How To Install Nginx Proxy Manager on Fedora 43

Managing multiple web applications and services can quickly become complex, especially when configuring reverse proxies and SSL certificates. Nginx Proxy Manager simplifies this entire process through an intuitive web-based interface that eliminates the need for manual Nginx configuration files. This powerful tool provides centralized management for all your proxy hosts, automatic SSL certificate generation through Let’s Encrypt, and robust access control features.
Fedora 43 offers an excellent foundation for hosting Nginx Proxy Manager, providing cutting-edge packages and strong security features. The Docker-based installation method ensures consistency, portability, and simplified maintenance. Whether you’re running a home lab, managing multiple client websites, or deploying production services, this guide walks you through every step of the installation process.
You’ll learn how to prepare your Fedora 43 system, install Docker and Docker Compose, deploy Nginx Proxy Manager, configure your first proxy host with SSL encryption, and implement security best practices. By following these detailed instructions, you’ll have a fully functional reverse proxy management system running within 30 minutes.
What is Nginx Proxy Manager?
Nginx Proxy Manager is a pre-built Docker container that provides a beautiful web interface for managing Nginx reverse proxy configurations. Instead of manually editing complex configuration files, you can create proxy hosts, request SSL certificates, and implement access controls through an intuitive dashboard.
The application sits in front of your web services and routes incoming traffic to the appropriate backend application. It handles SSL termination, allowing your internal services to run without HTTPS while still providing encrypted connections to end users. This architecture significantly reduces configuration complexity while enhancing security.
Key features include Let’s Encrypt SSL certificate integration with automatic renewal, stream forwarding for non-HTTP protocols, customizable access lists with HTTP authentication or IP whitelisting, and full support for WebSockets and HTTP/2. The solution works perfectly for home server enthusiasts, system administrators, and developers managing multiple web applications across different ports or servers.
The Docker-based deployment approach offers several advantages. Updates become straightforward with simple container recreation. Configuration persistence through volume mounts ensures your settings survive container restarts. Resource isolation prevents conflicts with other system services, while the standardized installation process works consistently across different Linux distributions including Fedora 43.
Prerequisites and System Requirements
Before beginning the installation, ensure your system meets the necessary hardware and software requirements. A minimum of 1GB RAM is required, though 2GB or more is recommended for optimal performance when managing multiple proxy hosts. Your system should have at least 20GB of available disk space to accommodate the operating system, Docker images, and SSL certificate storage.
Your Fedora 43 installation should be relatively fresh with administrative privileges available. You’ll need either root access or a user account with sudo permissions to execute system-level commands. An active internet connection is essential for downloading packages, Docker images, and requesting SSL certificates from Let’s Encrypt.
Network configuration requires attention to specific ports. Port 80 handles HTTP traffic and is necessary for Let’s Encrypt HTTP-01 challenge validation. Port 443 manages HTTPS traffic for secure connections. Port 81 provides access to the Nginx Proxy Manager administrative interface. Ensure these ports aren’t already occupied by other services on your system.
If you plan to use custom domain names with SSL certificates, you’ll need ownership of at least one domain with the ability to create DNS records. A static IP address or dynamic DNS service ensures consistent accessibility. For remote server management, SSH access allows secure command-line administration.
Basic familiarity with Linux command-line operations will help you follow along smoothly. Understanding fundamental networking concepts like DNS resolution, port forwarding, and reverse proxies provides helpful context, though detailed explanations accompany each step.
Step 1: Update Fedora 43 System
Starting with a fully updated system ensures you have the latest security patches and bug fixes. Open your terminal application and execute the system update command. This process synchronizes your package repositories and downloads available updates.
sudo dnf update -y
The -y flag automatically confirms any prompts, allowing the update process to complete without manual intervention. Depending on how recently you installed Fedora 43, this may download several hundred megabytes of updates.
After the update completes, upgrade your system to apply any pending kernel or core system updates:
sudo dnf upgrade -y
If kernel updates were installed, a system reboot ensures the new kernel loads properly. Check if a reboot is needed by examining the update output for kernel package mentions. Restart your system with:
sudo reboot
After rebooting, reconnect to your system and verify the update succeeded by checking your Fedora version:
cat /etc/fedora-release
This displays your current Fedora version, confirming you’re running Fedora 43.
Step 2: Install Docker and Docker Compose
Nginx Proxy Manager runs as a Docker container, providing isolation, portability, and simplified management. Docker Compose orchestrates multi-container applications through simple YAML configuration files, making deployment and updates straightforward.
Begin by installing the DNF plugins core package, which provides additional repository management capabilities:
sudo dnf install -y dnf-plugins-core
Next, add the official Docker repository to your system. This ensures you receive Docker packages directly from Docker Inc. rather than potentially outdated versions from Fedora repositories:
sudo dnf config-manager --add-repo https://download.docker.com/linux/fedora/docker-ce.repo
Now install Docker Engine along with its required components. This includes the Docker daemon, command-line interface, containerd runtime, and Docker Compose plugin:
sudo dnf install -y docker-ce docker-ce-cli containerd.io docker-buildx-plugin docker-compose-plugin
The installation process downloads several hundred megabytes of packages and their dependencies. Once complete, start the Docker service:
sudo systemctl start docker
Enable Docker to start automatically at system boot:
sudo systemctl enable docker
By default, Docker requires root privileges for all operations. Add your current user to the docker group to run Docker commands without sudo:
sudo usermod -aG docker $USER
This change takes effect after you log out and log back in. Alternatively, activate the group membership immediately with:
newgrp docker
Verify your Docker installation by running the test container:
docker run hello-world
This downloads a minimal test image and executes it. Successful output confirms Docker is properly installed and operational. You’ll see a message beginning with “Hello from Docker!” followed by information about how the test worked.
Check your Docker Compose installation:
docker compose version
This displays the installed Docker Compose version, confirming the plugin is available.
Step 3: Configure Firewall for Nginx Proxy Manager
Fedora 43 includes firewalld by default, providing robust network security. You must open the necessary ports for Nginx Proxy Manager to function correctly while maintaining system security.
First, verify the firewall is running:
sudo firewall-cmd --state
If the output shows “running,” proceed with port configuration. Open port 80 for HTTP traffic, which Let’s Encrypt requires for domain validation:
sudo firewall-cmd --permanent --add-port=80/tcp
Open port 443 for HTTPS encrypted traffic:
sudo firewall-cmd --permanent --add-port=443/tcp
Open port 81 for the Nginx Proxy Manager administrative interface:
sudo firewall-cmd --permanent --add-port=81/tcp
The --permanent flag ensures these rules persist across system reboots. However, permanent rules don’t take effect immediately. Reload the firewall configuration to apply changes:
sudo firewall-cmd --reload
Verify all three ports are now open:
sudo firewall-cmd --list-ports
The output should display 80/tcp 443/tcp 81/tcp, confirming successful configuration.
For enhanced security in production environments, consider restricting port 81 access to specific IP addresses. This prevents unauthorized access to your administrative interface from the public internet. You can implement this restriction later once Nginx Proxy Manager is operational.
Step 4: Create Directory Structure for NPM
Organizing your Nginx Proxy Manager installation in a dedicated directory structure simplifies management and ensures data persistence. Create a directory in your home folder:
mkdir -p ~/nginx-proxy-manager
Navigate into this directory:
cd ~/nginx-proxy-manager
Create subdirectories for persistent data storage:
mkdir -p data letsencrypt
The data directory stores Nginx Proxy Manager’s database, configuration files, and operational data. The letsencrypt directory holds SSL certificates and related files from Let’s Encrypt. These volume mounts ensure your configurations and certificates survive container restarts or updates.
Docker runs containers with specific user permissions. The directory structure you’ve created is owned by your user account, which works correctly for this installation method. More complex deployments might require explicit permission management, but the default configuration handles this installation appropriately.
Step 5: Create Docker Compose Configuration File
Docker Compose uses YAML files to define container configurations, making deployments reproducible and manageable. Create a new docker-compose.yml file in your nginx-proxy-manager directory:
nano docker-compose.yml
If you prefer a different text editor like vim or vi, substitute that command instead. Enter the following configuration:
version: '3.8'
services:
app:
image: 'jc21/nginx-proxy-manager:latest'
restart: unless-stopped
ports:
- '80:80'
- '81:81'
- '443:443'
volumes:
- ./data:/data
- ./letsencrypt:/etc/letsencrypt
Let’s examine each section of this configuration. The version specification indicates Docker Compose file format compatibility. Version 3.8 provides modern features while maintaining broad compatibility.
The services section defines containers to deploy. The app service runs Nginx Proxy Manager. The image line specifies the Docker Hub image to use, pulling the latest version from the jc21/nginx-proxy-manager repository.
The restart: unless-stopped policy ensures the container automatically restarts after system reboots or Docker daemon restarts, unless you explicitly stop it. This maintains service availability without manual intervention.
Port mappings follow the format host:container. The configuration maps port 80 on your Fedora system to port 80 in the container, and similarly for ports 81 and 443. This allows external traffic to reach the containerized application.
Volume mounts link directories on your host system to paths inside the container. The ./data:/data mapping connects your local data directory to the container’s /data path, where Nginx Proxy Manager stores its configuration. The ./letsencrypt:/etc/letsencrypt mapping persists SSL certificates.
Save the file by pressing Ctrl+O, then Enter, and exit nano with Ctrl+X. Your Docker Compose configuration is now ready for deployment.
Step 6: Deploy Nginx Proxy Manager Container
With your configuration file created, deploying Nginx Proxy Manager requires a single command. From your nginx-proxy-manager directory, execute:
docker compose up -d
The -d flag runs containers in detached mode, allowing them to operate in the background while returning control to your terminal. Docker Compose reads your docker-compose.yml file, downloads the Nginx Proxy Manager image if not already present, and creates the container.
The first run downloads approximately 200-300MB of image data. Subsequent deployments use the cached image unless you explicitly update it. Progress indicators show the download status for each image layer.
Once deployment completes, verify the container is running:
docker compose ps
This displays all containers defined in your docker-compose.yml file along with their current status. You should see the app service with a “running” state.
View container logs to ensure successful startup:
docker compose logs -f app
The -f flag follows log output in real-time, similar to tail -f. You’ll see initialization messages as Nginx Proxy Manager prepares its database and starts services. Look for messages indicating successful startup. Press Ctrl+C to stop following logs.
Check that the container is listening on the expected ports:
docker ps
This shows all running Docker containers. The Nginx Proxy Manager container should display port mappings for 80, 81, and 443.
If you encounter errors about port conflicts, another service is already using one of the required ports. Identify the conflicting service with sudo ss -tulpn | grep ':80' (replace 80 with the conflicting port number). Stop the conflicting service or modify your Nginx Proxy Manager configuration to use alternative ports.
Step 7: Access Nginx Proxy Manager Web Interface
With the container running, access the administrative interface through your web browser. Determine your server’s IP address:
hostname -I
This displays all IP addresses assigned to your system. Use the first address listed, which is typically your primary network interface. If accessing from the server itself, you can use localhost instead.
Open your web browser and navigate to:
http://YOUR_SERVER_IP:81
Replace YOUR_SERVER_IP with your actual IP address. For example: http://192.168.1.100:81
The Nginx Proxy Manager login screen appears after a few seconds. Use the default credentials for initial access:
- Email:
admin@example.com - Password:
changeme
After logging in, the system immediately prompts you to change these default credentials. This critical security step prevents unauthorized access to your proxy manager. Enter your email address and choose a strong password combining uppercase letters, lowercase letters, numbers, and special characters.
The main dashboard provides an overview of your proxy hosts, SSL certificates, and system health. The left sidebar contains navigation links for Proxy Hosts, Redirection Hosts, Streams, 404 Hosts, Users, Access Lists, and SSL Certificates. Take a moment to familiarize yourself with the interface layout.
Step 8: Configure Your First Proxy Host
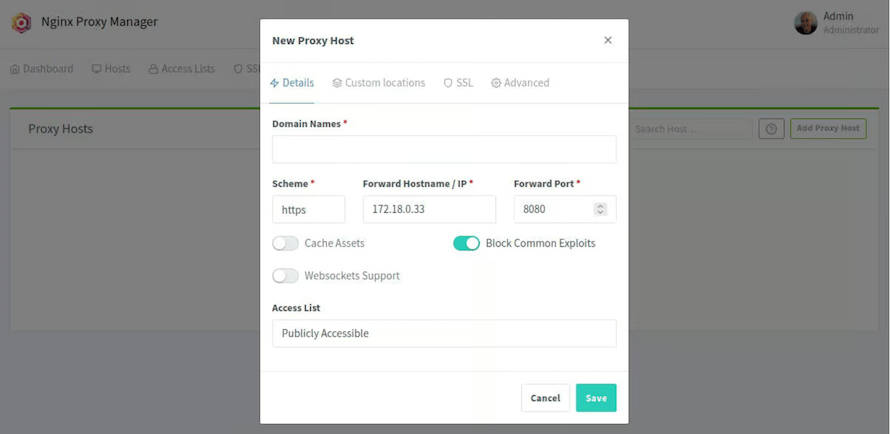
Creating a proxy host routes external traffic from a domain name to an internal service. This process demonstrates the core functionality of Nginx Proxy Manager. Click “Hosts” in the sidebar, then select “Proxy Hosts,” and click “Add Proxy Host.”
The configuration dialog contains three tabs: Details, SSL, and Advanced. In the Details tab, enter your domain name in the “Domain Names” field. This should be a fully qualified domain name like app.yourdomain.com that you control. Add multiple domains by clicking the additional domain field if needed.
Set the Scheme to http if your backend service runs on HTTP, or https if it already uses HTTPS. Most internal services use HTTP, relying on Nginx Proxy Manager for SSL termination.
Enter the Forward Hostname/IP address of your backend service. This could be localhost for services on the same server, a LAN IP address like 192.168.1.50 for services on your network, or a Docker container name if using Docker networking.
Specify the Forward Port number your backend service listens on. For example, a web application might use port 3000, while a Plex server uses port 32400.
Enable “Block Common Exploits” to activate basic security rules that prevent common attack patterns. This adds protection against SQL injection attempts, path traversal attacks, and other exploit techniques.
Enable “Websockets Support” if your backend application uses WebSocket connections for real-time communication. Many modern web applications, chat systems, and live update features require this.
Switch to the SSL tab to configure HTTPS encryption. Select “Request a new SSL Certificate” from the dropdown menu. This initiates a Let’s Encrypt certificate request for your domain.
Enter your email address for Let’s Encrypt notifications about certificate expiration or issues. Let’s Encrypt sends renewal reminders and security notifications to this address.
Enable “Force SSL” to automatically redirect all HTTP traffic to HTTPS. This ensures users always access your service through encrypted connections.
Enable “HTTP/2 Support” for improved performance with modern browsers. HTTP/2 provides faster page loads through multiplexing and header compression.
Optionally enable “HSTS Enabled” for enhanced security. HTTP Strict Transport Security tells browsers to always use HTTPS for your domain, preventing SSL strip attacks. Only enable this after confirming your SSL setup works correctly, as HSTS can cause access issues if misconfigured.
Click “Save” to create the proxy host. Nginx Proxy Manager immediately requests the SSL certificate from Let’s Encrypt. This process typically completes within 30 seconds, though it requires your domain’s DNS A record to point to your server’s IP address.
If certificate issuance fails, verify your domain’s DNS configuration propagated correctly using online DNS lookup tools. Ensure port 80 is accessible from the internet, as Let’s Encrypt uses HTTP-01 challenges to verify domain ownership. Check your router’s port forwarding rules if running Nginx Proxy Manager behind NAT.
Test your new proxy host by accessing your domain in a web browser. You should see your backend service with a valid SSL certificate, indicated by the padlock icon in your browser’s address bar.
Step 9: Managing SSL Certificates
Click “SSL Certificates” in the sidebar to view all certificates managed by Nginx Proxy Manager. Each certificate displays its domain names, expiration date, and status. Let’s Encrypt certificates remain valid for 90 days, with Nginx Proxy Manager automatically renewing them approximately 30 days before expiration.
The automatic renewal process runs daily, checking all certificates and renewing those approaching expiration. This eliminates manual certificate management, a significant advantage over traditional Nginx configurations.
To request a certificate without immediately creating a proxy host, click “Add SSL Certificate.” Choose “Let’s Encrypt” as the provider and enter your domain names. This approach works well when preparing certificates before configuring services.
Wildcard certificates cover all subdomains under a domain, like *.yourdomain.com. Request wildcard certificates using DNS-01 challenge validation instead of HTTP-01. This requires API access to your DNS provider for automatic record creation. Nginx Proxy Manager supports several popular DNS providers including Cloudflare, Google Cloud DNS, and Route53.
Custom certificates allow uploading SSL certificates purchased from commercial certificate authorities. This option suits organizations with specific compliance requirements or existing certificate investments. Upload the certificate file, private key file, and intermediate certificate chain file when adding custom certificates.
View certificate details by clicking the certificate entry. The details panel shows the full certificate chain, expiration date, and associated proxy hosts. Force immediate renewal by clicking the renewal button if needed, though the automatic system handles this reliably under normal circumstances.
Step 10: Implementing Access Control
Access Lists restrict who can access your proxy hosts through HTTP authentication or IP-based filtering. Navigate to “Access Lists” in the sidebar and click “Create Access List.”
Give your access list a descriptive name like “Admin Panel Access” or “Development Team Only.” The name helps identify the list’s purpose when assigning it to proxy hosts.
In the Authorization section, click “Add” to create username and password combinations. Enter a username and strong password for each authorized user. The system stores passwords securely using bcrypt hashing.
The Access section allows IP address filtering. Add IP addresses or CIDR ranges to the whitelist to permit access only from specific locations. Alternatively, add addresses to the blacklist to deny access from specific sources while allowing all others.
The “Satisfy Any” option allows access if either HTTP authentication succeeds or IP address matches the whitelist. “Satisfy All” requires both conditions to be met, providing stronger security for highly sensitive services.
Click “Save” to create the access list. Apply it to proxy hosts by editing existing hosts, selecting the “Details” tab, and choosing your access list from the dropdown menu. Save the proxy host to activate access restrictions.
When users attempt to access a protected proxy host, their browser displays an HTTP authentication prompt requesting username and password. Failed authentication attempts return an “Authorization Required” error.
Access lists prove valuable for internal tools, administrative interfaces, development environments, and any service requiring restricted access. Combine them with SSL certificates for comprehensive security covering both authentication and encryption.
Step 11: Managing and Maintaining NPM
Regular maintenance ensures Nginx Proxy Manager continues operating smoothly. Basic container management uses Docker Compose commands from your installation directory.
Stop the Nginx Proxy Manager container:
docker compose down
This gracefully stops and removes the container while preserving your data in the persistent volumes.
Restart the container to apply configuration changes or troubleshoot issues:
docker compose restart
Start the container after stopping it:
docker compose up -d
Update Nginx Proxy Manager to the latest version by pulling the new image:
docker compose pull
Then recreate the container with the updated image:
docker compose up -d
Docker detects the new image and recreates the container while preserving your data. The update process completes in seconds with minimal downtime.
Implement regular backups of your data directory to prevent configuration loss. Stop the container before backing up to ensure database consistency:
docker compose down
tar -czf npm-backup-$(date +%Y%m%d).tar.gz data letsencrypt docker-compose.yml
docker compose up -d
This creates a compressed archive containing all configuration data, SSL certificates, and your Docker Compose file. Store backups in a separate location or use automated backup solutions.
Monitor container resource usage with:
docker stats
This displays real-time CPU, memory, and network usage for all running containers. Nginx Proxy Manager typically uses minimal resources, consuming 50-100MB of RAM under normal operation.
View historical logs to troubleshoot issues:
docker compose logs --tail=100
This shows the last 100 log lines. Adjust the number to view more or fewer entries.
Troubleshooting Common Issues
Container startup failures often result from port conflicts. Check if another service uses ports 80, 81, or 443:
sudo ss -tulpn | grep -E ':(80|81|443)'
If conflicts exist, stop the conflicting service or modify your docker-compose.yml to use alternative ports.
Permission errors when accessing volumes indicate incorrect directory ownership. Ensure your user owns the data and letsencrypt directories:
ls -la ~/nginx-proxy-manager
Correct ownership issues with:
sudo chown -R $USER:$USER ~/nginx-proxy-manager/data ~/nginx-proxy-manager/letsencrypt
Inability to access the web interface typically indicates firewall issues. Verify firewall rules allow port 81:
sudo firewall-cmd --list-ports
Test port accessibility from another machine using telnet or netcat:
telnet YOUR_SERVER_IP 81
Proxy host connection failures require systematic debugging. First, verify the backend service is running and accessible from the Nginx Proxy Manager container. Test connectivity with:
docker compose exec app ping backend_hostname
Check DNS resolution if using domain names for backend services. Verify the backend service listens on the specified port.
SSL certificate request failures commonly occur when Let’s Encrypt cannot validate domain ownership. Ensure your domain’s DNS A record points to your server’s public IP address. Verify port 80 is accessible from the internet by using online port checkers. Check that your ISP doesn’t block port 80, which some residential providers do.
Let’s Encrypt implements rate limits preventing excessive certificate requests. If you receive rate limit errors, wait the specified period before retrying. Use Let’s Encrypt’s staging environment for testing by adding environment variables to your docker-compose.yml.
Performance issues rarely affect Nginx Proxy Manager itself. Instead, investigate backend service performance and network latency. Enable caching in proxy host configurations to improve response times for static assets.
Security Best Practices
- Change default administrative credentials immediately after first login. The default username and password are publicly documented, making them a security liability. Use a password manager to generate and store strong, unique passwords.
- Restrict administrative interface access by limiting port 81 to specific IP addresses. Configure firewall rules allowing only your management network:
sudo firewall-cmd --permanent --remove-port=81/tcp
sudo firewall-cmd --permanent --add-rich-rule='rule family="ipv4" source address="YOUR_IP/32" port port="81" protocol="tcp" accept'
sudo firewall-cmd --reload
Replace YOUR_IP with your management workstation’s IP address.
- Keep Nginx Proxy Manager updated by checking for new releases monthly. Subscribe to the project’s GitHub repository for security announcements. Updates often include security patches and vulnerability fixes.
- Enable “Block Common Exploits” for all proxy hosts to activate mod_security-inspired rules. These prevent common attack patterns without requiring complex WAF configuration.
- Implement access lists for administrative interfaces, development environments, and sensitive applications. Never expose administrative panels directly to the internet without authentication.
- Use strong SSL configurations by enabling “Force SSL” and “HTTP/2 Support” for all proxy hosts. Consider enabling HSTS for production sites after thorough testing.
- Regular backups protect against data loss from hardware failures, software bugs, or security incidents. Automate backup processes using cron jobs or backup utilities. Test backup restoration procedures periodically to ensure recoverability.
- Monitor access logs for suspicious activity patterns. Nginx Proxy Manager logs all requests, providing visibility into traffic patterns and potential security events.
- Keep your Fedora 43 system updated with security patches using regular
sudo dnf updateexecution. Enable automatic security updates for critical packages to reduce your security window. - Consider implementing fail2ban to automatically block IP addresses showing malicious behavior patterns. Configure fail2ban to monitor Nginx Proxy Manager logs for failed authentication attempts.
Congratulations! You have successfully installed Nginx Proxy Manager. Thanks for using this tutorial for installing Nginx Proxy Manager on Fedora 43 Linux system. For additional help or useful information, we recommend you check the official Nginx website.