.tar.gz" /home/*/.*krdp*
# Export installed packages list
pacman -Qe > "$BACKUP_DIR/installed-packages.txt"
echo "Backup completed: $BACKUP_DIR"Recovery procedures should be tested regularly to ensure they work correctly when needed. Document step-by-step recovery processes and maintain them in accessible locations.
Disaster recovery planning addresses scenarios where complete system rebuilds become necessary. Maintain documentation of hardware configurations, network settings, and installation procedures to expedite recovery processes.
Congratulations! You have successfully installed KRdp. Thanks for using this tutorial for installing KRdp on Manjaro Linux system. For additional help or useful information, we recommend you check the official KRdp website.