How To Install Nessus Scanner on Debian 13

Vulnerability scanning has become an indispensable component of modern cybersecurity infrastructure. Organizations face increasing threats from sophisticated attacks that exploit software vulnerabilities, misconfigurations, and security weaknesses. Nessus, developed by Tenable Security, stands as one of the most trusted and widely deployed vulnerability assessment tools in the industry, trusted by security professionals worldwide to identify and assess security risks across their networks.
This comprehensive guide walks you through the complete installation and configuration process of Nessus Scanner on Debian 13 (Trixie). Whether you’re a system administrator securing enterprise infrastructure, a security analyst conducting penetration tests, or an IT professional building a vulnerability management program, this tutorial provides detailed, actionable steps to get Nessus operational on your Debian system. You’ll learn everything from downloading the appropriate packages to performing your first vulnerability scan and interpreting the results effectively.
What is Nessus Scanner?
Nessus represents a powerful vulnerability assessment platform designed to discover security weaknesses before malicious actors can exploit them. Created and maintained by Tenable Security, this scanning solution has evolved over two decades to become the gold standard for vulnerability detection across diverse IT environments.
The scanner operates by performing comprehensive security assessments against networks, systems, applications, and cloud infrastructure. It identifies vulnerabilities by checking for known security issues, misconfigurations, default credentials, missing patches, and compliance violations. With a constantly updated database containing over 60,000 vulnerability checks, Nessus provides extensive coverage across operating systems, network devices, databases, web applications, and virtualization platforms.
Tenable offers three primary editions of Nessus to accommodate different use cases. Nessus Essentials provides free scanning capabilities for up to 16 IP addresses, making it ideal for small businesses, home labs, and educational purposes. Nessus Professional removes IP limitations and adds advanced scanning features for security professionals and mid-sized organizations. Nessus Expert extends capabilities further with cloud infrastructure assessment and container security scanning for enterprise environments.
Key Features and Benefits
Nessus delivers exceptional value through its comprehensive feature set designed for efficient vulnerability management. High-speed asset discovery automatically identifies devices, systems, and services across your network infrastructure, building an accurate inventory that forms the foundation for security assessments. The platform employs intelligent scanning algorithms that minimize network impact while maximizing coverage.
The vulnerability detection engine identifies thousands of security issues ranging from critical remote code execution flaws to informational findings. Each discovered vulnerability includes detailed descriptions, affected software versions, CVSS scores, and remediation guidance. The system prioritizes findings based on severity and exploitability, enabling security teams to focus resources where they matter most.
Credentialed scanning capabilities allow Nessus to authenticate to target systems and perform deep inspections. This approach uncovers vulnerabilities that network-level scans miss, including local privilege escalation issues, configuration weaknesses, and software-specific flaws. The scanner supports authentication methods for Linux, Windows, databases, network devices, and cloud platforms.
Compliance auditing features assess systems against industry frameworks and regulatory standards. Pre-built audit templates cover PCI DSS, HIPAA, GDPR, FFIEC, FISMA, CIS Benchmarks, and numerous other compliance requirements. Organizations can demonstrate security posture and identify compliance gaps through automated policy audits.
Integration capabilities enable Nessus to work seamlessly within existing security workflows. The platform exports data to SIEM solutions, ticketing systems, vulnerability management platforms, and reporting tools through APIs and standardized formats. This connectivity streamlines vulnerability remediation processes and enhances overall security operations.
Prerequisites
Before installing Nessus on Debian 13, ensure your system meets the necessary requirements for optimal performance.
System Requirements for Debian 13
Your Debian 13 system should have adequate resources to handle Nessus operations effectively. A minimum configuration includes 2 GB of RAM, though 4-8 GB is recommended for better performance, especially when running concurrent scans. Storage requirements call for at least 20 GB of available disk space, with 50 GB or more recommended to accommodate plugin databases, scan data, and system growth over time.
The processor should be a 64-bit (amd64) architecture with at least 1 GHz clock speed. Dual-core or quad-core processors with 2 GHz or higher speeds provide better scan performance and faster plugin compilation. SSD storage significantly improves Nessus responsiveness compared to traditional hard drives.
An active internet connection is essential during installation for downloading packages, activating licenses, and retrieving plugin updates. Network bandwidth affects scan speed when assessing remote targets, so adequate connectivity improves overall efficiency.
Software Prerequisites
Your Debian 13 installation should be fully updated before proceeding. Run system updates to ensure all packages are current and potential conflicts are minimized. You’ll need root access or sudo privileges to install system packages and configure services.
Essential utilities include curl or wget for downloading the Nessus package from Tenable’s servers. Most Debian installations include these tools by default, but verify their presence before starting. If curl is missing, install it with apt install curl.
A modern web browser is necessary to access the Nessus web interface after installation. Chrome, Firefox, or Edge work well for the browser-based console. The interface requires JavaScript and cookie support, so ensure these features are enabled.
Basic Linux command-line familiarity helps navigate the installation process smoothly. Understanding package management, service control, and firewall configuration streamlines the setup experience.
Network Requirements
Nessus operates through a web-based interface listening on TCP port 8834 by default. This port must be available and not in use by other services on your system. Check port availability before installation to avoid conflicts.
Firewall configuration may be necessary if you’re accessing Nessus remotely or have restrictive firewall rules. The firewall must permit connections to port 8834 from authorized IP addresses or networks. UFW or iptables configurations require adjustment to allow this traffic.
Obtain a Nessus Essentials activation code from Tenable’s website before beginning installation. Registration is free and provides immediate access to the activation code via email. Keep this code accessible as you’ll need it during initial configuration.
Step 1: Download Nessus Package for Debian 13
Begin by obtaining the correct Nessus package for your Debian 13 system. Navigate to the official Tenable Nessus download page at www.tenable.com/downloads/nessus. The page displays various Nessus versions and platform options.
Select the appropriate package from the Linux section. Choose the “Debian” category and select the .deb package for amd64 architecture. Debian 13 uses packages compatible with Debian 10, 11, and 12 distributions, so select the most recent Debian package available.
For direct server downloads, use curl to retrieve the package without needing a graphical interface:
curl --request GET \
--url 'https://www.tenable.com/downloads/api/v2/pages/nessus/files/Nessus-10.10.0-debian10_amd64.deb' \
--output 'Nessus-10.10.0-debian10_amd64.deb'Replace the version number with the current release available on Tenable’s website. The download size typically ranges from 100-150 MB depending on the version.
Alternatively, use wget if you prefer that utility:
wget https://www.tenable.com/downloads/api/v2/pages/nessus/files/Nessus-10.10.0-debian10_amd64.debVerify the downloaded file exists and has the expected size:
ls -lh Nessus*.debThe file should appear in your current directory with the appropriate size. If the download fails or the file size seems incorrect, repeat the download process or check your internet connection.
Step 2: Install Nessus on Debian 13
With the package downloaded, proceed to installation using Debian’s package management tools. The dpkg utility handles .deb package installation directly.
Execute the installation command with sudo privileges:
sudo dpkg -i Nessus-10.10.0-debian10_amd64.debThe installation process extracts and configures Nessus components. You’ll see output indicating package unpacking and setup progress. The installer places Nessus files in the /opt/nessus/ directory structure, which includes binaries, plugins, configuration files, and documentation.
If dependency issues arise during installation, resolve them using apt:
sudo apt install -fThis command automatically identifies and installs missing dependencies, then completes the Nessus installation. Dependency problems are uncommon with current Debian releases but may occur in minimal installations.
Alternatively, use apt directly to handle the package installation and dependency resolution simultaneously:
sudo apt install ./Nessus-10.10.0-debian10_amd64.debThe installation creates a systemd service unit for nessusd (the Nessus daemon), enabling easy service management through standard systemctl commands. User accounts and permissions are configured automatically during this phase.
Verify installation success by checking the Nessus directory:
ls -la /opt/nessus/You should see subdirectories including bin, etc, lib, sbin, and var, confirming successful installation. The entire process typically completes within 2-5 minutes depending on system performance.
Step 3: Start and Enable Nessus Service
After installation, start the Nessus service to begin operations. Systemd manages the nessusd daemon on Debian 13, providing reliable service control.
Start the Nessus service with this command:
sudo systemctl start nessusdThe service takes 30-60 seconds to initialize during first startup as it prepares the database and runtime environment. No output indicates successful execution.
Enable automatic startup at boot time to ensure Nessus runs after system restarts:
sudo systemctl enable nessusdCombine both operations into a single command for efficiency:
sudo systemctl enable --now nessusdVerify the service is running correctly:
sudo systemctl status nessusdThe output should display “active (running)” in green, along with process information and recent log entries. If the service fails to start, examine the status output for error messages indicating the problem.
Check that the nessusd process is listening on the expected port:
sudo ss -tlnp | grep 8834This command shows the listening socket on port 8834, confirming Nessus is ready to accept connections.
For troubleshooting startup issues, review system logs:
sudo journalctl -u nessusd -n 50This displays the last 50 log entries for the Nessus service, revealing configuration errors, port conflicts, or permission problems that prevent startup.
Step 4: Configure Firewall for Nessus Access
Firewall configuration ensures authorized access to the Nessus web interface while maintaining security. Debian systems commonly use UFW (Uncomplicated Firewall) or iptables for packet filtering.
Check if UFW is installed and active:
sudo ufw statusIf UFW is not installed, add it to your system:
sudo apt install ufwEnable the firewall if it’s currently inactive:
sudo ufw enableAllow incoming connections to port 8834:
sudo ufw allow 8834/tcpThis rule permits TCP traffic to port 8834 from any source address. For enhanced security, restrict access to specific IP addresses or networks:
sudo ufw allow from 192.168.1.0/24 to any port 8834Replace the IP range with your management network or administrator workstation addresses.
Verify the firewall rule is active:
sudo ufw status verboseThe output lists all active rules, including the newly created Nessus access rule.
For systems using iptables directly, add an equivalent rule:
sudo iptables -A INPUT -p tcp --dport 8834 -j ACCEPTSave iptables rules to persist across reboots:
sudo iptables-save > /etc/iptables/rules.v4Test firewall configuration by accessing the Nessus interface from your browser. Successful connection confirms proper firewall setup.
Step 5: Register for Nessus Essentials Activation Code
Nessus requires an activation code to enable scanning functionality. Tenable provides Nessus Essentials free of charge with reasonable usage limitations.
Visit the Tenable Nessus Essentials registration page at www.tenable.com/products/nessus/nessus-essentials. Complete the registration form with your information including name, email address, and organization details.
Nessus Essentials limits scanning to 16 IP addresses and is licensed for non-commercial use. These constraints work well for home labs, small networks, educational purposes, and security research.
After form submission, Tenable sends an activation code to your email address, typically arriving within minutes. Check your inbox and spam folder if the email doesn’t appear immediately.
The activation code is a lengthy alphanumeric string required during initial Nessus configuration. Keep this code accessible as you proceed to web interface setup.
Organizations requiring unlimited scanning, commercial use, or advanced features should consider Nessus Professional or Expert editions. These paid versions remove IP restrictions and add capabilities like compliance auditing, advanced scanning, and priority support.
Step 6: Access Nessus Web Interface
Nessus operates through a browser-based interface providing full control over scanning operations and configuration. Open your web browser and navigate to the Nessus URL.
For local access on the same machine:
https://localhost:8834For remote access from another computer:
https://server-ip-address:8834Replace “server-ip-address” with your Debian server’s actual IP address.
Your browser displays a security warning about the SSL certificate because Nessus uses a self-signed certificate by default. This warning is expected and doesn’t indicate a security problem. The self-signed certificate still encrypts traffic between your browser and Nessus, protecting credentials and sensitive data.
Accept the security exception to proceed. Different browsers present this option differently:
- Chrome: Click “Advanced” then “Proceed to localhost (unsafe)”
- Firefox: Click “Advanced” then “Accept the Risk and Continue”
- Edge: Click “Advanced” then “Continue to localhost (unsafe)”
The Nessus welcome screen appears after accepting the certificate warning. This page initiates the setup wizard that guides you through initial configuration.
If you cannot connect, verify the nessusd service is running, firewall rules are correct, and you’re using the right IP address and port. Network connectivity issues, service problems, or firewall blocks prevent successful access.
Step 7: Initial Nessus Configuration
The setup wizard streamlines initial configuration through a series of straightforward steps.
Selecting Nessus Edition
The first screen asks which Nessus edition you’re deploying. Select “Nessus Essentials” to use the free version with your activation code. Other options include Nessus Professional and Nessus Expert for paid licenses.
Activation Process
Enter the activation code received via email in the designated field. Copy and paste the code carefully to avoid typos, as the code is case-sensitive and contains easily confused characters.
Click “Continue” to validate the code with Tenable’s servers. This process requires internet connectivity as Nessus contacts Tenable to verify license authenticity. Activation typically completes within seconds.
If activation fails, verify the code is correct, check internet connectivity, and ensure no proxy or firewall blocks outbound HTTPS connections to Tenable’s servers.
Creating Administrator Account
Configure the administrative account that manages Nessus. Enter a username following standard naming conventions (alphanumeric characters, avoiding special symbols).
Create a strong password meeting security best practices. Use at least 12 characters combining uppercase letters, lowercase letters, numbers, and special characters. Avoid common words, sequential patterns, or personal information. Example strong password: T3n@bl3N3ssus!Scan
Confirm the password by entering it a second time. These credentials grant complete control over Nessus, so protect them carefully and store them securely using a password manager.
Plugin Compilation Phase
After account creation, Nessus downloads and compiles plugins. Plugins are individual security checks that detect specific vulnerabilities, misconfigurations, or compliance violations. The plugin database contains tens of thousands of checks covering diverse technologies.
This initial download retrieves the complete plugin set from Tenable’s servers, typically totaling several hundred megabytes. The compilation process indexes plugins and prepares them for scanning operations.
Expect this phase to take 5-15 minutes depending on internet speed and system resources. The interface displays progress indicators showing download percentage and compilation status. CPU and disk usage increase during compilation as the system processes plugin data.
Avoid interrupting this process. Interruption requires restarting the setup wizard and repeating plugin compilation. Once complete, Nessus is ready for scanning operations.
Step 8: Nessus Dashboard Overview
The Nessus dashboard serves as your command center for vulnerability management operations. After plugin compilation completes, you arrive at the main interface.
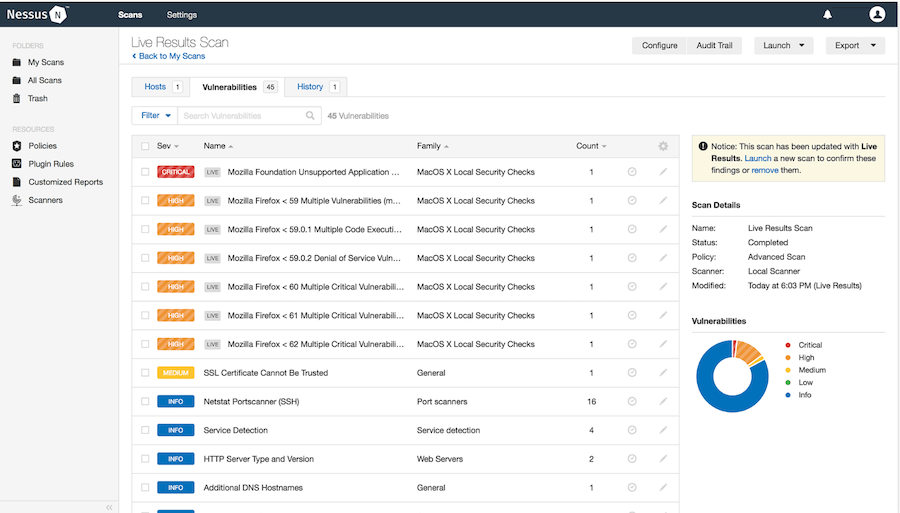
The navigation menu appears on the left side, providing access to key features. The “Scans” section displays all configured and completed scans, showing scan names, targets, schedules, and last run times. This view enables quick access to scan results and management operations.
The “Settings” section contains configuration options for Nessus including user management, scanner preferences, plugin updates, and system settings. Administrators customize Nessus behavior through these options to match organizational requirements.
The “Policies” section allows creation of custom scan templates. Policies define which vulnerability checks run, authentication credentials, performance settings, and reporting options. Reusable policies standardize scanning across your environment.
The “Plugin Rules” section provides granular control over individual vulnerability checks. Enable or disable specific plugins, configure thresholds, and manage false positive suppressions through this interface.
The dashboard’s central area displays scan summaries, vulnerability statistics, and system status. Visual charts show vulnerability distributions by severity, trending over time, and host comparisons.
Navigation is intuitive with clear labeling and logical organization. Hover tooltips provide additional context for various interface elements. The interface adapts to different screen sizes, working effectively on desktop monitors and tablets.
Step 9: Configure Your First Vulnerability Scan
Creating your first scan introduces Nessus’s core functionality and demonstrates the assessment process.
Creating a New Scan
Click the “New Scan” button in the Scans section. Nessus presents a template selection screen showing predefined scan configurations optimized for different scenarios.
The “Basic Network Scan” template provides a balanced approach suitable for general vulnerability assessment. It performs comprehensive checks without excessive scan time or network impact. Select this template for your first scan.
The “Advanced Scan” template offers complete customization of all scanning parameters. Use this option when you need fine-grained control over scan behavior.
Other templates include “Web Application Scan” for web server assessment, “Malware Scan” for malicious software detection, and “Credentialed Patch Audit” for authenticated patch compliance checking.
Scan Configuration Settings
After selecting a template, configure specific scan parameters.
Provide a descriptive scan name that clearly identifies its purpose, such as “Production Network Weekly Scan” or “DMZ Infrastructure Assessment.” Meaningful names help organize multiple scans and improve audit trails.
Define target hosts in the Targets field. Nessus accepts various formats:
- Single IP:
192.168.1.100 - IP range:
192.168.1.1-192.168.1.254 - CIDR notation:
192.168.1.0/24 - Hostnames:
server1.example.com - Multiple targets: Separate entries with commas or newlines
Consider scan scheduling to automate regular assessments. Options include one-time execution, daily scans, weekly scans on specific days, or monthly scans. Scheduled scans ensure continuous security monitoring without manual intervention.
Configure notification settings to receive email alerts when scans complete or encounter issues. Email notifications keep administrators informed without requiring constant interface monitoring.
Discovery settings control how Nessus identifies live hosts and open ports. Port scan ranges affect scan thoroughness and duration. Full port scans (1-65535) take longer but find services on non-standard ports, while common port scans (top 1000 ports) complete faster with reasonable coverage.
Assessment settings balance thoroughness against scan duration and network impact. More intensive scans detect additional vulnerabilities but consume more time and bandwidth. Adjust these based on network capacity and available scanning windows.
Report settings determine output format and detail level. Options range from concise executive summaries to comprehensive technical reports containing full vulnerability details.
Step 10: Perform Credentialed vs Non-Credentialed Scans
Nessus offers two fundamental scanning approaches with distinct advantages.
Non-credentialed scans assess targets from an external perspective without authentication. These scans identify network-visible vulnerabilities, open ports, running services, and remotely exploitable issues. This approach simulates how external attackers view your infrastructure and finds internet-facing vulnerabilities.
Non-credentialed scans have limitations. They cannot detect local vulnerabilities, missing patches, or configuration issues requiring system-level access. Many security problems only appear through authenticated inspection.
Credentialed scans authenticate to target systems and perform deep security assessments. By logging in with provided credentials, Nessus examines installed software, patch levels, configuration files, registry settings, and local security policies. This approach discovers vulnerabilities missed by external scanning and provides comprehensive security posture visibility.
Adding Authentication Credentials
Configure credentials in the scan settings under the Credentials section. Nessus supports numerous authentication methods including SSH keys for Linux, Windows domain credentials, database passwords, and SNMP community strings.
For Linux targets, provide SSH credentials with username and password or SSH private key. Create a dedicated scanning account with read-only permissions following the principle of least privilege. This account needs sufficient access to read system information without unnecessary administrative capabilities.
For Windows targets, supply domain or local administrator credentials. Domain accounts should have limited administrative privileges across target systems while local accounts apply to individual machines.
Nessus encrypts and securely stores all credentials. Passwords never appear in scan results or reports, protecting sensitive authentication information.
Best practice recommends using credentialed scans whenever possible for maximum vulnerability detection accuracy. Combine credentialed and non-credentialed scans to achieve both external and internal perspectives of your security posture.
Step 11: Launch and Monitor Your Scan
With configuration complete, execute the scan to begin vulnerability assessment.
Save the scan configuration by clicking the “Save” button. The scan appears in your scans list with “Configured” status.
Launch the scan by clicking the “Launch” button or play icon next to the scan name. Nessus immediately begins the assessment process, transitioning the scan status to “Running.”
The interface displays real-time progress indicators showing:
- Elapsed time since scan start
- Percentage completion
- Number of hosts assessed
- Vulnerabilities discovered so far
Nessus employs Live Results functionality, presenting findings as they’re discovered rather than waiting for scan completion. Click on the running scan to view current results, allowing early identification of critical issues requiring immediate attention.
Scan duration varies based on multiple factors including target count, network speed, enabled vulnerability checks, and target system responsiveness. Small networks with a dozen hosts might complete in 15-30 minutes, while large environments with hundreds of systems could require several hours.
Monitor system resources during scanning to ensure adequate capacity. Nessus uses CPU for vulnerability analysis and network bandwidth for communication with targets. Resource constraints slow scan progress but don’t affect accuracy.
Pause scans if necessary using the pause button. Paused scans retain current progress and resume from the same point when restarted. This feature helps manage scanning during business hours or when network capacity becomes limited.
Stop scans completely using the stop button if needed. Stopped scans retain discovered vulnerabilities but cannot be resumed, requiring complete restart if additional data is needed.
Step 12: Analyze Scan Results
Completed scans provide comprehensive security insights through detailed results and reports.
Access scan results by clicking on the completed scan in your scans list. The results dashboard presents vulnerability findings organized by severity.
Understanding Severity Levels
Nessus categorizes vulnerabilities into five severity levels:
Critical: Severe vulnerabilities allowing immediate remote compromise, complete system control, or data exposure. These demand urgent remediation, typically within 24-48 hours.
High: Serious security issues enabling significant unauthorized access or data compromise. Address high-severity findings within one week of discovery.
Medium: Moderate vulnerabilities requiring authentication or specific conditions for exploitation. Remediate within one month following discovery.
Low: Minor security weaknesses with limited impact or requiring significant attacker effort. Address during regular maintenance cycles.
Info: Informational findings providing environmental details without direct security impact. Use these for inventory and planning purposes.
Interpreting Vulnerability Details
Click individual vulnerabilities to access detailed information including:
Description: Comprehensive explanation of the security issue, affected software, and exploitation potential.
Solution: Specific remediation guidance including patches, configuration changes, or workarounds addressing the vulnerability.
See Also: References to CVE identifiers, vendor advisories, security bulletins, and additional information sources.
Risk Information: CVSS scores quantifying vulnerability severity using industry-standard metrics. CVSS provides objective risk assessment ranging from 0 (informational) to 10 (critical).
Vulnerability Information: Technical details about the flaw including vulnerable software versions, affected services, and discovery methods.
Plugin Information: Details about the Nessus plugin detecting this vulnerability including publication date and modification history.
Hosts: Complete list of affected systems exhibiting this vulnerability, enabling targeted remediation efforts.
Review findings carefully to understand your security posture. Prioritize remediation based on severity ratings, exploitability, exposed systems, and business criticality. Critical vulnerabilities on internet-facing systems demand immediate attention while low-severity findings on internal development systems can be scheduled for routine maintenance.
False positives occasionally appear in scan results. Verify suspicious findings through manual inspection or additional testing before dismissing them. Document false positives and configure plugin rules to suppress them in future scans.
Common Issues and Troubleshooting
Despite Nessus’s reliability, occasional issues require troubleshooting.
Plugin compilation taking too long: Initial plugin compilation should complete within 15 minutes on systems with adequate resources. Extended compilation time suggests internet bandwidth limitations or insufficient system resources. Verify network connectivity, check available RAM, and ensure sufficient disk space exists.
Cannot access web interface: Connection failures typically result from service problems or firewall blocks. Verify nessusd is running with systemctl status nessusd, confirm firewall permits port 8834 traffic, and check you’re using the correct URL. For remote access, ensure no network firewalls block connections to the Nessus server.
Scan not finding vulnerabilities: Unexpectedly clean scan results often indicate credential problems or network issues. Verify authentication credentials are correct and the scan account has sufficient permissions. Check network connectivity between Nessus and targets, ensuring no firewalls block scanning traffic. Confirm targets are online and responsive during scanning.
High false positive rate: Excessive false positives suggest outdated plugins or overly aggressive scan policies. Update plugins to the latest version and review scan policy settings for unnecessary checks. Tune individual plugins through plugin rules to reduce false positives while maintaining detection accuracy.
Service fails to start: Startup failures typically stem from port conflicts or permission issues. Verify port 8834 is available and not used by other services. Check nessusd has appropriate file permissions and examine logs with journalctl -u nessusd for specific error messages.
Activation code issues: Activation failures occur when codes are entered incorrectly or network problems prevent validation. Carefully verify the activation code matches the email exactly, checking for typos. Confirm internet connectivity allows outbound HTTPS to Tenable’s servers.
Slow scan performance: Lengthy scan times result from network latency, unresponsive targets, or aggressive scan policies. Adjust scan policy performance settings to reduce per-host probe intensity. Increase concurrent host scanning limits if network capacity permits. Exclude unresponsive hosts that delay overall scan completion.
View nessusd logs: Access detailed service logs for troubleshooting guidance:
sudo journalctl -u nessusd -fThis command displays real-time log output revealing configuration errors, network problems, or operational issues affecting Nessus functionality.
Security Considerations
Operating vulnerability scanners requires attention to security protecting both the scanner and assessed systems.
Secure the Nessus web interface with strong administrator passwords combining length, complexity, and uniqueness. Change default credentials immediately and avoid password reuse across systems. Consider implementing two-factor authentication if your Nessus edition supports it.
Implement proper SSL certificates replacing Nessus’s self-signed certificate with organization-issued certificates. Valid certificates eliminate security warnings and prevent man-in-the-middle attacks against the web interface. Obtain certificates from your internal PKI or public certificate authorities.
Restrict Nessus access to authorized security administrators only. Limit account creation to individuals with legitimate scanning responsibilities and review user accounts regularly. Remove accounts when personnel change roles or leave the organization.
Consider network segmentation when placing vulnerability scanners. Dedicated management networks isolate scanning traffic from production, enhancing security and simplifying network policy management. Scanners on dedicated networks also prevent accidental disruption of business operations.
Protect stored credentials within Nessus through proper access controls. Only administrators requiring credential management should access the Nessus console. Regular audits ensure credential integrity and identify any unauthorized changes.
Maintain regular updates to Nessus software and plugins addressing security vulnerabilities in the scanner itself. Subscribe to Tenable security advisories and apply updates promptly, just as you would for other critical infrastructure.
Enable audit logging and regularly review Nessus usage identifying unusual patterns or unauthorized activities. Log review ensures scanning adheres to organizational policies and detects potential misuse.
Ensure scanning activities comply with organizational security policies, regulatory requirements, and legal obligations. Document scanning authorization and obtain necessary approvals before assessing systems, particularly those belonging to customers or partners.
Congratulations! You have successfully installed Nessus. Thanks for using this tutorial for installing the Tenable Nessus Scanner on the Debian 13 “Trixie” system. For additional help or useful information, we recommend you check the official Nessus website.