How To Install Portainer on Fedora 42

Container management has become essential for modern software deployment. Portainer stands out as the most intuitive Docker management solution, offering a powerful web-based interface that simplifies container orchestration. This comprehensive guide walks you through installing Portainer on Fedora 42, from initial system preparation to advanced configuration options.
Fedora 42 provides an excellent foundation for containerized environments, combining cutting-edge technology with enterprise-grade stability. The installation process involves multiple steps, but following this tutorial ensures a smooth, secure deployment of Portainer that will serve your container management needs effectively.
What is Portainer and Why Use It?
Understanding Portainer’s Core Functionality
Portainer transforms Docker container management from complex command-line operations into an intuitive graphical experience. This lightweight management tool provides comprehensive oversight of Docker environments, including containers, images, volumes, and networks through a single web interface.
The platform offers two primary editions: Community Edition (CE) and Business Edition (BE). Community Edition provides essential container management features suitable for individual developers and small teams. Business Edition extends functionality with advanced security features, RBAC (Role-Based Access Control), and enterprise support options.
Container visualization becomes effortless with Portainer’s dashboard, displaying real-time resource usage, container states, and system health metrics. The interface eliminates the need for memorizing complex Docker commands while maintaining full control over containerized applications.
Advantages of Fedora 42 for Container Management
Fedora 42 represents a mature, secure platform optimized for containerized workloads. The distribution includes updated kernel features that enhance container performance and security isolation. DNF package manager streamlines software installation and dependency management, ensuring clean system maintenance.
Enterprise-ready features include SELinux integration, which provides mandatory access controls for containers. The system’s regular update cycle ensures access to latest security patches and performance improvements. Fedora’s commitment to open-source technologies aligns perfectly with container ecosystem principles.
System Requirements and Prerequisites
Hardware Specifications
Successful Portainer deployment requires adequate system resources. Minimum requirements include 2GB RAM, though 4GB provides better performance for multiple containers. Storage needs vary based on container usage, but allocating at least 20GB for the root filesystem ensures sufficient space for Docker images and volumes.
CPU requirements remain modest, with dual-core processors handling typical workloads effectively. Network connectivity must support required ports, including 9443 for HTTPS access and 9000 for HTTP connections. Additional ports may be needed depending on containerized applications.
Software Prerequisites
Docker Engine version 1.10 or higher provides the foundation for Portainer installation. Fedora 42 includes compatible Docker packages through official repositories. Administrative privileges (sudo access) are essential for installation and configuration tasks.
Basic command-line familiarity helps navigate the installation process, though this guide provides complete command examples. Network port availability verification prevents conflicts during installation. Firewall configuration knowledge assists with security setup.
Pre-Installation System Check
Begin by updating your Fedora 42 system to ensure all packages reflect the latest versions:
sudo dnf update -y
sudo rebootVerify system resources and available disk space:
df -h
free -h
lscpuCheck network connectivity and DNS resolution:
ping -c 4 google.com
nslookup docker.comInstalling Docker Engine on Fedora 42
Removing Conflicting Packages
Fedora repositories may contain unofficial Docker packages that conflict with official installations. Remove these packages to prevent issues:
sudo dnf remove docker \
docker-client \
docker-client-latest \
docker-common \
docker-latest \
docker-latest-logrotate \
docker-logrotate \
docker-selinux \
docker-engine-selinux \
docker-engineClean package cache and remove configuration remnants:
sudo dnf clean all
sudo rm -rf /var/lib/docker
sudo rm -rf /etc/dockerSetting Up Docker Repository
Docker’s official repository provides the most stable and secure installation source. Add the repository with proper GPG verification:
sudo dnf install -y dnf-plugins-core
sudo dnf config-manager --add-repo https://download.docker.com/linux/fedora/docker-ce.repoImport Docker’s GPG key for package verification:
sudo rpm --import https://download.docker.com/linux/fedora/gpgUpdate package metadata to include Docker repository:
sudo dnf makecacheInstalling Docker Components
Install Docker Engine, CLI tools, and containerd runtime:
sudo dnf install -y docker-ce docker-ce-cli containerd.io docker-buildx-plugin docker-compose-pluginThis command installs all essential Docker components. The installation process downloads approximately 100MB of packages, depending on existing system libraries.
Configuring Docker Service
Enable Docker service for automatic startup:
sudo systemctl enable docker
sudo systemctl start dockerAdd your user to the docker group to run Docker commands without sudo:
sudo usermod -aG docker $USERLog out and back in for group changes to take effect. Verify Docker installation:
docker --version
docker run hello-worldThe hello-world container confirms Docker functionality and network connectivity.
Installing Portainer Community Edition
Method 1: Direct Docker Installation
Create a dedicated volume for Portainer data persistence:
docker volume create portainer_dataDeploy Portainer using the official Docker image:
docker run -d -p 8000:8000 -p 9443:9443 --name portainer --restart=always -v /var/run/docker.sock:/var/run/docker.sock -v portainer_data:/data portainer/portainer-ce:latestThis command creates a container with several important configurations:
- Port 8000: Agent communication
- Port 9443: HTTPS web interface
- Port 9000: HTTP web interface (optional)
- Automatic restart policy
- Docker socket mounting for container management
- Persistent data storage
Method 2: Docker Compose Installation
Create a dedicated directory for Portainer configuration:
mkdir -p ~/portainer
cd ~/portainerCreate a Docker Compose file with comprehensive configuration:
version: '3.8'
services:
portainer:
image: portainer/portainer-ce:latest
container_name: portainer
restart: unless-stopped
ports:
- "8000:8000"
- "9443:9443"
volumes:
- /var/run/docker.sock:/var/run/docker.sock
- portainer_data:/data
environment:
- TZ=America/New_York
security_opt:
- no-new-privileges:true
volumes:
portainer_data:Deploy using Docker Compose:
docker-compose up -dInstallation Verification
Confirm Portainer container is running:
docker psCheck container logs for startup issues:
docker logs portainerTest network connectivity to Portainer interface:
curl -k https://localhost:9443Initial Portainer Setup and Configuration
First-Time Web Access
Open your web browser and navigate to https://your-server-ip:9443. Accept the self-signed SSL certificate warning, which is normal for initial installations. The secure connection ensures encrypted communication between your browser and Portainer.
For local installations, use https://localhost:9443 or https://127.0.0.1:9443. The interface loads within seconds on properly configured systems.
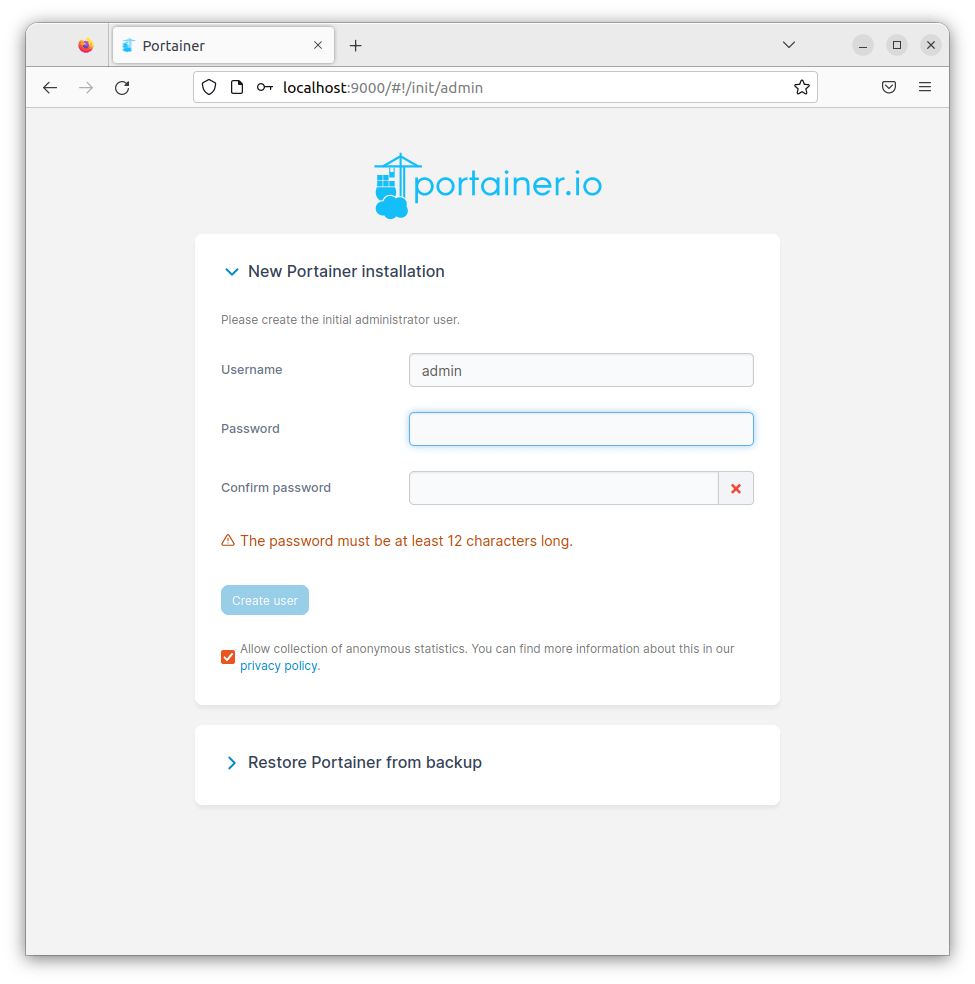
Administrator Account Creation
The initial setup requires creating an administrator account. Choose a strong password containing at least 12 characters with mixed case letters, numbers, and symbols. This account provides full administrative access to your Docker environment.
Username: admin
Password: [Strong password with 12+ characters]Click “Create user” to proceed. The system immediately redirects to the environment setup page.
Environment Configuration
Select “Local” environment for single-server installations. This connects Portainer to the local Docker daemon through the socket mounting configured during installation.
The dashboard displays comprehensive system information:
- Container count and status
- Image repository size
- Volume usage statistics
- Network configurations
- System resource utilization
Security Configuration
Navigate to Settings > SSL certificate to replace the self-signed certificate with a proper SSL certificate for production environments. Upload your certificate and private key files, then restart Portainer for changes to take effect.
Firewall and Network Configuration
Configuring Firewall Rules
Fedora 42 includes firewalld for network security management. Open required ports for Portainer access:
sudo firewall-cmd --permanent --add-port=9443/tcp
sudo firewall-cmd --permanent --add-port=9000/tcp
sudo firewall-cmd --permanent --add-port=8000/tcp
sudo firewall-cmd --reloadVerify firewall rules:
sudo firewall-cmd --list-portsNetwork Security Best Practices
Restrict Portainer access to trusted networks only. Configure firewall rules for specific source IP addresses:
sudo firewall-cmd --permanent --add-rich-rule="rule family='ipv4' source address='192.168.1.0/24' port protocol='tcp' port='9443' accept"
sudo firewall-cmd --reloadConsider implementing a reverse proxy with Nginx or Apache for additional security layers. This approach provides SSL termination, load balancing, and advanced access controls.
Advanced Configuration Options
Custom SSL Certificate Installation
Replace Portainer’s self-signed certificate with a trusted SSL certificate. Generate or obtain certificates from a Certificate Authority (CA):
sudo mkdir -p /opt/portainer/certs
sudo cp your-certificate.crt /opt/portainer/certs/
sudo cp your-private-key.key /opt/portainer/certs/
sudo chown -R 1000:1000 /opt/portainer/certsUpdate Portainer container with certificate volume mounting:
docker stop portainer
docker rm portainer
docker run -d -p 8000:8000 -p 9443:9443 --name portainer --restart=always -v /var/run/docker.sock:/var/run/docker.sock -v portainer_data:/data -v /opt/portainer/certs:/certs portainer/portainer-ce:latest --ssl --sslcert /certs/your-certificate.crt --sslkey /certs/your-private-key.keyResource Management Configuration
Optimize Portainer performance through resource allocation controls. Configure memory and CPU limits:
docker update --memory=1g --cpus=1 portainerMonitor resource usage through Docker stats:
docker stats portainerBackup and Recovery Setup
Implement automated backup procedures for Portainer data:
#!/bin/bash
BACKUP_DIR="/opt/backups/portainer"
DATE=$(date +%Y%m%d_%H%M%S)
mkdir -p $BACKUP_DIR
docker run --rm -v portainer_data:/data -v $BACKUP_DIR:/backup alpine tar czf /backup/portainer_backup_$DATE.tar.gz -C /data .Test backup restoration procedures regularly to ensure data integrity.
Troubleshooting Common Issues
Docker Service Problems
If Docker fails to start, check service status and logs:
sudo systemctl status docker
sudo journalctl -u docker.serviceCommon solutions include:
- Clearing Docker daemon configuration conflicts
- Checking storage driver compatibility
- Verifying user permissions
- Restarting Docker service
Port Conflict Resolution
Identify processes using required ports:
sudo netstat -tulpn | grep :9443
sudo lsof -i :9443Stop conflicting services or change Portainer port configuration:
docker stop portainer
docker rm portainer
docker run -d -p 8000:8000 -p 9444:9443 --name portainer --restart=always -v /var/run/docker.sock:/var/run/docker.sock -v portainer_data:/data portainer/portainer-ce:latestPermission and Access Issues
Docker socket permissions affect Portainer functionality. Verify socket permissions:
ls -la /var/run/docker.sock
sudo chmod 666 /var/run/docker.sockSELinux contexts may require adjustment:
sudo setsebool -P container_manage_cgroup true
sudo semanage permissive -a container_tContainer Management with Portainer
Basic Container Operations
Portainer simplifies container lifecycle management through intuitive interface controls. The Containers section displays all running and stopped containers with comprehensive details including resource usage, network connections, and volume mounts.
Create new containers by clicking “Add container” and configuring:
- Image selection from local registry or Docker Hub
- Port mapping for network access
- Volume mounting for persistent storage
- Environment variables for application configuration
- Resource limits for performance optimization
Image Management
The Images section provides centralized image repository management. Pull images directly from Docker Hub, private registries, or upload custom images through the web interface.
Image management features include:
- Tag-based organization
- Size optimization recommendations
- Security vulnerability scanning
- Automated image updates
- Registry authentication management
Volume and Network Management
Portainer streamlines storage and network configuration through graphical interfaces. Create named volumes for persistent data storage across container restarts.
Network management capabilities include:
- Custom network creation
- Container network assignment
- Port forwarding configuration
- Network isolation policies
- Inter-container communication setup
Security Best Practices
Access Control Implementation
Configure user authentication through Settings > Authentication. Portainer supports multiple authentication methods including internal database, LDAP, and OAuth providers.
Role-based access control (RBAC) limits user permissions based on assigned roles:
- Administrator: Full system access
- Operator: Container management without system changes
- Read-only: Monitoring and viewing permissions
Container Security
Implement security scanning for container images through integrated vulnerability databases. Configure automated scanning policies to identify security issues before deployment.
Security recommendations include:
- Regular image updates
- Minimal base image usage
- Non-root container execution
- Resource limit enforcement
- Network segmentation
Maintenance and Updates
Updating Portainer
Regular updates ensure access to latest features and security patches. Update Portainer while preserving configuration data:
docker stop portainer
docker rm portainer
docker pull portainer/portainer-ce:latest
docker run -d -p 8000:8000 -p 9443:9443 --name portainer --restart=always -v /var/run/docker.sock:/var/run/docker.sock -v portainer_data:/data portainer/portainer-ce:latestSystem Maintenance
Maintain optimal performance through regular system maintenance:
# Clean unused Docker resources
docker system prune -a
# Update Fedora packages
sudo dnf update
# Monitor system logs
sudo journalctl -u docker.service --since yesterdaySchedule maintenance tasks using cron jobs for automated execution.
Congratulations! You have successfully installed Portainer. Thanks for using this tutorial for installing Portainer on Fedora 42 Linux system. For additional help or useful information, we recommend you check the official Portainer website.