How To Install Nginx on Fedora 42

Nginx (pronounced “engine-x”) stands as one of the most powerful and versatile web servers available today. If you’re running Fedora 42, the latest release of this robust Linux distribution, setting up Nginx provides you with a high-performance web server that can handle everything from simple static websites to complex application deployments. This comprehensive guide walks you through the entire process of installing, configuring, and optimizing Nginx on Fedora 42, ensuring you have all the knowledge needed to deploy a secure and efficient web server environment.
Understanding Nginx and Its Benefits
Nginx is an open-source web server and reverse proxy server known for its exceptional performance, stability, and rich feature set. Unlike traditional web servers that use a thread-based approach, Nginx employs an event-driven, asynchronous architecture that allows it to handle thousands of concurrent connections with minimal resource consumption. This makes it particularly well-suited for high-traffic environments and resource-constrained systems.
When compared to Apache, its most common alternative, Nginx demonstrates superior performance under high loads while maintaining a smaller memory footprint. This efficiency stems from its core design philosophy of doing more with less.
The key advantages of Nginx include:
- Exceptional performance with static content delivery
- Efficient reverse proxy capabilities
- Built-in load balancing functionality
- Low resource utilization even under heavy traffic
- Straightforward configuration syntax
- Powerful URL rewriting and redirection
- HTTP/2 and HTTPS support out of the box
For modern web applications, Nginx serves as an ideal front-end server that can efficiently distribute requests, cache content, and terminate SSL connections, significantly improving overall system performance and user experience.
Prerequisites for Installation
Before proceeding with Nginx installation on Fedora 42, ensure your system meets the following requirements:
- A Fedora 42 system with root or sudo privileges
- A minimum of 512MB RAM (1GB or more recommended for production environments)
- At least 10GB of available disk space
- Basic familiarity with Linux command-line operations
- Network connectivity for package downloads
It’s crucial to verify that no other web servers (like Apache) are currently running on the system to avoid port conflicts. If another web server is installed, you’ll need to either stop and disable it or configure Nginx to use different ports.
You can check for running web servers with:
sudo systemctl status httpd
sudo systemctl status apache2If any of these services are active, you should disable them before proceeding:
sudo systemctl stop httpd
sudo systemctl disable httpdUpdating Fedora 42 System
Keeping your Fedora system updated is essential before installing any new software. This ensures compatibility and security by providing the latest package versions and security patches.
To update your Fedora 42 system, open a terminal and execute:
sudo dnf upgrade --refreshThe --refresh flag ensures that the package manager refreshes its metadata from the repository sources, guaranteeing that you’re getting the most current packages.
During the update process, the system will calculate dependencies and prompt you to confirm the installation of updated packages. Type ‘y’ and press Enter to proceed. Depending on your internet connection and the number of packages that need updating, this process may take several minutes.
After the update completes, it’s recommended to reboot your system to ensure all updates are properly applied:
sudo systemctl rebootInstalling Nginx
There are two primary methods for installing Nginx on Fedora 42: using the DNF package manager to install from the official Fedora repositories, or compiling from source for additional customization options. We’ll explore both approaches.
Installing from Fedora Repositories
The simplest and most straightforward method is to use Fedora’s built-in package manager, DNF. This approach ensures you get a stable version that integrates well with the system and receives automatic updates.
To install Nginx using DNF, run:
sudo dnf install nginxThe system will automatically resolve dependencies and download the necessary packages. When prompted, type ‘y’ and press Enter to confirm the installation.
After installation completes, you can verify the installed version and package details with:
nginx -v
rpm -qi nginxThis will display the installed Nginx version and detailed package information, including installation date, size, and description.
Installing from Source
For users who require specific features, custom modules, or the absolute latest version, installing Nginx from source provides maximum flexibility.
First, install the necessary build tools and dependencies:
sudo dnf install wget gcc make pcre-devel zlib-devel openssl-develNext, download the latest Nginx source code from the official website:
wget https://nginx.org/download/nginx-1.26.3.tar.gzExtract the downloaded archive:
tar -zxvf nginx-1.26.3.tar.gz
cd nginx-1.26.3Configure the build with your desired options. A basic configuration might look like:
./configure --prefix=/usr/share/nginx \
--sbin-path=/usr/sbin/nginx \
--modules-path=/usr/lib64/nginx/modules \
--conf-path=/etc/nginx/nginx.conf \
--error-log-path=/var/log/nginx/error.log \
--http-log-path=/var/log/nginx/access.log \
--pid-path=/var/run/nginx.pid \
--lock-path=/var/run/nginx.lock \
--with-http_ssl_module \
--with-http_v2_moduleCompile and install Nginx:
make
sudo make installAfter installation, create a systemd service file to manage Nginx:
sudo nano /etc/systemd/system/nginx.serviceAdd the following content:
[Unit]
Description=Nginx HTTP and reverse proxy server
After=network.target
[Service]
Type=forking
PIDFile=/var/run/nginx.pid
ExecStartPre=/usr/sbin/nginx -t -c /etc/nginx/nginx.conf
ExecStart=/usr/sbin/nginx -c /etc/nginx/nginx.conf
ExecReload=/bin/kill -s HUP $MAINPID
KillSignal=SIGQUIT
TimeoutStopSec=5
KillMode=mixed
PrivateTmp=true
[Install]
WantedBy=multi-user.targetSave and close the file, then reload the systemd daemon and enable Nginx to start at boot:
sudo systemctl daemon-reload
sudo systemctl enable nginxManaging the Nginx Service
Proper service management ensures Nginx operates reliably and can be controlled effectively. Fedora 42 uses systemd for service management, providing a consistent interface for controlling Nginx.
Starting Nginx for the First Time
To start the Nginx service, execute:
sudo systemctl start nginxVerify that Nginx is running correctly:
sudo systemctl status nginxThe output should indicate that the service is “active (running)” with a green status indicator.
Basic Service Management Commands
Here are essential commands for managing your Nginx service:
- Stop Nginx:
sudo systemctl stop nginx - Restart Nginx:
sudo systemctl restart nginx - Reload configuration without downtime:
sudo systemctl reload nginx - Enable Nginx to start on boot:
sudo systemctl enable nginx - Disable automatic startup:
sudo systemctl disable nginx
When making configuration changes, it’s recommended to test the syntax before applying them:
sudo nginx -tIf the test passes, you can then reload the configuration with:
sudo systemctl reload nginxThis approach allows configuration changes to take effect without interrupting active connections.
Configuring Firewall Rules
Fedora 42 uses firewalld as its default firewall management solution. For Nginx to be accessible from outside your server, you need to configure the firewall to allow HTTP (port 80) and, if needed, HTTPS (port 443) traffic.
Opening HTTP and HTTPS Ports
To allow HTTP traffic through the firewall:
sudo firewall-cmd --permanent --add-service=httpFor HTTPS connections:
sudo firewall-cmd --permanent --add-service=httpsApply the changes by reloading the firewall:
sudo firewall-cmd --reloadVerifying Firewall Configuration
Check that the services have been properly added:
sudo firewall-cmd --list-servicesThe output should include “http” and “https” among the enabled services.
For more detailed information about the allowed ports:
sudo firewall-cmd --list-allThis command displays all zones and their configurations, including ports and services allowed through the firewall.
Testing the Installation
After installation and firewall configuration, it’s important to verify that Nginx is functioning correctly.
Accessing the Default Page
Open a web browser and navigate to your server’s IP address or hostname:
http://your_server_ipYou should see the default Nginx welcome page, indicating that the server is running properly.
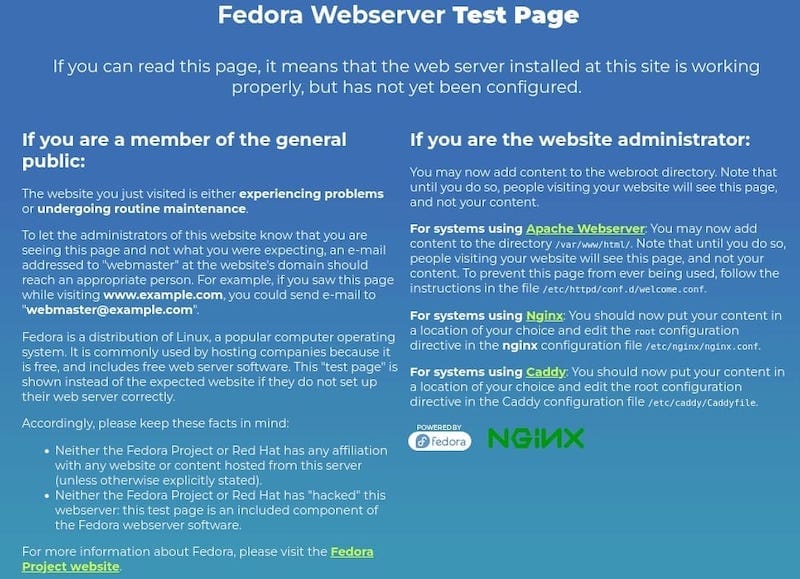
Alternatively, use the command line to test:
curl -I http://localhostThis should return an HTTP/1.1 200 OK response, confirming that Nginx is serving requests.
Troubleshooting Connection Issues
If you can’t access the default page, check the following:
- Verify Nginx is running:
sudo systemctl status nginx - Ensure firewall allows HTTP traffic:
sudo firewall-cmd --list-services - Check for syntax errors in configuration:
sudo nginx -t - Review Nginx error logs:
sudo cat /var/log/nginx/error.log
Common issues include SELinux restrictions, incorrect file permissions, or network configuration problems.
Basic Nginx Configuration
Understanding Nginx’s configuration structure is crucial for effective server management.
Configuration File Structure
On Fedora 42, Nginx’s main configuration file is located at /etc/nginx/nginx.conf. The configuration follows a hierarchical structure with contexts and directives:
- The main context contains global settings
- The
eventscontext manages connection processing - The
httpcontext contains web server and proxy settings - The
servercontext defines virtual host settings - The
locationcontext specifies how to handle specific URL patterns
Additional configuration files can be included using the include directive, providing a modular approach to configuration.
Essential Configuration Parameters
Here are key parameters to understand in the main configuration file:
user: Specifies the user and group under which Nginx worker processes runworker_processes: Defines the number of worker processes (auto or specific number)error_log: Path to the error log file and logging levelpid: Path to the file storing the process IDworker_connections: Maximum number of simultaneous connections per worker
A typical basic configuration might look like:
user nginx;
worker_processes auto;
error_log /var/log/nginx/error.log notice;
pid /run/nginx.pid;
events {
worker_connections 1024;
}
http {
include /etc/nginx/mime.types;
default_type application/octet-stream;
log_format main '$remote_addr - $remote_user [$time_local] "$request" '
'$status $body_bytes_sent "$http_referer" '
'"$http_user_agent" "$http_x_forwarded_for"';
access_log /var/log/nginx/access.log main;
sendfile on;
tcp_nopush on;
keepalive_timeout 65;
gzip on;
include /etc/nginx/conf.d/*.conf;
}After making changes, always test the configuration before applying it:
sudo nginx -t
sudo systemctl reload nginxSetting Up Virtual Hosts
Virtual hosts (server blocks) allow you to serve multiple websites from a single Nginx instance.
Creating a Basic Virtual Host
First, create a directory structure for your website:
sudo mkdir -p /var/www/html/example.com
sudo chown -R $USER:nginx /var/www/html/example.com
sudo chmod -R 750 /var/www/html/example.comCreate a sample index.html file:
echo "<html><body><h1>Welcome to example.com</h1></body></html>" > /var/www/html/example.com/index.htmlNext, create a server block configuration file:
sudo nano /etc/nginx/conf.d/example.com.confAdd the following configuration:
server {
listen 80;
server_name example.com www.example.com;
root /var/www/html/example.com;
index index.html index.htm;
location / {
try_files $uri $uri/ =404;
}
error_page 404 /404.html;
error_page 500 502 503 504 /50x.html;
location = /50x.html {
root /usr/share/nginx/html;
}
}Test and reload the configuration:
sudo nginx -t
sudo systemctl reload nginxSetting Proper File Permissions and SELinux Contexts
On Fedora 42, proper file permissions and SELinux contexts are crucial for Nginx to function correctly.
For file permissions, the recommended ownership is root:nginx for web content directories and files:
sudo chown -R root:nginx /var/www/html
sudo chmod -R 750 /var/www/htmlFor SELinux contexts, you need to set the appropriate type for web content:
sudo semanage fcontext -a -t httpd_sys_content_t "/var/www/html(/.*)?"
sudo restorecon -Rv /var/www/htmlYou can verify the SELinux context with:
ls -Z /var/www/htmlThe output should show system_u:object_r:httpd_sys_content_t:s0 as the context.
Securing Nginx with SSL/TLS
Implementing HTTPS is essential for secure communications between your web server and clients.
Obtaining SSL Certificates
There are several ways to obtain SSL certificates:
- Let’s Encrypt (free, automated certificates):
sudo dnf install certbot python3-certbot-nginx sudo certbot --nginx -d example.com -d www.example.com - Self-signed certificates (for testing):
sudo mkdir -p /etc/nginx/ssl sudo openssl req -x509 -nodes -days 365 -newkey rsa:2048 -keyout /etc/nginx/ssl/nginx.key -out /etc/nginx/ssl/nginx.crt
Configuring HTTPS in Nginx
Update your server block to include SSL configuration:
server {
listen 80;
server_name example.com www.example.com;
return 301 https://$host$request_uri;
}
server {
listen 443 ssl http2;
server_name example.com www.example.com;
ssl_certificate /etc/nginx/ssl/nginx.crt;
ssl_certificate_key /etc/nginx/ssl/nginx.key;
ssl_protocols TLSv1.2 TLSv1.3;
ssl_prefer_server_ciphers on;
ssl_ciphers "EECDH+AESGCM:EDH+AESGCM";
ssl_session_cache shared:SSL:10m;
root /var/www/html/example.com;
index index.html index.htm;
location / {
try_files $uri $uri/ =404;
}
}Apply the configuration:
sudo nginx -t
sudo systemctl reload nginxPerformance Optimization
Optimizing Nginx performance can significantly improve your site’s loading times and resource utilization.
Worker Process Configuration
Adjust the number of worker processes to match your server’s CPU cores:
worker_processes auto; # Automatically detects CPU coresEnabling Compression
Enable gzip compression to reduce bandwidth usage:
gzip on;
gzip_comp_level 5;
gzip_min_length 256;
gzip_proxied any;
gzip_vary on;
gzip_types
application/javascript
application/json
application/xml
text/css
text/plain
text/xml;Caching Configuration
Implement browser caching:
location ~* \.(jpg|jpeg|png|gif|ico|css|js)$ {
expires 30d;
add_header Cache-Control "public, no-transform";
}Buffer Size Optimization
Adjust buffer sizes based on your site’s needs:
client_body_buffer_size 10K;
client_header_buffer_size 1k;
client_max_body_size 8m;
large_client_header_buffers 2 1k;Troubleshooting Common Issues
Even with careful setup, issues can arise with Nginx. Here’s how to address common problems.
403 Forbidden Errors
This often relates to file permissions or SELinux:
- Check file permissions:
ls -la /var/www/html/ - Verify SELinux contexts:
ls -Z /var/www/html/ - Set proper contexts if needed:
sudo semanage fcontext -a -t httpd_sys_content_t "/var/www/html(/.*)?" sudo restorecon -Rv /var/www/html
502 Bad Gateway Errors
Common with reverse proxy configurations:
- Check if the upstream service is running
- Review Nginx error logs:
sudo cat /var/log/nginx/error.log - Verify proxy configurations and connectivity
Connection Refused Errors
If Nginx won’t start or accept connections:
- Check for port conflicts:
sudo ss -tulpn | grep -E ':80|:443' - Verify syntax:
sudo nginx -t - Check service status:
sudo systemctl status nginx - Examine system logs:
sudo journalctl -u nginx
Upgrading Nginx
Keeping Nginx updated is important for security and performance.
Upgrading Packages from Repositories
For Nginx installed via DNF:
sudo dnf update nginxBackup Before Upgrading
Always back up your configuration before upgrading:
sudo cp -r /etc/nginx /etc/nginx.bakTesting After Upgrades
After upgrading, test your configuration:
sudo nginx -t
sudo systemctl restart nginxBest Practices for Nginx on Fedora
Following these practices ensures a robust and secure Nginx deployment.
Security Recommendations
- Use the principle of least privilege for file permissions
- Implement proper SELinux contexts
- Hide server version information:
server_tokens off; - Limit allowed HTTP methods:
if ($request_method !~ ^(GET|HEAD|POST)$) { return 444; }
Configuration Management
- Use include directives for modular configuration
- Maintain separate server blocks in the conf.d directory
- Comment your configurations thoroughly
- Use version control for tracking configuration changes
Monitoring and Maintenance
- Regularly review log files
- Set up log rotation to manage disk space
- Monitor resource usage
- Schedule regular security updates
Congratulations! You have successfully installed Nginx. Thanks for using this tutorial for installing the Nginx web server on Fedora 42 Linux system. For additional help or useful information, we recommend you check the official Nginx website.