How To Install Nginx Proxy Manager on Fedora 42

Managing multiple web services and applications can quickly become overwhelming, especially when dealing with SSL certificates, domain routing, and security configurations. Nginx Proxy Manager emerges as a powerful solution that simplifies reverse proxy management through an intuitive web interface. This comprehensive guide will walk you through installing Nginx Proxy Manager on Fedora 42, covering everything from initial system preparation to advanced configuration techniques.
Fedora 42 provides an excellent foundation for hosting Nginx Proxy Manager due to its cutting-edge package management, robust security features, and enterprise-grade stability. Whether you’re managing a home lab, deploying business applications, or setting up development environments, this tutorial will equip you with the knowledge to successfully implement and maintain your proxy infrastructure.
What is Nginx Proxy Manager?
Nginx Proxy Manager is a user-friendly web interface that simplifies the configuration and management of nginx reverse proxy servers. Unlike traditional nginx configurations that require manual editing of complex configuration files, this tool provides a streamlined dashboard for managing proxy hosts, SSL certificates, and access controls.
The platform excels in several key areas that make it particularly valuable for system administrators and developers. SSL certificate management becomes effortless with automatic Let’s Encrypt integration, eliminating the manual process of certificate generation and renewal. The intuitive web interface allows users to create and modify proxy configurations without deep nginx knowledge, while advanced features like custom headers, websocket support, and caching provide enterprise-level functionality.
Common use cases include home lab environments where multiple services need external access, business deployments requiring secure application routing, and development environments where rapid configuration changes are essential. The tool particularly shines in scenarios involving multiple subdomains, complex routing requirements, or environments where non-technical users need to manage proxy configurations.
Why Use Fedora 42?
Fedora 42 represents the latest advancement in Red Hat’s community-driven Linux distribution, offering several compelling advantages for hosting proxy management solutions. Cutting-edge package availability ensures access to the most recent versions of Docker, nginx, and associated tools, while robust security frameworks like SELinux provide enhanced protection against potential vulnerabilities.
The distribution’s DNF package manager delivers superior dependency resolution and update management compared to many alternatives. Fedora’s rapid release cycle means security patches and feature updates arrive quickly, maintaining system security and functionality. Additionally, enterprise-grade stability inherited from Red Hat’s enterprise focus provides confidence in production deployments.
Compared to Ubuntu or Debian-based systems, Fedora offers more recent kernel versions and cutting-edge technologies. For Nginx Proxy Manager specifically, Fedora’s container support, firewall management tools, and systemd integration create an optimal hosting environment that balances innovation with reliability.
Prerequisites and System Preparation
Successful Nginx Proxy Manager deployment requires proper system preparation and understanding of minimum requirements. Hardware specifications should include at least 1GB RAM, 10GB available disk space, and a dual-core processor, though 2GB RAM is recommended for optimal performance.
System backup represents a critical preparatory step that many administrators overlook. Create comprehensive backups of configuration files, user data, and system snapshots before beginning installation. This precaution enables rapid recovery if complications arise during the deployment process.
Update your Fedora 42 system to ensure all packages reflect the latest security patches and bug fixes:
sudo dnf update -y
sudo dnf upgrade -y
sudo systemctl rebootNetwork configuration verification ensures proper connectivity and domain resolution. Test internet connectivity, verify DNS resolution functionality, and confirm that required ports (80, 443, 81) are available for use. User permissions should be configured to allow sudo access for the installation user, as many commands require elevated privileges.
Document your current system configuration, including running services, open ports, and custom configurations. This documentation proves invaluable for troubleshooting and future maintenance activities.
Installing Essential Dependencies
Nginx Proxy Manager requires several core dependencies that must be installed and configured before proceeding with the main installation. Docker containerization provides the most reliable deployment method, though native installation remains an option for specific use cases.
Install Docker and related components using Fedora’s DNF package manager:
sudo dnf install -y dnf-plugins-core
sudo dnf config-manager --add-repo https://download.docker.com/linux/fedora/docker-ce.repo
sudo dnf install -y docker-ce docker-ce-cli containerd.io docker-buildx-plugin docker-compose-pluginGit installation enables repository cloning and version control capabilities:
sudo dnf install -y git curl wgetStart and enable Docker services to ensure automatic startup on system boot:
sudo systemctl enable --now docker
sudo usermod -aG docker $USERService verification confirms proper installation and functionality:
docker --version
docker compose version
systemctl status dockerLog out and back in to apply group membership changes, or use newgrp docker to refresh group permissions without logging out.
Choosing Deployment Method: Docker vs Native Installation
Understanding the deployment options helps determine the most appropriate installation method for your specific environment and requirements. Docker containerization offers significant advantages including simplified dependency management, easy updates, and isolated execution environments that prevent conflicts with system packages.
Docker benefits include consistent behavior across different systems, simplified backup and restoration procedures, and the ability to run multiple isolated instances. Container deployment also facilitates easy version rollbacks and provides clear separation between application and system dependencies.
Native installation advantages include potentially better performance due to reduced containerization overhead, deeper system integration, and more granular control over individual components. However, native deployment requires more complex dependency management and update procedures.
Scalability considerations favor Docker deployment for most scenarios, as container orchestration tools enable horizontal scaling and load distribution. Security implications vary, with containers providing process isolation while native installations offer more direct system integration options.
For most users, Docker deployment represents the optimal choice due to its simplicity, reliability, and maintainability advantages.
Installing Docker and Docker Compose on Fedora 42
Docker installation on Fedora 42 requires adding the official Docker repository to ensure access to the latest stable versions. Repository configuration provides more recent versions than the default Fedora repositories and ensures proper security updates.
Configure the Docker repository and install required packages:
sudo dnf remove -y docker docker-client docker-client-latest docker-common docker-latest docker-latest-logrotate docker-logrotate docker-selinux docker-engine-selinux docker-engine
sudo dnf install -y dnf-plugins-core
sudo dnf config-manager --add-repo https://download.docker.com/linux/fedora/docker-ce.repo
sudo dnf install -y docker-ce docker-ce-cli containerd.io docker-buildx-plugin docker-compose-pluginService configuration ensures Docker starts automatically and runs with appropriate permissions:
sudo systemctl enable docker
sudo systemctl start docker
sudo usermod -aG docker $USERInstallation verification confirms proper functionality and version information:
docker --version
docker compose version
sudo docker run --rm hello-worldTroubleshooting common issues may involve SELinux configuration adjustments or firewall modifications. If Docker fails to start, check system logs using journalctl -u docker and verify that virtualization is enabled in BIOS settings.
Downloading and Configuring Nginx Proxy Manager (Docker Method)
Nginx Proxy Manager deployment using Docker requires creating a structured directory layout and configuration files that define service parameters, networking requirements, and persistent data storage locations. Directory organization provides clarity and simplifies maintenance procedures.
Create a dedicated directory structure for your Nginx Proxy Manager installation:
mkdir -p ~/nginx-proxy-manager/{data,letsencrypt}
cd ~/nginx-proxy-managerDocker Compose configuration defines all necessary services, networking, and volume mappings. Create a comprehensive docker-compose.yml file:
version: '3.8'
services:
nginx-proxy-manager:
image: 'jc21/nginx-proxy-manager:latest'
restart: unless-stopped
ports:
- '80:80'
- '81:81'
- '443:443'
volumes:
- ./data:/data
- ./letsencrypt:/etc/letsencrypt
environment:
DB_MYSQL_HOST: "db"
DB_MYSQL_PORT: 3306
DB_MYSQL_USER: "npm"
DB_MYSQL_PASSWORD: "npm_password_change_this"
DB_MYSQL_NAME: "npm"
depends_on:
- db
db:
image: 'mariadb:latest'
restart: unless-stopped
environment:
MYSQL_ROOT_PASSWORD: "root_password_change_this"
MYSQL_DATABASE: "npm"
MYSQL_USER: "npm"
MYSQL_PASSWORD: "npm_password_change_this"
volumes:
- ./mysql:/var/lib/mysqlSecurity considerations require changing default passwords and implementing proper access controls. Volume mapping ensures data persistence across container restarts and provides easy backup access.
Starting Nginx Proxy Manager with Docker Compose
Container deployment involves initializing services, monitoring startup processes, and verifying proper functionality across all components. Service orchestration through Docker Compose coordinates database initialization and application startup sequences.
Launch your Nginx Proxy Manager installation:
cd ~/nginx-proxy-manager
docker compose up -dStartup monitoring helps identify potential issues early in the deployment process:
docker compose logs -f
docker compose psHealth verification ensures all services are running correctly and accepting connections:
docker compose exec nginx-proxy-manager nginx -t
curl -I http://localhost:81Troubleshooting startup issues may involve checking container logs, verifying port availability, and ensuring proper file permissions. Common problems include port conflicts, insufficient disk space, or database connection failures.
Monitor initial database setup and application initialization through log output. Database initialization typically takes several minutes during first startup, so patience is essential during initial deployment.
Native (Manual) Installation Process (Optional)
Manual installation provides maximum control and customization options, though it requires more extensive system administration knowledge and ongoing maintenance responsibilities. Native deployment suits environments where containerization is not desired or permitted.
Repository cloning and dependency installation form the foundation of manual deployment:
git clone https://github.com/NginxProxyManager/nginx-proxy-manager.git
cd nginx-proxy-manager
sudo dnf install -y nodejs npm nginx mariadb-serverDatabase configuration requires manual setup and security hardening:
sudo systemctl enable --now mariadb
sudo mysql_secure_installation
mysql -u root -pCreate the required database and user within the MySQL prompt:
CREATE DATABASE npm;
CREATE USER 'npm'@'localhost' IDENTIFIED BY 'secure_password_here';
GRANT ALL PRIVILEGES ON npm.* TO 'npm'@'localhost';
FLUSH PRIVILEGES;
EXIT;Application configuration involves building the project and configuring system services for automatic startup. This method requires ongoing maintenance and manual updates, making it less suitable for most deployments.
Configuring Fedora Firewall for Nginx Proxy Manager
Fedora’s firewalld provides robust network security through zone-based filtering and service-specific rules. Port configuration must accommodate HTTP (80), HTTPS (443), and administrative (81) traffic while maintaining security best practices.
Configure essential firewall rules for Nginx Proxy Manager operation:
sudo firewall-cmd --permanent --add-service=http
sudo firewall-cmd --permanent --add-service=https
sudo firewall-cmd --permanent --add-port=81/tcp
sudo firewall-cmd --reloadSecurity hardening involves restricting administrative access to trusted networks:
sudo firewall-cmd --permanent --add-rich-rule="rule family='ipv4' source address='192.168.1.0/24' port protocol='tcp' port='81' accept"
sudo firewall-cmd --permanent --remove-port=81/tcp
sudo firewall-cmd --reloadVerification procedures confirm proper rule application and connectivity:
sudo firewall-cmd --list-all
nmap -p 80,443,81 localhostAdvanced configurations may include custom zones, logging rules, and integration with intrusion detection systems. Zone management allows different security levels for various network interfaces and connection types.
Initial Access and Nginx Proxy Manager Dashboard
Accessing the Nginx Proxy Manager web interface marks the transition from installation to configuration and ongoing management. Initial connection requires navigating to your server’s IP address on port 81 using a web browser.
Default administrative credentials provide initial access:
- Email: admin@example.com
- Password: changeme
First login procedures mandate immediate password changes and administrative email updates to ensure security. The system enforces strong password requirements and may require additional security configurations.
Dashboard navigation reveals several key sections including Proxy Hosts, Redirection Hosts, Streams, Access Lists, and Certificates. Interface orientation helps new users understand available functionality and workflow patterns.
User account management allows creation of additional administrative users, role assignment, and access control implementation. Security configuration includes enabling two-factor authentication, session timeout settings, and audit logging capabilities.
Adding Your First Proxy Host
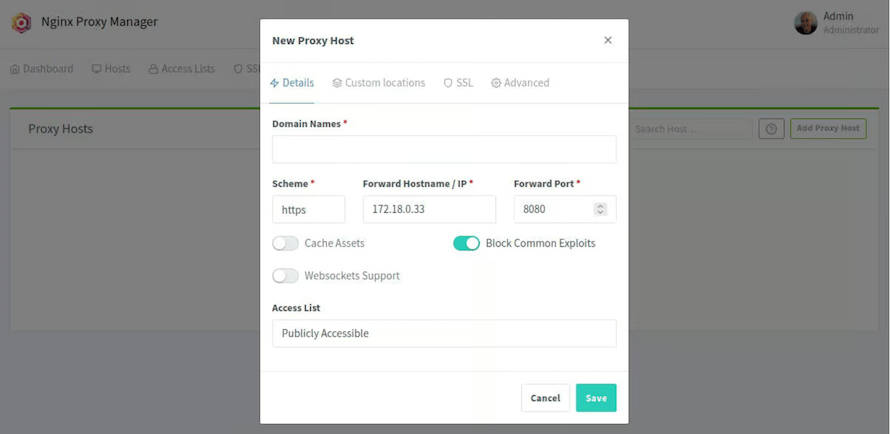
Proxy host creation represents the core functionality that makes Nginx Proxy Manager valuable for managing web services and applications. Host configuration involves defining source domains, destination services, and routing parameters.
Navigate to the Proxy Hosts section and select Add Proxy Host. Basic configuration requires several essential parameters:
- Domain Names: Enter the fully qualified domain name that users will access
- Scheme: Select HTTP or HTTPS for the backend service
- Forward Hostname/IP: Specify the internal server address
- Forward Port: Define the backend service port
Advanced options provide additional functionality including custom headers, caching configurations, and WebSocket support. Custom locations enable complex routing scenarios and API endpoint management.
SSL configuration can be configured immediately or added later through the SSL tab. Access control allows restricting access through IP allowlists, geographic restrictions, or authentication requirements.
Testing procedures verify proper proxy functionality:
curl -H "Host: your-domain.com" http://your-server-ip
nslookup your-domain.comTroubleshooting common issues includes verifying DNS configuration, checking backend service availability, and reviewing nginx error logs.
Securing Connections with Free SSL Certificates (Let’s Encrypt)
SSL certificate management through Let’s Encrypt integration provides automated certificate provisioning, renewal, and validation without manual intervention or recurring costs. Certificate automation eliminates traditional certificate management complexity while maintaining enterprise-grade security.
Let’s Encrypt configuration requires valid domain names with proper DNS resolution pointing to your server. Domain validation occurs through HTTP-01 or DNS-01 challenge methods, with HTTP-01 being the default and most straightforward approach.
Navigate to your proxy host configuration and select the SSL tab. Certificate request involves selecting Request a new SSL Certificate and choosing Use a Let’s Encrypt Certificate:
- Force SSL: Automatically redirect HTTP to HTTPS
- HTTP/2 Support: Enable modern protocol features
- HSTS Enabled: Implement HTTP Strict Transport Security
- HSTS Subdomains: Extend HSTS to all subdomains
Automatic renewal occurs every 60 days through automated processes. Renewal monitoring helps identify potential issues before certificates expire:
docker compose exec nginx-proxy-manager certbot certificates
docker compose logs nginx-proxy-manager | grep -i certTroubleshooting SSL issues may involve verifying domain ownership, checking DNS propagation, or resolving rate limiting constraints from Let’s Encrypt.
Managing Users, Access, and Permissions
User management capabilities enable team collaboration and role-based access control for organizations managing multiple services and administrators. Multi-user environments benefit from granular permission systems and audit capabilities.
User creation involves navigating to the Users section and selecting Add User. Role assignment determines access levels and administrative capabilities:
- Admin: Full system access and configuration capabilities
- User: Limited access to specific proxy hosts or functions
Permission granularity allows restricting access to specific domains, certificate management, or user administration functions. Security policies should enforce strong password requirements, regular password changes, and account lockout procedures.
Best practices include regular user audits, removing unnecessary accounts, and implementing principle of least privilege access controls. Activity monitoring through audit logs helps track configuration changes and potential security incidents.
Common Troubleshooting and Maintenance Tips
Effective troubleshooting requires understanding common failure modes, diagnostic procedures, and resolution strategies for Nginx Proxy Manager deployments. Log analysis provides the foundation for identifying and resolving most operational issues.
Container log access reveals application-level information:
docker compose logs nginx-proxy-manager
docker compose logs db
journalctl -u dockerCommon issues and their resolution strategies:
- Certificate renewal failures: Check domain DNS, verify connectivity, review Let’s Encrypt rate limits
- Database connection errors: Verify credentials, check container networking, review database logs
- Proxy host unreachable: Confirm backend service status, verify network connectivity, check firewall rules
- Performance issues: Monitor resource usage, review cache settings, optimize database queries
Update procedures ensure security patches and feature improvements:
cd ~/nginx-proxy-manager
docker compose pull
docker compose up -dBackup strategies protect against data loss and enable rapid recovery:
# Backup configuration and data
tar -czf npm-backup-$(date +%Y%m%d).tar.gz data/ letsencrypt/ docker-compose.yml
# Database backup
docker compose exec db mysqldump -u npm -p npm > npm-database-backup-$(date +%Y%m%d).sqlRemoving or Upgrading Nginx Proxy Manager
System maintenance occasionally requires removing or upgrading Nginx Proxy Manager installations. Proper procedures prevent data loss and ensure clean system states for future installations.
Upgrade procedures using Docker Compose:
cd ~/nginx-proxy-manager
docker compose down
docker compose pull
docker compose up -dComplete removal when Nginx Proxy Manager is no longer needed:
cd ~/nginx-proxy-manager
docker compose down -v
cd ..
rm -rf nginx-proxy-manager/
docker image prune -fData preservation during upgrades or migrations requires comprehensive backup procedures and verification of backup integrity before proceeding with system changes.
Best Practices for Security & Performance
Production deployments require implementing security hardening and performance optimization measures that go beyond basic installation requirements. Security frameworks should address access controls, network security, and monitoring capabilities.
Essential security measures:
- Regular updates: Maintain current versions of all components
- Access restriction: Limit administrative interface access to trusted networks
- Strong authentication: Implement complex passwords and consider two-factor authentication
- Monitoring: Enable comprehensive logging and alerting for security events
Performance optimization techniques include:
- Resource monitoring: Track CPU, memory, and disk usage patterns
- Cache configuration: Implement appropriate caching strategies for static content
- Database optimization: Regular maintenance and query optimization
- Network tuning: Optimize nginx worker processes and connection handling
Monitoring solutions provide visibility into system health and performance metrics. Automated alerting enables proactive response to potential issues before they impact service availability.
Congratulations! You have successfully installed Nginx Proxy Manager. Thanks for using this tutorial for installing Nginx Proxy Manager on Fedora 42 system. For additional help or useful information, we recommend you check the official Nginx website.