How To Install Monitorix on CentOS Stream 10

System monitoring plays a crucial role in maintaining server performance and identifying potential issues before they impact operations. Monitorix stands out as a lightweight, open-source monitoring solution that provides comprehensive system insights through an intuitive web interface. This powerful tool monitors everything from CPU usage and memory allocation to network traffic and service availability, making it an excellent choice for administrators managing CentOS Stream 10 servers.
Unlike resource-intensive monitoring solutions, Monitorix operates efficiently with minimal system overhead while delivering detailed performance metrics. The tool generates beautiful graphs using RRDtool and presents them through a built-in web server, eliminating the need for complex external dependencies. Whether you’re managing a production server or monitoring embedded devices, Monitorix adapts to various environments seamlessly.
This comprehensive guide walks you through every step of installing and configuring Monitorix on CentOS Stream 10. You’ll learn to set up dependencies, configure the monitoring system, manage services, and troubleshoot common issues. By the end of this tutorial, you’ll have a fully functional monitoring system providing real-time insights into your server’s performance.
Understanding Monitorix Architecture
Monitorix employs a simple yet effective architecture consisting of two primary components. The monitorix daemon serves as the data collector, running continuously as a system service to gather performance metrics from various sources. This Perl-based daemon operates silently in the background, consuming minimal resources while maintaining comprehensive monitoring coverage.
The second component, monitorix.cgi, handles the web interface presentation. This CGI script processes requests from the built-in HTTP server and generates the graphical displays users interact with. The built-in HTTP server listens on port 8080 by default, providing immediate access to monitoring data without requiring additional web server configuration.
Data collection occurs at regular intervals, with information stored in RRD (Round Robin Database) format. This storage method maintains fixed-size databases that automatically manage historical data retention. The system generates graphs dynamically, allowing users to view statistics across different time periods including daily, weekly, monthly, and yearly views.
The architecture supports extensive customization through a single configuration file located at /etc/monitorix/monitorix.conf. This centralized approach simplifies management while providing granular control over monitoring parameters. The modular design enables selective monitoring of specific services and system components based on your requirements.
Prerequisites and System Requirements
Before installing Monitorix on CentOS Stream 10, ensure your system meets the necessary requirements. A fresh CentOS Stream 10 installation provides the ideal foundation, minimizing potential conflicts with existing software configurations. The system should have at least 512MB of RAM, though 1GB or more is recommended for optimal performance when monitoring multiple services.
Administrative privileges are essential for installation and configuration tasks. You’ll need either root access or a user account with sudo privileges to execute system-level commands. SSH access to the server is required for remote installations, though local terminal access works equally well for desktop environments.
Network connectivity is crucial for downloading packages from repositories and accessing the web interface remotely. Ensure your system can reach external package repositories and that firewall rules don’t block necessary communication ports. The EPEL (Extra Packages for Enterprise Linux) repository must be accessible, as Monitorix packages are distributed through this channel.
Hardware requirements remain minimal due to Monitorix’s lightweight design. A modern CPU with at least one core handles the monitoring tasks efficiently. Storage requirements depend on retention periods and the number of monitored services, but typically require less than 100MB for basic configurations. Network bandwidth impact is negligible since data collection occurs locally.
Installing Required Dependencies
CentOS Stream 10 requires several dependencies before Monitorix installation can proceed. Begin by enabling the EPEL repository, which provides access to additional packages not included in the base distribution. Execute the following command to install EPEL:
sudo dnf install epel-releaseUpdate your system packages to ensure compatibility with the latest software versions:
sudo dnf update -yInstall the essential Perl dependencies required by Monitorix. These packages provide the foundation for data collection, graph generation, and web interface functionality:
sudo dnf install rrdtool rrdtool-perl perl-libwww-perl perl-MailTools perl-CGI perl-DBI perl-XML-Simple perl-Config-General perl-IO-Socket-SSL perl-HTTP-Server-Simple wgetAdditional Perl modules enhance Monitorix functionality. Install these supplementary packages for comprehensive monitoring capabilities:
sudo dnf install perl-LWP-Protocol-https perl-LWP-Protocol-http10 perl-MIME-LiteVerify the installation of critical dependencies by checking their versions. RRDtool is particularly important as it handles all graph generation tasks. Confirm its installation with:
rrdtool --versionIf any dependency installation fails, check your network connectivity and repository configuration. Some packages may have different names in CentOS Stream 10 compared to earlier versions. Use dnf search to locate alternative package names if needed.
Installing Monitorix Package
With dependencies in place, proceed to install the Monitorix package from the EPEL repository. The installation process is straightforward using dnf:
sudo dnf install monitorixVerify the installation completed successfully by checking the installed version:
monitorix -vThis command displays the version information and confirms Monitorix is properly installed on your system. The output should show version details along with the installation date.
Examine the default installation directory structure to understand file locations. Monitorix creates several important directories during installation:
/etc/monitorix/– Configuration files/var/lib/monitorix/– Database and temporary files/usr/share/monitorix/– Web interface files/var/log/monitorix/– Log files
Check file permissions to ensure proper access rights. The monitorix user account should have appropriate permissions to read configuration files and write to data directories. Incorrect permissions can prevent the service from starting or collecting data properly.
If installation fails, verify EPEL repository availability and your system’s package manager configuration. Network connectivity issues or repository mirror problems can cause installation failures. Try refreshing the package database with sudo dnf makecache before retrying the installation.
Initial Configuration Setup
Monitorix configuration relies on a single text file that controls all monitoring aspects. Before making changes, create a backup of the default configuration:
sudo cp /etc/monitorix/monitorix.conf /etc/monitorix/monitorix.conf.backupOpen the configuration file for editing using your preferred text editor:
sudo nano /etc/monitorix/monitorix.confBegin by customizing basic identification parameters. Set a descriptive title that appears in the web interface:
title = Your Server Monitorix DashboardConfigure the hostname parameter to reflect your server’s identity:
hostname = server.yourdomain.comThe built-in HTTP server configuration requires attention for proper remote access. Locate the httpd_builtin section and verify the following settings:
<httpd_builtin>
enabled = y
host = 0.0.0.0
port = 8080
user = nobody
group = nobody
</httpd_builtin>Setting the host to 0.0.0.0 allows connections from any IP address. For security, consider specifying your server’s IP address instead. The default port 8080 works well unless conflicts exist with other services.
Configure access control to restrict monitoring dashboard access. The hosts_allow and hosts_deny parameters control which IP addresses can connect:
hosts_allow = 192.168.1.0/24, 10.0.0.0/8
hosts_deny = allThis configuration permits access from local network ranges while blocking all other connections. Adjust these settings according to your network topology and security requirements.
Service Management and Startup
After configuration, start the Monitorix service to begin data collection. CentOS Stream 10 uses systemd for service management, making the process straightforward:
sudo systemctl start monitorixEnable automatic startup on system boot to ensure monitoring continues after server restarts:
sudo systemctl enable monitorixVerify the service is running correctly by checking its status:
sudo systemctl status monitorixA successful start displays active status with recent log entries. The service should show as “active (running)” with no error messages. If the service fails to start, examine the error messages for troubleshooting guidance.
Confirm Monitorix is listening on the configured port using netstat or ss:
sudo ss -tlnp | grep 8080This command should show the Monitorix process listening on port 8080. If no output appears, check the configuration file for errors or service startup issues.
Monitor the service logs for any warnings or errors during initial startup:
sudo journalctl -u monitorix -fThe logs provide valuable information about the service’s operation and can help identify configuration problems or missing dependencies.
Firewall Configuration
CentOS Stream 10 includes firewalld by default, which may block access to the Monitorix web interface. Check the current firewall status:
sudo firewall-cmd --stateIf firewalld is active, configure it to allow connections on port 8080:
sudo firewall-cmd --add-port=8080/tcp --permanent
sudo firewall-cmd --reloadVerify the rule was added successfully:
sudo firewall-cmd --list-portsFor enhanced security, consider restricting access to specific IP addresses or networks instead of opening the port globally:
sudo firewall-cmd --add-rich-rule='rule family="ipv4" source address="192.168.1.0/24" port protocol="tcp" port="8080" accept' --permanent
sudo firewall-cmd --reloadThis rule allows access only from the 192.168.1.0/24 network range. Adjust the source address to match your network configuration.
SELinux may also restrict Monitorix operation. If graphs don’t appear or error messages mention access denied to RRD database files, check SELinux status:
sestatusTemporarily set SELinux to permissive mode for testing:
sudo setenforce 0If this resolves the issue, create appropriate SELinux policies rather than permanently disabling SELinux. Consult the SELinux documentation for creating custom policies for Monitorix.
Accessing the Web Interface
With the service running and firewall configured, access the Monitorix web interface through your browser. Navigate to:
http://your-server-ip:8080/monitorixFor local access, use:
http://localhost:8080/monitorixThe initial page displays a simple interface with navigation options for different monitoring categories. Don’t expect immediate graph data – Monitorix requires several minutes to collect initial data points before generating meaningful graphs.
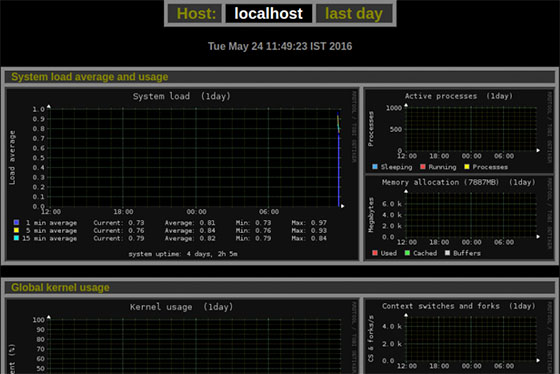
The web interface organizes monitoring data into logical categories including system load, disk usage, network activity, and service statistics. Each category contains multiple graphs showing different aspects of system performance over various time periods.
Navigation is intuitive with dropdown menus allowing selection of specific time ranges from hours to years. The interface supports zooming into specific time periods for detailed analysis of performance trends or anomalies.
If the web interface doesn’t load, verify the service is running, firewall rules are correct, and no network connectivity issues exist. Check browser console for JavaScript errors that might indicate compatibility issues.
Graph Configuration and Customization
Monitorix offers extensive graph customization options through its configuration file. Different monitoring modules can be enabled or disabled based on your requirements. This selective approach reduces resource usage and focuses on relevant metrics.
The system module monitors basic system statistics including CPU usage, memory allocation, and load averages. Enable detailed per-CPU monitoring for multi-core systems:
<system>
enabled = y
detail = 2
</system>Network monitoring tracks traffic on up to 10 network interfaces. Configure specific interfaces to monitor:
<network>
enabled = y
list = eth0, eth1
</network>Filesystem monitoring provides disk usage and I/O statistics for mounted filesystems. Specify which filesystems to monitor:
<fs>
enabled = y
list = /, /home, /var
</fs>Service monitoring tracks various system services including SSH, HTTP, FTP, and database servers. Enable monitoring for services running on your system:
<port>
enabled = y
list = 22, 80, 443, 3306
</port>Temperature monitoring requires compatible hardware and sensors. Enable if your system supports hardware monitoring:
<system>
temp_scale = c
</system>Graph appearance can be customized including colors, sizing, and layout options. Adjust these settings based on your preferences and display requirements.
Advanced Configuration Options
Advanced users can leverage Monitorix’s sophisticated features for comprehensive monitoring environments. Email notifications provide alerts when specific thresholds are exceeded. Configure SMTP settings in the configuration file:
<emailreports>
enabled = y
smtp_hostname = mail.yourdomain.com
from_address = monitorix@yourdomain.com
to_address = admin@yourdomain.com
</emailreports>Multi-server monitoring allows centralized monitoring of multiple systems. Configure the multihost feature to collect data from remote servers:
<multihost>
enabled = y
list = server1.domain.com, server2.domain.com
</multihost>Integration with external web servers like Apache or Nginx provides additional flexibility. Configure reverse proxy settings to serve Monitorix through standard HTTP ports while maintaining security.
Database retention policies control how long historical data is preserved. Adjust these settings based on storage capacity and analysis requirements:
<rrdtool>
default_rows = 2016
default_steps = 300
</rrdtool>Custom graph creation allows monitoring of specific applications or services not covered by default modules. Create custom scripts to collect data and integrate with Monitorix’s RRDtool framework.
Troubleshooting Common Issues
Service startup failures often result from configuration errors or missing dependencies. Check the service logs for specific error messages:
sudo journalctl -u monitorix --no-pagerConfiguration file syntax errors prevent service startup. Validate the configuration file syntax:
sudo monitorix -c /etc/monitorix/monitorix.conf -tEmpty graphs or missing data indicate collection problems. Verify file permissions on the data directory:
sudo ls -la /var/lib/monitorix/The monitorix user must have read/write access to this directory. Correct permissions if necessary:
sudo chown -R monitorix:monitorix /var/lib/monitorix/Network connectivity issues prevent remote access to the web interface. Test connectivity from client machines:
telnet server-ip 8080High CPU usage may indicate inefficient monitoring configurations. Review enabled modules and reduce monitoring frequency if necessary. Disable unnecessary graphs to reduce system load.
SELinux violations appear in audit logs when access is denied. Check for SELinux-related errors:
sudo ausearch -m avc -ts recentCreate appropriate SELinux policies or temporarily set permissive mode for testing purposes.
Security Best Practices
Securing Monitorix involves multiple layers of protection starting with network access control. Implement firewall rules that restrict access to authorized IP addresses only. Avoid exposing the monitoring interface to public networks without additional security measures.
HTTPS encryption protects data transmission between browsers and the monitoring interface. Configure a reverse proxy with SSL certificates to encrypt communications:
sudo dnf install nginxCreate an Nginx configuration that proxies requests to Monitorix while providing SSL termination. This approach maintains security while preserving functionality.
Authentication mechanisms prevent unauthorized access to monitoring data. Configure basic authentication through the web server or implement more sophisticated authentication systems integrated with existing user management infrastructure.
Regular security updates ensure protection against newly discovered vulnerabilities. Monitor security advisories for Monitorix and its dependencies:
sudo dnf check-update monitorixFile system permissions should follow the principle of least privilege. Regularly audit file permissions and ownership to ensure appropriate access controls remain in place.
Log monitoring provides visibility into access patterns and potential security incidents. Review Monitorix logs regularly for suspicious activity patterns or unauthorized access attempts.
Maintenance and Updates
Regular maintenance ensures optimal Monitorix performance and security. Update the software periodically to receive bug fixes and security patches:
sudo dnf update monitorixMonitor disk space usage in the data directory as RRD databases can grow over time. Implement log rotation policies to manage disk space efficiently:
sudo logrotate -f /etc/logrotate.d/monitorixConfiguration backups protect against accidental modifications or system failures. Maintain regular backups of the configuration file and custom modifications:
sudo cp /etc/monitorix/monitorix.conf /backup/monitorix-$(date +%Y%m%d).confPerformance monitoring of the monitoring system itself prevents resource exhaustion. Review system resource usage periodically and adjust monitoring scope if necessary.
Database maintenance may be required for long-running installations. RRDtool databases are generally self-maintaining, but periodic verification ensures data integrity:
sudo -u monitorix rrdtool dump /var/lib/monitorix/system.rrd > /dev/nullService restart procedures should be documented and tested regularly. Plan maintenance windows for updates that require service interruption.
Congratulations! You have successfully installed Monitorix. Thanks for using this tutorial for installing the Monitorix network monitoring tool on CentOS Stream 10 systems. For additional help or useful information, we recommend you check the official Monitorix website.