How To Install OpenLDAP on Ubuntu 24.04 LTS

OpenLDAP is a powerful open-source implementation of the LDAP (Lightweight Directory Access Protocol) system. It provides organizations of all sizes with a centralized method to manage user accounts, permissions, and other resources. Instead of deploying multiple authentication databases across various services, many administrators prefer a single authenticated directory so that users can securely log in and gain access to the resources they need. This guide explains how to install and configure OpenLDAP on Ubuntu 24.04, giving you the confidence to set up a fully functional LDAP directory service for your environment.
Ubuntu 24.04 is an excellent platform for modern networking services, offering robust stability and the latest software repositories. By leveraging OpenLDAP, organizations can streamline identity management and ensure that data is readily available, consistent, and protected. This tutorial guides you, step by step, through everything from the initial prerequisites to advanced configurations and ongoing maintenance tasks. It includes practical tips, best practices, and troubleshooting steps to minimize issues along the way.
Whether you are an experienced system administrator or new to directory services, this article will equip you with the knowledge you need to establish a reliable OpenLDAP server to handle authentication and directory lookups. The result will be a secure, centralized directory that helps you manage users, groups, and other resources in an increasingly complex network environment.
Understanding OpenLDAP Basics
OpenLDAP is a free and open-source implementation of LDAP, which is responsible for providing lightweight but flexible directory services. LDAP servers can store data in a hierarchical format that mirrors organizational structures, making it straightforward to manage complex entries such as users, groups, and even device or application attributes.
The purpose of a directory service is to serve as a single point of reference for resources. Instead of storing credentials separately on each system, a complete LDAP solution offers a centralized database accessible from multiple clients. When a user logs in or requests access to a particular service, the system consults the LDAP directory to authenticate the user and check relevant permissions. This streamlined approach saves both time and effort, particularly for larger environments or those with frequent user turnover.
Understanding a few key terms will simplify the setup process. For instance, the Base DN (distinguished name) refers to the starting point for directory lookups. SLAPD (Standalone LDAP Daemon) is the main service that stores the directory data, manages authentication, and handles queries. Additionally, schemas define the structure of the data that can be stored, specifying the attributes available for each type of object. By mastering these core concepts, you’ll be able to plan a robust and efficient LDAP directory that can evolve alongside your growing needs.
Pre-Installation Steps
Before beginning the installation of OpenLDAP on Ubuntu 24.04, make sure your system is up to date and has all necessary prerequisites. Keeping the operating system updated ensures that any security vulnerabilities and software bugs are addressed.
First, log into your Ubuntu 24.04 server via SSH or a local terminal. Then run:
sudo apt update && sudo apt upgrade -y
This command updates the package lists and upgrades installed packages to their latest versions. Once the update and upgrade process completes, it’s good practice to define or confirm your system hostname and network configuration. Having a consistent and properly set hostname is crucial for certain LDAP operations and secure communications.
Also consider checking available disk space, CPU resources, and memory. Although OpenLDAP itself does not require heavy resources, larger organizations or environments with extensive entries may demand more memory or CPU power. If you plan on implementing data replication or advanced features, ensure your system specifications can handle the additional load. Finally, create backups of critical data in case any unforeseen issue arises.
Installation Process
Installing OpenLDAP on Ubuntu 24.04 is relatively straightforward. The Ubuntu repositories package all required components, including the main OpenLDAP server (SLAPD) and additional tools for LDAP administration. Follow these steps to get started:
- Update Package Index:
sudo apt updateThis refreshes Ubuntu’s list of available packages to ensure you get the latest versions.
- Install SLAPD and LDAP Utilities:
sudo apt install slapd ldap-utils -yThe
slapdpackage contains the OpenLDAP server, whileldap-utilsprovides essential utilities such asldapsearchandldapmodify.
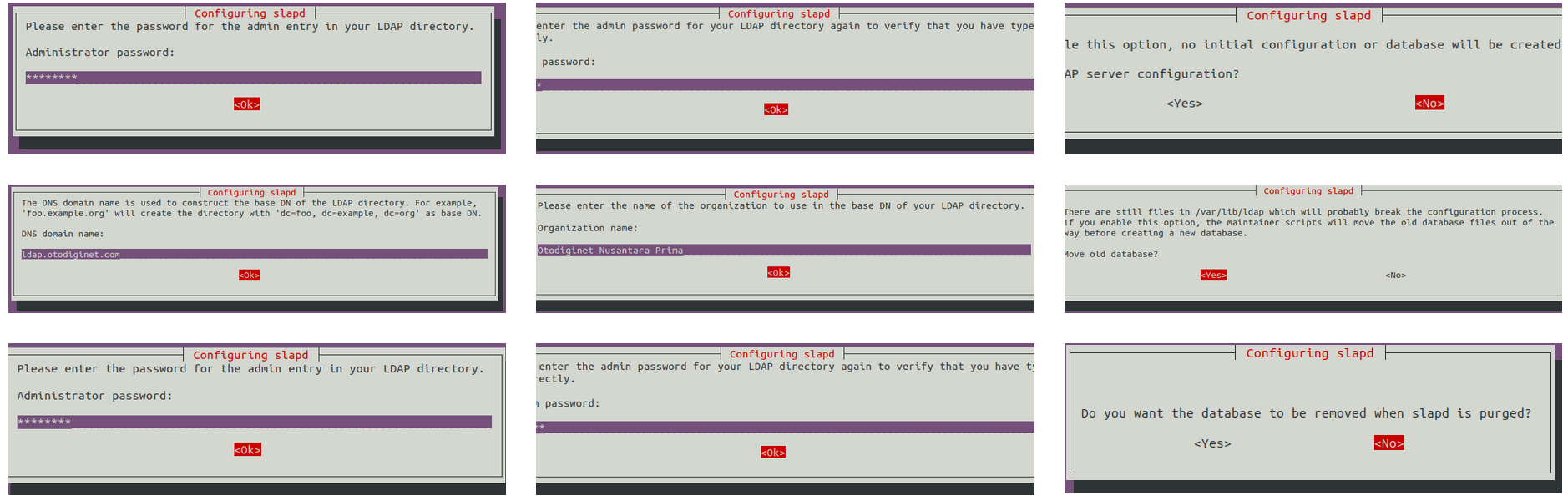
- Set Administrative Password:During the installation, you will be prompted to provide an administrative password for the Directory Manager. Confirm your choice carefully and ensure it is strong. This password is only for LDAP administration and will not affect system login.
- Configure SLAPD:After the package installation, Ubuntu’s post-installation scripts activate the slapd configuration utility. This step sets up your Base DN and administrative password. If you are not prompted, you can run:
sudo dpkg-reconfigure slapdWhen prompted, select appropriate settings for your environment, such as your organization’s domain name.
- Check Service Status:
sudo systemctl status slapdThis command verifies whether the slapd daemon is active and running. If it isn’t, you can start it with:
sudo systemctl start slapd sudo systemctl enable slapd
Upon completion of these steps, you will have a basic OpenLDAP server up and ready. However, it is still using default settings. In most production environments, you’ll want to further configure the database, define your own organizational structure, and enable encryption to secure communications.
Basic Configuration
OpenLDAP’s initial setup uses an online configuration (olc) model. This model replaces the legacy slapd.conf configuration file, making it easier to update settings without restarting services. Here’s how to manage some of the main configuration items.
First, confirm your LDAP domain components. Typically, if your domain is example.com, the Base DN might be dc=example,dc=com. You can verify the domain settings by running:
sudo ldapsearch -LLL -Y EXTERNAL -H ldapi:/// -b cn=config dn
This command searches within the cn=config context. Look for entries that reference your domain.
To adjust the domain name or other critical parameters, use the dpkg-reconfigure slapd command mentioned earlier, or manually modify olcDatabase entries using ldapmodify. For example:
sudo ldapmodify -Y EXTERNAL -H ldapi:///
Then type dn and changeType instructions to update specific attributes. Carefully proceed with manual edits, because a mistake in the online configuration can break your LDAP server.
Another key step is to create a root organizational unit (OU) for your users and groups. This is often accomplished by writing an LDIF (LDAP Data Interchange Format) file. For instance, create a file named base.ldif with content such as:
dn: ou=people,dc=example,dc=com
objectClass: organizationalUnit
ou: people
dn: ou=groups,dc=example,dc=com
objectClass: organizationalUnit
ou: groups
Then load it into the directory using:
ldapadd -x -D cn=admin,dc=example,dc=com -W -f base.ldif
Replace cn=admin,dc=example,dc=com with your administrative DN and supply the password you configured during installation. This step offers a simple foundation for further expansions in your directory structure.
Creating Organizational Structure
A well-structured LDAP directory simplifies user management, permissions, and future expansions. While a minimal installation might allow you to lump everything under a single node, it is better to map the structure to reflect actual departments or business units. This principle of analogous organization helps keep your directory clean and navigable.
You might separate entries into OUs (organizational units) for People, Groups, Services, and more. For instance, if you have multiple departments, you can create dedicated OUs for Engineering, Human Resources, or Finance. Each OU can then hold user or group entries relevant to that part of the organization.
In addition to OUs, you can define group objects to bundle users who share common roles, privileges, or tasks. OpenLDAP supports different group object classes, such as posixGroup for Unix-like systems or groupOfNames for broader organizational needs. By assigning users to these groups, you can easily grant or revoke permissions across multiple services.
When creating entries for your directory, remember that every object must have a unique distinguished name (DN). This DN includes the object’s hierarchy, for example: uid=john.doe,ou=people,dc=example,dc=com. Establish a consistent naming convention early on to avoid confusion and ensure that future expansions remain structured. Early planning sets you up for success and prevents the need to overhaul the directory structure later on.
Security Configuration
Protecting LDAP communications is essential for safeguarding user credentials, especially in a production environment. By default, LDAP transmits data in plaintext unless you enable TLS/SSL. To encrypt traffic, you can generate or obtain SSL certificates and install them on the server. Typically, an officially signed certificate is ideal; however, for testing purposes, self-signed certificates can suffice.
To enable TLS, update olcSecurity settings within the configuration database. This process usually involves specifying olcTLSCACertificateFile, olcTLSCertificateFile, and olcTLSCertificateKeyFile. Confirm that the slapd user has the appropriate permissions to access these certificates. Once the certificates are in place, reload or restart the service:
sudo systemctl restart slapd
Additionally, implement strong password policies through the ppolicy overlay if needed. This overlay enforces rules such as password expiration, complexity, and lockout for repeated failed attempts. Finally, deploy Access Control Lists (ACLs) to strictly limit who can read, write, or modify entries. With careful planning, these measures ensure the confidentiality and integrity of your LDAP directory.
Testing and Verification
Once the server is configured, test your OpenLDAP setup to confirm it is working properly. First, verify that the LDAP daemon is running and listening on the correct ports:
sudo systemctl status slapd
sudo netstat -tulpn | grep slapd
Next, use the ldapsearch utility to query the directory:
ldapsearch -x -b "dc=example,dc=com" "(objectClass=*)"
This command should return entries in your directory without errors. If you enabled secure LDAP (LDAPS), use the corresponding LDAPS configuration in your query or your tools. For instance, check connectivity using:
ldapsearch -H ldaps://server_domain -x -b "dc=example,dc=com"
Any errors with these commands may indicate issues related to certificates, ACLs, or user permissions. Correct them before moving on to advanced configurations.
Advanced Configuration
After establishing a stable OpenLDAP environment, you can explore advanced settings to improve performance and redundancy. One common enhancement is replication, where a master server copies data to a series of replicas. This approach improves reliability and distributes the authentication load, ensuring that even if the main server experiences downtime, authentication services continue uninterrupted.
To enable replication, configure the syncrepl directive within the olcDatabase configuration. This requires specifying each server’s URI and credentials. You can then designate one server as the master, while others run as consumers that poll for updates. Successful replication results in near-real-time synchronization of directory entries.
Schema modifications are another avenue for customization. OpenLDAP includes various standard schemas for representing user accounts, organizational hierarchies, or even custom object classes. You can extend existing schemas by creating your own definitions, enabling you to track specialized attributes. Finally, consider implementing caching mechanisms or performance tuning parameters, such as indexing frequently queried attributes, to optimize the directory’s responsiveness.
Maintenance and Management
LDAP servers require periodic maintenance to keep them running optimally. Regularly monitor logs to catch errors related to authentication, replication, or performance. Tools like journalctl -u slapd or less /var/log/syslog help trace issues in real time. In addition, create snapshots or backups of your directory data. For instance, you can export all entries using:
slapcat -n 1 -l backup.ldif
Storing full LDIF backups off-site or on a secondary server ensures data recoverability in case of corruption or hardware failure. When new patches or features become available, regularly apply updates. Ubuntu 24.04 receives security updates for the life of the LTS, so installing them promptly keeps your LDAP server secure. Finally, revisit your directory structure, ACLs, and password policies periodically to verify they still meet organizational requirements.
Congratulations! You have successfully installed OpenLDAP. Thanks for using this tutorial for installing the OpenLDAP on Ubuntu 24.04 LTS system. For additional help or useful information, we recommend you check the official OpenLDAP website.