How To Install Rancher on Linux Mint 22

Rancher stands as a powerful open-source container management platform designed to simplify Kubernetes cluster deployment and orchestration across diverse computing environments. This comprehensive guide walks through the complete installation process of Rancher on Linux Mint 22, providing step-by-step instructions that enable system administrators and DevOps professionals to establish a robust container management infrastructure.
Linux Mint 22, built upon the solid foundation of Ubuntu 24.04 LTS, offers excellent compatibility with Rancher’s requirements and provides a stable environment for container orchestration workloads. The installation method covered in this tutorial utilizes Docker-based deployment, which offers simplicity and rapid setup for development, testing, and learning environments. Whether managing multiple Kubernetes clusters, deploying containerized applications, or seeking centralized control over container infrastructure, Rancher delivers the tools needed for efficient cloud-native operations.
Understanding Rancher
What is Rancher?
Rancher represents a complete software stack for teams adopting containers and Kubernetes for application delivery. It addresses the operational and security challenges of managing multiple Kubernetes clusters across any infrastructure. The platform eliminates the complexity traditionally associated with Kubernetes deployment by providing intuitive interfaces and automation capabilities that streamline cluster creation, management, and monitoring.
Container orchestration becomes significantly more manageable with Rancher’s unified control plane. Organizations can deploy clusters on bare metal servers, public cloud platforms, private data centers, or hybrid environments without dealing with infrastructure-specific complexities. This flexibility makes Rancher an ideal solution for enterprises standardizing their container management approach across heterogeneous computing resources.
Key Features and Benefits
Rancher’s multi-cluster management capability enables administrators to control numerous Kubernetes clusters from a single dashboard interface. This centralized approach dramatically reduces operational overhead while maintaining granular control over individual cluster configurations. The built-in web-based UI simplifies tasks that would otherwise require extensive kubectl command knowledge and complex YAML file manipulation.
Security features include comprehensive role-based access control (RBAC) systems, policy enforcement mechanisms, and integrated security scanning tools. Authentication can be configured through multiple providers including Active Directory, LDAP, GitHub, and SAML, ensuring seamless integration with existing enterprise identity management systems. The platform also supports deployment across major cloud providers such as Google Kubernetes Engine (GKE), Amazon Elastic Kubernetes Service (EKS), and Azure Kubernetes Service (AKS), while maintaining consistent management experiences regardless of underlying infrastructure.
Prerequisites and System Requirements
Hardware Requirements
Proper hardware allocation ensures optimal Rancher performance and stability. A minimum configuration requires 2 CPU cores and 4 GB of RAM for basic server functionality, though this specification suits only light testing scenarios. Production-grade deployments or environments managing multiple clusters should provision at least 4 CPU cores and 8 GB of RAM to handle increased workload demands.
Storage considerations prove equally important for long-term operations. Allocate a minimum of 60 GB disk space to accommodate Docker images, container data, application logs, and backup files. The x86_64 processor architecture with hardware virtualization support (AMD-V or Intel VT-x) is mandatory, as these extensions enable efficient container isolation and resource management.
Software Requirements
Linux Mint 22 serves as the base operating system, leveraging its Ubuntu 24.04 LTS foundation for package compatibility and long-term support. Administrative privileges are essential throughout the installation process, requiring either sudo access or direct root user capabilities. Network connectivity must remain stable during installation to download Docker packages, container images, and necessary dependencies from official repositories.
System packages should be updated to their latest versions before proceeding with Rancher installation. This practice prevents compatibility issues and ensures security patches are applied. A modern web browser is required for accessing the Rancher WebUI after deployment, with Chrome, Firefox, or Edge recommended for best compatibility.
Network Requirements
Port availability is critical for Rancher functionality. HTTP traffic requires port 80, while HTTPS communications need port 443 accessible for secure web interface access. The Kubernetes API server communicates through port 6443, which must be open for proper cluster management operations.
Firewall configurations should permit container networking without blocking essential traffic flows. Network Time Protocol (NTP) synchronization ensures accurate time across the system, preventing certificate validation failures that occur when system clocks drift. For production environments, configuring a static IP address or establishing proper DNS resolution enhances accessibility and reliability.
Step 1: Update Linux Mint 22 System
System updates form the foundation of a stable installation environment. Outdated packages can introduce compatibility problems or security vulnerabilities that compromise Rancher functionality. Begin by refreshing the package repository index to ensure access to the latest software versions available in configured repositories.
Execute the update command to synchronize package information:
sudo apt updateThis command contacts configured repository servers and downloads current package metadata. Following the repository refresh, upgrade installed packages to their newest versions:
sudo apt upgrade -yThe -y flag automatically confirms upgrade prompts, streamlining the process. Monitor the output for any errors or warnings that might indicate repository issues or dependency conflicts.
If kernel updates are installed during the upgrade process, reboot the system to activate the new kernel version. This step ensures all system components operate with the latest security patches and feature improvements. A simple reboot command accomplishes this:
sudo rebootStep 2: Install Docker on Linux Mint 22
Remove Old Docker Versions
Existing Docker installations can conflict with fresh deployments, causing unpredictable behavior or installation failures. Removing previous versions creates a clean slate for the new installation. Legacy Docker packages were distributed under different names across various Linux distribution versions, necessitating removal of multiple package variations.
Execute the removal command to purge old Docker installations:
sudo apt remove -y docker docker-engine docker.io containerd runcThis command targets common legacy Docker package names. The system may report that some packages are not installed, which is normal and indicates no action was needed for those specific components.
Install Docker Dependencies
Docker requires several system libraries and utilities to function properly. These dependencies handle secure package transmission, certificate management, and cryptographic operations. Install the required packages using the following command:
sudo apt install -y apt-transport-https ca-certificates curl gnupgThe apt-transport-https package enables the APT package manager to retrieve packages over HTTPS connections. The ca-certificates package provides trusted certificate authorities for SSL/TLS verification, while curl facilitates file downloads from web sources. The gnupg package manages cryptographic keys used to verify package authenticity.
Import Docker GPG Key
Docker signs its packages with cryptographic keys to ensure integrity and authenticity. Importing the official Docker GPG key allows the package manager to verify that downloaded packages haven’t been tampered with. Create the keyrings directory with appropriate permissions:
sudo install -m 0755 -d /etc/apt/keyringsDownload the Docker repository GPG key:
sudo curl -fsSL https://download.docker.com/linux/ubuntu/gpg -o /etc/apt/keyrings/docker.ascSet proper permissions on the key file:
sudo chmod a+r /etc/apt/keyrings/docker.ascAdd Docker APT Repository
The official Docker repository provides the latest Docker Engine releases optimized for Ubuntu-based distributions. Adding this repository ensures access to current versions and security updates. Configure the repository using the following command:
echo "deb [arch=$(dpkg --print-architecture) signed-by=/etc/apt/keyrings/docker.asc] https://download.docker.com/linux/ubuntu $(. /etc/os-release && echo "$UBUNTU_CODENAME") stable" | sudo tee /etc/apt/sources.list.d/docker.list > /dev/nullThis command dynamically determines the system architecture and Ubuntu codename, ensuring correct repository configuration. Update the package index to incorporate the newly added repository:
sudo apt updateInstall Docker Engine
With repositories configured and GPG keys imported, Docker Engine installation proceeds smoothly. The Docker package bundle includes the core engine, command-line interface, container runtime, and additional plugins. Install Docker with the comprehensive package set:
sudo apt install -y docker-ce docker-ce-cli containerd.io docker-buildx-plugin docker-compose-pluginThis installation includes Docker Community Edition (docker-ce), the Docker CLI client (docker-ce-cli), the containerd runtime, BuildKit plugin for advanced image building, and Docker Compose for multi-container applications. Verify the installation by checking the Docker version:
docker --versionExpected output displays version information confirming successful installation.
Configure Docker Service
The Docker daemon must run continuously to manage container lifecycles. Enabling the service ensures Docker starts automatically at system boot, maintaining container availability across reboots. Start the Docker service immediately:
sudo systemctl start dockerEnable automatic startup at boot time:
sudo systemctl enable dockerVerify the service is active and running:
sudo systemctl status dockerThe status output should display “active (running)” in green text, indicating the Docker daemon is operational.
Add User to Docker Group
By default, Docker commands require root privileges for execution. Adding the current user to the docker group eliminates the need for sudo prefixes on every command, improving workflow efficiency. Execute the user modification command:
sudo usermod -aG docker $USERActivate the group membership without logging out:
newgrp dockerTest non-privileged access by running a simple Docker command:
docker psThis should execute without permission errors. Note that docker group membership grants significant system access, as containers can be configured to access host resources.
Step 3: Deploy Rancher Container
Pull and Run Rancher Docker Image
Rancher deployment utilizes a single Docker container that encapsulates the entire management platform. The container runs a local Kubernetes cluster internally to support Rancher’s functionality, requiring privileged mode for nested container operations. Execute the Rancher deployment command:
docker run -d --restart=unless-stopped -p 80:80 -p 443:443 --privileged rancher/rancher:latestBreaking down the command parameters reveals the configuration choices:
- The -d flag runs the container in detached mode, allowing it to operate in the background
- The –restart=unless-stopped policy ensures automatic container restart after system reboots or unexpected failures
- Port mappings -p 80:80 -p 443:443 expose HTTP and HTTPS services for web interface access
- The –privileged flag grants extended container capabilities necessary for running Kubernetes components inside the container
- The rancher/rancher:latest image specification pulls the most recent stable Rancher release
Docker downloads the Rancher image layers if not already present locally. Image size typically ranges from 1-2 GB, requiring several minutes to download depending on connection speed.
Verify Container Deployment
Confirming successful container deployment prevents troubleshooting delays later in the process. List running containers to verify Rancher is active:
docker psThe output displays container details including container ID, image name, creation time, status, and port mappings. Look for a container running the rancher/rancher image with “Up” status.
Examine container logs to monitor the initialization process:
docker logs rancher-serverReplace rancher-server with the actual container name or ID from the previous command output. Log entries show the bootstrap sequence, internal Kubernetes cluster creation, and service startup progress.
Initial Bootstrap Process
Rancher performs extensive initialization during first startup, installing and configuring a local Kubernetes cluster within the container. This bootstrap process typically requires 2-3 minutes on systems meeting minimum specifications. Higher-specification systems complete initialization faster, while resource-constrained environments may take longer.
Monitor log output for completion indicators. Look for entries mentioning “Bootstrap Password” and messages indicating services are ready. Avoid attempting web interface access before bootstrap completes, as connections will fail or display error pages.
Resource consumption peaks during initial deployment as Kubernetes components initialize. CPU usage may reach 100% temporarily, while memory consumption rises to 2-3 GB before stabilizing. This behavior is normal and subsides once initialization completes.
Step 4: Access Rancher Web Interface
Retrieve Initial Admin Password
Rancher generates a random bootstrap password during first startup to secure the initial administrative account. This password appears in container logs and must be retrieved before accessing the web interface. Extract the bootstrap password using the following command:
docker logs container-id 2>&1 | grep "Bootstrap Password:"Replace container-id with your actual container identifier obtained from docker ps. The output displays a line containing the bootstrap password string, typically a long alphanumeric sequence.
Alternative retrieval method using container name:
docker logs rancher-server 2>&1 | grep "Bootstrap Password:"Copy the password string carefully, as it’s case-sensitive and contains no spaces. Some terminal emulators allow text selection and copying with mouse operations, simplifying this step.
Login to Rancher WebUI
Open a web browser and navigate to the Rancher server using HTTPS protocol. Replace the placeholder with your actual server IP address:
https://your-server-ipFor local installations, use https://localhost or https://127.0.0.1. The browser displays a security warning about the self-signed SSL certificate, which is expected behavior for default Rancher installations.
Modern browsers present different warning screens:
- Chrome shows “Your connection is not private” with an “Advanced” button
- Firefox displays “Warning: Potential Security Risk Ahead” with details option
- Edge presents “Your connection isn’t private” with advanced information
Proceed past the warning by clicking “Advanced” or equivalent, then selecting “Proceed to [address]” or “Accept the Risk and Continue”. This action is safe for internal deployments using self-signed certificates.
Complete Initial Configuration
The Rancher welcome screen prompts for the bootstrap password retrieved from container logs. Enter the password in the provided field and click “Continue” or “Log In With Local User”. After successful authentication, Rancher presents the initial setup wizard.
The first configuration screen requires setting a new permanent administrator password. Choose a strong password meeting these requirements:
- Minimum length of 12 characters
- Combination of uppercase and lowercase letters
- Include numbers and special characters
- Avoid common dictionary words or patterns
The next step configures the Rancher server URL, which determines how cluster nodes communicate with the management server. For local installations, the default value suffices. For network-accessible deployments, enter the server’s hostname or IP address.
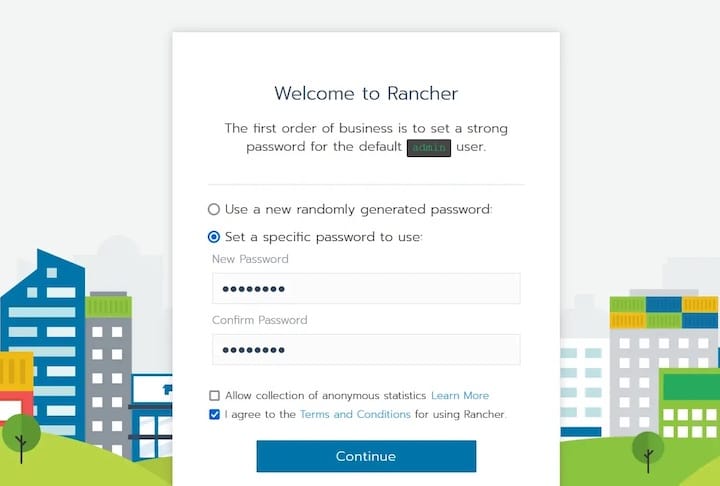
Rancher requests permission to collect anonymous usage data for product improvement. This telemetry setting can be enabled or disabled based on organizational policies. Complete the setup wizard to access the main Rancher dashboard.
Step 5: Configure Firewall Rules
Firewall configuration ensures Rancher services remain accessible while maintaining system security. Linux Mint typically uses UFW (Uncomplicated Firewall) for packet filtering management. Check current firewall status:
sudo ufw statusIf the firewall is inactive, enabling it provides security benefits but requires careful rule configuration to avoid blocking essential services. Allow HTTP traffic on port 80:
sudo ufw allow 80/tcpAllow HTTPS traffic on port 443:
sudo ufw allow 443/tcpAllow Kubernetes API server communication on port 6443:
sudo ufw allow 6443/tcpThese rules permit inbound connections to Rancher’s web interface and API endpoints. If SSH access is required, ensure port 22 is also allowed before enabling the firewall:
sudo ufw allow 22/tcpEnable the firewall with configured rules:
sudo ufw enableVerify rules are active:
sudo ufw status verboseKubernetes networking can conflict with certain firewall configurations, particularly when using firewalld instead of UFW. Some installations require firewall zones configured for Pod CIDR ranges to prevent packet filtering interference. For development environments, temporarily disabling the firewall can isolate networking issues, though this approach shouldn’t be used in production.
Post-Installation Configuration
Exploring the Rancher Dashboard
The Rancher dashboard provides centralized access to cluster management, monitoring, and configuration tools. The main navigation menu appears on the left side, organizing functions into logical categories. The “Cluster Management” section displays all registered clusters, their health status, Kubernetes versions, and node counts.
Global settings control platform-wide configurations affecting all clusters. These settings include authentication providers, server URL configuration, telemetry options, and feature flags for experimental capabilities. The user interface adjusts dynamically based on selected context, showing cluster-specific options when a particular cluster is active.
Resource monitoring displays real-time metrics for CPU, memory, and storage utilization across managed clusters. These visualizations help identify performance bottlenecks and capacity planning needs. The catalog section provides pre-configured application templates for common workloads, accelerating deployment of databases, web servers, and other services.
Configuring Admin Settings
Authentication configuration determines how users access the Rancher platform. Navigate to “Users & Authentication” in the global settings to configure providers. Local authentication maintains user accounts within Rancher’s database, suitable for small teams or testing environments.
Enterprise deployments typically integrate with existing directory services. Active Directory and LDAP options allow centralized user management, while GitHub and SAML providers enable federated authentication. Each provider requires specific configuration parameters like server addresses, bind credentials, and search base DNs.
SSL/TLS certificate settings allow replacement of the default self-signed certificate with organization-issued or commercial certificates. Proper certificates eliminate browser warnings and enable secure external access. Upload custom certificates through the “Settings” section under “General” options.
Security Best Practices
Implementing robust password policies strengthens account security across all user levels. Rancher enforces minimum password length of 12 characters by default, though this can be adjusted between 2 and 256 characters based on organizational requirements. Regular password rotation policies should be established, requiring users to update credentials quarterly.
Two-factor authentication adds an additional security layer, requiring both password knowledge and physical device possession for access. While native 2FA support varies by Rancher version, integration with SAML or OIDC providers offers multi-factor capabilities.
Audit logging captures all API transactions, user actions, and system events for security monitoring and compliance purposes. Enable audit logging through advanced settings and configure log rotation to manage storage consumption. Review logs regularly for suspicious activities like unauthorized access attempts, unusual cluster modifications, or privilege escalation.
Network access restriction limits Rancher exposure to authorized IP ranges. Implement firewall rules or cloud security groups that permit connections only from known administrator networks or VPN endpoints. This defense-in-depth approach reduces attack surface even if authentication mechanisms are compromised.
Creating Your First Kubernetes Cluster
Cluster Creation Options
Rancher supports multiple cluster deployment methods accommodating diverse infrastructure scenarios. Custom cluster creation provisions Kubernetes on existing infrastructure by registering physical servers, virtual machines, or cloud instances as cluster nodes. This approach provides maximum flexibility, supporting bare metal, VMware, or any compute platform running supported operating systems.
Infrastructure provider integration enables Rancher to automatically provision nodes on cloud platforms including Amazon Web Services, Microsoft Azure, Google Cloud Platform, and DigitalOcean. Template-based provisioning streamlines cluster creation, automatically configuring networking, storage, and compute resources according to specified parameters.
Hosted Kubernetes providers like GKE, EKS, and AKS can be managed through Rancher’s unified interface. This option leverages cloud-native Kubernetes services while gaining Rancher’s enhanced management, monitoring, and security capabilities.
Existing cluster import brings pre-deployed Kubernetes clusters under Rancher management without reinstallation. This non-invasive approach suits environments with established clusters requiring improved management tools.
Creating a Custom Cluster
Navigate to the “Cluster Management” section and click “Create” to begin cluster provisioning. Select “Custom” as the cluster type for manual node registration. Specify cluster name, Kubernetes version, and network provider options. Common network plugins include Calico, Flannel, and Weave, each offering different features and performance characteristics.
Advanced cluster options configure control plane redundancy, etcd snapshot schedules, and cluster-specific authentication. Default settings suit most deployments, though production environments benefit from reviewing all options.
After configuring cluster parameters, Rancher generates a node registration command containing cluster-specific tokens. Copy this command and execute it on each machine that should join the cluster. The registration command installs the Rancher agent, which establishes communication with the management server and provisions Kubernetes components.
Monitor cluster provisioning progress through the dashboard. Node status transitions from “Registering” to “Provisioning” to “Active” as setup completes. Full cluster initialization typically requires 5-10 minutes depending on node count and network performance.
Importing Existing Clusters
Select “Import Existing” from the cluster creation menu to add pre-deployed Kubernetes clusters. Provide a descriptive cluster name that identifies the environment being imported. Rancher generates a kubectl command that deploys the import agent into the target cluster.
Execute the provided command on the existing cluster using administrative credentials:
kubectl apply -f https://rancher-server/v3/import/cluster-token.yamlThe import agent establishes secure communication with the Rancher server, registering cluster resources for management. Import completion typically occurs within 2-3 minutes, after which the cluster appears in the Rancher dashboard with full monitoring and management capabilities.
Imported clusters retain their existing configurations, workloads, and networking settings. Rancher adds management overlays without disrupting running applications. Access to cluster features depends on Rancher’s ability to communicate with the Kubernetes API server, so ensure network connectivity and firewall rules permit this traffic.
Common Troubleshooting Issues
Container Won’t Start
Container startup failures typically stem from port conflicts, permission problems, or insufficient resources. Verify Docker daemon is running correctly:
sudo systemctl status dockerIf Docker is inactive, start the service and check system logs for error messages. Port conflicts occur when other services occupy ports 80 or 443. Identify port usage:
sudo lsof -i :80
sudo lsof -i :443Stop conflicting services or modify Rancher port mappings to use alternative ports. Insufficient system resources prevent container initialization. Monitor system resource availability:
free -h
df -hEnsure adequate RAM and disk space meet minimum requirements. Permission issues with the Docker socket prevent container management operations. Verify the current user has docker group membership:
groups $USERReapply group membership if necessary using commands from the Docker installation section.
Cannot Access WebUI
Web interface accessibility problems often relate to firewall restrictions or SSL certificate handling. Verify the Rancher container is running and listening on expected ports:
docker ps
netstat -tlnp | grep -E '(80|443)'Firewall rules must permit inbound traffic on ports 80 and 443. Review and adjust UFW rules as described in the firewall configuration section. Browser SSL warnings for self-signed certificates are expected but can prevent access if not properly acknowledged.
Some browsers cache certificate decisions, requiring cache clearing or private browsing mode for fresh connection attempts. Network connectivity between client and server can be tested using curl:
curl -k https://rancher-server-ipThe -k flag bypasses SSL verification for testing purposes. Successful responses indicate network connectivity, while timeouts or connection refused errors point to network or firewall issues.
Internal nginx or ingress controller failures within the Rancher container prevent request handling. Examine container logs for error messages:
docker logs rancher-server | tail -50Look for panic messages, certificate errors, or port binding failures.
Kubernetes API Connection Errors
Kubernetes API connectivity issues prevent cluster management operations and node registration. Port 6443 must be accessible for API server communication. Verify firewall rules allow this traffic:
sudo ufw status | grep 6443Certificate validation errors commonly occur when system time is incorrect. Time synchronization via NTP ensures certificate validity periods are properly evaluated. Check system time accuracy:
timedatectl statusEnable NTP synchronization if disabled:
sudo timedatectl set-ntp trueRancher v2.6 and later have specific compatibility requirements with certain Ubuntu kernel versions. Some Ubuntu 22.04 installations experience connection issues resolved by kernel updates. Check for available kernel updates:
sudo apt update
sudo apt upgrade linux-image-genericLocal Kubernetes cluster bootstrap failures within the Rancher container prevent full functionality. These failures typically appear in container logs as repeated restart attempts or component crash messages. Insufficient container resources cause bootstrap failures. Increase Docker memory limits or allocate more system RAM.
Maintenance and Updates
Updating Rancher
Rancher updates deliver new features, security patches, and bug fixes requiring periodic application. Check the current version in the web interface footer or through the API. Before upgrading, create comprehensive backups of Rancher data to enable rollback if problems occur.
Pull the latest Rancher image from Docker Hub:
docker pull rancher/rancher:latestFor specific version targeting, replace latest with the desired version tag. Stop the running Rancher container:
docker stop rancher-serverRemove the stopped container while preserving data volumes:
docker rm rancher-serverLaunch a new container with the updated image using identical run parameters from the initial deployment:
docker run -d --restart=unless-stopped -p 80:80 -p 443:443 --privileged rancher/rancher:latestRancher automatically migrates database schemas and applies configuration updates during first startup after upgrade. Monitor container logs during this process to identify any migration issues.
Backup and Restore
Regular backup schedules protect against data loss from hardware failures, configuration errors, or security incidents. Rancher’s backup operator provides automated backup capabilities for Kubernetes-based deployments. For Docker installations, backup procedures focus on container volumes and etcd data.
Create container volume backups by stopping the Rancher container and archiving the data directory:
docker stop rancher-server
sudo tar -czvf rancher-backup-$(date +%Y%m%d).tar.gz /var/lib/rancher
docker start rancher-serverStore backup archives on separate systems or cloud storage to enable disaster recovery when primary infrastructure fails. Test backup restoration procedures regularly to verify backup integrity and restoration time objectives.
Etcd backups capture cluster state information critical for cluster recovery. Rancher automatically configures etcd snapshots for managed clusters according to retention policies. Access and download etcd snapshots through the cluster management interface under backup settings.
Performance Optimization Tips
Optimal Rancher performance requires balancing resource allocation, workload demands, and infrastructure capabilities. System resource monitoring identifies bottlenecks limiting platform performance. The Rancher dashboard displays real-time metrics for CPU, memory, and storage utilization.
Docker daemon optimization improves container lifecycle operations and image management efficiency. Configure Docker with appropriate storage drivers for the underlying filesystem. Overlay2 provides good performance on most modern Linux systems.
Database performance directly impacts Rancher responsiveness, particularly for environments managing many clusters. Etcd tuning parameters adjust snapshot intervals, compaction schedules, and quota limits. Default settings suit most deployments, though large-scale installations benefit from customization.
Network performance tuning addresses container networking overhead and inter-cluster communication latency. Select network plugins matching workload characteristics – Calico excels in security policy scenarios, while Flannel offers simplicity for basic networking needs.
Regular cleanup operations prevent resource exhaustion from accumulated container images and stopped containers. Remove unused images:
docker system prune -aResource quotas and limits prevent individual workloads from consuming disproportionate cluster resources. Define default limits in cluster settings and override per namespace as needed.
Load balancing distributes traffic across multiple Rancher instances in high-availability configurations. While single-container deployments don’t require load balancing, production environments should implement HA configurations with external load balancers.
Congratulations! You have successfully installed Rancher. Thanks for using this tutorial for installing Rancher container management on Linux Mint 22 system. For additional help or useful information, we recommend you check the official Rancher website.