How To Install Rancher on AlmaLinux 10

Container orchestration has become the backbone of modern infrastructure management. Rancher stands out as one of the most powerful and user-friendly Kubernetes management platforms available today. When combined with AlmaLinux 10’s enterprise-grade stability, this combination creates a robust foundation for managing containerized applications at scale.
This comprehensive guide walks you through the complete installation process of Rancher on AlmaLinux 10. Whether you’re a system administrator looking to streamline cluster management or a DevOps engineer seeking efficient container orchestration, this tutorial provides everything needed for a successful deployment. By following these detailed instructions, you’ll have a fully functional Rancher installation capable of managing multiple Kubernetes clusters through an intuitive web interface.
What Makes Rancher and AlmaLinux 10 the Perfect Combination
Rancher simplifies Kubernetes cluster management through its centralized dashboard, making complex container orchestration accessible to teams of all skill levels. Its multi-cluster management capabilities, integrated monitoring tools, and comprehensive security features have made it a preferred choice for organizations worldwide.
AlmaLinux 10 brings enterprise-level reliability with its Red Hat Enterprise Linux compatibility, ensuring stability and long-term support for production environments. This operating system provides the solid foundation necessary for running mission-critical containerized workloads.
Prerequisites and System Requirements
Hardware Specifications for Optimal Performance
Before beginning the installation process, ensure your system meets the minimum requirements for running Rancher effectively. The hardware specifications directly impact performance and the number of clusters you can manage simultaneously.
Your AlmaLinux 10 server requires at least 2 vCPUs for basic functionality, though 4 vCPUs are recommended for production environments. Memory requirements start at 2 GB RAM minimum, with 4-8 GB recommended depending on your expected workload. Disk space needs begin at 20 GB for the base system and container storage, but allocating 50-100 GB provides better performance and growth capacity.
Network connectivity remains crucial for container image downloads and cluster communication. A persistent internet connection with adequate bandwidth ensures smooth operation during peak usage periods.
Software Prerequisites and Dependencies
A fresh AlmaLinux 10 installation provides the cleanest starting point for Rancher deployment. Ensure you have root access or sudo privileges, as the installation process requires elevated permissions for system modifications and service management.
SSH access becomes essential for remote server management, especially in production environments where direct console access may be limited. Configure SSH key authentication for enhanced security before proceeding with the installation.
Network and Security Configuration Requirements
Rancher requires specific network ports for proper operation. HTTP traffic uses port 80, while HTTPS connections utilize port 443. Docker’s container communication needs various ephemeral ports, typically in the 30000-32767 range for NodePort services.
Firewall configuration must allow these ports while maintaining security best practices. SELinux settings require adjustment to accommodate container operations without compromising system security.
System Preparation and Environment Setup
Updating AlmaLinux 10 Packages
Begin by updating your AlmaLinux 10 system to ensure all packages are current and security patches are applied. This step prevents compatibility issues and provides the latest bug fixes.
sudo dnf update -y
sudo dnf clean all
sudo dnf makecacheThe update process may take several minutes depending on your internet connection and the number of packages requiring updates. Reboot the system after major kernel updates to ensure all changes take effect properly.
Configuring SELinux for Container Operations
SELinux provides additional security layers but requires configuration for container operations. While production environments benefit from maintaining SELinux in enforcing mode, initial installations often work better with permissive mode.
sudo setenforce 0
sudo sed -i 's/^SELINUX=enforcing/SELINUX=permissive/' /etc/selinux/configThis configuration allows containers to operate while maintaining SELinux policies for the base system. Advanced users can configure specific SELinux policies for container operations instead of using permissive mode.
Firewall Configuration for Rancher Services
Configure the firewall to allow necessary traffic while maintaining security. AlmaLinux 10 uses firewalld as the default firewall management tool.
sudo firewall-cmd --permanent --add-port=80/tcp
sudo firewall-cmd --permanent --add-port=443/tcp
sudo firewall-cmd --permanent --add-port=2376/tcp
sudo firewall-cmd --permanent --add-port=2379-2380/tcp
sudo firewall-cmd --reloadThese rules enable HTTP, HTTPS, Docker daemon, and etcd communication ports essential for Rancher operation.
Network Configuration and Hostname Setup
Set an appropriate hostname for your Rancher server to ensure proper identification within your network infrastructure. A descriptive hostname helps with management and troubleshooting.
sudo hostnamectl set-hostname rancher.yourdomain.com
echo "127.0.0.1 rancher.yourdomain.com" | sudo tee -a /etc/hostsVerify DNS resolution works correctly, as Rancher relies on proper name resolution for cluster communication and certificate validation.
Docker Installation and Configuration
Adding the Official Docker Repository
AlmaLinux 10 requires the official Docker CE repository for installation. This ensures you receive the latest stable Docker version with security updates and bug fixes.
sudo dnf config-manager --add-repo https://download.docker.com/linux/centos/docker-ce.repo
sudo dnf makecacheThe repository addition process downloads and verifies the repository metadata, preparing your system for Docker package installation.
Installing Docker Components
Install the complete Docker CE package suite, including the daemon, CLI tools, and containerd runtime. These components work together to provide full container functionality.
sudo dnf install -y docker-ce docker-ce-cli containerd.io docker-compose-pluginThe installation process automatically resolves dependencies and installs required system libraries. If installation fails due to repository issues, download the packages manually from Docker’s official website.
Docker Service Configuration and Optimization
Start and enable the Docker service to ensure automatic startup after system reboots. Proper service configuration prevents service interruptions and maintains container availability.
sudo systemctl start docker
sudo systemctl enable docker
sudo systemctl status dockerAdd your user account to the docker group to avoid requiring sudo for every Docker command. This change requires logging out and back in to take effect.
sudo usermod -aG docker $USER
newgrp dockerDocker System Verification
Verify Docker installation by running the hello-world container. This test confirms proper installation and network connectivity for image downloads.
docker run hello-worldSuccessful execution indicates Docker is properly installed and configured for container operations.
Advanced Docker Configuration for Rancher
Optimize Docker settings for Rancher workloads by configuring the daemon with appropriate logging and storage drivers. Create the Docker daemon configuration file:
sudo mkdir -p /etc/docker
cat <<EOF | sudo tee /etc/docker/daemon.json
{
"log-driver": "json-file",
"log-opts": {
"max-size": "10m",
"max-file": "3"
},
"storage-driver": "overlay2"
}
EOFRestart Docker to apply the new configuration settings:
sudo systemctl restart dockerRancher Container Deployment
Downloading the Rancher Server Image
Pull the latest Rancher server image from Docker Hub. The stable release provides the most reliable experience for production deployments.
docker pull rancher/rancher:latestFor production environments, consider using a specific version tag instead of “latest” to maintain consistency across deployments and enable easier rollbacks if needed.
Container Launch with Complete Configuration
Deploy the Rancher container with the full command including all necessary options for production use:
docker run -d --restart=unless-stopped \
--name rancher-server \
-p 80:80 -p 443:443 \
--privileged \
rancher/rancher:latestThis command creates a detached container that automatically restarts unless manually stopped. The port mappings expose Rancher’s web interface on standard HTTP and HTTPS ports.
Understanding Container Configuration Options
The --privileged flag grants the container access to host system resources necessary for managing other containers and clusters. While this increases security considerations, it’s required for full Rancher functionality.
The --restart=unless-stopped policy ensures the Rancher container automatically restarts after system reboots or unexpected crashes, maintaining service availability.
Advanced Container Deployment Options
For enhanced data persistence and backup capabilities, mount external volumes for Rancher data:
docker run -d --restart=unless-stopped \
--name rancher-server \
-p 80:80 -p 443:443 \
--privileged \
-v /opt/rancher:/var/lib/rancher \
rancher/rancher:latestThis configuration stores Rancher data in /opt/rancher on the host system, enabling easier backups and data recovery.
Container Health Verification and Monitoring
Monitor the Rancher container startup process by checking logs and container status:
docker ps
docker logs rancher-serverThe startup process typically takes 2-3 minutes as Rancher initializes its internal database and prepares the web interface. Watch the logs for any error messages that might indicate configuration problems.
SSL Certificate Configuration and Security
Default SSL Certificate Behavior
Rancher automatically generates self-signed SSL certificates for immediate functionality. While suitable for testing environments, production deployments should use trusted certificates from recognized certificate authorities.
The self-signed certificate causes browser security warnings that users must accept to access the interface. This behavior is normal and expected during initial setup.
Custom SSL Certificate Integration
For production environments, integrate custom SSL certificates by mounting certificate files into the container:
docker run -d --restart=unless-stopped \
--name rancher-server \
-p 80:80 -p 443:443 \
--privileged \
-v /opt/rancher/certs/tls.crt:/etc/rancher/ssl/cert.pem \
-v /opt/rancher/certs/tls.key:/etc/rancher/ssl/key.pem \
-v /opt/rancher/certs/cacerts.pem:/etc/rancher/ssl/cacerts.pem \
rancher/rancher:latestEnsure certificate files have proper permissions and are readable by the container user.
Initial Access and Configuration
Accessing the Rancher Web Interface
Open your web browser and navigate to your server’s IP address or hostname using HTTPS. The initial connection may display security warnings due to self-signed certificates.
https://your-server-ipAccept the security warning to proceed to the Rancher login page. Modern browsers require explicit acceptance of self-signed certificates.
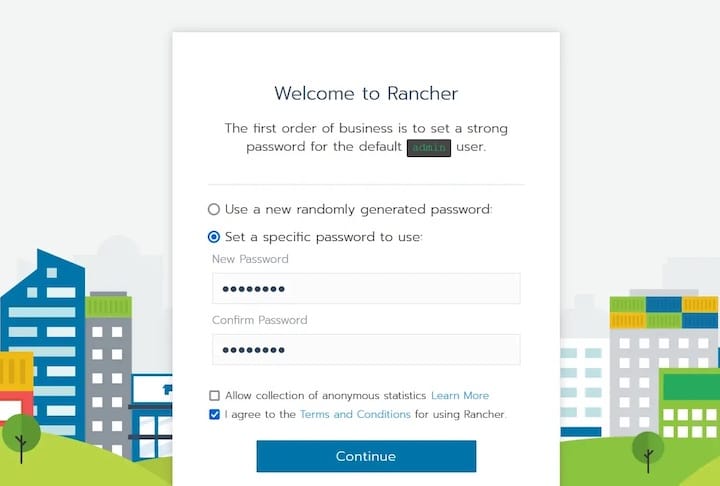
First-Time Setup and Administrator Account
The initial setup wizard guides you through creating the administrator account and configuring basic settings. Choose a strong password meeting complexity requirements for enhanced security.
Set the Rancher Server URL to match your server’s hostname or IP address. This URL is used by managed clusters to communicate with the Rancher server, so ensure it’s accessible from all nodes.
Authentication Provider Configuration
Configure authentication providers based on your organization’s requirements. Local authentication works for small deployments, while larger organizations benefit from LDAP, Active Directory, or OAuth integration.
The authentication setup determines how users access Rancher and what permissions they receive. Plan your authentication strategy before configuring multiple clusters.
Initial Project and Namespace Setup
Rancher creates default projects and namespaces during initial setup. Understanding these organizational structures helps with resource management and access control as your deployment grows.
Projects provide logical groupings for related applications and services, while namespaces offer finer-grained resource isolation within projects.
Post-Installation Optimization and Management
System Monitoring and Health Checks
Implement monitoring for both the Rancher container and the underlying AlmaLinux 10 system. Regular health checks prevent issues before they impact service availability.
Monitor container resource usage with:
docker stats rancher-serverSet up log rotation to prevent log files from consuming excessive disk space:
sudo logrotate -f /etc/logrotate.confBackup and Recovery Procedures
Establish regular backup procedures for Rancher data and configuration. The mounted data directory contains all cluster definitions, user settings, and application configurations.
Create automated backups using cron jobs:
#!/bin/bash
BACKUP_DIR="/backups/rancher/$(date +%Y%m%d-%H%M%S)"
mkdir -p $BACKUP_DIR
cp -r /opt/rancher $BACKUP_DIR/
docker exec rancher-server kubectl get all --all-namespaces > $BACKUP_DIR/cluster-state.yamlTest backup restoration procedures regularly to ensure data recovery works when needed.
Performance Tuning and Optimization
Optimize system performance by adjusting kernel parameters for container workloads:
echo 'net.bridge.bridge-nf-call-iptables=1' | sudo tee -a /etc/sysctl.conf
echo 'net.ipv4.ip_forward=1' | sudo tee -a /etc/sysctl.conf
sudo sysctl -pThese settings improve network performance for containerized applications and cluster communication.
Troubleshooting Common Issues
Installation and Startup Problems
Docker service failures often result from insufficient system resources or conflicting services. Check system logs for detailed error messages:
sudo journalctl -u docker.service -fContainer image download failures typically indicate network connectivity issues or repository access problems. Verify internet connectivity and DNS resolution:
nslookup docker.io
ping -c 4 8.8.8.8Access and Authentication Issues
Web interface connectivity problems often stem from firewall configuration or SSL certificate issues. Verify port accessibility:
sudo netstat -tlnp | grep :443
curl -k https://localhostAuthentication provider integration failures require checking provider-specific logs and network connectivity to authentication servers.
Performance and Resource Issues
High memory usage may indicate insufficient system resources or memory leaks. Monitor container resource consumption and adjust limits if necessary:
docker update --memory=4g rancher-serverContainer restart loops usually indicate configuration errors or resource constraints. Check container logs for specific error messages and system resource availability.
SELinux and Security Context Problems
SELinux denials appear in audit logs and can prevent proper container operation. Check for denials:
sudo ausearch -m avc -ts recentGenerate custom SELinux policies for persistent issues, or adjust file contexts for mounted volumes:
sudo chcon -Rt container_file_t /opt/rancherSecurity Best Practices and Hardening
Container Security Implementation
Run containers with minimal privileges when possible, though Rancher requires privileged access for full functionality. Regularly scan container images for vulnerabilities:
docker scan rancher/rancher:latestKeep container images updated with the latest security patches by regularly pulling new versions and redeploying containers.
Network Security and Access Control
Implement network segmentation using firewall rules and VLANs to isolate cluster traffic from general network traffic. Configure VPN access for remote administration to encrypt management communications.
Use strong firewall rules that allow only necessary traffic:
sudo firewall-cmd --permanent --add-rich-rule="rule family='ipv4' source address='192.168.1.0/24' port protocol='tcp' port='443' accept"
sudo firewall-cmd --reloadAuthentication and Authorization Controls
Implement multi-factor authentication for administrator accounts and enforce strong password policies. Configure role-based access control (RBAC) to limit user permissions based on job responsibilities.
Regular audit user access and remove unused accounts to maintain security hygiene.
Monitoring and Audit Logging
Enable comprehensive logging for security monitoring and compliance requirements. Configure log forwarding to centralized logging systems for better visibility:
docker run -d --restart=unless-stopped \
--name rancher-server \
-p 80:80 -p 443:443 \
--privileged \
-e AUDIT_LEVEL=2 \
rancher/rancher:latestSet up automated alerts for security events and unusual access patterns.
Advanced Configuration and Next Steps
High Availability and Scaling
Migrate from single-node deployments to high-availability configurations as your infrastructure grows. HA setups require load balancers and shared storage for optimal reliability.
Plan for multi-region deployments if geographic distribution becomes necessary for performance or compliance requirements.
CI/CD Pipeline Integration
Integrate Rancher with continuous integration and deployment pipelines for automated application deployment. GitOps workflows provide declarative infrastructure management and improved change tracking.
Configure container registries for storing private application images and implementing image scanning policies.
Advanced Rancher Features
Explore Rancher’s advanced features like Fleet for GitOps management, integrated monitoring with Prometheus and Grafana, and policy enforcement with OPA Gatekeeper.
These features provide enterprise-grade capabilities for managing large-scale container deployments across multiple clusters and environments.
Congratulations! You have successfully installed Rancher. Thanks for using this tutorial for installing Rancher on your AlmaLinux OS 10 system. For additional help or useful information, we recommend you check the official Rancher website.