How To Install Nginx Proxy Manager on Rocky Linux 10

Managing multiple web applications and services behind a single IP address can be challenging without the right tools. Nginx Proxy Manager (NPM) transforms this complex task into a straightforward process through its intuitive web-based interface. This powerful reverse proxy solution eliminates the need for manual Nginx configuration files while providing advanced features like automatic SSL certificate management, load balancing, and comprehensive access control.
Rocky Linux 10, the latest enterprise-grade distribution based on Red Hat Enterprise Linux, offers exceptional stability and security for production environments. When combined with Nginx Proxy Manager, it creates a robust foundation for hosting multiple applications, whether in homelab setups or enterprise deployments. This guide provides comprehensive instructions for installing and configuring NPM on Rocky Linux 10, ensuring optimal performance and security.
The installation process involves several critical components: Docker containerization, firewall configuration, SSL certificate automation, and proxy host management. Each step requires careful attention to security best practices and system optimization. By following this detailed walkthrough, administrators will establish a professional-grade reverse proxy solution capable of handling multiple domains, subdomains, and backend services efficiently.
Prerequisites and System Requirements
Before beginning the Nginx Proxy Manager installation, ensure your Rocky Linux 10 system meets the minimum hardware and software requirements. The system should have at least 1GB of RAM, though 2GB is recommended for optimal performance when handling multiple proxy hosts. Disk space requirements include a minimum of 10GB available storage, with additional space needed for SSL certificates, logs, and Docker containers.
A fresh Rocky Linux 10 installation provides the ideal starting point for this deployment. The system requires root or sudo access for installing packages, configuring services, and managing firewall rules. Network connectivity is essential for downloading Docker images, obtaining SSL certificates, and accessing external repositories. Additionally, having a registered domain name with proper DNS configuration enables full SSL certificate functionality and production-ready deployment.
Basic command-line proficiency is necessary for executing installation commands and troubleshooting potential issues. Familiarity with Docker concepts, while helpful, is not required as this guide covers all necessary container management tasks. Understanding fundamental networking concepts like port forwarding, DNS records, and reverse proxy functionality will enhance the learning experience and troubleshooting capabilities.
Step 1: Preparing Rocky Linux 10 System
System Updates and Package Management
Begin by updating the Rocky Linux 10 system to ensure all packages are current and security patches are applied. Connect to your server via SSH and execute the following commands with root privileges:
sudo dnf update -y
sudo dnf upgrade -yThis process updates the package index and installs the latest versions of installed packages. The update procedure may take several minutes depending on system specifications and internet connectivity. After completion, reboot the system to ensure all kernel updates and system changes take effect properly.
Install essential packages required for the NPM installation process. These packages provide necessary tools for repository management, network operations, and system administration:
sudo dnf install -y curl wget git nano vim unzip firewalld
sudo dnf install -y yum-utils device-mapper-persistent-data lvm2Creating Dedicated System Users
Establish a dedicated user account for managing Nginx Proxy Manager operations. This security best practice isolates NPM processes from the root user and provides better access control:
sudo useradd -m -s /bin/bash npmuser
sudo usermod -aG wheel npmuserSet a strong password for the new user account and configure sudo access. This approach ensures administrative tasks can be performed without using the root account directly:
sudo passwd npmuserCreate the necessary directory structure for NPM data persistence and configuration files. Proper directory organization facilitates easier maintenance and backup procedures:
sudo mkdir -p /opt/nginx-proxy-manager
sudo chown npmuser:npmuser /opt/nginx-proxy-manager
sudo chmod 755 /opt/nginx-proxy-managerStep 2: Installing Docker and Docker Compose
Docker Repository Configuration
Docker serves as the containerization platform for running Nginx Proxy Manager. Rocky Linux 10 requires the official Docker repository for accessing the latest Docker Engine releases. Remove any existing Docker installations to prevent conflicts:
sudo dnf remove docker docker-client docker-client-latest docker-common
sudo dnf remove docker-latest docker-latest-logrotate docker-logrotate docker-engineAdd the official Docker repository to the DNF package manager. This ensures access to the most recent Docker versions with security updates and feature enhancements:
sudo dnf config-manager --add-repo https://download.docker.com/linux/centos/docker-ce.repoThe repository configuration enables automatic updates and provides access to Docker CE (Community Edition), Docker CLI tools, and containerd runtime components.
Docker Engine Installation
Install Docker Engine, CLI tools, and the Docker Compose plugin using DNF package manager. This comprehensive installation provides all components necessary for container management:
sudo dnf install -y docker-ce docker-ce-cli containerd.io
sudo dnf install -y docker-buildx-plugin docker-compose-pluginStart the Docker service and enable automatic startup on system boot. These commands ensure Docker availability across system restarts:
sudo systemctl start docker
sudo systemctl enable dockerVerify the Docker installation by checking the service status and running a test container. This validation confirms proper installation and functionality:
sudo systemctl status docker
sudo docker run hello-worldDocker User Configuration
Add the npmuser to the Docker group to enable container management without sudo privileges. This configuration streamlines NPM operations and improves security by avoiding unnecessary root access:
sudo usermod -aG docker npmuser
newgrp dockerTest Docker access with the npmuser account to ensure proper group membership and permissions:
su - npmuser
docker --version
docker compose versionThe successful execution of these commands confirms Docker is properly installed and configured for NPM deployment.
Step 3: Configuring Firewall for NPM
Firewall Service Setup
Rocky Linux 10 includes firewalld as the default firewall management tool. Ensure the firewall service is active and properly configured before proceeding with NPM installation:
sudo systemctl start firewalld
sudo systemctl enable firewalld
sudo firewall-cmd --stateOpening Required Ports
Nginx Proxy Manager requires specific ports for HTTP traffic, HTTPS traffic, and administrative access. Configure these ports using firewalld’s permanent rules to ensure persistence across reboots:
sudo firewall-cmd --permanent --zone=public --add-service=http
sudo firewall-cmd --permanent --zone=public --add-service=https
sudo firewall-cmd --permanent --zone=public --add-port=81/tcpThe port 81 provides access to the NPM administrative interface, while ports 80 and 443 handle HTTP and HTTPS traffic respectively. Apply the firewall changes and verify the configuration:
sudo firewall-cmd --reload
sudo firewall-cmd --list-allSecurity Considerations
Consider implementing additional security measures for production environments. These may include restricting administrative access to specific IP addresses or implementing fail2ban for brute force protection:
sudo firewall-cmd --permanent --zone=public --add-rich-rule="rule family='ipv4' source address='YOUR_IP_ADDRESS' port port='81' protocol='tcp' accept"Replace “YOUR_IP_ADDRESS” with the actual IP address from which administrative access is required. This restriction enhances security by limiting NPM interface access to authorized sources only.
Step 4: Installing Nginx Proxy Manager
Project Directory Structure
Create a dedicated directory structure for the NPM deployment. Proper organization facilitates easier maintenance, backups, and updates:
cd /opt/nginx-proxy-manager
mkdir -p data letsencryptSwitch to the npmuser account for the remaining installation steps. This security practice ensures proper file ownership and permissions:
su - npmuser
cd /opt/nginx-proxy-managerDocker Compose Configuration
Create the docker-compose.yml file that defines the NPM container configuration. This file specifies container images, volume mounts, port mappings, and network settings:
nano docker-compose.ymlInsert the following Docker Compose configuration, which includes the latest NPM image and proper volume persistence:
version: '3.8'
services:
app:
image: 'jc21/nginx-proxy-manager:latest'
container_name: nginx-proxy-manager
restart: unless-stopped
ports:
- '80:80'
- '443:443'
- '81:81'
volumes:
- ./data:/data
- ./letsencrypt:/etc/letsencrypt
environment:
DISABLE_IPV6: 'true'
healthcheck:
test: ["CMD", "/bin/check-health"]
interval: 10s
timeout: 3s
retries: 3This configuration includes health checking for container monitoring and IPv6 disable option for simplified network configuration. Save and exit the file using Ctrl+X, then Y, then Enter.
Advanced Database Configuration
For production environments requiring enhanced performance, consider implementing a dedicated MariaDB database. Create an extended docker-compose.yml file with database integration:
version: '3.8'
services:
app:
image: 'jc21/nginx-proxy-manager:latest'
container_name: nginx-proxy-manager
restart: unless-stopped
ports:
- '80:80'
- '443:443'
- '81:81'
environment:
DB_MYSQL_HOST: "db"
DB_MYSQL_PORT: 3306
DB_MYSQL_USER: "npm"
DB_MYSQL_PASSWORD: "npm_secure_password"
DB_MYSQL_NAME: "npm"
DISABLE_IPV6: 'true'
volumes:
- ./data:/data
- ./letsencrypt:/etc/letsencrypt
depends_on:
- db
healthcheck:
test: ["CMD", "/bin/check-health"]
interval: 10s
timeout: 3s
retries: 3
db:
image: 'mariadb:latest'
container_name: npm-database
restart: unless-stopped
environment:
MYSQL_ROOT_PASSWORD: "root_secure_password"
MYSQL_DATABASE: "npm"
MYSQL_USER: "npm"
MYSQL_PASSWORD: "npm_secure_password"
volumes:
- ./mysql:/var/lib/mysqlReplace the placeholder passwords with strong, unique passwords for enhanced security. This configuration provides improved performance and scalability for environments managing numerous proxy hosts.
Deploying NPM
Launch the Nginx Proxy Manager using Docker Compose. This command downloads the necessary container images and starts the services:
docker compose up -dMonitor the container startup process to ensure successful deployment:
docker compose logs -fVerify that all containers are running properly:
docker compose psThe output should display the NPM container in an “Up” state with proper port mappings. If issues occur, review the logs for error messages and troubleshooting information.
Step 5: Initial NPM Configuration
Accessing Administrative Interface
Open a web browser and navigate to your server’s IP address on port 81. The NPM login interface should display, indicating successful installation:
http://YOUR_SERVER_IP:81Use the default administrator credentials for initial login:
- Email: admin@example.com
- Password: changeme
These credentials provide temporary access for initial configuration. Change them immediately after first login for security purposes.
Security Configuration
Upon first login, NPM prompts for new administrator credentials. Create a secure email address and strong password combination:
- Update the email address to a valid administrative email
- Set a complex password with mixed characters, numbers, and symbols
- Confirm the password change and note the new credentials
Enable two-factor authentication if available in your NPM version. This additional security layer protects against unauthorized access even if credentials are compromised.
Basic System Settings
Navigate to the Settings menu to configure essential NPM parameters. These settings affect global NPM behavior and security policies:
- Default Site: Configure the default website displayed for undefined domains
- Let’s Encrypt Settings: Enter a valid email address for SSL certificate registration
- Advanced Settings: Configure proxy timeouts, buffer sizes, and other performance parameters
Save all configuration changes and restart NPM if prompted. These settings establish the foundation for reliable proxy operations and SSL certificate management.
Step 6: Creating Your First Proxy Host
Proxy Host Fundamentals
Proxy hosts define the relationship between domain names and backend services. Each proxy host specifies how NPM should handle incoming requests for specific domains or subdomains. Understanding these concepts is crucial for effective NPM utilization.
The proxy configuration involves three main components: the domain name (frontend), the destination service (backend), and optional SSL certificate settings. NPM supports various backend types including web servers, application servers, and other network services.
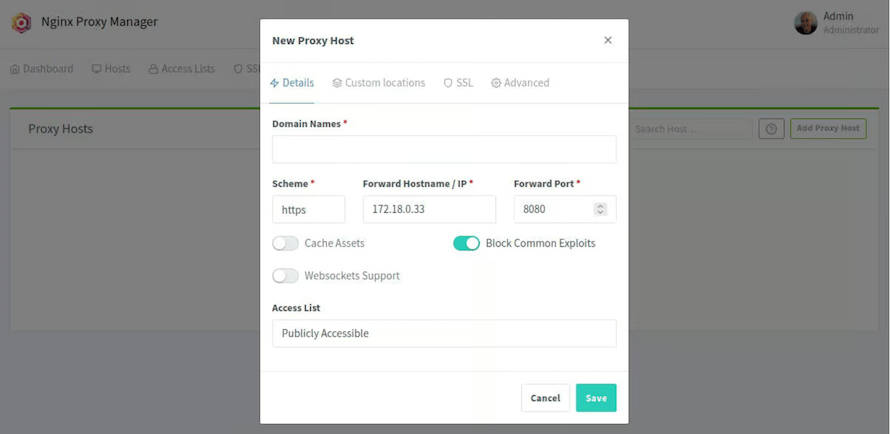
Adding Proxy Host Configuration
Navigate to the “Proxy Hosts” section in the NPM interface and click “Add Proxy Host”. The configuration form requires several essential parameters:
Domain Configuration:
- Domain Names: Enter the primary domain and any aliases
- Scheme: Select HTTP or HTTPS based on backend service
- Forward Hostname/IP: Specify the backend server address
- Forward Port: Define the backend service port
Advanced Settings:
- Cache Assets: Enable for static content caching
- Block Exploits: Activate security filtering
- Websockets Support: Enable for real-time applications
- Access List: Configure IP-based access restrictions
SSL Certificate Integration
Enable SSL certificates for secure HTTPS connections. NPM provides multiple certificate options:
- Let’s Encrypt: Automatic certificate generation and renewal
- Custom Certificate: Upload existing SSL certificates
- Self-Signed: Generate certificates for internal use
For Let’s Encrypt certificates, ensure DNS records point to your server before requesting certificates. The validation process requires external access to ports 80 and 443.
Certificate Configuration Steps:
- Select “Request a new SSL certificate”
- Choose “Let’s Encrypt” as the certificate provider
- Enter a valid email address for notifications
- Enable “Force SSL” for HTTPS enforcement
- Optionally enable “HTTP/2 Support” for improved performance
Save the configuration and monitor the certificate generation process. Successful certificate creation enables secure HTTPS access to your proxied service.
Step 7: Advanced SSL Certificate Management
Let’s Encrypt Automation
NPM’s Let’s Encrypt integration provides automated SSL certificate management with minimal configuration. The system handles certificate generation, validation, and renewal processes automatically. This automation eliminates manual certificate management tasks while ensuring continuous SSL security.
The certificate generation process involves several validation methods:
- HTTP-01: Validates domain ownership via HTTP requests
- DNS-01: Uses DNS TXT records for validation (supports wildcard certificates)
- TLS-ALPN-01: Validates through TLS connections
For most deployments, HTTP-01 validation provides the simplest implementation. Ensure ports 80 and 443 are accessible from the internet for successful validation.
Wildcard Certificate Configuration
Wildcard certificates secure multiple subdomains with a single certificate. This approach simplifies certificate management for organizations with numerous subdomains. NPM supports wildcard certificates through DNS-01 validation.
Wildcard Certificate Setup:
- Navigate to SSL Certificates section
- Click “Add SSL Certificate”
- Select “Let’s Encrypt” provider
- Enter domain as “*.yourdomain.com”
- Choose DNS Challenge validation
- Configure DNS provider credentials
The DNS challenge requires API access to your DNS provider for automated TXT record creation. Popular providers include Cloudflare, Route 53, and DigitalOcean DNS.
Certificate Renewal and Monitoring
NPM automatically renews Let’s Encrypt certificates before expiration. The default renewal process occurs 30 days before certificate expiry. Monitor certificate status through the NPM interface and configure notification emails for renewal alerts.
Certificate Monitoring Features:
- Certificate expiration tracking
- Automatic renewal status
- Email notifications for renewal events
- Certificate validation status monitoring
Configure backup procedures for certificate files stored in the /opt/nginx-proxy-manager/letsencrypt directory. Regular backups ensure certificate recovery in case of system failures or data corruption.
Step 8: Advanced Configuration Options
Stream Configuration
NPM supports TCP and UDP stream proxying for non-HTTP services. This functionality enables proxying database connections, mail servers, and other network services through the NPM interface.
Stream Proxy Setup:
- Navigate to “Streams” section in NPM interface
- Click “Add Stream”
- Configure incoming port and destination
- Specify TCP or UDP protocol
- Enable SSL termination if required
Stream proxies operate independently of HTTP proxy hosts and require separate firewall rules for the configured ports. Ensure proper firewall configuration for stream proxy functionality.
Custom Nginx Configurations
NPM allows custom Nginx configurations for advanced proxy requirements. These configurations provide granular control over proxy behavior, security headers, and performance optimizations.
Advanced Configuration Options:
- Custom location blocks for specific URL patterns
- Security headers for enhanced protection
- Rate limiting for DDoS mitigation
- Custom proxy headers for backend communication
- Gzip compression for improved performance
Access custom configurations through the “Advanced” tab in proxy host settings. Exercise caution when modifying these settings, as incorrect configurations can disrupt proxy functionality.
Load Balancing and High Availability
NPM supports basic load balancing across multiple backend servers. This functionality distributes traffic across multiple instances for improved performance and redundancy.
Load Balancing Configuration:
- Create multiple proxy hosts with identical domain names
- Specify different backend servers for each host
- Configure health checks for backend monitoring
- Implement session affinity if required
For enterprise deployments, consider implementing NPM in high availability mode with multiple instances behind a hardware load balancer or cloud load balancing service.
Step 9: Maintenance and Monitoring
Regular Update Procedures
Maintain NPM security and functionality through regular updates. Docker-based deployments simplify the update process while preserving configuration and data persistence.
Update Process:
cd /opt/nginx-proxy-manager
docker compose pull
docker compose up -d --force-recreateThis procedure downloads the latest NPM image and recreates containers with updated versions. Monitor the update process and verify functionality after completion.
Backup Strategies
Implement comprehensive backup procedures for NPM data, configurations, and SSL certificates. Regular backups ensure rapid recovery in case of system failures or data corruption.
Essential Backup Components:
- NPM database (/opt/nginx-proxy-manager/data)
- SSL certificates (/opt/nginx-proxy-manager/letsencrypt)
- Docker Compose configuration files
- Custom Nginx configurations
# Create backup script
#!/bin/bash
BACKUP_DIR="/backup/npm-$(date +%Y%m%d-%H%M%S)"
mkdir -p $BACKUP_DIR
cp -r /opt/nginx-proxy-manager $BACKUP_DIR/
tar -czf $BACKUP_DIR.tar.gz $BACKUP_DIR
rm -rf $BACKUP_DIRSchedule automated backups using cron jobs for consistent data protection. Store backups in multiple locations including remote storage for disaster recovery capabilities.
Performance Monitoring
Monitor NPM performance and resource utilization to ensure optimal operation. Docker provides built-in monitoring capabilities for container resource usage and health status.
Monitoring Commands:
# Container resource usage
docker stats nginx-proxy-manager
# Container logs
docker compose logs -f
# System resource monitoring
htopImplement log rotation to prevent disk space exhaustion from NPM access logs and error logs. Configure log retention policies based on compliance requirements and available storage capacity.
Troubleshooting Common Issues
Installation and Deployment Problems
Docker installation failures often result from repository configuration issues or conflicting packages. Verify repository configuration and remove conflicting Docker installations before retry attempts.
Common Installation Issues:
- SELinux policy conflicts preventing container startup
- Insufficient disk space for Docker images
- Network connectivity issues preventing image downloads
- Port binding conflicts with existing services
Resolve SELinux issues by configuring appropriate policies or temporarily setting SELinux to permissive mode during installation. Ensure adequate disk space and network connectivity for successful deployment.
SSL Certificate Generation Failures
Certificate generation failures typically involve DNS configuration, firewall rules, or Let’s Encrypt rate limits. Verify domain DNS records and firewall configuration before troubleshooting certificate issues.
Certificate Troubleshooting Steps:
- Verify DNS A/AAAA records point to correct IP address
- Confirm ports 80 and 443 are accessible externally
- Check Let’s Encrypt rate limits for domain
- Review NPM logs for specific error messages
Let’s Encrypt imposes rate limits of 50 certificates per registered domain per week. Exceeded rate limits require waiting for limit reset or using alternative certificate providers.
Network and Connectivity Issues
Proxy host connectivity problems often stem from backend service configuration, network routing, or firewall restrictions. Systematically test each component to isolate the root cause.
Connectivity Troubleshooting:
- Verify backend service accessibility from NPM container
- Test network connectivity using ping or telnet
- Review NPM access logs for error patterns
- Check Docker network configuration for proper routing
Use docker exec commands to access the NPM container for network troubleshooting:
docker exec -it nginx-proxy-manager /bin/bash
ping backend-server
curl -I http://backend-server:portCongratulations! You have successfully installed Nginx Proxy Manager. Thanks for using this tutorial for installing Nginx Proxy Manager on Rocky Linux 10 system. For additional help or useful information, we recommend you check the official Nginx website.