How To Install Monitorix on Fedora 42

Monitorix stands as one of the most powerful yet lightweight monitoring solutions for Linux systems, providing comprehensive insights into system performance and network resources. For Fedora 42 users seeking a reliable monitoring tool with minimal resource consumption, Monitorix offers an excellent solution with its rich visualization capabilities and extensive customization options. This guide walks you through the complete process of installing, configuring, and optimizing Monitorix on Fedora 42, ensuring you can leverage its full potential to monitor your system effectively.
Introduction
Monitorix is a free, open-source system monitoring tool designed to track and visualize a wide range of system and network resources in Linux environments. It operates with minimal system overhead while providing comprehensive monitoring capabilities through an intuitive web interface. Originally developed for Red Hat-based distributions like Fedora, Monitorix has become a go-to solution for system administrators who need detailed insights into their systems’ performance.
In Fedora 42, Monitorix version 3.16.0-2.fc42 is available through the official repositories, making installation straightforward. This tool collects data on system metrics such as CPU usage, memory utilization, disk activity, network traffic, and many other parameters, presenting this information in easily digestible graphs.
By the end of this guide, you’ll have a fully functional Monitorix installation on your Fedora 42 system, configured to meet your specific monitoring needs. Whether you’re managing a production server or simply want to keep tabs on your workstation’s performance, Monitorix provides the visibility you need with minimal configuration effort.
Understanding Monitorix
Core Functionality and Architecture
Monitorix functions as a comprehensive monitoring solution that collects, analyzes, and visualizes system performance data. It operates through two main components: the monitorix daemon and the monitorix.cgi script. The daemon runs continuously in the background, collecting performance metrics at regular intervals and storing them in RRD (Round Robin Database) files. The CGI script generates the graphs and web interface that displays this collected data in a user-friendly format.
Since version 3.0, Monitorix has included its own built-in HTTP server, eliminating the need for a separate web server installation. This architectural improvement simplifies deployment while maintaining the tool’s lightweight footprint.
Historical Development
Monitorix was initially developed specifically for Red Hat, Fedora, and CentOS distributions, explaining its seamless integration with Fedora 42. Over time, it has evolved from its 1.x version to the current 3.x architecture, expanding its capabilities and improving its performance. This evolution has transformed Monitorix from a basic monitoring tool to a comprehensive solution capable of tracking diverse system parameters across various Linux distributions.
Monitoring Capabilities
The monitoring capabilities of Monitorix are extensive, including:
- System load and resource utilization
- Detailed CPU metrics and performance
- Memory usage and management
- Swap activity and virtual memory statistics
- Storage device I/O operations
- Filesystem usage and status
- Network interface traffic and statistics
- Network service activity monitoring
- System temperatures and sensor readings
- Process activity and resource consumption
- User activity and login statistics
This comprehensive range of monitoring parameters makes Monitorix an invaluable tool for system administrators who need detailed insights into their systems’ performance characteristics.
System Requirements for Fedora 42
Before installing Monitorix on Fedora 42, ensure your system meets the minimum requirements for optimal performance. Although Monitorix is designed to be lightweight, proper resource allocation ensures smooth operation, particularly for systems under constant monitoring.
Hardware Requirements
For effective monitoring with Monitorix, your Fedora 42 system should ideally have:
- CPU: Any modern processor (single core is sufficient, though multi-core improves performance when monitoring numerous parameters)
- RAM: Minimum 512MB, recommended 1GB or more for extensive monitoring
- Disk space: At least 500MB for installation and initial database storage; additional space needed as monitoring data accumulates over time
- Network connectivity: Required if monitoring remote systems or accessing the web interface from other machines
Software Compatibility
Monitorix is fully compatible with Fedora 42 and requires several dependencies that are typically available through the standard repositories:
- Perl 5.10 or higher (included in base Fedora installation)
- RRDtool and Perl bindings
- Various Perl modules including libwww-perl, MailTools, and XML-Simple
- Basic system utilities included in standard Fedora installations
Environment Considerations
For production environments, allocate additional resources based on the scope of monitoring:
- Increase disk space allocation if planning to maintain long-term historical data
- Consider memory requirements if monitoring numerous services simultaneously
- Adjust network settings if Monitorix will be accessed by multiple users or remote systems
With these requirements satisfied, your Fedora 42 system is ready for Monitorix installation, providing a solid foundation for comprehensive system monitoring.
Pre-Installation Steps
Proper preparation ensures a smooth Monitorix installation process. Complete these essential pre-installation steps to create an optimal environment for your monitoring system.
Update Your Fedora 42 System
Start by ensuring your Fedora 42 system has the latest updates installed. This minimizes potential compatibility issues and ensures security patches are applied:
sudo dnf check-update
sudo dnf upgrade --refreshAfter updating, restart your system if kernel updates were applied:
sudo systemctl rebootCheck for Potential Conflicts
If you’re already using monitoring tools like Nagios, Zabbix, or Prometheus, verify they won’t conflict with Monitorix, particularly regarding port usage:
sudo netstat -tulpn | grep 8080If another service is already using port 8080 (Monitorix’s default port), note this for later configuration adjustments.
Set Up Appropriate User Permissions
Ensure your user account has sudo privileges to perform the installation:
sudo whoamiThis command should return “root”, confirming proper sudo access.
Back Up Important System Files
Before making system changes, back up configuration files that might be modified:
sudo mkdir -p /root/backups/pre-monitorix
sudo cp -r /etc/httpd/conf.d/ /root/backups/pre-monitorix/ 2>/dev/null || trueVerify Firewall Settings
Check your current firewall settings and ensure port 8080 will be accessible if you plan to access Monitorix remotely:
sudo firewall-cmd --list-allIf needed, configure the firewall to allow access to port 8080:
sudo firewall-cmd --permanent --add-port=8080/tcp
sudo firewall-cmd --reloadVerify SELinux Status
SELinux can sometimes interfere with Monitorix operations. Check its current status:
getenforceIf SELinux is in enforcing mode, you may need to create appropriate policies later or temporarily set it to permissive mode during troubleshooting.
Installation Methods
Fedora 42 offers multiple approaches to install Monitorix, with the official repository method being the simplest and most reliable. This section details the various installation methods available, allowing you to choose the one that best suits your requirements.
Official Repository Installation
The recommended method for installing Monitorix on Fedora 42 is through the official repositories, providing a straightforward process with automatic dependency management.
Step 1: Install Monitorix package
Execute the following command to install Monitorix and its core dependencies:
sudo dnf install monitorixThe system will display the packages to be installed and their dependencies. Confirm the installation when prompted.
Step 2: Verify the installation
After installation completes, verify that Monitorix was installed correctly:
rpm -q monitorixThis should display the installed version, confirming successful installation.
Step 3: Check for missing dependencies
Ensure all required dependencies are installed:
sudo dnf install perl-CGI perl-HTTP-Server-Simple perl-rrdtool perl-Config-General perl-LWP-Protocol-https perl-MIME-Lite perl-DBI perl-XML-SimpleThis comprehensive approach ensures all potential dependencies are available, even those not automatically installed during the initial process.
Alternative Installation Methods
While the official repository method is recommended, alternative approaches may be necessary in certain scenarios.
Manual RPM Installation
If you need a specific version not available in the repositories:
- Download the desired Monitorix RPM package from the official website:
wget https://www.monitorix.org/rpm/monitorix-[version].rpm - Install the downloaded package:
sudo dnf install ./monitorix-[version].rpm - Resolve dependencies manually if needed:
sudo dnf install -f
Building from Source
For advanced users requiring customization or the latest development version:
- Install development tools and dependencies:
sudo dnf install git perl-devel rrdtool-devel gcc make - Clone the repository:
git clone https://github.com/mikaku/monitorix.git - Navigate to the source directory:
cd monitorix - Configure and install:
./configure --prefix=/usr make sudo make install
Required Dependencies
Monitorix relies on several dependencies to function properly. This section provides a comprehensive overview of these dependencies and guides you through their installation and verification process on Fedora 42.
Core Dependencies
The following packages are essential for Monitorix’s basic functionality:
- Perl and Perl modules: Monitorix is written in Perl and requires several modules
- RRDtool: Responsible for creating and maintaining the round-robin databases that store monitoring data
- HTTP-Server-Simple: Powers the built-in web server functionality
- CGI module: Enables the web interface to display monitoring data
Installing Dependencies
Execute the following command to install all required dependencies in one step:
sudo dnf install perl perl-libwww-perl perl-MailTools perl-MIME-Lite perl-CGI perl-DBI perl-XML-Simple perl-Config-General perl-HTTP-Server-Simple rrdtool perl-rrdtool perl-IO-Socket-SSL perl-LWP-Protocol-httpsThis comprehensive command ensures all necessary components are installed, preventing potential issues during Monitorix operation.
Optional Dependencies
Depending on your monitoring needs, additional packages may enhance Monitorix functionality:
For email notifications:
sudo dnf install perl-Net-SMTP-SSL perl-Authen-SASLFor MySQL/MariaDB monitoring:
sudo dnf install perl-DBD-MySQLFor temperature monitoring:
sudo dnf install lm_sensorsAfter installing lm_sensors, configure it for your hardware:
sudo sensors-detectFollow the on-screen prompts to detect and configure sensor monitoring.
Verifying Dependencies
To ensure all dependencies are correctly installed and functional, perform these verification steps:
- Verify Perl modules:
perl -e 'use CGI; use RRDs; use HTTP::Server::Simple; print "All required modules are installed.\n"'If no error messages appear, the required Perl modules are available.
- Check RRDtool functionality:
rrdtool --versionThis should display the installed RRDtool version.
- Confirm HTTP server capability:
perl -MHTTP::Server::Simple -e 'print "HTTP::Server::Simple version: $HTTP::Server::Simple::VERSION\n"'
Basic Configuration
After installation, Monitorix requires configuration to match your system specifications and monitoring requirements. The main configuration file contains numerous options that control Monitorix’s behavior, data collection, and presentation.
Understanding the Configuration File
Monitorix’s primary configuration file is located at /etc/monitorix/monitorix.conf. Before making changes, create a backup:
sudo cp /etc/monitorix/monitorix.conf /etc/monitorix/monitorix.conf.backupThe configuration file is structured into logical sections, each controlling different aspects of Monitorix’s functionality:
- Global settings: Controls basic behavior, appearance, and performance parameters
- Module configurations: Enables/disables specific monitoring modules
- Graph settings: Controls the appearance and behavior of graphs
- Alert configurations: Defines thresholds and notification methods
Essential Configuration Parameters
Open the configuration file for editing:
sudo nano /etc/monitorix/monitorix.confModify these essential parameters to customize your Monitorix installation:
Basic Settings
title = My Fedora 42 Server
hostname = fedora42.example.com
theme_color = black
refresh_rate = 150
iface_mode = graph
enable_zoom = yReplace “My Fedora 42 Server” with your preferred title and “fedora42.example.com” with your actual hostname.
Port Configuration
If port 8080 conflicts with another service, change the port setting:
port = 8081Network Interface Settings
Configure the network interfaces to monitor:
<graph_enable>
...
net = y
...
</graph_enable>
<net>
list = eth0, wlan0
...
</net>Replace “eth0, wlan0” with your actual interface names, which can be determined using:
ip addr show | grep -E '^[0-9]+: ' | awk -F': ' '{print $2}'Filesystem Monitoring
Configure filesystem monitoring:
<graph_enable>
...
fs = y
...
</graph_enable>
<fs>
list = /, /home, /var
...
</fs>Replace “/”, “/home”, “/var” with the filesystems you want to monitor.
Using Man Pages for Reference
Fedora 42 includes comprehensive man pages for Monitorix configuration:
man monitorix.confThis command displays detailed information about all available configuration options, providing valuable reference during the configuration process.
After completing your configuration changes, save the file and restart Monitorix to apply the changes:
sudo systemctl restart monitorixAdvanced Configuration Options
Beyond basic setup, Monitorix offers extensive advanced configuration options for tailoring the monitoring system to specialized requirements. These advanced settings enable precise control over monitoring parameters, graph appearance, and data collection behavior.
Customizing Graphs and Monitored Services
Monitorix provides granular control over which services are monitored and how their data is displayed:
Enable/Disable Specific Graphs
Edit the <graph_enable> section to activate only the modules you need:
<graph_enable>
system = y
kern = y
proc = y
hptemp = n
lmsens = y
nvidia = n
disk = y
fs = y
net = y
serv = y
</graph_enable>This selective approach conserves system resources by only monitoring essential services.
Graph Appearance Settings
Customize graph visual properties in the respective service sections:
<system>
rigid = 0
limit = 100
gap_size = 0
alert_load_avg = 0
</system>rigid: Sets whether the graph has fixed upper limits (1) or scales automatically (0)limit: Defines the maximum value for rigid graphsgap_size: Controls missing data visualization (0 means data points are connected)alert_*: Sets thresholds for alerts
Filesystem Monitoring Configuration
Configure detailed filesystem monitoring with descriptive labels:
<fs>
list = /, /home, /var, /tmp
desc = Root, Home, System, Temporary
graph_mode = separate
include_regex = ^ext|^xfs|^btrfs|^zfs
alert_threshold_warning = 92
alert_threshold_critical = 98
</fs>This configuration monitors four filesystems with custom descriptions, separates them into individual graphs, includes only specific filesystem types, and sets warning thresholds at 92% and 98% usage.
Network Monitoring Settings
Fine-tune network interface monitoring:
<net>
list = enp0s3, wlp2s0
desc = LAN, Wireless
gateway = gateway
show_traffic_per_process = y
hide_mac_address = n
hide_fqdn = y
show_drops = y
</net>This configuration monitors two interfaces with custom descriptions, tracks per-process network usage, displays MAC addresses while hiding fully qualified domain names, and shows packet drops.
Email Alert Configuration
Set up automated email notifications for critical events:
<email_alert>
enabled = y
sender_address = monitorix@example.com
recipient_address = admin@example.com
subject = Monitorix Alert: $hostname
smtp_hostname = smtp.example.com
smtp_port = 587
use_tls = y
tls_ca_file = /etc/pki/tls/certs/ca-bundle.crt
username = monitorix@example.com
password = SecurePassword123
auth_method = LOGIN
compose_message = y
</email_alert>Replace placeholder values with your actual SMTP server details and credentials.
Performance Tuning Options
Optimize Monitorix’s performance for your specific environment:
enable_parallelizing = y
include_dir = /etc/monitorix/conf.d
max_processes = 8
timeout = 10
log_file = /var/log/monitorix
secure_log = /var/log/secure
syslog = /var/log/messagesThese settings enable parallel data collection with a maximum of 8 processes, set a 10-second timeout for operations, and define log file locations.
Starting and Managing the Monitorix Service
Properly managing the Monitorix service ensures reliable monitoring and data collection. This section covers the essential service management operations, including starting, stopping, enabling automatic startup, and troubleshooting service-related issues.
Starting the Service Manually
To start Monitorix immediately after installation or configuration changes:
sudo systemctl start monitorixThis command initiates the Monitorix daemon, which begins collecting and processing system data according to your configuration settings.
Enabling Automatic Startup
To ensure Monitorix starts automatically when your Fedora 42 system boots:
sudo systemctl enable monitorixThis command configures systemd to launch Monitorix during system initialization, guaranteeing continuous monitoring even after system reboots.
Checking Service Status
To verify Monitorix is running properly and review its current status:
sudo systemctl status monitorixThis command displays detailed information about the service, including:
- Whether it’s active or inactive
- How long it’s been running
- Recent log entries
- Process information
Example output of a healthy service:
● monitorix.service - Monitorix
Loaded: loaded (/usr/lib/systemd/system/monitorix.service; enabled; vendor preset: disabled)
Active: active (running) since Sat 2025-05-17 18:15:03 WIB; 17min ago
Main PID: 1234 (monitorix)
Tasks: 2 (limit: 4915)
Memory: 18.5M
CGroup: /system.slice/monitorix.service
└─1234 /usr/bin/perl /usr/bin/monitorix -c /etc/monitorix/monitorix.conf -p /var/run/monitorix.pid
May 17 18:15:03 fedora42 systemd[1]: Started Monitorix.
May 17 18:15:04 fedora42 monitorix[1234]: Starting Monitorix 3.16.0-2.fc42...Restarting After Configuration Changes
After modifying the configuration file, restart the service to apply changes:
sudo systemctl restart monitorixThis command stops the running instance and starts a fresh one with the updated configuration.
Service Management Troubleshooting
If Monitorix fails to start or operates incorrectly, use these troubleshooting approaches:
Check for startup errors:
sudo journalctl -u monitorixThis displays the complete service log, helping identify configuration or dependency issues.
Verify configuration syntax:
monitorix -c /etc/monitorix/monitorix.conf -vThe -v flag performs a validation check on your configuration file, highlighting syntax errors.
Test with foreground execution:
sudo systemctl stop monitorix
sudo monitorix -c /etc/monitorix/monitorix.conf -dThe -d flag runs Monitorix in debugging mode with foreground output, revealing detailed operational information that can help diagnose issues.
Check for port conflicts:
sudo ss -tulpn | grep $(grep ^port /etc/monitorix/monitorix.conf | awk '{print $3}')This command identifies processes using the port configured for Monitorix, potentially revealing conflicts.
Accessing the Monitorix Web Interface
After successfully installing and configuring Monitorix, accessing its web interface allows you to visualize the collected monitoring data through an intuitive, graph-based presentation.
Default Access Methods
Monitorix’s web interface is typically accessible through:
http://localhost:8080/monitorix/If accessing from another computer on the network, replace “localhost” with your server’s IP address or hostname:
http://your_server_ip:8080/monitorix/If you modified the default port in the configuration file, adjust the URL accordingly:
http://localhost:custom_port/monitorix/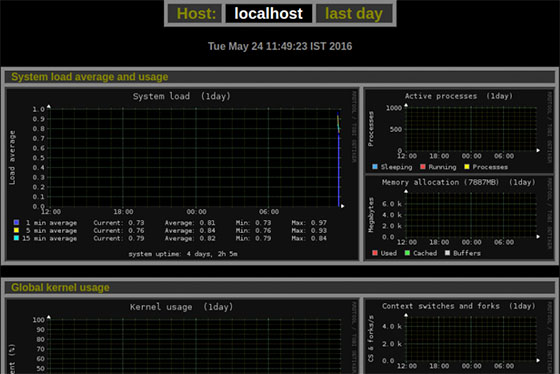
Web Interface Layout and Navigation
Upon accessing the web interface, you’ll find a well-organized monitoring dashboard with these key elements:
Main Page
The landing page displays graph categories in alphabetical order, including:
- CPU usage and system load
- Memory and swap utilization
- Network interface traffic
- Disk activity and filesystem usage
- Process statistics
- System services status
Navigation System
The interface features intuitive navigation elements:
- Category links at the top of the page for quick section access
- Daily, weekly, monthly, and yearly view options for each graph
- Interactive zoom functionality (if enabled in configuration)
- Graph-specific options for customizing the display
Understanding Graph Displays
Each graph provides valuable visual information:
- X-axis represents time intervals
- Y-axis displays the measured value
- Multiple metrics may appear on a single graph with different colors
- Hovering over graph elements displays specific values
- Clicking on a graph may provide additional details or zoom capabilities
Browser Compatibility Considerations
Monitorix’s web interface works with all modern browsers, but for optimal experience:
- Use recent versions of Firefox, Chrome, Safari, or Edge
- Enable JavaScript for full functionality
- Adjust browser zoom levels for better graph visibility on high-resolution displays
- Consider using desktop browsers for detailed analysis, as mobile browsers may not display all graph details optimally
Troubleshooting Access Issues
If you cannot access the web interface, verify:
- The Monitorix service is running:
sudo systemctl status monitorix - The configured port is open in your firewall:
sudo firewall-cmd --list-all | grep 8080If not listed, add it:
sudo firewall-cmd --permanent --add-port=8080/tcp sudo firewall-cmd --reload - No port conflicts exist:
sudo ss -tulpn | grep :8080Verify Monitorix is the process using this port.
- SELinux is not blocking access:
sudo ausearch -m avc -ts recent | grep monitorixIf SELinux issues appear, consider creating appropriate policies or temporarily setting SELinux to permissive mode:
sudo setenforce 0 # Temporary until reboot
Securing Monitorix
Properly securing your Monitorix installation is crucial, especially when deployed in production environments or when accessible over a network. This section covers essential security measures to protect your monitoring data and prevent unauthorized access.
Setting Up HTTP Authentication
By default, Monitorix’s web interface lacks authentication, potentially exposing system information. Implement HTTP Basic Authentication to require credentials:
Step 1: Create authentication file and user
sudo dnf install httpd-tools
sudo mkdir -p /etc/monitorix/auth
sudo htpasswd -c /etc/monitorix/auth/.htpasswd adminYou’ll be prompted to create and confirm a password for the “admin” user. To add more users later, omit the -c flag:
sudo htpasswd /etc/monitorix/auth/.htpasswd additional_userStep 2: Configure authentication in Monitorix
Edit the configuration file:
sudo nano /etc/monitorix/monitorix.confIn the <httpd_builtin> section, add authentication parameters:
<httpd_builtin>
...
auth = y
htpasswd = /etc/monitorix/auth/.htpasswd
...
</httpd_builtin>Step 3: Restart Monitorix to apply changes
sudo systemctl restart monitorixNow, accessing the Monitorix web interface will require authentication with your created credentials.
Implementing HTTPS for Secure Access
For sensitive environments, encrypt web traffic using HTTPS:
Step 1: Create or obtain SSL certificates
For self-signed certificates (suitable for internal use):
sudo mkdir -p /etc/monitorix/ssl
sudo openssl req -new -x509 -days 365 -nodes \
-out /etc/monitorix/ssl/monitorix.crt \
-keyout /etc/monitorix/ssl/monitorix.keyFor production environments, consider using Let’s Encrypt certificates.
Step 2: Configure HTTPS in Monitorix
Edit the configuration file:
sudo nano /etc/monitorix/monitorix.confUpdate the <httpd_builtin> section:
<httpd_builtin>
...
enabled = y
host =
port = 8443
user = nobody
group = nobody
log_file = /var/log/monitorix-httpd
hosts_deny =
hosts_allow =
ssl = y
ssl_cert_file = /etc/monitorix/ssl/monitorix.crt
ssl_key_file = /etc/monitorix/ssl/monitorix.key
...
</httpd_builtin>Step 3: Update firewall rules and restart service
sudo firewall-cmd --permanent --add-port=8443/tcp
sudo firewall-cmd --reload
sudo systemctl restart monitorixNow access Monitorix securely via:
https://your_server:8443/monitorix/Firewall Configuration Recommendations
Restrict access to the Monitorix interface by configuring firewall rules:
Allow access only from specific IP addresses:
sudo firewall-cmd --permanent --add-rich-rule='rule family="ipv4" source address="192.168.1.0/24" port port="8080" protocol="tcp" accept'
sudo firewall-cmd --permanent --remove-port=8080/tcp
sudo firewall-cmd --reloadReplace 192.168.1.0/24 with your trusted network range.
SELinux Considerations
Fedora 42 uses SELinux by default, which may restrict Monitorix operations. Address SELinux-related issues with these approaches:
Option 1: Create custom SELinux policy
sudo grep monitorix /var/log/audit/audit.log | audit2allow -M monitorix_custom
sudo semodule -i monitorix_custom.ppOption 2: Set appropriate contexts
sudo semanage fcontext -a -t httpd_sys_content_t "/var/lib/monitorix/www(/.*)?"
sudo semanage fcontext -a -t httpd_sys_rw_content_t "/var/lib/monitorix/db(/.*)?"
sudo restorecon -Rv /var/lib/monitorix/Option 3: Configure SELinux boolean settings
sudo setsebool -P httpd_can_network_connect 1Integrating with Existing Web Servers
While Monitorix comes with its own built-in web server, you may prefer to integrate it with your existing web server infrastructure. This approach offers several advantages, including unified access control, centralized SSL management, and seamless integration with your existing web applications.
Configuration with Apache
Apache is widely used on Fedora systems and offers robust integration capabilities with Monitorix:
Step 1: Install Apache if not already present
sudo dnf install httpdStep 2: Disable Monitorix’s built-in HTTP server
Edit /etc/monitorix/monitorix.conf:
sudo nano /etc/monitorix/monitorix.confIn the <httpd_builtin> section, disable the server:
<httpd_builtin>
enabled = n
...
</httpd_builtin>Step 3: Create an Apache configuration file for Monitorix
sudo nano /etc/httpd/conf.d/monitorix.confAdd the following configuration:
Alias /monitorix /var/lib/monitorix/www
<Directory /var/lib/monitorix/www/>
Options None
AllowOverride None
Require all granted
</Directory>
ScriptAlias /monitorix-cgi /var/lib/monitorix/www/cgi
<Directory /var/lib/monitorix/www/cgi/>
Options +ExecCGI
AddHandler cgi-script .cgi
AllowOverride None
Require all granted
</Directory>For secured access, add authentication:
<Directory /var/lib/monitorix/www/>
Options None
AllowOverride None
AuthType Basic
AuthName "Monitorix Access"
AuthUserFile /etc/monitorix/auth/.htpasswd
Require valid-user
</Directory>Step 4: Set SELinux contexts for Apache
sudo setsebool -P httpd_can_network_connect 1
sudo chcon -R -t httpd_sys_content_t /var/lib/monitorix/www/
sudo chcon -R -t httpd_sys_script_exec_t /var/lib/monitorix/www/cgi/Step 5: Restart services
sudo systemctl restart monitorix httpdConfiguration with Nginx
Nginx offers high performance and is increasingly popular for web hosting:
Step 1: Install Nginx and FastCGI
sudo dnf install nginx fcgiwrapStep 2: Disable Monitorix’s built-in HTTP server (as shown in the Apache section)
Step 3: Create Nginx configuration for Monitorix
sudo nano /etc/nginx/conf.d/monitorix.confAdd the following configuration:
server {
listen 80;
server_name _;
location /monitorix/ {
root /var/lib/monitorix/www/;
index index.html;
}
location /monitorix-cgi/ {
alias /var/lib/monitorix/www/cgi/;
fastcgi_pass unix:/var/run/fcgiwrap.socket;
include fastcgi_params;
fastcgi_param SCRIPT_FILENAME $request_filename;
}
}For adding authentication:
location /monitorix/ {
root /var/lib/monitorix/www/;
index index.html;
auth_basic "Monitorix Access";
auth_basic_user_file /etc/monitorix/auth/.htpasswd;
}Step 4: Set appropriate permissions
sudo chown -R nginx:nginx /var/lib/monitorix/www/
sudo chmod -R 755 /var/lib/monitorix/www/Step 5: Restart services
sudo systemctl restart monitorix nginx fcgiwrapConfiguration with Lighttpd
Lighttpd is a lightweight web server suitable for resource-constrained environments:
Step 1: Install Lighttpd
sudo dnf install lighttpd lighttpd-fastcgiStep 2: Disable Monitorix’s built-in HTTP server (as shown previously)
Step 3: Create Lighttpd configuration for Monitorix
sudo nano /etc/lighttpd/conf.d/monitorix.confAdd the following configuration:
alias.url += ( "/monitorix" => "/var/lib/monitorix/www" )
alias.url += ( "/monitorix-cgi" => "/var/lib/monitorix/www/cgi" )
$HTTP["url"] =~ "^/monitorix-cgi/" {
cgi.assign = ( ".cgi" => "/usr/bin/perl" )
}Step 4: Enable modules and restart services
sudo lighttpd-enable-mod fastcgi
sudo systemctl restart monitorix lighttpdCommon Issues and Troubleshooting
Even with careful installation and configuration, you may encounter issues with Monitorix on Fedora 42. This section addresses common problems and provides practical solutions to resolve them efficiently.
Permission Problems with RRD Databases
One of the most frequent issues involves permissions for the RRD database files that store monitoring data.
Symptoms:
- Missing or incomplete graphs
- Error messages in logs about “permission denied”
- Graphs showing no data despite the service running
Solutions:
- Check and correct permissions:
sudo ls -la /var/lib/monitorix/db/ - Set appropriate ownership:
sudo chown -R monitorix:monitorix /var/lib/monitorix/db/ - Set correct permissions:
sudo chmod -R 755 /var/lib/monitorix/db/ - Verify SELinux contexts:
sudo restorecon -Rv /var/lib/monitorix/db/
Resolving SELinux-Related Issues
SELinux can block Monitorix operations, particularly file access and network connections.
Symptoms:
- Service starts but doesn’t collect data
- Empty graphs despite correct configuration
- “Access denied” errors in audit logs
Solutions:
- Check for SELinux denials:
sudo ausearch -m AVC -ts recent | grep monitorix - Generate and apply a custom policy:
sudo grep monitorix /var/log/audit/audit.log | audit2allow -M monitorix_policy sudo semodule -i monitorix_policy.pp - Configure appropriate boolean settings:
sudo setsebool -P httpd_can_network_connect 1 sudo setsebool -P httpd_can_network_connect_db 1 - If unable to resolve specific issues, temporarily set SELinux to permissive mode for testing:
sudo setenforce 0 # Temporary until reboot
For a permanent change, edit /etc/selinux/config and set SELINUX=permissive, then reboot.
Fixing Graph Display Problems
Sometimes graphs may appear empty or display errors despite proper configuration.
Symptoms:
- Empty graphs with no data
- Error messages in the web interface
- Incomplete or corrupted graphs
Solutions:
- Verify RRD files exist and have data:
sudo ls -la /var/lib/monitorix/db/*.rrd sudo file /var/lib/monitorix/db/*.rrd - Reset problematic RRD files if corrupted:
sudo rm /var/lib/monitorix/db/problematic_file.rrd sudo systemctl restart monitorix - Check for JavaScript errors in browser console (press F12 in most browsers)
- Verify correct data collection for specific modules:
sudo grep -i error /var/log/monitorix
Troubleshooting Network Monitoring Issues
Network monitoring can be particularly challenging due to interface naming and access rights.
Symptoms:
- Missing network graphs
- Zero traffic shown despite active network usage
- Error messages about specific interfaces
Solutions:
- Verify interface names match configuration:
ip addr show - Update configuration with correct interface names:
sudo nano /etc/monitorix/monitorix.confLocate the
<net>section and update thelistparameter with your actual interface names. - Ensure Monitorix has rights to read network statistics:
sudo setcap cap_net_admin,cap_net_raw+ep /usr/bin/monitorix - For persistent failures, try disabling and re-enabling the network module:
# Edit monitorix.conf and in the <graph_enable> section: # set net = n, restart monitorix # set net = y, restart monitorix again
Debugging Service Startup Failures
If Monitorix fails to start or crashes shortly after startup, systematic debugging is required.
Symptoms:
- Service fails to start
- Service starts but quickly terminates
- Status shows “failed” or “inactive”
Solutions:
- Check service status for specific errors:
sudo systemctl status monitorix - Review journal logs:
sudo journalctl -u monitorix -n 50 - Run Monitorix manually with debugging enabled:
sudo monitorix -c /etc/monitorix/monitorix.conf -d - Verify all dependencies are installed:
sudo dnf install --skip-broken perl-CGI perl-HTTP-Server-Simple perl-rrdtool perl-Config-General perl-LWP-Protocol-https perl-MIME-Lite perl-DBI perl-XML-Simple - Check for syntax errors in configuration:
sudo monitorix -c /etc/monitorix/monitorix.conf -v
Congratulations! You have successfully installed Monitorix. Thanks for using this tutorial for installing the Monitorix monitoring tool on your Fedora 42 Linux system. For additional or useful information, we recommend you check the official Monitorix website.