How To Install Pritunl VPN Server on Fedora 42

Virtual Private Networks (VPNs) have become essential tools for securing network communications in today’s digital landscape. Pritunl, an open-source VPN server solution, offers a robust platform with an intuitive web interface that simplifies VPN management. This comprehensive guide will walk you through the complete process of installing and configuring Pritunl VPN Server on Fedora 42, providing you with a secure, reliable VPN infrastructure for your organizational needs.
Understanding Pritunl VPN
Pritunl is a powerful, enterprise-grade VPN server solution that combines simplicity with advanced functionality. Built as an open-source alternative to commercial VPN platforms, Pritunl provides a user-friendly web interface that makes VPN management accessible even to those with limited technical expertise.
Pritunl implements OpenVPN and WireGuard protocols, offering strong encryption standards to ensure your data remains secure during transmission. The architecture supports both single-server deployments for smaller organizations and distributed deployments for enterprises requiring high availability and scalability.
One of Pritunl’s key advantages over other VPN solutions is its comprehensive feature set, including multi-factor authentication, user management, and detailed access controls. These security measures, combined with its intuitive interface, make Pritunl an excellent choice for organizations of all sizes seeking to implement a reliable VPN infrastructure.
Prerequisites
Before proceeding with the installation process, ensure your system meets the following requirements:
- A Fedora 42 server with at least 1GB RAM and 10GB disk space
- Root or sudo access to the server
- A fully qualified domain name (FQDN) pointed to your server (recommended but optional)
- Unrestricted outbound internet access from your server
- Basic familiarity with Linux command-line operations
Your network configuration should allow traffic on the following ports:
- TCP port 443 (for the web interface)
- UDP port 1194 (default OpenVPN port)
- TCP port 80 (for Let’s Encrypt verification)
- UDP port 51820 (if using WireGuard)
Additionally, ensure that your server’s firewall is properly configured to allow these connections. Fedora uses firewalld by default, which we’ll configure later in this guide.
Preparing Your Fedora 42 System
The first step toward a successful Pritunl installation is preparing your Fedora 42 system. Begin by updating your system packages to ensure you’re working with the latest software versions and security patches.
sudo dnf update -yAfter updating your system, install the necessary development tools and dependencies that Pritunl requires:
sudo dnf install -y dnf-plugins-core
sudo dnf install -y python3 python3-devel openssl-devel net-toolsPritunl requires specific network kernel modules for optimal performance. Load these modules and configure them to start automatically after system reboots:
sudo modprobe ip_tables
sudo modprobe iptable_filter
sudo modprobe iptable_nat
echo "ip_tables" | sudo tee -a /etc/modules-load.d/pritunl.conf
echo "iptable_filter" | sudo tee -a /etc/modules-load.d/pritunl.conf
echo "iptable_nat" | sudo tee -a /etc/modules-load.d/pritunl.confFor optimal performance and connection handling, adjust the system limits:
sudo sh -c 'echo "* hard nofile 64000" >> /etc/security/limits.conf'
sudo sh -c 'echo "* soft nofile 64000" >> /etc/security/limits.conf'
sudo sh -c 'echo "root hard nofile 64000" >> /etc/security/limits.conf'
sudo sh -c 'echo "root soft nofile 64000" >> /etc/security/limits.conf'To ensure proper VPN functionality, configure the firewall to allow necessary traffic. Fedora 42 uses firewalld by default:
sudo firewall-cmd --permanent --add-port=443/tcp
sudo firewall-cmd --permanent --add-port=1194/udp
sudo firewall-cmd --permanent --add-port=80/tcp
sudo firewall-cmd --permanent --add-port=51820/udp
sudo firewall-cmd --reloadFinally, if SELinux is enabled (which is recommended for enhanced security), configure it to allow Pritunl to operate correctly:
sudo setsebool -P httpd_can_network_connect 1Installing MongoDB
Pritunl uses MongoDB as its database backend to store configuration data, user information, and operational statistics. Let’s install MongoDB 6.0 to ensure compatibility with Pritunl.
First, create a repository file for MongoDB:
sudo tee /etc/yum.repos.d/mongodb-org-6.0.repo << EOF
[mongodb-org-6.0]
name=MongoDB Repository
baseurl=https://repo.mongodb.org/yum/redhat/\$releasever/mongodb-org/6.0/x86_64/
gpgcheck=1
enabled=1
gpgkey=https://www.mongodb.org/static/pgp/server-6.0.asc
EOFNow install MongoDB:
sudo dnf install -y mongodb-orgAfter installation, start the MongoDB service and enable it to launch automatically at system boot:
sudo systemctl start mongod
sudo systemctl enable mongodVerify that MongoDB is running properly:
sudo systemctl status mongodFor optimal MongoDB performance with Pritunl, adjust the database configuration:
sudo tee /etc/mongod.conf << EOF
storage:
dbPath: /var/lib/mongodb
journal:
enabled: true
systemLog:
destination: file
logAppend: true
path: /var/log/mongodb/mongod.log
net:
port: 27017
bindIp: 127.0.0.1
processManagement:
timeZoneInfo: /usr/share/zoneinfo
EOFRestart MongoDB to apply these changes:
sudo systemctl restart mongodAdding Pritunl Repository
Now that MongoDB is installed and configured, let’s add the Pritunl repository to install the VPN server software.
Create a repository file for Pritunl:
sudo tee /etc/yum.repos.d/pritunl.repo << EOF
[pritunl]
name=Pritunl Repository
baseurl=https://repo.pritunl.com/stable/yum/fedora/42/
gpgcheck=1
enabled=1
EOFImport the Pritunl GPG key to verify package authenticity:
sudo gpg --keyserver hkp://keyserver.ubuntu.com --recv-keys 7568D9BB55FF9E5287D586017AE645C0CF8E292A
sudo gpg --armor --export 7568D9BB55FF9E5287D586017AE645C0CF8E292A > key.tmp
sudo rpm --import key.tmp
rm -f key.tmpIf the keyserver is offline, you can alternatively download the key directly:
curl https://raw.githubusercontent.com/pritunl/pgp/master/pritunl_repo_pub.asc | sudo rpm --import -Update the package database to include the new repository:
sudo dnf updateInstalling Pritunl Server
With the repository properly configured, installing Pritunl is straightforward:
sudo dnf install -y pritunlTo support WireGuard VPN protocol, also install the WireGuard packages:
sudo dnf install -y wireguard-toolsAfter installation, start the Pritunl service and enable it to launch at system boot:
sudo systemctl start pritunl
sudo systemctl enable pritunlVerify that Pritunl is running correctly:
sudo systemctl status pritunlTo ensure the services are functioning properly, check the logs:
sudo journalctl -u pritunl -fInitial Web Interface Setup
With Pritunl installed and running, you can now access the web interface to complete the setup process. Open your web browser and navigate to https://your-server-ip-address.
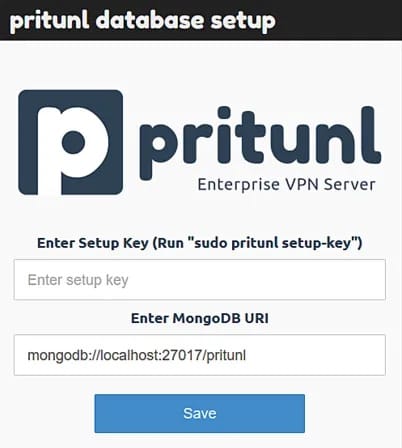
Since Pritunl initially uses a self-signed certificate, your browser will likely display a security warning. Proceed by clicking “Advanced” and then “Accept the Risk and Continue” (the exact wording may vary depending on your browser).
You’ll be presented with a setup screen asking for a setup key. To generate this key, run:
sudo pritunl setup-keyCopy the output key, paste it into the web interface’s setup key field, and click “Save”.
Next, you’ll see the login screen. To retrieve the default login credentials, run:
sudo pritunl default-passwordThis command will display the default username and password. Use these credentials to log in to the web interface.
After logging in for the first time, you’ll be prompted to change the default password. Choose a strong password that includes a mix of uppercase and lowercase letters, numbers, and special characters.
Configuring SSL/TLS Certificates
Secure communication between clients and your VPN server is critical. Pritunl initially uses a self-signed certificate, but for production use, it’s recommended to implement a valid SSL certificate.
Pritunl offers integrated Let’s Encrypt support, making it easy to obtain a free, trusted certificate. To use this feature:
- Navigate to the “Settings” tab in the Pritunl web interface
- Under the “Server” section, locate “Let’s Encrypt Domain”
- Enter your server’s fully qualified domain name
- Click “Save”
Alternatively, if you have an existing SSL certificate, you can upload it through the web interface:
- Navigate to the “Settings” tab
- Locate the “Server Certificate” and “Server Key” fields
- Paste your certificate and key information
- Click “Save”
After configuring SSL, the web interface will automatically restart. You’ll need to log in again, but this time with a secure, trusted connection.
Creating Organizations and Users
Pritunl uses organizations to group users logically. To create your first organization:
- In the web interface, navigate to the “Users” tab
- Click “Add Organization”
- Enter a name for your organization (e.g., “MyCompany”)
- Click “Add” to create the organization
Once you’ve created an organization, you can add users:
- In the “Users” tab, select your organization from the list
- Click “Add User”
- Enter a username
- Optionally, set an email address and PIN
- Choose authentication options (e.g., enable two-factor authentication)
- Click “Add” to create the user
The user will be added to your organization, but they won’t be able to connect until you create a server and link it to the organization.
Configuring Servers
In Pritunl, servers define the VPN connection parameters. To create a server:
- Navigate to the “Servers” tab in the web interface
- Click “Add Server”
- Configure the following settings:
- Name: A descriptive name for your server
- Protocol: Choose between UDP (faster but can be blocked) and TCP (more reliable)
- Port: The port number for VPN connections (default is 1194)
- Virtual Network: The network range for VPN clients (e.g., 10.0.0.0/24)
- DNS Servers: Specify DNS servers for VPN clients
- Click “Add” to create the server
For advanced configurations, you can adjust additional settings such as:
- Intra-server networking for multi-server setups
- IPv6 support
- Compression settings
- Jumbo frames support
Each setting includes a helpful description in the interface to guide your configuration choices.
Attaching Organizations to Servers
After creating both an organization and a server, you need to link them together:
- Navigate to the “Servers” tab
- Click on the server you created
- Click “Attach Organization”
- Select the organization from the dropdown menu
- Click “Attach” to link the organization to the server
You can attach multiple organizations to a single server, which is useful for creating different access levels or security zones. For each attachment, you can configure organization-specific settings such as:
- Network access rules
- DNS settings
- Routes
After attaching an organization, you need to start the server:
- In the “Servers” tab, locate your server
- Click “Start Server”
The server status will change to “Online” once it’s running properly.
Managing Network Routes
Proper routing is essential for VPN functionality. Pritunl allows you to configure routes through the web interface:
- Navigate to the “Servers” tab
- Select your server
- Click on the “Routes” sub-tab
- Click “Add Route”
- Enter the network address (e.g., 192.168.1.0/24)
- Enter the virtual network gateway (usually the first IP in your VPN subnet)
- Click “Add” to create the route
For split tunneling, where only specific traffic goes through the VPN:
- In the server settings, enable “Split Tunnel”
- Add specific routes for the networks you want to access through the VPN
- All other traffic will bypass the VPN
To test network connectivity after setting up routes:
- Connect a client to the VPN
- Attempt to ping resources on the configured routes
- Check the Pritunl logs for any routing errors
Client Profile Generation
Once your server is running and organizations are attached, you can generate client profiles:
- Navigate to the “Users” tab
- Select a user
- Click “Generate New Profile”
- Select the server from the dropdown menu
- Choose the profile format (inline or separate files)
- Click “Generate” to create the profile
Pritunl offers several ways to distribute these profiles:
- Download the profile directly
- Email the profile to the user (if email is configured)
- Generate a temporary download link
- Display a QR code for mobile device scanning
For enhanced security, you can set profiles to expire after a certain period:
- In the user settings, enable “Temporary Profile”
- Set an expiration time (hours, days, or weeks)
- Generate the profile as normal
When the profile expires, the user will need a new profile to connect.
Installing Pritunl Client
While Pritunl works with standard OpenVPN clients, the official Pritunl client offers additional features and a seamless experience. Clients are available for various platforms:
Linux
# For Fedora
sudo tee /etc/yum.repos.d/pritunl-client.repo << EOF [pritunl-client] name=Pritunl Client Repository baseurl=https://repo.pritunl.com/stable/yum/fedora/42/ gpgcheck=1 enabled=1 EOF sudo gpg --keyserver hkp://keyserver.ubuntu.com --recv-keys 7568D9BB55FF9E5287D586017AE645C0CF8E292A sudo gpg --armor --export 7568D9BB55FF9E5287D586017AE645C0CF8E292A > key.tmp
sudo rpm --import key.tmp
rm -f key.tmp
sudo dnf install pritunl-client-electronWindows
- Download the installer from the official website (https://client.pritunl.com)
- Run the installer and follow the on-screen instructions
- The Pritunl client will be installed and added to startup applications
macOS
- Download the macOS package from the official website
- Open the downloaded package and drag the Pritunl application to your Applications folder
- Launch Pritunl from your Applications folder
Mobile Devices
- For Android: Download from Google Play Store
- For iOS: Download from Apple App Store
Connecting to Your VPN Server
Once you have installed the Pritunl client, connecting to your VPN server is straightforward:
- Launch the Pritunl client application
- Import your profile using one of these methods:
- Drag and drop the profile file
- Click “Import Profile” and select the file
- Scan the QR code from the web interface
- Use the profile URI link
- Enter your PIN if configured
- Click “Connect” to establish the VPN connection
To verify the connection is working:
- Check the client status (it should show “Connected”)
- Verify your IP address has changed (using a service like whatismyip.com)
- Test access to resources on your internal network
If you encounter connection issues:
- Check server and client logs
- Verify firewall settings
- Ensure the server is running
Security Best Practices
Implementing proper security measures is crucial for maintaining a secure VPN environment:
Two-Factor Authentication
Enable two-factor authentication for all users:
- Navigate to the “Users” tab
- Edit a user
- Enable “Two-step Authentication”
- Choose an authentication method (Google Authenticator, Duo, etc.)
- Save the changes
Regular Updates
Keep your Pritunl server updated:
sudo dnf update pritunl mongodb-orgUser Access Auditing
Regularly review user access logs:
- Navigate to the “Logs” tab in the web interface
- Filter by user, organization, or action
- Look for unusual patterns or unauthorized access attempts
Server Hardening
Enhance your server’s security:
- Limit SSH access using key-based authentication
- Implement fail2ban to prevent brute-force attacks
- Keep your Fedora system updated
- Use a firewall to restrict unnecessary access
Advanced Configuration Options
For enterprises and advanced users, Pritunl offers additional configuration options:
Custom DNS Configuration
Configure custom DNS servers for VPN clients:
- Navigate to the “Servers” tab
- Edit your server
- Enter DNS server IP addresses in the “DNS Servers” field
- Click “Save”
Traffic Rules
Implement traffic rules to control data flow:
- Navigate to the “Servers” tab
- Select your server
- Click the “Rules” sub-tab
- Add rules to allow or deny specific traffic
Bandwidth Limitations
Set bandwidth limits for users or organizations:
- Edit an organization
- Set “Rate Limit” to restrict bandwidth
- Click “Save”
Server Linking
For distributed deployments, link multiple Pritunl servers:
- Navigate to the “Settings” tab
- Configure “Server ID” and “Server API Key”
- Use these credentials to link servers in different locations
Monitoring and Logging
Effective monitoring ensures your VPN operates smoothly:
Built-in Monitoring
Pritunl includes a dashboard with real-time statistics:
- Navigate to the “Dashboard” tab to view:
- Active users and connections
- Server load and bandwidth usage
- Recent events and alerts
Log Analysis
Review system logs to troubleshoot issues:
# View Pritunl logs
sudo journalctl -u pritunl -f
# View MongoDB logs
sudo journalctl -u mongod -fPerformance Monitoring
Monitor system performance to ensure optimal operation:
# Check system resource usage
top
htopUser Session Tracking
Track active user sessions:
- Navigate to the “Users” tab
- View the “Online” column to see active users
- Click on a user to see detailed connection information
Backup and Recovery
Implementing a backup strategy is essential for disaster recovery:
Database Backup
Regularly back up your MongoDB database:
# Create a database backup
mongodump --out /var/backups/pritunl-$(date +%Y-%m-%d)Configuration Backup
Export your Pritunl configuration:
- Navigate to the “Settings” tab
- Scroll to the “Backup” section
- Click “Download Backup”
- Store the backup file in a secure location
Disaster Recovery
In case of system failure:
- Install Pritunl on a new server
- Restore your MongoDB backup
- Import your configuration backup
- Verify settings and restart services
Troubleshooting Common Issues
Even with careful setup, issues may arise. Here are solutions to common problems:
Connection Failures
If clients can’t connect:
- Check server status and logs
- Verify firewall settings
- Ensure the client profile is current
- Check for network issues between client and server
Authentication Problems
If users can’t authenticate:
- Reset user passwords or PINs
- Verify two-factor authentication settings
- Check for expired profiles
- Ensure the user is attached to an active server
DNS Resolution Issues
If clients can’t resolve domain names:
- Check DNS server settings in the server configuration
- Verify that DNS traffic is permitted through the VPN
- Try alternative DNS servers
- Check client DNS configuration
Performance Optimization
If performance is slow:
- Change from TCP to UDP protocol if possible
- Adjust compression settings
- Increase server resources
- Check for bottlenecks in your network infrastructure
Congratulations! You have successfully installed Pritunl VPN. Thanks for using this tutorial for installing the Pritunl VPN Server on your Fedora 42 Linux system. For additional help or useful information, we recommend you check the official Pritunl website.