How To Install phpMyAdmin on Rocky Linux 10

phpMyAdmin stands as one of the most popular web-based database administration tools for MySQL and MariaDB servers. This powerful interface simplifies complex database management tasks through an intuitive web interface. Rocky Linux 10, positioned as the premier enterprise-grade successor to CentOS, provides an ideal foundation for hosting phpMyAdmin installations.
The combination of phpMyAdmin and Rocky Linux delivers exceptional stability, security, and performance for database management environments. System administrators and developers benefit from Rocky Linux’s enterprise-class reliability while leveraging phpMyAdmin’s comprehensive database management capabilities. This integration proves particularly valuable for organizations requiring robust, cost-effective database administration solutions.
Throughout this comprehensive guide, you’ll master the complete installation process from initial system preparation through advanced security configuration. The tutorial covers prerequisite software installation, multiple phpMyAdmin deployment methods, security hardening techniques, and essential troubleshooting procedures. Whether you’re managing a single development server or multiple production environments, this guide provides the expertise needed for successful phpMyAdmin implementation.
Prerequisites and System Requirements
System Requirements
Rocky Linux 10 installation demands specific hardware and software prerequisites for optimal phpMyAdmin performance. A minimum of 1GB RAM ensures smooth operation, though 2GB or more is recommended for production environments. The system requires at least 10GB of available disk space to accommodate the operating system, web server, database engine, and phpMyAdmin components.
Network connectivity remains essential for downloading packages and accessing the web interface. Ensure your server maintains stable internet connectivity during installation and configuration phases. Administrative privileges through root access or sudo capabilities are mandatory for installing system packages and configuring services.
Required Software Components
The LAMP (Linux, Apache, MySQL/MariaDB, PHP) stack forms the foundation for phpMyAdmin deployment. Apache web server serves as the primary HTTP service, handling web requests and delivering the phpMyAdmin interface to client browsers. MariaDB or MySQL database server provides the backend database engine that phpMyAdmin manages.
PHP serves as the server-side scripting language powering phpMyAdmin’s functionality. Essential PHP extensions include mysqli for database connectivity, mbstring for multi-byte string handling, zip for archive management, and json for data serialization. Additional extensions like curl, gd, and openssl enhance phpMyAdmin’s capabilities and security features.
Pre-Installation Checklist
System updates ensure compatibility and security before beginning the installation process. Verify that all existing packages are current and security patches are applied. Plan firewall configurations to allow HTTP and HTTPS traffic while maintaining security protocols.
Prepare your domain name or IP address for accessing the phpMyAdmin interface. Consider backup strategies for existing data and configurations before implementing changes. Document current system settings to facilitate troubleshooting if issues arise during installation.
Installing the LAMP Stack Foundation
System Update and Preparation
Begin by updating your Rocky Linux 10 system to ensure all packages are current and security patches are applied:
sudo dnf update -yThe DNF package manager downloads and installs all available updates. This process may take several minutes depending on the number of outdated packages. System updates often include kernel updates that require a system reboot to take effect.
After completing updates, verify the system’s current status and reboot if kernel updates were installed:
sudo systemctl rebootPackage manager configuration ensures optimal performance during subsequent installations. The DNF package manager automatically handles dependency resolution and maintains package integrity throughout the installation process.
Apache Web Server Installation
Install the Apache HTTP server using the DNF package manager:
sudo dnf install httpd -yStart the Apache service and configure it to automatically start during system boot:
sudo systemctl start httpd
sudo systemctl enable httpdVerify Apache service status to ensure proper installation and operation:
sudo systemctl status httpdTest the Apache installation by accessing the default web page. Open a web browser and navigate to your server’s IP address. The Apache test page confirms successful installation and proper service operation.
The httpd service creates necessary directories and configuration files automatically. Default document root location is /var/www/html, where web content is stored and served to client requests.
Firewall Configuration for Apache
Configure the firewall to allow HTTP and HTTPS traffic through the appropriate ports:
sudo firewall-cmd --permanent --add-service=http
sudo firewall-cmd --permanent --add-service=httpsReload the firewall configuration to apply the new rules:
sudo firewall-cmd --reloadVerify firewall rule implementation to ensure proper access control:
sudo firewall-cmd --list-servicesThe firewall-cmd utility manages Rocky Linux’s built-in firewall system. Permanent rules persist across system reboots, ensuring consistent access control. HTTP service operates on port 80, while HTTPS operates on port 443.
MariaDB Database Server Setup
Install the MariaDB server package and supporting components:
sudo dnf install mariadb-server mariadb -yStart the MariaDB service and enable automatic startup:
sudo systemctl start mariadb
sudo systemctl enable mariadbExecute the security installation script to configure database security settings:
sudo mysql_secure_installationThe security script prompts for various configuration options. Set a strong root password, remove anonymous user accounts, disable remote root login, and delete test databases. These security measures protect against unauthorized access and potential security vulnerabilities.
Test database connectivity using the MySQL client:
mysql -u root -pPHP Installation and Configuration
Install PHP and essential extensions required for phpMyAdmin operation:
sudo dnf install php php-mysqli php-mbstring php-zip php-json php-curl php-gd -yThe PHP installation includes the core interpreter and necessary extensions. The mysqli extension enables database connectivity, while mbstring handles multi-byte character strings. Additional extensions enhance functionality and security capabilities.
Restart the Apache service to load PHP modules:
sudo systemctl restart httpdVerify PHP installation by creating a test file:
echo "<?php phpinfo(); ?>" | sudo tee /var/www/html/info.phpAccess the PHP information page through your web browser to confirm proper installation and module loading.
phpMyAdmin Installation Methods
Installation via Manual Download
Download the latest stable phpMyAdmin release from the official website:
cd /tmp
wget https://www.phpmyadmin.net/downloads/phpMyAdmin-latest-all-languages.tar.gzExtract the downloaded archive:
tar xzf phpMyAdmin-latest-all-languages.tar.gzMove the extracted files to the appropriate directory:
sudo mv phpMyAdmin-*-all-languages /usr/share/phpmyadminSet proper ownership and permissions for phpMyAdmin files:
sudo chown -R apache:apache /usr/share/phpmyadmin
sudo chmod -R 755 /usr/share/phpmyadminManual installation provides control over the specific version and ensures access to the latest features. This method requires regular manual updates to maintain security and functionality. The installation process places phpMyAdmin in a system directory accessible by the web server.
Create a symbolic link to make phpMyAdmin accessible through the web server:
sudo ln -s /usr/share/phpmyadmin /var/www/html/phpmyadminInstallation via EPEL Repository
Install the Extra Packages for Enterprise Linux (EPEL) repository:
sudo dnf install epel-release -yUpdate the package repository information:
sudo dnf update -yInstall phpMyAdmin through the repository system:
sudo dnf install phpmyadmin -yRepository installation automatically handles dependencies and provides easy update management through the standard package manager. The EPEL repository maintains tested versions compatible with Rocky Linux systems. Automatic dependency resolution simplifies the installation process and ensures component compatibility.
Repository installation places configuration files in standard system locations and integrates with system management tools. This method provides easier maintenance and update procedures compared to manual installation approaches.
phpMyAdmin Configuration
Creating Configuration File
Navigate to the phpMyAdmin directory and copy the sample configuration:
cd /usr/share/phpmyadmin
sudo cp config.sample.inc.php config.inc.phpEdit the configuration file to customize phpMyAdmin settings:
sudo nano config.inc.phpGenerate a random blowfish secret for session encryption:
openssl rand -base64 32Add the generated secret to the configuration file:
$cfg['blowfish_secret'] = 'your-generated-secret-here';Configure the database server settings within the configuration file. Set the hostname to ‘localhost’ for local database connections. Specify authentication type and configure additional security parameters according to your security requirements.
Database Configuration
Create the phpMyAdmin configuration database:
mysql -u root -p < /usr/share/phpmyadmin/sql/create_tables.sqlCreate a dedicated phpMyAdmin control user account:
CREATE USER 'pmauser'@'localhost' IDENTIFIED BY 'strongpassword';
GRANT SELECT, INSERT, UPDATE, DELETE ON phpmyadmin.* TO 'pmauser'@'localhost';
FLUSH PRIVILEGES;Update the configuration file with the control user credentials:
$cfg['Servers'][$i]['controluser'] = 'pmauser';
$cfg['Servers'][$i]['controlpass'] = 'strongpassword';The control database enhances phpMyAdmin functionality by providing storage for bookmarks, recent tables, favorites, and user preferences. This configuration enables advanced features and improves user experience through persistent settings storage.
Apache Virtual Host Configuration
Create a dedicated Apache configuration file for phpMyAdmin:
sudo nano /etc/httpd/conf.d/phpmyadmin.confAdd the following configuration content:
Alias /phpmyadmin /usr/share/phpmyadmin
<Directory /usr/share/phpmyadmin>
AddDefaultCharset UTF-8
<IfModule mod_authz_core.c>
Require ip 127.0.0.1
Require ip ::1
# Add your network range
Require ip 192.168.1.0/24
</IfModule>
</Directory>
<Directory /usr/share/phpmyadmin/setup>
<IfModule mod_authz_core.c>
Require ip 127.0.0.1
Require ip ::1
</IfModule>
</Directory>The Apache configuration restricts access to specific IP addresses and networks. Customize the IP ranges according to your security requirements and network topology. The setup directory requires additional restrictions due to its sensitive nature.
Restart Apache to apply the configuration changes:
sudo systemctl restart httpdPHP Configuration Optimization
Modify PHP settings for optimal phpMyAdmin performance:
sudo nano /etc/php.iniAdjust the following parameters:
memory_limit = 256M
upload_max_filesize = 128M
post_max_size = 128M
max_execution_time = 300
max_input_time = 300These optimizations accommodate large database imports and improve overall performance. Memory limits prevent PHP from consuming excessive system resources while allowing sufficient capacity for database operations. Upload and execution time limits accommodate large file imports and complex queries.
Restart Apache to apply PHP configuration changes:
sudo systemctl restart httpdSecurity Hardening and Access Control
Access Control Configuration
Implement IP-based access restrictions to limit phpMyAdmin accessibility:
<Directory /usr/share/phpmyadmin>
<RequireAll>
Require ip 192.168.1.0/24
Require ip 10.0.0.0/8
# Add specific trusted IPs
Require ip 203.0.113.100
</RequireAll>
</Directory>Configure HTTP authentication for an additional security layer:
<Directory /usr/share/phpmyadmin>
AuthType Basic
AuthName "phpMyAdmin Access"
AuthUserFile /etc/httpd/.htpasswd
Require valid-user
</Directory>Create the password file for HTTP authentication:
sudo htpasswd -c /etc/httpd/.htpasswd adminNetwork-based access control provides the first line of defense against unauthorized access attempts. Combine IP restrictions with authentication requirements for enhanced security. Regular review and updates of access control lists maintain security effectiveness.
User Account Security
Create dedicated database user accounts with limited privileges:
CREATE USER 'dbuser'@'localhost' IDENTIFIED BY 'complexpassword';
GRANT SELECT, INSERT, UPDATE, DELETE ON specific_database.* TO 'dbuser'@'localhost';
FLUSH PRIVILEGES;Implement strong password policies for all database accounts. Passwords should include uppercase and lowercase letters, numbers, and special characters. Minimum password length should exceed eight characters with complexity requirements enforced through policy.
Disable remote root access to prevent unauthorized administrative access:
DELETE FROM mysql.user WHERE User='root' AND Host NOT IN ('localhost', '127.0.0.1', '::1');
FLUSH PRIVILEGES;Regular account auditing identifies unused or compromised accounts. Remove unnecessary user accounts and review permissions periodically to maintain security posture.
SSL/TLS Implementation
Install SSL certificate for encrypted connections:
sudo dnf install mod_ssl -yConfigure SSL virtual host for phpMyAdmin:
<VirtualHost *:443>
ServerName yourdomain.com
DocumentRoot /var/www/html
SSLEngine on
SSLCertificateFile /etc/pki/tls/certs/localhost.crt
SSLCertificateKeyFile /etc/pki/tls/private/localhost.key
Alias /phpmyadmin /usr/share/phpmyadmin
</VirtualHost>Force HTTPS redirection for all phpMyAdmin access:
<VirtualHost *:80>
ServerName yourdomain.com
Redirect permanent /phpmyadmin https://yourdomain.com/phpmyadmin
</VirtualHost>Additional Security Measures
Change the default phpMyAdmin URL to obscure its location:
Alias /secretpath /usr/share/phpmyadminConfigure session timeout to automatically log out inactive users:
$cfg['LoginCookieValidity'] = 1800; // 30 minutesImplement fail2ban for automated intrusion prevention:
sudo dnf install fail2ban -yConfigure fail2ban to monitor Apache logs for phpMyAdmin brute force attempts. Regular security updates and monitoring maintain protection against emerging threats. Log file analysis reveals potential security incidents and helps identify attack patterns.
Testing and Verification
Initial Access Testing
Access phpMyAdmin through your web browser using the configured URL:
https://your-server-ip/phpmyadminThe login screen should display properly with appropriate styling and functionality. Test database connectivity by logging in with the root account or a configured database user. Verify that the interface loads completely without errors or missing components.
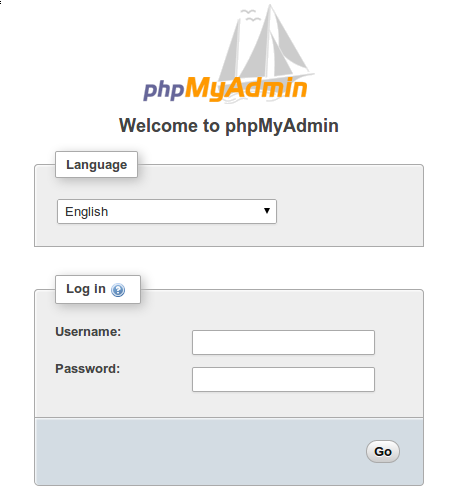
Navigate through various phpMyAdmin sections to ensure full functionality. Test database browsing, table viewing, and basic operations like creating and dropping databases. The interface should respond promptly and display information accurately.
Functionality Testing
Create a test database to verify full operational capability:
CREATE DATABASE test_db;
USE test_db;
CREATE TABLE test_table (id INT PRIMARY KEY, name VARCHAR(50));
INSERT INTO test_table VALUES (1, 'Test Entry');Test import and export functionality using sample data files. Upload a small SQL file to verify import capabilities work correctly. Export the test database to confirm export functionality operates properly.
Verify user permission systems by creating limited user accounts and testing their access restrictions. Confirm that users can only access authorized databases and perform permitted operations.
Security Testing
Verify access restrictions by attempting connections from unauthorized IP addresses. The system should deny access and display appropriate error messages. Test authentication mechanisms to ensure proper credential validation.
Validate SSL certificate functionality and force HTTPS redirection. Confirm that all connections use encrypted protocols and certificate warnings don’t appear for valid certificates. Test firewall rules to ensure proper port access and restriction.
Troubleshooting Common Issues
Access Permission Errors
The “Forbidden” error typically indicates Apache configuration or permission issues. Verify directory permissions for phpMyAdmin files:
ls -la /usr/share/phpmyadminCorrect file ownership if necessary:
sudo chown -R apache:apache /usr/share/phpmyadminSELinux may prevent Apache from accessing phpMyAdmin files. Check SELinux status and configure appropriate contexts:
sudo setsebool -P httpd_can_network_connect 1
sudo restorecon -R /usr/share/phpmyadminReview Apache error logs for specific permission issues:
sudo tail -f /var/log/httpd/error_logPHP Extension Issues
Missing PHP extensions cause various phpMyAdmin errors. Install additional required extensions:
sudo dnf install php-xml php-common php-gd php-intl -yVerify PHP extension loading:
php -m | grep -i extension_nameRestart Apache after installing new PHP extensions:
sudo systemctl restart httpdDatabase Connection Problems
Database connection failures require systematic troubleshooting. Verify MariaDB service status:
sudo systemctl status mariadbTest database connectivity manually:
mysql -u root -pCheck network connectivity and port accessibility:
netstat -tulpn | grep 3306Review database error logs for specific connection issues:
sudo tail -f /var/log/mariadb/mariadb.logBest Practices and Maintenance
Regular Updates
Maintain current phpMyAdmin versions to address security vulnerabilities and benefit from feature improvements. Monitor official announcements and security advisories for update notifications.
For manual installations, download and install updates regularly:
cd /tmp
wget https://www.phpmyadmin.net/downloads/phpMyAdmin-latest-all-languages.tar.gzRepository installations simplify update procedures:
sudo dnf update phpmyadminSchedule regular system maintenance windows for applying updates and security patches. Test updates in development environments before applying to production systems.
Performance Optimization
Monitor system resource usage and optimize MySQL configuration parameters. Adjust buffer sizes and cache settings based on database size and usage patterns:
innodb_buffer_pool_size = 256M
query_cache_size = 64M
tmp_table_size = 32MConfigure PHP opcache for improved performance:
opcache.enable = 1
opcache.memory_consumption = 128
opcache.max_accelerated_files = 4000Regular database maintenance improves performance and prevents issues. Schedule automated maintenance tasks including table optimization and log rotation.
Backup and Recovery
Implement comprehensive backup strategies covering databases, configuration files, and phpMyAdmin installations. Automated backups ensure data protection without manual intervention:
#!/bin/bash
mysqldump --all-databases > /backup/mysql_$(date +%Y%m%d).sql
tar czf /backup/phpmyadmin_config_$(date +%Y%m%d).tar.gz /usr/share/phpmyadmin/config.inc.phpTest backup restoration procedures regularly to verify data integrity and recovery capabilities. Document recovery procedures and maintain current restoration instructions.
Congratulations! You have successfully installed phpMyAdmin. Thanks for using this tutorial for installing phpMyAdmin on your Rocky Linux 10 system. For additional help or useful information, we recommend you check the official phpMyAdmin website.