How To Install Nextcloud on Debian 13

Nextcloud transforms server infrastructure into a powerful, self-hosted cloud storage platform that gives complete control over data privacy and security. This comprehensive guide walks through installing Nextcloud on Debian 13 (Trixie) using the LAMP stack, providing detailed instructions for system administrators, developers, and tech enthusiasts seeking enterprise-grade cloud solutions. The installation process takes approximately 20-30 minutes and results in a production-ready Nextcloud instance with optimized performance configurations.
What is Nextcloud and Why Use It on Debian 13?
Nextcloud represents open-source PHP-based software designed for file sharing, synchronization, and collaborative work environments. The platform offers end-to-end encryption, calendar and contact management, online document editing, and an extensive app ecosystem that extends functionality beyond basic cloud storage. Organizations worldwide deploy Nextcloud as an alternative to proprietary cloud services, maintaining complete sovereignty over sensitive data.
Debian 13 (Trixie) provides exceptional stability and security features that make it ideal for hosting production Nextcloud instances. The operating system includes PHP 8.4 support and regularly updated packages that ensure compatibility with the latest Nextcloud releases. Long-term support and robust security updates protect installations from emerging vulnerabilities while maintaining system stability.
Prerequisites and Requirements
Before beginning the installation process, ensure the server meets specific technical requirements. The system should run Debian 13 with a minimum of 2GB RAM and 20GB available disk space for optimal performance. Root access or sudo privileges enable execution of administrative commands throughout the installation process.
A fully qualified domain name with properly configured DNS A records pointing to the server’s IP address facilitates web access and SSL certificate generation. Open ports 80 (HTTP) and 443 (HTTPS) allow incoming traffic to reach the Nextcloud installation. Basic Linux command-line knowledge helps troubleshoot potential issues during setup. SSH access to the server enables remote administration and configuration management.
Step 1: Update and Prepare the Debian 13 System
System updates prevent dependency conflicts and patch security vulnerabilities before installing new software. Begin by connecting to the Debian 13 server via SSH and executing the following commands:
sudo apt update
sudo apt upgrade -yThe apt update command refreshes package repository indexes, retrieving information about the newest versions of packages and their dependencies. The apt upgrade command installs available updates for all currently installed packages, maintaining system security and stability. Verify successful completion by checking for any error messages in the terminal output.
Step 2: Install the LAMP Stack Components
The LAMP stack (Linux, Apache, MySQL/MariaDB, PHP) provides the foundation for running Nextcloud. Each component plays a critical role in serving files, processing requests, and storing data.
Installing Apache Web Server
Apache serves as the web server that delivers Nextcloud files to browsers and client applications. Install Apache2 and start the service with these commands:
sudo apt install apache2 -y
sudo systemctl start apache2
sudo systemctl enable apache2The systemctl enable command configures Apache to start automatically after system reboots. Verify the installation by checking service status:
sudo systemctl status apache2Active status indicates successful installation. Test Apache by navigating to the server’s IP address in a web browser, which should display the default Apache welcome page.
Installing MariaDB Database Server
MariaDB stores Nextcloud’s configuration data, user information, file metadata, and sharing permissions. Install and configure MariaDB with these commands:
sudo apt install mariadb-server -y
sudo systemctl start mariadb
sudo systemctl enable mariadbSecure the MariaDB installation immediately after setup to prevent unauthorized access:
sudo mysql_secure_installationFollow the interactive prompts to set a root password, remove anonymous users, disallow remote root login, and remove test databases. These security measures protect the database from common attack vectors.
Installing PHP 8.4 and Required Extensions
PHP processes server-side code that powers Nextcloud’s functionality. Install PHP 8.4 along with essential extensions:
sudo apt install php php-fpm php-mysql php-gd php-curl php-mbstring php-xml php-zip php-intl php-bcmath php-gmp php-imagick php-apcu php-redis libapache2-mod-php -yEach PHP extension serves specific purposes. The php-gd module enables image processing for thumbnail generation. The php-curl extension facilitates external HTTP connections. The php-mbstring library handles multi-byte string operations for internationalization support. The php-xml module processes XML data structures. The php-zip extension manages compressed archive handling. The php-intl library provides internationalization functions. The php-mysql driver connects PHP to the MariaDB database.
Verify PHP installation and check the version:
php -vThe output should display PHP 8.4 or higher.
Step 3: Configure the Database for Nextcloud
Database configuration establishes secure storage for Nextcloud’s operational data. Access the MariaDB command-line interface as root:
sudo mysql -u root -pCreate a dedicated database for Nextcloud with appropriate character encoding:
CREATE DATABASE nextcloud CHARACTER SET utf8mb4 COLLATE utf8mb4_general_ci;The UTF8MB4 character set supports full Unicode, including emoji and special characters. Create a dedicated database user with a strong password:
CREATE USER 'nextclouduser'@'localhost' IDENTIFIED BY 'secure_password_here';Replace secure_password_here with a complex password containing uppercase letters, lowercase letters, numbers, and special characters. Grant necessary privileges to the Nextcloud user:
GRANT ALL PRIVILEGES ON nextcloud.* TO 'nextclouduser'@'localhost';
FLUSH PRIVILEGES;
EXIT;These privileges allow the Nextcloud user to SELECT, INSERT, UPDATE, DELETE, CREATE, DROP, INDEX, and ALTER tables within the nextcloud database. Flushing privileges ensures MariaDB immediately applies the permission changes.
Step 4: Download and Extract Nextcloud
Downloading Nextcloud from official sources ensures authenticity and security. Navigate to the web server document root:
cd /var/www/Download the latest stable Nextcloud release:
sudo wget https://download.nextcloud.com/server/releases/latest.zipInstall the unzip utility if not already present:
sudo apt install unzip -yExtract the downloaded archive:
sudo unzip latest.zipSet proper ownership to the Apache web server user:
sudo chown -R www-data:www-data /var/www/nextcloud/Configure appropriate file permissions for security:
sudo chmod -R 755 /var/www/nextcloud/These permissions allow the web server to read and execute files while preventing unauthorized modifications. Remove the installation archive to free disk space:
sudo rm latest.zipStep 5: Create Apache Virtual Host Configuration
Virtual host configuration directs Apache to serve Nextcloud files when users access the designated domain. Create a new configuration file:
sudo nano /etc/apache2/sites-available/nextcloud.confAdd the following virtual host configuration:
<VirtualHost *:80>
ServerName cloud.yourdomain.com
DocumentRoot /var/www/nextcloud/
ErrorLog ${APACHE_LOG_DIR}/nextcloud-error.log
CustomLog ${APACHE_LOG_DIR}/nextcloud-access.log combined
<Directory /var/www/nextcloud/>
Require all granted
AllowOverride All
Options FollowSymLinks MultiViews
<IfModule mod_dav.c>
Dav off
</IfModule>
</Directory>
</VirtualHost>Replace cloud.yourdomain.com with your actual domain name. The AllowOverride All directive permits .htaccess files to override server configurations. The Dav off setting disables Apache’s WebDAV module since Nextcloud uses its own SabreDAV implementation.
Enable the virtual host configuration:
sudo a2ensite nextcloud.confEnable required Apache modules for Nextcloud functionality:
sudo a2enmod rewrite headers env dir mime setenvifThe rewrite module enables URL rewriting for pretty URLs. The headers module allows HTTP header manipulation for security features. Disable the default Apache site to prevent conflicts:
sudo a2dissite 000-default.confTest Apache configuration syntax:
sudo apachectl configtestA “Syntax OK” response indicates correct configuration. Restart Apache to apply changes:
sudo systemctl restart apache2Step 6: Complete Nextcloud Web Installation
The Nextcloud installation wizard configures initial settings through an intuitive web interface. Open a web browser and navigate to your domain (http://cloud.yourdomain.com). The Nextcloud setup page appears automatically on first access.
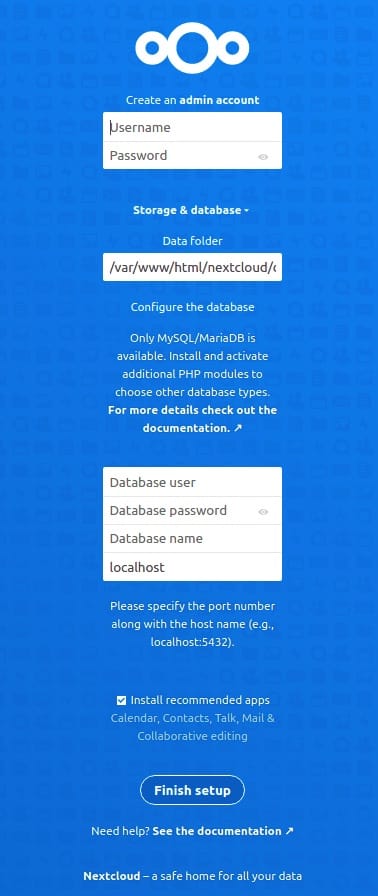
Create an administrative user account by entering a username and strong password. Strong passwords should contain at least 12 characters with mixed case letters, numbers, and symbols. Configure the data directory location, accepting the default /var/www/nextcloud/data path or specifying a custom location with adequate storage capacity.
Enter database connection details in the corresponding fields. Select “MySQL/MariaDB” as the database type. Input the database name (nextcloud), database username (nextclouduser), database password (the secure password created earlier), and database host (localhost). Review recommended applications and select those needed for initial installation.
Click “Finish setup” to initiate the installation process. Nextcloud automatically creates necessary database tables, configures internal settings, and prepares the environment. The initial setup may take several minutes depending on server resources. Upon completion, Nextcloud redirects to the dashboard interface where file management, settings configuration, and app installation become accessible.
Step 7: Implement SSL/TLS with Let’s Encrypt
HTTPS encryption protects data transmission between clients and servers, preventing interception of sensitive information. Install Certbot and the Apache plugin:
sudo apt install certbot python3-certbot-apache -yRequest an SSL certificate for the Nextcloud domain:
sudo certbot --apache -d cloud.yourdomain.comCertbot automatically validates domain ownership through DNS verification. Enter an email address for renewal notifications and certificate expiration warnings. Accept the terms of service when prompted. Choose whether to redirect HTTP traffic to HTTPS (recommended for enhanced security).
Certbot modifies Apache configuration files to enable SSL and configure automatic HTTPS redirection. Test automatic certificate renewal to ensure continuous security:
sudo certbot renew --dry-runSuccessful output confirms proper renewal configuration. Certificates automatically renew every 90 days through a systemd timer. Verify SSL installation by accessing the site via HTTPS and checking for the padlock icon in the browser address bar.
Step 8: Optimize PHP Configuration for Performance
PHP configuration tuning improves upload capacity and processing performance. Locate the PHP configuration file for Apache:
sudo nano /etc/php/8.4/apache2/php.iniModify the following directives to accommodate large file uploads and extended processing times:
memory_limit = 768M
upload_max_filesize = 1024M
post_max_size = 1024M
max_execution_time = 300
max_input_time = 300The memory_limit directive allocates sufficient memory for PHP processes handling large files. The upload_max_filesize setting determines the maximum size of individual uploaded files. The post_max_size value must equal or exceed upload_max_filesize to accommodate complete file uploads. The max_execution_time and max_input_time settings prevent timeouts during long-running operations like large file processing.
Enable and configure OPcache for improved performance:
opcache.enable=1
opcache.memory_consumption=256
opcache.interned_strings_buffer=16
opcache.max_accelerated_files=10000
opcache.revalidate_freq=1
opcache.save_comments=1OPcache stores precompiled PHP bytecode in memory, reducing processing overhead and improving response times. Restart Apache to apply PHP configuration changes:
sudo systemctl restart apache2Step 9: Configure Redis for Caching and Performance
Redis caching dramatically improves Nextcloud performance by storing frequently accessed data in memory. Install Redis server:
sudo apt install redis-server -yConfigure Redis to use Unix sockets instead of TCP connections for enhanced speed:
sudo nano /etc/redis/redis.confModify the following settings:
port 0
unixsocket /var/run/redis/redis-server.sock
unixsocketperm 770Setting port to 0 disables TCP listening. The Unix socket path specifies the location for socket communication. The socket permissions allow the www-data user to access Redis.
Add the www-data user to the redis group:
sudo usermod -a -G redis www-dataRestart Redis to apply configuration changes:
sudo systemctl restart redis-serverEdit the Nextcloud configuration file to enable caching:
sudo nano /var/www/nextcloud/config/config.phpAdd the following caching directives before the closing parenthesis:
'memcache.local' => '\OC\Memcache\APCu',
'memcache.distributed' => '\OC\Memcache\Redis',
'memcache.locking' => '\OC\Memcache\Redis',
'redis' => [
'host' => '/var/run/redis/redis-server.sock',
'port' => 0,
],This configuration uses APCu for local caching (fastest option) and Redis for distributed caching and file locking. The combination provides optimal performance for single-server deployments.
Step 10: Set Up Cron Jobs for Background Tasks
Cron-based background job execution ensures reliable task processing independent of web server activity. Access the www-data user’s crontab:
sudo crontab -u www-data -eAdd the following cron entry:
*/5 * * * * php -f /var/www/nextcloud/cron.phpThis configuration executes Nextcloud’s cron.php script every 5 minutes. Background tasks include file scanning, notification sending, and maintenance operations.
Access Nextcloud admin settings and navigate to Basic Settings. Select “Cron” as the background jobs execution method. The page displays the last cron execution time, confirming proper configuration.
Security Hardening and Best Practices
Comprehensive security measures protect Nextcloud installations from unauthorized access and attacks. Install and configure the Uncomplicated Firewall (UFW):
sudo apt install ufw -y
sudo ufw allow OpenSSH
sudo ufw allow 80/tcp
sudo ufw allow 443/tcp
sudo ufw enableThese rules permit SSH access and web traffic while blocking all other incoming connections. Install fail2ban to prevent brute-force authentication attacks:
sudo apt install fail2ban -y
sudo systemctl enable fail2ban
sudo systemctl start fail2banConfigure trusted domains in config.php to prevent host header poisoning:
sudo nano /var/www/nextcloud/config/config.phpEnsure the trusted_domains array includes only legitimate access domains:
'trusted_domains' => [
0 => 'cloud.yourdomain.com',
],Enable two-factor authentication for administrative accounts through Nextcloud’s app store. Install the “Two-Factor TOTP Provider” app from the Apps menu. Regular security updates maintain protection against emerging vulnerabilities:
sudo apt update && sudo apt upgrade -yImplement automated backup strategies using rsync, duplicity, or dedicated backup solutions. Store backups in geographically separate locations to ensure disaster recovery capabilities.
Troubleshooting Common Installation Issues
Database connection errors typically result from incorrect credentials or privilege issues. Verify database credentials in config.php match those created during database setup. Check MariaDB service status and restart if necessary.
PHP module missing errors indicate incomplete dependency installation. Review the PHP extensions list and install any missing modules using apt. Permission denied issues arise from incorrect file ownership or permissions. Reset ownership to www-data:www-data and apply appropriate permissions:
sudo chown -R www-data:www-data /var/www/nextcloud/
sudo chmod -R 755 /var/www/nextcloud/Apache configuration syntax errors prevent server restart. Run apachectl configtest to identify configuration file issues. Memory limit exceeded problems require PHP memory_limit increases in php.ini.
SSL certificate generation failures often stem from DNS propagation delays or port accessibility issues. Verify DNS records point correctly to the server IP address. Ensure ports 80 and 443 accept incoming connections.
Trusted domain errors appear when accessing Nextcloud from unapproved domains. Add the accessing domain to the trusted_domains array in config.php. White screen or 500 errors indicate PHP execution problems. Check Apache error logs for detailed diagnostics:
sudo tail -f /var/log/apache2/error.logReview Nextcloud logs for application-specific errors:
sudo tail -f /var/www/nextcloud/data/nextcloud.logCongratulations! You have successfully installed Nextcloud. Thanks for using this tutorial to install the latest version of Nextcloud own cloud storage on Debian 13 “Trixie” system. For additional help or useful information, we recommend you check the official Nextcloud website.