How To Install Nginx Proxy Manager on Debian 13

Setting up a reverse proxy server has become essential for modern web infrastructure management. Nginx Proxy Manager provides an intuitive, web-based interface that simplifies the complex task of managing reverse proxies, SSL certificates, and traffic routing on Debian systems. This comprehensive guide walks through the complete installation process of Nginx Proxy Manager on Debian 13 “Trixie,” the latest stable release that brings enhanced security features and improved system performance.
The power of Nginx Proxy Manager lies in its ability to transform complicated command-line configurations into a user-friendly graphical interface. System administrators no longer need to manually edit Nginx configuration files or manage SSL certificates through complex terminal commands. Instead, they can leverage NPM’s streamlined dashboard to create proxy hosts, manage SSL certificates through Let’s Encrypt integration, and monitor web traffic with just a few clicks.
Prerequisites and System Requirements
Debian 13 System Requirements
Debian 13 “Trixie” requires specific hardware specifications to run Nginx Proxy Manager effectively. The minimum system requirements include 2 GB of RAM and 20 GB of available disk space on an x86_64 processor architecture. However, production environments benefit significantly from upgraded specifications: 4 GB or more RAM and at least 50 GB of disk space ensure optimal performance when handling multiple proxy hosts and SSL certificate management.
Network configuration plays a crucial role in NPM deployment. The server requires reliable internet connectivity for Let’s Encrypt certificate validation and Docker image downloads. Firewall considerations must account for incoming traffic on ports 80 (HTTP), 443 (HTTPS), and 81 (NPM admin interface).
Essential Prerequisites
Root or sudo access represents the fundamental requirement for NPM installation on Debian 13. Administrative privileges enable package installation, service management, and Docker container deployment. Basic command-line proficiency and SSH access facilitate remote server management and troubleshooting procedures.
Domain name ownership, while optional, significantly enhances NPM functionality. SSL certificate generation through Let’s Encrypt requires domain validation, making proper DNS configuration essential for production deployments. Understanding containerization concepts and Docker fundamentals helps administrators grasp NPM’s architecture and troubleshoot potential issues effectively.
Preparing Debian 13 for Installation
System Updates and Package Management
Fresh Debian 13 installations require comprehensive system updates before installing additional software. Execute the following commands to refresh package repositories and upgrade installed packages:
sudo apt update && sudo apt upgrade -yThis process ensures all system packages reflect the latest security patches and bug fixes available in the Debian 13 repositories. Package management optimization prevents dependency conflicts during Docker and NPM installation phases.
Installing Essential Dependencies
NPM installation depends on several critical packages that facilitate Docker installation and container management. Install the required dependencies using this command sequence:
sudo apt install -y curl gnupg2 ca-certificates lsb-release apt-transport-https software-properties-commonEach package serves specific functions in the installation process. The curl package enables secure file downloads from remote repositories. The gnupg2 package provides cryptographic signature verification for Docker’s official repository. Certificate authorities bundle (ca-certificates) ensures secure HTTPS connections during package downloads and Docker operations.
Firewall Configuration
Debian 13 systems benefit from immediate firewall configuration to secure NPM deployment. Install and configure UFW (Uncomplicated Firewall) with these commands:
sudo apt install ufw
sudo ufw default deny incoming
sudo ufw default allow outgoing
sudo ufw allow ssh
sudo ufw allow 80/tcp
sudo ufw allow 443/tcp
sudo ufw allow 81/tcp
sudo ufw enablePort 80 handles HTTP traffic redirection to HTTPS, while port 443 manages encrypted HTTPS connections. Port 81 provides access to the NPM administrative interface, requiring careful consideration for production environments. Consider restricting administrative access to specific IP addresses for enhanced security.
Docker Installation and Setup
Installing Docker Engine
Docker serves as the foundation for NPM deployment, providing containerization technology that simplifies installation and maintenance. Begin by adding Docker’s official GPG key and repository:
curl -fsSL https://download.docker.com/linux/debian/gpg | sudo gpg --dearmor -o /usr/share/keyrings/docker-archive-keyring.gpg
echo "deb [arch=$(dpkg --print-architecture) signed-by=/usr/share/keyrings/docker-archive-keyring.gpg] https://download.docker.com/linux/debian $(lsb_release -cs) stable" | sudo tee /etc/apt/sources.list.d/docker.list > /dev/nullUpdate package repositories and install Docker components:
sudo apt update
sudo apt install -y docker-ce docker-ce-cli containerd.ioVerify successful Docker installation by checking the version and running a test container:
docker --version
sudo docker run hello-worldThe hello-world container confirms Docker’s ability to pull images from Docker Hub and execute containers successfully.
Installing Docker Compose
Docker Compose orchestrates multi-container applications like NPM, which requires both the proxy manager and database containers. Download and install Docker Compose v2.18.1 or later:
sudo curl -L "https://github.com/docker/compose/releases/latest/download/docker-compose-$(uname -s)-$(uname -m)" -o /usr/local/bin/docker-compose
sudo chmod +x /usr/local/bin/docker-composeVerify Docker Compose installation and version compatibility:
docker-compose --versionDocker Service Configuration
Enable Docker service startup on boot to ensure NPM availability after system restarts:
sudo systemctl enable docker
sudo systemctl start dockerAdding users to the docker group eliminates the need for sudo commands with Docker operations, though this approach requires security consideration:
sudo usermod -aG docker $USERLog out and back in for group membership changes to take effect.
Installing Nginx Proxy Manager
Creating Project Directory Structure
Organized project directory structure facilitates NPM management and future updates. Create a dedicated directory for NPM deployment:
mkdir ~/nginx-proxy-manager
cd ~/nginx-proxy-managerThis approach centralizes NPM configuration files and simplifies backup procedures. Proper file organization prevents configuration loss during system maintenance or updates.
Docker Compose Configuration
Create a docker-compose.yml file containing NPM’s container definitions and configuration parameters:
version: '3.8'
services:
npm:
image: 'jc21/nginx-proxy-manager:latest'
restart: unless-stopped
ports:
- '80:80'
- '81:81'
- '443:443'
volumes:
- ./data:/data
- ./letsencrypt:/etc/letsencrypt
environment:
DB_MYSQL_HOST: "db"
DB_MYSQL_PORT: 3306
DB_MYSQL_USER: "npm"
DB_MYSQL_PASSWORD: "npm"
DB_MYSQL_NAME: "npm"
depends_on:
- db
db:
image: 'mariadb:latest'
restart: unless-stopped
environment:
MYSQL_ROOT_PASSWORD: 'npm'
MYSQL_DATABASE: 'npm'
MYSQL_USER: 'npm'
MYSQL_PASSWORD: 'npm'
volumes:
- ./mysql:/var/lib/mysqlThe configuration maps essential ports for HTTP (80), HTTPS (443), and administrative access (81). Volume mappings ensure data persistence across container restarts and updates.
Database Configuration
MariaDB container provides persistent storage for NPM configurations, proxy hosts, and SSL certificate data. The database configuration includes environment variables that establish connection parameters between NPM and MariaDB containers.
Database security considerations include password customization and access restrictions. Production deployments should implement stronger passwords and restrict database access to the NPM container only. Volume persistence ensures configuration data survives container updates and system restarts.
Volume and Data Persistence
NPM requires persistent storage for configuration data and SSL certificates. The ./data volume stores NPM application data, user accounts, and proxy configurations. The ./letsencrypt volume preserves SSL certificates and Let’s Encrypt account information across container updates.
File permissions and ownership management becomes critical for volume-mounted directories. Ensure the Docker daemon can read and write to mounted volumes:
sudo chown -R 1000:1000 ./data ./letsencrypt ./mysqlLaunching the Services
Deploy NPM using Docker Compose with the following command:
docker-compose up -dThe -d flag runs containers in detached mode, allowing continued terminal access. Monitor container startup progress and identify potential issues:
docker-compose logs -fSuccessful deployment displays NPM and MariaDB container startup messages without error indicators.
Initial Configuration and Access
Accessing the Web Interface
Navigate to the NPM administrative interface using a web browser pointed to http://server-ip:81. Replace server-ip with your Debian 13 server’s actual IP address. The initial login screen presents default credentials that require immediate modification for security purposes.
Default administrator credentials use admin@example.com as the username and changeme as the password. These credentials provide full administrative access to NPM configuration and should be changed immediately upon first login.
First-Time Setup Wizard
The initial configuration wizard guides administrators through essential security setup procedures. Change the default administrator email and password using strong authentication credentials. Implement complex passwords containing uppercase letters, lowercase letters, numbers, and special characters for maximum security.
User profile configuration includes email settings for Let’s Encrypt certificate notifications and administrative alerts. Proper email configuration ensures administrators receive critical notifications about certificate renewals and system events.
Basic Security Hardening
Immediate security measures protect NPM from unauthorized access and potential exploitation. Consider changing the default administrative port from 81 to a non-standard port for additional security. Firewall modifications should reflect port changes to maintain administrative access.
Administrative interface access restrictions enhance security through IP address whitelisting. Configure firewall rules to limit administrative access to specific networks or IP ranges. This approach prevents unauthorized access attempts from external networks while maintaining legitimate administrative access.
SSL Certificate Configuration
Let’s Encrypt Integration
NPM’s integrated Let’s Encrypt support automates SSL certificate generation and renewal processes. The system supports both HTTP-01 and DNS-01 challenge types for domain validation. HTTP-01 challenges require accessible websites on ports 80 and 443, while DNS-01 challenges utilize DNS TXT records for validation.
Let’s Encrypt rate limiting policies restrict certificate requests to prevent abuse. The service allows 50 certificates per registered domain per week and 300 new orders per account per 3 hours. Understanding these limitations helps plan certificate deployment strategies for multiple domains and subdomains.
Domain Configuration
SSL certificate generation requires proper DNS configuration pointing domain names to the Debian 13 server IP address. Create A records in your DNS management interface linking domain names to the server hosting NPM. DNS propagation typically completes within 24 hours, though most changes propagate within minutes.
Domain validation processes verify domain ownership before certificate issuance. Ensure web servers respond correctly to HTTP requests on port 80 for HTTP-01 challenges. DNS-based validation requires TXT record creation with specific validation tokens provided by Let’s Encrypt.
SSL Best Practices
Modern TLS configuration enhances security through contemporary cipher suites and protocol versions. NPM automatically configures secure SSL settings, including TLS 1.2 and 1.3 support with strong cipher selections. HTTP/2 enablement improves website performance through multiplexed connections and header compression.
Certificate monitoring ensures timely renewal before expiration dates. NPM automates certificate renewal attempts 30 days before expiration, providing multiple retry opportunities. Manual renewal options exist for troubleshooting renewal failures or testing certificate configurations.
Creating Proxy Hosts
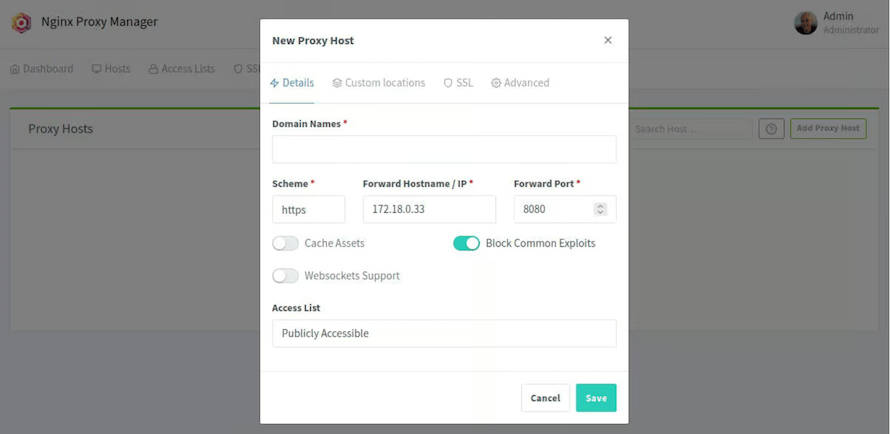
Adding First Proxy Host
Proxy host creation begins through NPM’s intuitive web interface accessible via the dashboard. Click “Add Proxy Host” and configure the domain name, forward hostname/IP address, and target port number. The domain name should match DNS A records pointing to the NPM server.
Forward hostname configuration specifies the backend service receiving proxied requests. Use IP addresses for services running on the same server or different network hosts. Port configuration must match the target service’s listening port, commonly 8080, 3000, or other application-specific ports.
SSL certificate assignment occurs during proxy host creation or through subsequent modifications. Select “Request a new SSL certificate” to generate Let’s Encrypt certificates automatically. Enable “Force SSL” to redirect HTTP requests to HTTPS for enhanced security.
Advanced Proxy Options
WebSocket support enables real-time applications like chat systems, live updates, and interactive dashboards. Enable WebSocket support in the Advanced tab when configuring proxy hosts for applications requiring bidirectional communication.
Custom Nginx configuration snippets provide advanced functionality beyond NPM’s standard options. Add custom directives in the Advanced tab to implement specialized routing, caching, or security headers. Exercise caution with custom configurations to avoid breaking proxy functionality.
Load balancing capabilities distribute traffic across multiple backend servers for improved performance and reliability. Configure multiple upstream servers in custom Nginx snippets to implement round-robin, least connections, or IP hash load balancing algorithms.
Access Lists and Authentication
Access control lists restrict proxy host access to specific IP addresses, networks, or geographical regions. Create access lists through the Access Lists menu and assign them to proxy hosts requiring restricted access. This feature proves valuable for administrative interfaces and internal applications.
Basic HTTP authentication provides simple username/password protection for proxy hosts. Configure authentication through the Access Lists feature, creating credential sets for different user groups. Consider integrating external authentication services for more sophisticated access control requirements.
Security Hardening and Best Practices
Securing the Admin Interface
Self-proxying NPM’s administrative interface through an SSL-enabled proxy host enhances security significantly. Create a dedicated domain name for NPM administration and configure it as a proxy host targeting localhost:81. This approach encrypts administrative traffic and enables advanced access controls.
Custom domain setup for administrative access eliminates the need to remember IP addresses and port numbers. Configure DNS records pointing an administrative subdomain to the NPM server, then create a proxy host with SSL certificate generation enabled.
Two-factor authentication integration requires external authentication services or reverse proxy configurations with authentication middleware. Consider implementing additional security layers for production environments handling sensitive applications or data.
Network Security
Firewall optimization focuses on minimal necessary port exposure while maintaining required functionality. Review and restrict firewall rules to essential ports only. Consider implementing fail2ban or similar intrusion prevention systems to automatically block suspicious access attempts.
Docker network isolation enhances container security through dedicated networks and restricted inter-container communication. Create custom Docker networks for NPM deployment to isolate containers from other system services and applications.
Regular security updates ensure continued protection against discovered vulnerabilities. Implement automated update procedures for Docker images and Debian system packages. Monitor security advisories for NPM and related components to identify required updates promptly.
Monitoring and Logging
Log file analysis provides insights into proxy performance, security events, and troubleshooting information. NPM stores logs within Docker containers, accessible through docker-compose logs commands. Implement log rotation and external log shipping for production environments requiring comprehensive monitoring.
SSL certificate expiration monitoring prevents service disruptions from expired certificates. Configure monitoring systems to alert administrators about certificates approaching expiration dates. NPM’s dashboard displays certificate status and expiration information for proactive management.
Performance monitoring tracks proxy response times, connection counts, and resource utilization metrics. Implement external monitoring solutions to track NPM availability and performance from user perspectives. Consider integrating monitoring data with alerting systems for proactive issue resolution.
Troubleshooting Common Issues
Installation Problems
Docker service startup failures often result from insufficient system resources or conflicting software installations. Verify Docker daemon status using systemctl status docker and examine error messages in system logs. Restart Docker services and review container resource requirements to resolve startup issues.
Permission problems typically manifest as file access errors or container startup failures. Ensure proper ownership and permissions on volume-mounted directories. The Docker daemon requires read/write access to NPM data directories for successful operation.
Network connectivity issues prevent Docker image downloads and Let’s Encrypt certificate validation. Verify internet connectivity and DNS resolution from the Debian 13 server. Check firewall rules to ensure outbound HTTPS connections reach Docker registries and Let’s Encrypt servers.
SSL Certificate Issues
Let’s Encrypt rate limiting triggers when certificate request volumes exceed service limits. Monitor certificate request frequency and implement staging environment testing to avoid production rate limits. Utilize Let’s Encrypt’s staging environment for testing certificate configurations without affecting production rate limits.
DNS propagation delays cause domain validation failures during certificate generation. Verify DNS A records point correctly to the NPM server and allow sufficient time for global DNS propagation. Use DNS checking tools to confirm proper domain resolution before attempting certificate generation.
Certificate renewal failures require manual intervention to identify and resolve underlying issues. Common causes include DNS changes, firewall modifications, or service interruptions during renewal attempts. Review NPM logs and Let’s Encrypt account status to diagnose renewal problems effectively.
Performance Optimization
Resource usage monitoring identifies bottlenecks affecting NPM performance and backend service availability. Monitor CPU, memory, and disk utilization on the Debian 13 server hosting NPM containers. Consider resource limits for Docker containers to prevent resource exhaustion scenarios.
Database performance optimization improves NPM responsiveness during configuration changes and SSL certificate operations. MariaDB container configuration benefits from memory allocation tuning and query optimization. Regular database maintenance prevents performance degradation over time.
Nginx configuration optimization enhances proxy performance for high-traffic scenarios. Custom Nginx configurations can implement caching, compression, and connection optimization for improved user experience. Monitor backend service performance to identify potential optimization opportunities.
Maintenance and Updates
Regular Maintenance Tasks
Container updates ensure NPM installations receive security patches and feature enhancements. Use docker-compose pull to download updated container images, followed by docker-compose up -d to deploy updates. Schedule regular update procedures during maintenance windows to minimize service disruption.
Database maintenance includes backup creation and performance optimization procedures. Implement automated backup scripts to preserve NPM configuration data and SSL certificates. Regular backups enable rapid recovery from hardware failures or configuration corruption.
Log rotation prevents disk space exhaustion from accumulated log files. Configure log rotation policies for Docker containers and system logs to maintain adequate free disk space. Consider implementing log shipping to external systems for long-term log retention and analysis.
Monitoring and Health Checks
Automated health monitoring detects service availability issues and performance degradation before user impact occurs. Implement monitoring checks for NPM web interface accessibility and backend service connectivity. Configure alerting systems to notify administrators of detected issues promptly.
Backup verification ensures backup procedures create recoverable data sets. Regularly test backup restoration procedures in isolated environments to validate backup integrity. Document restoration procedures for rapid recovery during emergency situations.
Performance monitoring tracks system resource utilization and service response times over extended periods. Identify trends indicating capacity planning requirements or optimization opportunities. Implement capacity alerts to provide advance warning of resource constraints requiring attention.
Congratulations! You have successfully installed Nginx Proxy Manager. Thanks for using this tutorial for installing Nginx Proxy Manager on Debian 13 “Trixie” system. For additional help or useful information, we recommend you check the official Nginx website.