How To Install phpMyAdmin on Debian 13

Managing databases through command-line interfaces can be challenging, especially for users who prefer visual tools. phpMyAdmin offers a powerful web-based solution for administering MySQL and MariaDB databases, eliminating the need for complex terminal commands. This comprehensive guide walks through the complete installation process on Debian 13 (Trixie), from setting up the LAMP stack to securing the installation for production environments.
The entire process takes approximately 15-20 minutes. By the end of this tutorial, a fully functional database management system will be accessible through any web browser.
Understanding phpMyAdmin and Its Requirements
What is phpMyAdmin?
phpMyAdmin is an open-source database administration tool written in PHP. It provides a graphical user interface for managing MySQL and MariaDB database servers. The application runs directly in web browsers, offering intuitive controls for database operations that would otherwise require extensive SQL knowledge.
Users can create, modify, and delete databases with simple clicks. The tool supports advanced features like user permission management, query execution, and complex table relationship handling. Import and export functionality simplifies backup operations and data migration tasks.
Why Use phpMyAdmin on Debian 13?
Debian 13, codenamed Trixie, represents the latest stable release with modern package repositories. The operating system’s stability makes it ideal for hosting database management tools. phpMyAdmin integrates seamlessly with Debian’s package management system, ensuring smooth updates and security patches.
The combination offers cross-platform compatibility and benefits from active community support. Database administrators can manage multiple servers from a single interface. The graphical environment reduces errors common with manual SQL commands, particularly for complex operations involving multiple tables or user permissions.
Prerequisites and System Requirements
Before beginning the installation, ensure these requirements are met:
A server running Debian 13 (Trixie) operating system with at least 1GB RAM and 10GB available disk space. Root or sudo user privileges are essential for installing system-level packages. A stable internet connection enables package downloads from Debian repositories.
SSH access is recommended for remote server management. Basic familiarity with Linux command-line operations helps troubleshoot potential issues. Optionally, having a registered domain name with DNS A records pointing to the server IP address allows custom subdomain access for phpMyAdmin.
Step 1: Update System Packages
Keeping system packages current prevents compatibility issues during installation. Outdated packages can cause conflicts with newer software dependencies. Execute the following command to refresh package lists:
sudo apt update -yThis command contacts Debian repositories and updates the local package index. Next, upgrade installed packages to their latest versions:
sudo apt upgrade -yThe system may display a list of packages requiring updates. Confirm the upgrade when prompted. Some updates might require a system reboot, particularly kernel updates. Check if a reboot is necessary by examining the /var/run/reboot-required file.
Regular system updates form the foundation of server security. This practice should continue throughout the server’s operational lifetime, not just during initial setup.
Step 2: Install Apache Web Server
Apache serves as the web server component that delivers phpMyAdmin’s interface to browsers. It handles HTTP requests and processes PHP scripts. Install Apache with this command:
sudo apt install apache2 -yThe package manager downloads and installs Apache along with required dependencies. Start the Apache service immediately:
sudo systemctl start apache2Enable Apache to launch automatically during system boot:
sudo systemctl enable apache2Verify Apache is running correctly:
sudo systemctl status apache2The output should display “active (running)” in green text. Test the installation by opening a web browser and navigating to the server’s IP address. The default Apache2 Debian page should appear, confirming successful installation.
If the page doesn’t load, check firewall settings. UFW (Uncomplicated Firewall) might be blocking HTTP traffic. Allow Apache through the firewall:
sudo ufw allow 'Apache'Step 3: Install MariaDB Database Server
MariaDB provides the database backend that phpMyAdmin manages. This open-source relational database management system offers excellent compatibility with MySQL. Install MariaDB server and client packages:
sudo apt install mariadb-server mariadb-client -yStart the MariaDB service:
sudo systemctl start mariadbEnable automatic startup on boot:
sudo systemctl enable mariadbConfirm the service is active:
sudo systemctl status mariadbSecuring MariaDB Installation
Fresh MariaDB installations include default settings unsuitable for production environments. The security script removes these vulnerabilities. Run the interactive security configuration:
sudo mysql_secure_installationThe script presents several prompts. When asked about switching to Unix socket authentication, select “N” for no. Set a strong root password when prompted—use a combination of uppercase letters, lowercase letters, numbers, and special characters with at least 16 characters.
Remove anonymous users by selecting “Y” when asked. These accounts pose significant security risks. Disable remote root login by selecting “Y”—root access should only occur from localhost. Remove the test database by selecting “Y” since it’s unnecessary for production systems. Reload privilege tables by selecting “Y” to apply all changes immediately.
These security measures significantly reduce the attack surface. Never use simple or dictionary-based passwords for database root accounts.
Step 4: Install PHP and Required Extensions
PHP processes phpMyAdmin’s code and connects to database servers. Multiple PHP extensions enable specific phpMyAdmin features. Install PHP along with necessary modules:
sudo apt install php php-mysqli php-mbstring php-zip php-gd php-json php-curl libapache2-mod-php -yEach extension serves specific purposes:
The php-mysqli extension provides MySQL database connectivity through improved APIs. The php-mbstring module handles multi-byte string operations, essential for international character support. The php-zip extension enables compression functionality for import and export operations. The php-gd library generates images and manipulates graphics. The php-json module parses and generates JSON data structures. The php-curl extension facilitates URL transfers and remote API connections. The libapache2-mod-php package integrates PHP processing into Apache.
Verify PHP installation by checking the version:
php -vThe command displays the installed PHP version and build information. Restart Apache to load the PHP module:
sudo systemctl restart apache2Apache now processes PHP files automatically. Optionally, create a test PHP file to verify functionality:
echo "<?php phpinfo(); ?>" | sudo tee /var/www/html/info.phpAccess this file through a browser at http://server-ip/info.php. The PHP information page displays configuration details. Remove this test file after verification for security:
sudo rm /var/www/html/info.phpStep 5: Install phpMyAdmin
Debian repositories include phpMyAdmin packages with automatic configuration options. Install phpMyAdmin using the APT package manager:
sudo apt install phpmyadmin -yConfiguration Prompts
The installation process presents interactive configuration screens. The first prompt asks which web server to configure automatically. Use the spacebar to select “apache2″—an asterisk appears in the brackets when selected. Press Tab to highlight “Ok” and press Enter.
The next screen asks about database configuration with dbconfig-common. Select “Yes” to allow automatic database setup. This creates the necessary phpMyAdmin configuration database and tables.
Enter a secure password for the phpMyAdmin application when prompted. This password protects the phpMyAdmin configuration database, separate from user database passwords. Confirm the password on the next screen.
The installer configures Apache automatically, creating the necessary configuration files. phpMyAdmin installs to /usr/share/phpmyadmin by default. Verify the installation:
dpkg -l | grep phpmyadminThis command lists installed phpMyAdmin packages and versions.
Alternative Manual Installation
Advanced users might prefer manual installation from source for the latest features. Download the current release from the official phpMyAdmin website. Extract the archive to the web directory and manually configure settings. This method requires more technical knowledge but offers greater control over the installation.
Package installation through APT remains recommended for most users. It ensures automatic security updates through Debian’s package management system.
Step 6: Create Database and User for phpMyAdmin
Using the root account for daily database operations poses security risks. Create a dedicated database user with limited privileges. Access the MariaDB console:
sudo mariadb -u root -pEnter the root password set during the security configuration. The MariaDB prompt appears, indicated by MariaDB [(none)]>.
Creating a Test Database
Create a sample database for testing:
CREATE DATABASE testdb;MariaDB confirms database creation with “Query OK” message. Database names should follow consistent naming conventions—use lowercase letters and underscores instead of spaces.
Creating a Dedicated Database User
Create a new user with password authentication:
CREATE USER 'dbuser'@'localhost' IDENTIFIED BY 'SecurePassword123!@#';Replace “dbuser” with a preferred username and “SecurePassword123!@#” with a strong, unique password. The @'localhost' specification restricts connections to the local server only.
Grant appropriate privileges to the new user:
GRANT ALL PRIVILEGES ON testdb.* TO 'dbuser'@'localhost';This command grants full permissions on the testdb database. For production environments, limit privileges to only required operations. For example, a read-only user needs only SELECT privileges:
GRANT SELECT ON testdb.* TO 'readonly_user'@'localhost' IDENTIFIED BY 'AnotherSecurePassword';Apply privilege changes immediately:
FLUSH PRIVILEGES;Exit the MariaDB console:
EXIT;Security Considerations for Database Users
Never reuse passwords across different database users or systems. Each user should have privileges limited to their specific needs. Regularly audit user accounts and remove unused credentials. Document user purposes and privilege levels for future reference.
Consider implementing password rotation policies for sensitive environments. Use password managers to generate and store complex credentials securely.
Step 7: Configure Apache for phpMyAdmin
Apache requires proper configuration to serve phpMyAdmin correctly. The package installation creates default configurations, but additional optimization improves security and functionality.
Enabling Required Apache Modules
Enable the rewrite module for URL manipulation:
sudo a2enmod rewriteRestart Apache to load the module:
sudo systemctl restart apache2Creating Custom Virtual Host Configuration
Custom virtual hosts enable subdomain access and better security isolation. Create a new virtual host file:
sudo nano /etc/apache2/sites-available/phpmyadmin.confAdd the following configuration:
<VirtualHost *:80>
ServerName pma.yourdomain.com
DocumentRoot /usr/share/phpmyadmin
<Directory /usr/share/phpmyadmin>
Options FollowSymLinks
DirectoryIndex index.php
AllowOverride All
Require all granted
</Directory>
ErrorLog ${APACHE_LOG_DIR}/phpmyadmin_error.log
CustomLog ${APACHE_LOG_DIR}/phpmyadmin_access.log combined
</VirtualHost>Replace “pma.yourdomain.com” with the actual subdomain. The DocumentRoot points to phpMyAdmin’s installation directory. The Directory block sets permissions and behavior for the phpMyAdmin directory.
Save the file and exit the editor (Ctrl+X, then Y, then Enter). Enable the new virtual host:
sudo a2ensite phpmyadmin.confTest Apache configuration syntax:
sudo apachectl configtestThe output should display “Syntax OK”. If errors appear, review the virtual host file for typos. Reload Apache to apply changes:
sudo systemctl reload apache2Accessing phpMyAdmin via Subdomain
Configure DNS records at the domain registrar or DNS provider. Create an A record pointing “pma.yourdomain.com” to the server’s IP address. DNS propagation takes 5-60 minutes typically.
Alternatively, access phpMyAdmin using the server’s IP address followed by “/phpmyadmin“:
http://server-ip/phpmyadminBoth methods provide access to the same phpMyAdmin installation.
Step 8: Secure phpMyAdmin Installation
Default phpMyAdmin installations are vulnerable to various attacks. Implementing security measures protects against unauthorized access and brute-force attempts.
Change Default Access URL
The standard /phpmyadmin path is well-known to attackers. Changing this URL reduces automated attack exposure. Edit the Apache configuration:
sudo nano /etc/phpmyadmin/apache.confLocate the Alias /phpmyadmin line and change it to a custom path:
Alias /secure-db-admin /usr/share/phpmyadminSave the file and restart Apache:
sudo systemctl restart apache2Access phpMyAdmin at the new URL: http://server-ip/secure-db-admin
Implement HTTPS/SSL Certificate
Transmitting database credentials over unencrypted HTTP connections exposes sensitive information. SSL certificates encrypt all traffic between browsers and servers. Install Certbot for Let’s Encrypt certificates:
sudo apt install certbot python3-certbot-apache -yObtain and install an SSL certificate:
sudo certbot --apache -d pma.yourdomain.comCertbot prompts for an email address for renewal notifications. Accept the terms of service when prompted. Choose whether to redirect HTTP traffic to HTTPS automatically—select option 2 for forced redirection.
Certbot configures Apache automatically and enables SSL. Test automatic renewal:
sudo certbot renew --dry-runSuccessful output confirms automatic renewal functionality. Certificates renew every 90 days without manual intervention.
Add HTTP Authentication Layer
Adding HTTP authentication creates a second security barrier before reaching the phpMyAdmin login screen. Install Apache utilities:
sudo apt install apache2-utils -yCreate a password file:
sudo htpasswd -c /etc/phpmyadmin/.htpasswd adminEnter a strong password when prompted. Add additional users without the -c flag:
sudo htpasswd /etc/phpmyadmin/.htpasswd seconduserEdit the phpMyAdmin Apache configuration:
sudo nano /etc/apache2/sites-available/phpmyadmin.confAdd authentication directives inside the Directory block:
<Directory /usr/share/phpmyadmin>
Options FollowSymLinks
DirectoryIndex index.php
AllowOverride All
AuthType Basic
AuthName "Restricted Access"
AuthUserFile /etc/phpmyadmin/.htpasswd
Require valid-user
</Directory>Save and reload Apache:
sudo systemctl reload apache2Browsers now prompt for HTTP authentication credentials before displaying the phpMyAdmin login page.
Restrict Access by IP Address
Limiting access to specific IP addresses provides additional security. Edit the virtual host configuration:
sudo nano /etc/apache2/sites-available/phpmyadmin.confReplace Require all granted with IP restrictions:
<Directory /usr/share/phpmyadmin>
Options FollowSymLinks
DirectoryIndex index.php
AllowOverride All
Require ip 203.0.113.10
Require ip 198.51.100.20
</Directory>Replace the example IP addresses with trusted addresses. Save and reload Apache. Only specified IP addresses can access phpMyAdmin.
Configure firewall rules for additional protection:
sudo ufw allow from 203.0.113.10 to any port 80
sudo ufw allow from 203.0.113.10 to any port 443Disable Root Login
Prevent root account access through phpMyAdmin. Edit the configuration file:
sudo nano /etc/phpmyadmin/config.inc.phpAdd this line after the existing configuration directives:
$cfg['Servers'][$i]['AllowRoot'] = false;Save the file. Root account access through phpMyAdmin is now blocked. Use dedicated database users instead.
Step 9: Configure phpMyAdmin Settings
Fine-tuning phpMyAdmin settings optimizes performance and functionality.
Blowfish Secret Configuration
The blowfish secret encrypts cookie-based authentication. Locate the configuration file:
sudo nano /etc/phpmyadmin/config.inc.phpFind the blowfish_secret line. If empty, add a 32-character random string:
$cfg['blowfish_secret'] = 'Kj8HfG9sD2mN4vB7xC1qW5eR3tY6uI0o';Generate random strings using:
openssl rand -base64 32Use the output as the blowfish secret value.
Adjusting PHP Upload Limits
Default PHP upload limits might be insufficient for large database imports. Edit the PHP configuration:
sudo nano /etc/php/8.4/apache2/php.iniThe version number (8.4) varies based on the installed PHP version. Locate and modify these directives:
upload_max_filesize = 128M
post_max_size = 128M
max_execution_time = 600
max_input_time = 600
memory_limit = 256MThese values support database files up to 128MB with 10-minute execution timeouts. Adjust based on specific requirements. Save the file and restart Apache:
sudo systemctl restart apache2Temporary Directory Configuration
phpMyAdmin requires writable temporary storage. Edit the configuration:
sudo nano /etc/phpmyadmin/config.inc.phpAdd or modify the TempDir setting:
$cfg['TempDir'] = '/var/lib/phpmyadmin/tmp';Create the directory with appropriate permissions:
sudo mkdir -p /var/lib/phpmyadmin/tmp
sudo chown -R www-data:www-data /var/lib/phpmyadmin/tmp
sudo chmod 700 /var/lib/phpmyadmin/tmpThese permissions ensure only the Apache user can access temporary files.
Step 10: Access and Test phpMyAdmin
With installation and configuration complete, access phpMyAdmin to verify functionality.
Accessing phpMyAdmin Interface
Open a web browser and navigate to the configured URL:
https://pma.yourdomain.comOr using the IP address with custom path:
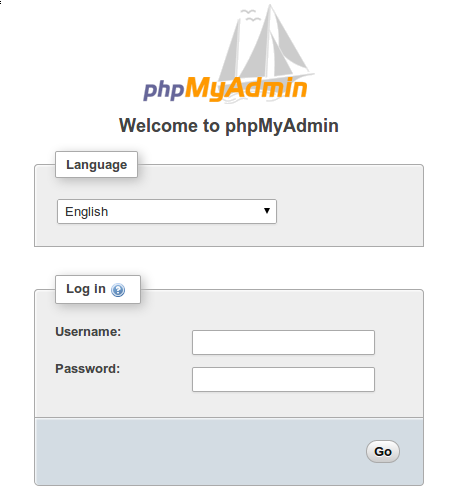
https://server-ip/secure-db-adminIf HTTP authentication was configured, enter those credentials first. The phpMyAdmin login page displays with username and password fields.
Enter the database username and password created earlier (dbuser and its password). Click “Go” to log in. The phpMyAdmin dashboard appears, showing the left sidebar with available databases.
Testing Database Operations
Verify the testdb database appears in the left sidebar. Click on it to view tables. Create a sample table by clicking the “New” tab at the top.
Enter a table name like “users” and set the number of columns to 3. Click “Go”. Define columns:
- Column 1: name (VARCHAR, length 100)
- Column 2: email (VARCHAR, length 100)
- Column 3: created_at (TIMESTAMP, DEFAULT CURRENT_TIMESTAMP)
Click “Save” to create the table. Insert sample data by clicking the “Insert” tab. Fill in values for name and email fields. Click “Go” to insert the record.
Navigate to the “Browse” tab to view inserted data. The interface displays table contents in a readable format.
Verifying Additional Functionality
Test the import feature by clicking the “Import” tab. Browse for a SQL file or use the sample query box. The export functionality works similarly—click “Export” to generate database backups in various formats.
Explore the “SQL” tab to run custom queries directly. The “Users” section under the main phpMyAdmin interface allows managing database user accounts and privileges.
All core CRUD operations (Create, Read, Update, Delete) should function properly through the graphical interface.
Common Troubleshooting Issues
Even with careful installation, issues occasionally arise. These solutions address the most frequent problems.
“Access Denied” Errors
Authentication failures typically result from incorrect credentials or improper user privileges. Verify the username and password match what was created in MariaDB. Check that the user has appropriate privileges:
sudo mariadb -u root -pWithin MariaDB, query user permissions:
SELECT User, Host FROM mysql.user;
SHOW GRANTS FOR 'dbuser'@'localhost';If privileges are missing, grant them again:
GRANT ALL PRIVILEGES ON testdb.* TO 'dbuser'@'localhost';
FLUSH PRIVILEGES;Reset user passwords if necessary:
ALTER USER 'dbuser'@'localhost' IDENTIFIED BY 'NewSecurePassword';
FLUSH PRIVILEGES;“404 Not Found” Error
Missing Apache configuration or incorrect symbolic links cause 404 errors. Verify phpMyAdmin is installed:
dpkg -l | grep phpmyadminCheck that the Apache configuration file exists:
ls -la /etc/apache2/conf-enabled/ | grep phpmyadminIf missing, create the symbolic link manually:
sudo ln -s /etc/phpmyadmin/apache.conf /etc/apache2/conf-enabled/phpmyadmin.confAlternatively, create a symbolic link in the web root:
sudo ln -s /usr/share/phpmyadmin /var/www/html/phpmyadminRestart Apache after making changes:
sudo systemctl restart apache2PHP Extension Missing Warnings
phpMyAdmin displays warnings about missing PHP extensions that affect functionality. Install missing extensions individually:
sudo apt install php-mbstring php-zip php-gd php-json php-curl -yVerify installed PHP modules:
php -m | grep mysqli
php -m | grep mbstringEnable extensions if installed but not active:
sudo phpenmod mysqli
sudo phpenmod mbstringRestart Apache to load newly installed extensions:
sudo systemctl restart apache2Session Timeout Issues
Frequent session expiration disrupts workflow. Increase the session timeout value in phpMyAdmin configuration:
sudo nano /etc/phpmyadmin/config.inc.phpAdd or modify the LoginCookieValidity setting:
$cfg['LoginCookieValidity'] = 3600;This sets the session timeout to 3600 seconds (1 hour). Adjust the value based on security requirements versus convenience.
Also increase PHP session timeout:
sudo nano /etc/php/8.2/apache2/php.iniModify these settings:
session.gc_maxlifetime = 3600
session.cookie_lifetime = 3600Clear browser cookies and cache, then restart Apache.
Import File Size Errors
Attempting to import databases larger than configured limits produces errors. Check current limits in phpMyAdmin by clicking the Import tab—the maximum file size displays at the top.
Increase PHP upload limits as described in Step 9. For extremely large databases exceeding practical upload limits, use command-line import instead:
mysql -u dbuser -p testdb < large_database.sqlThis method bypasses PHP upload restrictions entirely.
“Token Mismatch” Error
Token mismatch errors indicate session or cookie problems. Ensure cookies are enabled in the browser. Clear browser cookies and cache completely. Check that the blowfish_secret is configured in phpMyAdmin configuration.
Verify the session.save_path directory has proper permissions:
ls -la $(php -i | grep session.save_path | awk '{print $3}')The directory should be writable by the www-data user. If permission issues exist:
sudo chmod 733 /var/lib/php/sessionsBest Practices for phpMyAdmin Usage
Maintaining secure and efficient phpMyAdmin installations requires ongoing attention.
Regular Maintenance
Keep phpMyAdmin updated through Debian’s package manager:
sudo apt update
sudo apt upgrade phpmyadminSubscribe to security mailing lists for phpMyAdmin and Debian. Monitor /var/log/apache2/phpmyadmin_access.log for unusual access patterns. Schedule regular security audits examining user accounts and access logs.
Perform test restorations of database backups quarterly. Documentation ensures recovery procedures work correctly. Update configuration documentation when making changes.
Security Hygiene
Generate unique, complex passwords for every database user account. Implement password rotation policies for high-security environments. Review database user accounts monthly, removing unused credentials immediately.
Limit user privileges to minimum required levels. Users needing only data viewing should have SELECT privileges exclusively. Monitor failed login attempts through Apache logs. Consider implementing Fail2ban rules to block repeated authentication failures.
Enable two-factor authentication where supported. Keep detailed logs of database changes for audit trails. Restrict SSH access to database servers using key-based authentication only.
Performance Optimization
Disable phpMyAdmin features not actively used. Reduce the number of rows displayed per page for large tables. Use command-line tools for operations involving massive datasets or complex migrations.
Configure query caching in MariaDB to improve performance:
sudo nano /etc/mysql/mariadb.conf.d/50-server.cnfAdd caching parameters:
query_cache_type = 1
query_cache_size = 128M
query_cache_limit = 2MRestart MariaDB after configuration changes. Monitor server resource usage and scale vertically or horizontally as needed.
Backup Strategies
Implement automated daily database backups using cron jobs:
sudo crontab -eAdd a backup command:
0 2 * * * mysqldump -u root -pPASSWORD --all-databases | gzip > /backup/db_$(date +\%Y\%m\%d).sql.gzStore backups on separate physical storage or cloud services. Maintain at least 30 days of backup history. Test restoration procedures regularly to ensure backup integrity.
Document backup and recovery processes thoroughly. Include restoration commands and time estimates. Train multiple team members on recovery procedures to prevent single points of failure.
Encrypt backup files containing sensitive data. Use tools like GPG for file encryption before transferring to storage locations.
Congratulations! You have successfully installed phpMyAdmin. Thanks for using this tutorial to install the latest version of phpMyAdmin on Debian 13 “Trixie” system. For additional help or useful information, we recommend you check the official phpMyAdmin website.