How To Install Pritunl VPN Server on AlmaLinux 10

Pritunl stands as one of the most powerful and user-friendly open-source VPN solutions available today. This enterprise-grade distributed VPN server offers exceptional security, scalability, and ease of management through its intuitive web-based interface. For system administrators seeking to deploy a robust VPN infrastructure on AlmaLinux 10, Pritunl provides an ideal combination of OpenVPN and WireGuard support, MongoDB-backed architecture, and comprehensive management capabilities.
AlmaLinux 10 serves as an excellent foundation for hosting Pritunl, offering enterprise-level stability and security features that complement Pritunl’s advanced functionality. The platform’s RHEL compatibility ensures reliable performance while maintaining the flexibility needed for modern VPN deployments. This comprehensive guide will walk you through every aspect of installing and configuring Pritunl VPN server on AlmaLinux 10, from initial system preparation to advanced security hardening.
Prerequisites and System Requirements
Before beginning the Pritunl installation process, ensure your AlmaLinux 10 system meets the necessary requirements for optimal performance and stability.
Hardware Requirements
Your server should have a minimum of 1GB RAM, though 2GB or more is recommended for production environments. CPU requirements are modest, with a single core sufficient for small deployments, but multi-core processors provide better performance for high-traffic scenarios. Storage needs vary based on user count and logging requirements, with at least 10GB of free disk space recommended for initial installation and operation.
Software Requirements
A fresh AlmaLinux 10 installation provides the cleanest foundation for Pritunl deployment. Ensure you have a user account with sudo privileges, as root access is required for package installation and system configuration. While not mandatory, having a domain name pointing to your server significantly simplifies client access and SSL certificate management.
Network Requirements
Proper network configuration is crucial for VPN functionality. Your server needs a static IP address or dynamic DNS setup for consistent client connectivity. Essential firewall ports include HTTP (80), HTTPS (443), and the VPN service ports (typically 1194 for OpenVPN and various ports for WireGuard). Consider your network topology and ensure the chosen VPN subnet doesn’t conflict with existing local networks.
System Preparation and Updates
Begin by ensuring your AlmaLinux 10 system is fully updated and properly configured for Pritunl installation.
Updating the System
Start with a comprehensive system update to ensure all packages are current:
sudo dnf update -y
sudo dnf install epel-release -yThe EPEL (Extra Packages for Enterprise Linux) repository provides additional packages essential for Pritunl functionality. This repository extends AlmaLinux’s package availability with community-maintained software that complements enterprise distributions.
Firewall Configuration
Proper firewall configuration is critical for VPN operation. Configure firewalld to allow necessary traffic:
sudo firewall-cmd --permanent --add-service=http
sudo firewall-cmd --permanent --add-service=https
sudo firewall-cmd --permanent --add-port=1194/tcp
sudo firewall-cmd --permanent --add-port=1194/udp
sudo firewall-cmd --reloadThese commands open ports for web interface access and VPN traffic. The HTTP and HTTPS services enable web-based management, while port 1194 handles OpenVPN connections.
SELinux Considerations
Verify SELinux status and ensure proper configuration:
sudo getenforceWhile SELinux provides additional security, it may require specific policies for Pritunl operation. For production environments, consider configuring appropriate SELinux policies rather than disabling the service entirely.
Repository Setup and GPG Key Management
Pritunl requires specific repositories for installation, including MongoDB and the Pritunl package repository itself.
Adding MongoDB Repository
Pritunl utilizes MongoDB as its backend database, requiring the official MongoDB repository:
sudo tee /etc/yum.repos.d/mongodb-org-8.0.repo << EOF
[mongodb-org-8.0]
name=MongoDB Repository
baseurl=https://repo.mongodb.org/yum/redhat/9/mongodb-org/8.0/x86_64/
gpgcheck=1
enabled=1
gpgkey=https://pgp.mongodb.com/server-8.0.asc
EOFThis configuration creates a repository file pointing to MongoDB 8.0, which provides the database backend for Pritunl’s user management and configuration storage.
Adding Pritunl Repository
Create the Pritunl repository configuration:
sudo tee /etc/yum.repos.d/pritunl.repo << EOF
[pritunl]
name=Pritunl Repository
baseurl=https://repo.pritunl.com/stable/yum/oraclelinux/9/
gpgcheck=1
enabled=1
gpgkey=https://raw.githubusercontent.com/pritunl/pgp/master/pritunl_repo_pub.asc
EOFRepository Verification
Verify repository addition and connectivity:
sudo dnf repolist | grep -E "(mongodb|pritunl)"
sudo dnf check-updateThese commands confirm repository availability and ensure package managers can access the necessary software sources.
MongoDB Database Installation and Configuration
MongoDB serves as Pritunl’s database backend, storing user information, server configurations, and operational data.
MongoDB Installation Process
Install MongoDB using the configured repository:
sudo dnf install mongodb-org -yThis command installs the complete MongoDB package suite, including the database server, client tools, and administrative utilities.
MongoDB Service Management
Configure MongoDB for automatic startup and begin the service:
sudo systemctl start mongod
sudo systemctl enable mongod
sudo systemctl status mongodVerify MongoDB is running correctly by checking the service status. The output should indicate an active and running state.
Database Preparation for Pritunl
While Pritunl automatically configures its database requirements, ensure MongoDB is accessible:
sudo ss -tlnp | grep :27017This command verifies MongoDB is listening on its default port (27017), confirming the database is ready for Pritunl integration.
MongoDB Security Hardening
For production environments, implement basic MongoDB security measures:
sudo systemctl restart mongodConsider configuring authentication and network binding based on your security requirements. MongoDB’s default configuration provides reasonable security for single-server deployments.
Pritunl VPN Server Installation
With repositories configured and MongoDB operational, proceed with Pritunl installation.
Package Installation
Install Pritunl using the configured repository:
sudo dnf install pritunl -yThe installation process downloads Pritunl and its dependencies, preparing the system for VPN server operation.
Service Configuration
Configure Pritunl for automatic startup:
sudo systemctl start pritunl
sudo systemctl enable pritunl
sudo systemctl status pritunlVerify the Pritunl service is active and running properly. The status command should show an active state without errors.
Initial System Integration
Pritunl integrates with systemd for service management and creates necessary configuration directories. Verify the installation by checking the Pritunl version:
sudo pritunl versionThis command confirms successful installation and displays the installed Pritunl version.
Initial Pritunl Configuration
Pritunl requires initial configuration before the web interface becomes accessible.
Setup Key Generation
Generate the initial setup key required for database initialization:
sudo pritunl setup-keyThis command produces a unique setup key that authorizes initial database configuration. Record this key carefully, as it’s required for web interface setup.
File Limit Configuration
Increase system file limits to prevent connection issues under high load:
sudo sh -c 'echo "* hard nofile 64000" >> /etc/security/limits.conf'
sudo sh -c 'echo "* soft nofile 64000" >> /etc/security/limits.conf'
sudo sh -c 'echo "root hard nofile 64000" >> /etc/security/limits.conf'
sudo sh -c 'echo "root soft nofile 64000" >> /etc/security/limits.conf'These modifications prevent file descriptor exhaustion during high-traffic periods.
Database Connection Configuration
Pritunl automatically connects to the local MongoDB instance. Verify the connection by checking Pritunl logs:
sudo journalctl -u pritunl -fMonitor the logs for successful database connection messages and any configuration warnings.
Web Interface Access and Initial Setup
The Pritunl web interface provides comprehensive management capabilities through a user-friendly dashboard.
Accessing the Web Interface
Open a web browser and navigate to your server’s IP address or domain name using HTTPS:
https://your-server-ip-or-domainThe initial access presents a database setup screen requiring the previously generated setup key.
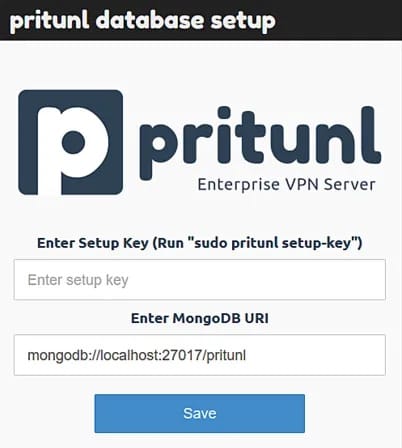
First-Time Setup Process
Enter the setup key generated earlier into the provided field and click Save. The system initializes the database and prepares the administrative interface. This process may take several moments depending on system performance.
Default Credentials Management
Retrieve the default administrative credentials:
sudo pritunl default-passwordThis command displays the default username and password for initial login. Record these credentials securely before proceeding.
Administrative Account Configuration
Log in using the default credentials and immediately change the administrator password. Navigate to the user settings and establish a strong, unique password. Consider enabling two-factor authentication for enhanced security.
VPN Server Configuration
Pritunl’s organizational structure requires creating organizations, users, and servers before establishing VPN connectivity.
Creating Organizations
Organizations group users and servers logically within Pritunl. Create a new organization through the web interface by clicking “Add Organization” and providing a descriptive name. Organizations enable granular access control and simplified user management.
Server Creation and Configuration
Add a new VPN server by navigating to the Servers section and clicking “Add Server”. Configure essential parameters including:
- Server name and description
- Network address range (avoid conflicts with existing networks)
- Port and protocol selection (UDP recommended for performance)
- DNS server configuration (consider using public DNS servers like 8.8.8.8)
Network Routing Configuration
Configure server routes to control traffic flow through the VPN. The default 0.0.0.0/0 route tunnels all traffic through the VPN server. For split-tunnel configurations, remove the default route and add specific network ranges as needed.
Server Attachment and Management
Attach organizations to servers by clicking “Attach Organization” and selecting the appropriate organization. Start the server by clicking the “Start Server” button. Monitor server status through the dashboard, which displays connection counts and operational status.
User Management and Access Control
Effective user management ensures secure and organized VPN access.
Creating VPN Users
Add users through the Users section by clicking “Add User” within the appropriate organization. Provide user details including name, email address (optional), and PIN (optional). The PIN provides an additional authentication layer for enhanced security.
User Authentication Options
Pritunl supports multiple authentication methods:
- PIN-based authentication for simple user verification
- Two-factor authentication using Google Authenticator or similar applications
- Integration with external authentication systems for enterprise environments
Profile Generation and Distribution
Download user profiles through the Users section by clicking the download button next to each user. Pritunl generates OpenVPN-compatible profiles that work with various client applications. Profile links provide temporary download URLs for secure distribution.
User Access Management
Monitor user connections through the dashboard and manage access by enabling or disabling accounts as needed. Set connection limits and bandwidth restrictions based on organizational requirements.
Client Installation and Connection
Pritunl clients enable users to connect to the VPN server from various platforms.
Pritunl Client Options
Pritunl offers multiple client options:
- Command-line client for Linux systems
- Graphical clients for Windows and macOS
- Mobile applications for iOS and Android devices
Client Configuration
Install the Pritunl client on AlmaLinux systems:
sudo dnf install pritunl-clientAdd user profiles using the command-line interface:
sudo pritunl-client add pritunl://profile-uri-hereConnection Verification
Establish VPN connections using the profile ID:
sudo pritunl-client start profile-idVerify connectivity by checking the connection status and testing network access. Monitor logs for connection issues or authentication failures.
Troubleshooting Common Issues
Address common installation and operational challenges to ensure reliable VPN service.
Installation Problems
Repository connectivity issues may prevent package installation. Verify repository configurations and network connectivity. DNS resolution problems can block package downloads, requiring alternative DNS servers or proxy configurations.
Connection Issues
Firewall misconfigurations commonly block VPN traffic. Ensure all necessary ports are open and properly configured. Client connection failures may result from network routing conflicts or authentication problems.
Performance Optimization
Monitor server resources and adjust configurations for optimal performance. High connection volumes may require increased file limits and system resource allocation. Consider implementing load balancing for large deployments.
Log Analysis and Debugging
Pritunl logs provide valuable troubleshooting information:
sudo journalctl -u pritunl
sudo tail -f /var/log/pritunl.logAnalyze logs for error patterns and connection issues. MongoDB logs may also reveal database-related problems affecting Pritunl operation.
Security Best Practices and Hardening
Implement comprehensive security measures to protect your Pritunl deployment.
Server Security Hardening
Keep AlmaLinux 10 updated with latest security patches. Remove unnecessary services and software to reduce attack surface. Configure SSH key-based authentication and disable password authentication for remote access.
VPN Security Configuration
Use strong encryption protocols and regularly update certificates. Implement proper access controls and monitor user activity for suspicious behavior. Regular security audits help identify potential vulnerabilities.
Monitoring and Auditing
Enable comprehensive logging for security monitoring. Implement intrusion detection systems and regular security assessments. Automated monitoring tools can alert administrators to security events or performance issues.
Regular Maintenance Tasks
Schedule regular updates for Pritunl, MongoDB, and AlmaLinux. Implement backup procedures for configuration data and user profiles. Test disaster recovery procedures to ensure business continuity.
Congratulations! You have successfully installed Pritunl VPN. Thanks for using this tutorial for installing the Pritunl VPN Server on your AlmaLinux OS 10 system. For additional help or useful information, we recommend you check the official Pritunl website.