How To Install Mattermost on CentOS Stream 10

Mattermost stands as a powerful, open-source alternative to proprietary collaboration platforms like Slack. As organizations increasingly prioritize data sovereignty and customizable communication solutions, self-hosted platforms like Mattermost have gained significant traction. This comprehensive guide will walk you through installing Mattermost on CentOS Stream 10, providing you with a secure, reliable, and fully-controlled messaging platform for your team or enterprise.
CentOS Stream 10 offers an excellent foundation for Mattermost deployment, combining the stability of enterprise-grade Linux with the forward-looking features that make it ideal for modern server applications. By following this guide, system administrators and DevOps engineers will gain the knowledge needed to deploy a production-ready Mattermost instance with proper security considerations and optimization techniques.
Prerequisites
Before diving into the installation process, ensuring your system meets the necessary requirements will save you troubleshooting time later. Mattermost’s performance depends significantly on your hardware configuration and supporting software environment.
Hardware Requirements
For a successful Mattermost installation on CentOS Stream 10, your server should meet these minimum specifications:
- 2GB RAM (minimum for small teams)
- 1 vCPU/core (supports up to 1,000 users)
- 20GB storage for application data and logs
- Additional storage for file uploads and media sharing
For larger deployments supporting over 1,000 users, consider upgrading to at least 4GB RAM and 2 vCPUs for optimal performance.
Software Requirements
Your CentOS Stream 10 installation will need these components:
- Fresh installation of CentOS Stream 10
- PostgreSQL 13+ database (recommended by Mattermost)
- Web server (NGINX or Apache) for reverse proxy
- Administrative (sudo) privileges for installation
System Preparation
Begin by updating your CentOS Stream 10 system packages to ensure you’re working with the latest security patches and dependencies:
sudo dnf update -yVerify your system architecture compatibility using:
lscpu | grep -i "architecture\|cpu op-mode"This ensures your system supports the x86_64_v3 architecture required for optimal Mattermost performance.
Installing Dependencies
Mattermost relies on several key components to function properly. Let’s set these up one by one.
PostgreSQL Database Setup
While Mattermost supports both PostgreSQL and MySQL/MariaDB, PostgreSQL is the recommended database for production environments due to its stability and performance characteristics.
First, install PostgreSQL on your CentOS Stream 10 server:
sudo dnf install -y postgresql-server postgresql-contribInitialize the database and enable automatic startup:
sudo postgresql-setup --initdb
sudo systemctl enable postgresql
sudo systemctl start postgresqlNow create a dedicated database and user for Mattermost:
sudo -u postgres psqlOnce in the PostgreSQL shell, execute the following SQL commands:
CREATE DATABASE mattermost;
CREATE USER mmuser WITH PASSWORD 'your_secure_password';
GRANT ALL PRIVILEGES ON DATABASE mattermost TO mmuser;
\qRemember to replace ‘your_secure_password’ with a strong, unique password.
Configure PostgreSQL to accept connections from Mattermost by editing the client authentication configuration file:
sudo nano /var/lib/pgsql/data/pg_hba.confAdd this line before the existing “host” entries:
host mattermost mmuser 127.0.0.1/32 md5Save the file and restart PostgreSQL:
sudo systemctl restart postgresqlNGINX Installation
NGINX will serve as a reverse proxy for Mattermost, handling SSL termination and providing an additional security layer:
sudo dnf install -y nginxConfigure NGINX to start automatically on system boot:
sudo systemctl enable nginx
sudo systemctl start nginxMattermost Installation
With dependencies in place, we can now install the Mattermost server itself.
Downloading Binaries
Obtain the latest Mattermost release package from the official download page:
cd /tmp
wget https://releases.mattermost.com/10.7.0/mattermost-10.7.0-linux-amd64.tar.gzVerify the integrity of the downloaded file with SHA-256 checksum:
sha256sum mattermost-*.tar.gzCompare this value with the official checksum provided on the Mattermost downloads page for security verification.
File Extraction & Permissions
Extract the archive and move files to the installation location:
tar -xvf mattermost-*.tar.gz
sudo mv mattermost /optCreate a dedicated system user and group for running Mattermost securely:
sudo useradd --system --user-group mattermostCreate the data directory for storing files, images, and attachments:
sudo mkdir -p /opt/mattermost/dataSet appropriate ownership and permissions:
sudo chown -R mattermost:mattermost /opt/mattermost
sudo chmod -R g+w /opt/mattermostProper permission configuration is critical for security while allowing Mattermost to function correctly.
Configuration
Proper configuration ensures your Mattermost server operates efficiently and securely.
config.json Modifications
The main configuration file for Mattermost is located at /opt/mattermost/config/config.json. Create a backup before making changes:
sudo cp /opt/mattermost/config/config.json /opt/mattermost/config/config.defaults.jsonEdit the configuration file:
sudo nano /opt/mattermost/config/config.jsonAt minimum, make the following changes:
1. Configure database connection:
"SqlSettings": {
"DriverName": "postgres",
"DataSource": "postgres://mmuser:your_secure_password@localhost:5432/mattermost?sslmode=disable&connect_timeout=10"
}2. Configure site URL (replace with your actual domain):
"ServiceSettings": {
"SiteURL": "https://mattermost.yourdomain.com"
}3. Set support email for user assistance:
"SupportSettings": {
"SupportEmail": "admin@yourdomain.com"
}Remember to replace the placeholder values with your actual configuration details.
System User Configuration
Ensure the Mattermost service runs with appropriate system privileges. We’ve already created the mattermost user earlier, but it’s important to verify that all directories maintain proper ownership:
sudo chown -R mattermost:mattermost /opt/mattermostThis prevents Mattermost from running with excessive privileges while ensuring it can access all needed files.
Systemd Service Setup
Creating a systemd service enables automatic startup of Mattermost and proper service management.
Create a service file for Mattermost:
sudo nano /etc/systemd/system/mattermost.serviceAdd the following configuration:
[Unit]
Description=Mattermost
After=network.target postgresql.service
[Service]
Type=notify
User=mattermost
Group=mattermost
ExecStart=/opt/mattermost/bin/mattermost
TimeoutStartSec=3600
Restart=always
RestartSec=10
WorkingDirectory=/opt/mattermost
LimitNOFILE=49152
[Install]
WantedBy=multi-user.targetEnable and start the Mattermost service:
sudo systemctl daemon-reload
sudo systemctl enable mattermost
sudo systemctl start mattermostVerify the service is running properly:
sudo systemctl status mattermostThis should show “active (running)” if everything is configured correctly.
Security Hardening
Proper security measures protect your Mattermost instance from unauthorized access and potential vulnerabilities.
Firewall Configuration
CentOS Stream 10 uses firewalld as its default firewall management tool. Configure it to allow HTTP/HTTPS traffic:
sudo firewall-cmd --permanent --add-service=http
sudo firewall-cmd --permanent --add-service=https
sudo firewall-cmd --reloadTo verify your firewall configuration:
sudo firewall-cmd --list-allSELinux Policies
CentOS Stream 10 enables SELinux by default, which provides additional security through mandatory access controls. Configure the appropriate contexts for Mattermost:
sudo semanage fcontext -a -t httpd_sys_content_t "/opt/mattermost(/.*)?"
sudo restorecon -Rv /opt/mattermostAdditionally, allow NGINX to act as a reverse proxy:
sudo setsebool -P httpd_can_network_connect 1These SELinux policies provide an additional security layer while allowing Mattermost to function correctly.
SSL Configuration
Encrypting traffic to your Mattermost server is essential for security. Let’s Encrypt provides free SSL certificates that are widely trusted.
Let’s Encrypt Certificates
First, install the Certbot tool for Let’s Encrypt:
sudo dnf install -y certbot python3-certbot-nginxObtain an SSL certificate for your domain:
sudo certbot --nginx -d mattermost.yourdomain.comFollow the interactive prompts to complete the process. Certbot will automatically configure NGINX to use the new certificate and set up renewal.
Verify automatic renewal works correctly:
sudo certbot renew --dry-runA successful test ensures your certificates will renew automatically before expiration.
Reverse Proxy Setup
A reverse proxy provides additional security and performance benefits by handling client connections and forwarding requests to Mattermost.
NGINX Configuration
Create a dedicated configuration file for your Mattermost site:
sudo nano /etc/nginx/conf.d/mattermost.confAdd the following configuration, replacing “mattermost.yourdomain.com” with your actual domain:
server {
listen 80;
server_name mattermost.yourdomain.com;
# Redirect HTTP to HTTPS
return 301 https://$server_name$request_uri;
}
server {
listen 443 ssl http2;
server_name mattermost.yourdomain.com;
# SSL configuration
ssl_certificate /etc/letsencrypt/live/mattermost.yourdomain.com/fullchain.pem;
ssl_certificate_key /etc/letsencrypt/live/mattermost.yourdomain.com/privkey.pem;
ssl_session_timeout 1d;
ssl_protocols TLSv1.2 TLSv1.3;
ssl_prefer_server_ciphers off;
ssl_session_cache shared:SSL:10m;
# Security headers
add_header Strict-Transport-Security "max-age=63072000" always;
add_header X-Content-Type-Options nosniff;
add_header X-Frame-Options DENY;
add_header X-XSS-Protection "1; mode=block";
# Proxy settings
location / {
proxy_pass http://127.0.0.1:8065;
proxy_http_version 1.1;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection "upgrade";
proxy_set_header Host $http_host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header X-Frame-Options SAMEORIGIN;
proxy_buffers 256 16k;
proxy_buffer_size 16k;
client_max_body_size 50M;
}
}Test and reload the NGINX configuration:
sudo nginx -t
sudo systemctl reload nginxSMTP Email Configuration
Email notifications are crucial for user engagement in Mattermost. Setting up SMTP enables account verification, password resets, and notifications.
Install Postfix for local mail delivery:
sudo dnf install -y postfix
sudo systemctl enable postfix
sudo systemctl start postfixUpdate your Mattermost configuration to use the SMTP server:
sudo nano /opt/mattermost/config/config.jsonAdd the following email configuration:
"EmailSettings": {
"EnableSignUpWithEmail": true,
"EnableSignInWithEmail": true,
"SendEmailNotifications": true,
"RequireEmailVerification": true,
"FeedbackName": "Mattermost Notifications",
"FeedbackEmail": "noreply@yourdomain.com",
"SMTPUsername": "your-smtp-username",
"SMTPPassword": "your-smtp-password",
"SMTPServer": "smtp.yourmailprovider.com",
"SMTPPort": "587",
"ConnectionSecurity": "STARTTLS",
"EnableSMTPAuth": true
}Restart Mattermost to apply the changes:
sudo systemctl restart mattermostPost-Installation Tasks
After successful installation, complete these additional steps to finalize your Mattermost deployment.
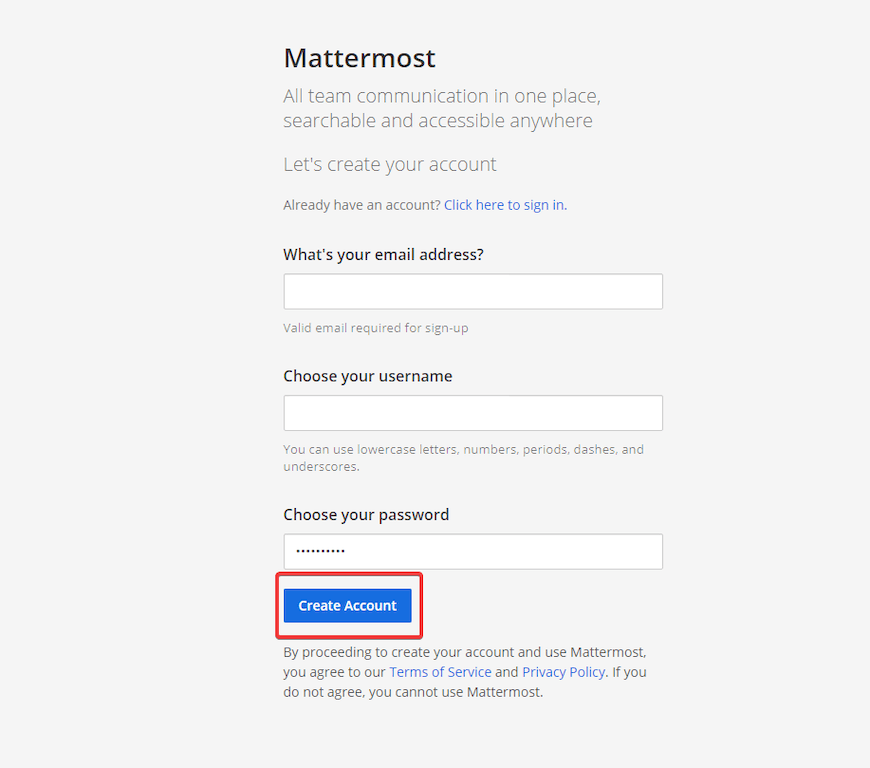
Admin Account Creation
Access your Mattermost installation through your web browser at https://mattermost.yourdomain.com. You’ll be guided through the initial setup process:
- Create the first system administrator account
- Configure team settings
- Set up notification preferences
This first account has full administrative privileges, so secure it with a strong password and consider enabling multi-factor authentication.
Team Configuration
Create and organize teams based on your organizational structure:
- Navigate to System Console > User Management > Teams
- Click “Create New Team”
- Configure team-specific settings, including membership restrictions and default channels
Consider creating a welcome guide in the default channel to help users get started.
Backup Strategy
Implement a regular backup strategy to protect your Mattermost data:
# Database backup
pg_dump -U postgres mattermost > mattermost_db_backup_$(date +%Y%m%d).sql
# File data backup
sudo tar -czf mattermost_data_backup_$(date +%Y%m%d).tar.gz /opt/mattermost/data
# Configuration backup
sudo cp /opt/mattermost/config/config.json mattermost_config_backup_$(date +%Y%m%d).jsonStore these backups securely, preferably on a separate system or cloud storage.
Troubleshooting
Even with careful installation, issues may arise. Here are solutions to common Mattermost problems.
Service Startup Issues
If Mattermost fails to start, check the logs:
sudo journalctl -u mattermost --since "1 hour ago"Common issues include:
- Database connection problems: Verify PostgreSQL is running (
sudo systemctl status postgresql) and connection details are correct in config.json - Permission errors: Ensure proper ownership of the /opt/mattermost directory
- Port conflicts: Verify no other service is using port 8065
Database Connection Errors
For database connectivity issues:
# Verify PostgreSQL is running
sudo systemctl status postgresql
# Check database permissions
sudo -u postgres psql -c "\l" | grep mattermostEnsure the pg_hba.conf file allows connections from Mattermost.
Log Analysis
Mattermost logs contain valuable troubleshooting information:
sudo tail -f /opt/mattermost/logs/mattermost.logFor more detailed logging:
- Navigate to System Console > Environment > Logging
- Change File Log Level to DEBUG temporarily
- Reproduce the issue
- Return log level to INFO after troubleshooting
This provides comprehensive information about the specific problem you’re experiencing.
Congratulations! You have successfully installed Mattermost. Thanks for using this tutorial for installing Mattermost on your CentOS Stream 10 system. For additional help or useful information, we recommend you check the official Mattermost website.