How To Install Redmine on Fedora 42

Redmine stands as one of the most powerful open-source project management tools available today, offering comprehensive issue tracking, project planning, and collaboration features. Installing Redmine on Fedora 42 provides organizations with a robust, scalable platform for managing complex projects while maintaining complete control over their data and infrastructure.
This comprehensive guide walks through every step of the Redmine installation process on Fedora 42, from initial system preparation to advanced configuration and security hardening. Whether you’re a system administrator setting up enterprise project management infrastructure or a developer creating a team collaboration environment, this tutorial provides the detailed instructions and troubleshooting guidance needed for a successful deployment.
System Requirements and Prerequisites
Hardware Requirements
Before beginning the installation process, ensure your Fedora 42 system meets the minimum hardware specifications for running Redmine effectively. The minimum requirements include 1 GB of RAM and a single CPU core, though these specifications are suitable only for small teams or development environments.
For production deployments serving multiple concurrent users, allocate at least 2 GB of RAM and 2 CPU cores to ensure optimal performance. Storage requirements vary based on expected usage, but plan for a minimum of 5 GB of free disk space to accommodate the application, database, and file attachments. Network connectivity is essential for web access, and consider bandwidth requirements based on your expected user base and file sharing needs.
Software Dependencies
Fedora 42 provides an excellent foundation for Redmine deployment, offering modern package management and robust security features. The installation requires Ruby version 2.5 or higher, with Ruby 3.1, 3.2, or 3.3 providing optimal compatibility with current Redmine releases.
Database selection significantly impacts performance and scalability. Redmine supports PostgreSQL, MySQL/MariaDB, and SQLite, with PostgreSQL recommended for production environments due to its advanced features and performance characteristics. Web server options include Apache HTTP Server and Nginx, both offering excellent performance when properly configured.
User Permissions and Security
Proper user management forms the foundation of a secure Redmine installation. Root or sudo access is required for system-level package installation and service configuration. Creating a dedicated system user for running Redmine enhances security by isolating the application from system-critical processes.
Firewall configuration requires careful attention to security while ensuring necessary services remain accessible. SELinux settings on Fedora 42 may require adjustment to accommodate Ruby applications, though maintaining security context integrity remains paramount for production deployments.
Preparing the Fedora 42 Environment
System Updates and Package Management
Begin by ensuring your Fedora 42 system contains the latest packages and security updates. Execute the following command to refresh the package database and install available updates:
sudo dnf update -yThis command synchronizes package repositories and applies all pending updates, establishing a stable foundation for Redmine installation. The process may require several minutes depending on the number of available updates and your internet connection speed.
Configure the system locale and timezone to match your organizational requirements:
sudo localectl set-locale LANG=en_US.UTF-8
sudo timedatectl set-timezone America/New_YorkVerify system architecture compatibility by checking that your Fedora 42 installation supports the required 64-bit packages:
uname -mInstalling Core Dependencies
Install the comprehensive set of development tools and libraries required for Ruby application compilation and execution:
sudo dnf groupinstall "Development Tools" "C Development Tools and Libraries" -y
sudo dnf install gcc make ruby ruby-devel rubygems bundler git ImageMagick ImageMagick-devel zlib-devel curl-devel openssl-devel -yThese packages provide the compilation environment necessary for building native Ruby gems and handling image processing tasks. ImageMagick enables Redmine to generate thumbnails and manipulate uploaded images, while the development libraries support various Ruby gems that may require native compilation.
Verify Ruby installation and version compatibility:
ruby --version
gem --version
bundler --versionEnsure the displayed Ruby version meets Redmine’s minimum requirements of 2.5 or higher for optimal compatibility.
Database Setup and Configuration
Choosing the Right Database
Database selection impacts both performance and administrative complexity. PostgreSQL offers advanced features, excellent performance, and robust transaction handling, making it ideal for production environments. MySQL/MariaDB provides widespread compatibility and familiar administration tools, while SQLite suits development and small-team deployments.
For production environments handling multiple projects and users, PostgreSQL delivers superior performance and supports advanced querying capabilities that enhance Redmine’s reporting features. The choice between MySQL/MariaDB and PostgreSQL often depends on existing infrastructure and administrative expertise.
PostgreSQL Installation and Setup
Install PostgreSQL 17 and related development packages on Fedora 42:
sudo dnf install postgresql-server postgresql-devel postgresql-contrib -yInitialize the PostgreSQL database cluster and start the service:
sudo postgresql-setup --initdb
sudo systemctl enable postgresql --nowCreate a dedicated database and user for Redmine with appropriate permissions:
sudo -u postgres createdb redmine_production
sudo -u postgres createuser redmine_user
sudo -u postgres psql -c "ALTER USER redmine_user WITH PASSWORD 'secure_password_here';"
sudo -u postgres psql -c "GRANT ALL PRIVILEGES ON DATABASE redmine_production TO redmine_user;"Configure PostgreSQL authentication by editing the pg_hba.conf file:
sudo nano /var/lib/pgsql/data/pg_hba.confAdd the following line to enable password authentication for the Redmine user:
local redmine_production redmine_user md5Restart PostgreSQL to apply authentication changes:
sudo systemctl restart postgresqlMySQL/MariaDB Installation and Setup
Install MariaDB server and development packages for MySQL compatibility:
sudo dnf install mariadb-server mariadb-devel -yStart and enable MariaDB service:
sudo systemctl enable mariadb --nowSecure the MariaDB installation by running the security script:
sudo mysql_secure_installationFollow the interactive prompts to set the root password, remove anonymous users, disable remote root login, and remove test databases. Create a dedicated database and user for Redmine:
sudo mysql -u root -pExecute the following SQL commands within the MySQL prompt:
CREATE DATABASE redmine_production CHARACTER SET utf8mb4 COLLATE utf8mb4_unicode_ci;
CREATE USER 'redmine_user'@'localhost' IDENTIFIED BY 'secure_password_here';
GRANT ALL PRIVILEGES ON redmine_production.* TO 'redmine_user'@'localhost';
FLUSH PRIVILEGES;
EXIT;The utf8mb4 character set ensures full Unicode support, including emojis and extended characters that may appear in project descriptions or comments.
Downloading and Installing Redmine
Creating System User and Directory Structure
Create a dedicated system user for running Redmine, enhancing security through process isolation:
sudo useradd -r -m -d /opt/redmine redmineThis command creates a system user with the home directory set to /opt/redmine, providing a dedicated space for the application installation. Establish proper directory ownership and permissions:
sudo mkdir -p /opt/redmine
sudo chown redmine:redmine /opt/redmineObtaining Redmine Source Code
Download the latest stable Redmine release from the official website:
cd /tmp
wget https://www.redmine.org/releases/redmine-6.0.6.tar.gzVerify the download integrity if checksums are provided on the download page. Extract the archive to the installation directory:
sudo tar -xzf redmine-6.0.6.tar.gz -C /opt/
sudo mv /opt/redmine-6.0.6 /opt/redmine/redmine
sudo chown -R redmine:redmine /opt/redmine/The directory structure now contains the complete Redmine application under /opt/redmine/redmine, with proper ownership assigned to the redmine user.
Installing Ruby Dependencies
Navigate to the Redmine directory and install required gems using Bundler:
sudo -u redmine -H bash -l -c 'cd /opt/redmine/redmine && bundle install --without development test'This command installs only production dependencies, excluding development and testing gems that are unnecessary for deployment. The process downloads and compiles various Ruby gems, which may take several minutes depending on system performance and internet connectivity.
If gem installation encounters compilation errors, ensure all development packages are properly installed:
sudo dnf install gcc-c++ libffi-devel readline-devel -yRedmine Configuration
Database Connection Setup
Copy the database configuration template and create the production configuration:
sudo -u redmine cp /opt/redmine/redmine/config/database.yml.example /opt/redmine/redmine/config/database.ymlEdit the database configuration file to match your database setup:
sudo -u redmine nano /opt/redmine/redmine/config/database.ymlFor PostgreSQL configuration, update the production section:
production:
adapter: postgresql
database: redmine_production
host: localhost
username: redmine_user
password: "secure_password_here"
encoding: utf8
pool: 5
timeout: 5000For MySQL/MariaDB configuration, use:
production:
adapter: mysql2
database: redmine_production
host: localhost
username: redmine_user
password: "secure_password_here"
encoding: utf8mb4
collation: utf8mb4_unicode_ci
pool: 5
timeout: 5000The pool setting controls database connection pooling, while timeout prevents hanging connections during high load periods.
Application Configuration
Create the application configuration file from the template:
sudo -u redmine cp /opt/redmine/redmine/config/configuration.yml.example /opt/redmine/redmine/config/configuration.ymlEdit the configuration file to customize Redmine settings:
sudo -u redmine nano /opt/redmine/redmine/config/configuration.ymlConfigure email delivery for notifications:
production:
email_delivery:
delivery_method: :smtp
smtp_settings:
address: "smtp.example.com"
port: 587
authentication: :login
domain: "example.com"
user_name: "redmine@example.com"
password: "email_password"
enable_starttls_auto: trueConfigure file attachment storage and maximum sizes:
attachments_storage_path: /opt/redmine/files
max_attachment_size: 5242880 # 5MB in bytesSecurity Token Generation and Database Migration
Generate secure session tokens for application security:
sudo -u redmine -H bash -l -c 'cd /opt/redmine/redmine && bundle exec rake generate_secret_token RAILS_ENV=production'Execute database migrations to create the required schema:
sudo -u redmine -H bash -l -c 'cd /opt/redmine/redmine && RAILS_ENV=production bundle exec rake db:migrate'Load default configuration data and create the initial administrator account:
sudo -u redmine -H bash -l -c 'cd /opt/redmine/redmine && RAILS_ENV=production bundle exec rake redmine:load_default_data'During the data loading process, select your preferred language when prompted. The default administrator account uses “admin” as both username and password, which must be changed immediately after first login for security purposes.
Web Server Configuration
Apache HTTP Server Setup
Install Apache HTTP Server and necessary modules:
sudo dnf install httpd httpd-devel -yInstall Passenger module for Ruby application serving:
sudo gem install passenger
sudo passenger-install-apache2-module --autoThe Passenger installation process provides Apache configuration directives that must be added to the Apache configuration. Create a Redmine virtual host configuration:
sudo nano /etc/httpd/conf.d/redmine.confAdd the following configuration:
LoadModule passenger_module /usr/local/share/gems/gems/passenger-x.x.x/buildout/apache2/mod_passenger.so
PassengerRoot /usr/local/share/gems/gems/passenger-x.x.x
PassengerDefaultRuby /usr/bin/ruby
<VirtualHost *:80>
ServerName your-domain.com
DocumentRoot /opt/redmine/redmine/public
PassengerAppRoot /opt/redmine/redmine
PassengerUser redmine
PassengerGroup redmine
PassengerMinInstances 1
PassengerMaxPoolSize 6
<Directory /opt/redmine/redmine/public>
AllowOverride all
Options -MultiViews
Require all granted
</Directory>
</VirtualHost>Adjust the Passenger version numbers in the LoadModule and PassengerRoot directives to match your installation. Add the Apache user to the redmine group for file access:
sudo usermod -aG redmine apacheEnable and start Apache service:
sudo systemctl enable httpd --nowNginx Configuration
Install Nginx web server for high-performance Ruby application serving:
sudo dnf install nginx -yCreate an Nginx server block configuration for Redmine:
sudo nano /etc/nginx/conf.d/redmine.confConfigure Nginx to serve Redmine through upstream application servers:
upstream redmine_app {
server 127.0.0.1:3000;
}
server {
listen 80;
server_name your-domain.com;
root /opt/redmine/redmine/public;
location / {
try_files $uri @redmine;
}
location @redmine {
proxy_pass http://redmine_app;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
}
location ~ ^/(assets|images|javascripts|stylesheets|themes) {
expires 1y;
add_header Cache-Control public;
access_log off;
}
}This configuration serves static assets directly through Nginx while proxying dynamic requests to the Ruby application. Enable and start Nginx:
sudo systemctl enable nginx --nowSSL/HTTPS Configuration
SSL Certificate Setup
Generate self-signed certificates for testing environments:
sudo mkdir /etc/ssl/private
sudo openssl req -x509 -nodes -days 365 -newkey rsa:2048 -keyout /etc/ssl/private/redmine.key -out /etc/ssl/certs/redmine.crtFor production environments, obtain certificates from Let’s Encrypt using Certbot:
sudo dnf install certbot python3-certbot-apache -y
sudo certbot --apache -d your-domain.comThe Certbot process automatically configures Apache for HTTPS and sets up automatic certificate renewal.
HTTPS Enforcement and Security
Update your Apache or Nginx configuration to enforce HTTPS redirects. For Apache, modify the virtual host configuration:
<VirtualHost *:80>
ServerName your-domain.com
Redirect permanent / https://your-domain.com/
</VirtualHost>
<VirtualHost *:443>
ServerName your-domain.com
DocumentRoot /opt/redmine/redmine/public
SSLEngine on
SSLCertificateFile /etc/ssl/certs/redmine.crt
SSLCertificateKeyFile /etc/ssl/private/redmine.key
# Additional SSL security headers
Header always set Strict-Transport-Security "max-age=63072000; includeSubDomains; preload"
Header always set X-Frame-Options DENY
Header always set X-Content-Type-Options nosniff
</VirtualHost>Configure Redmine to recognize HTTPS requests by updating the application configuration:
production:
protocol: "https"
host_name: "your-domain.com"File Permissions and Security Hardening
Setting Correct File Permissions
Establish proper file ownership and permissions for security and functionality:
sudo chown -R redmine:redmine /opt/redmine/
sudo chmod -R 755 /opt/redmine/redmine/
sudo chmod -R 777 /opt/redmine/redmine/tmp/
sudo chmod -R 777 /opt/redmine/redmine/log/
sudo chmod -R 755 /opt/redmine/redmine/files/Secure sensitive configuration files by restricting access:
sudo chmod 600 /opt/redmine/redmine/config/database.yml
sudo chmod 600 /opt/redmine/redmine/config/configuration.ymlSet up log rotation to prevent disk space exhaustion:
sudo nano /etc/logrotate.d/redmineAdd the following logrotate configuration:
/opt/redmine/redmine/log/*.log {
weekly
missingok
rotate 52
compress
delaycompress
notifempty
create 640 redmine redmine
}Security Best Practices
Configure the firewall to allow only necessary ports while maintaining security:
sudo firewall-cmd --permanent --add-service=http
sudo firewall-cmd --permanent --add-service=https
sudo firewall-cmd --reloadFor custom ports or SSH access, add specific rules:
sudo firewall-cmd --permanent --add-port=22/tcp
sudo firewall-cmd --reloadConfigure SELinux contexts for Ruby applications if SELinux enforcement is enabled:
sudo setsebool -P httpd_can_network_connect 1
sudo semanage fcontext -a -t httpd_exec_t "/opt/redmine/redmine/public(/.*)?"
sudo restorecon -R /opt/redmine/redmine/public/Testing and Initial Setup
Starting Redmine Services
Create a systemd service file for Redmine application management:
sudo nano /etc/systemd/system/redmine.serviceConfigure the service definition:
[Unit]
Description=Redmine Project Management
After=network.target
[Service]
Type=simple
User=redmine
Group=redmine
WorkingDirectory=/opt/redmine/redmine
ExecStart=/usr/local/bin/bundle exec rails server -e production -p 3000
Restart=always
RestartSec=10
[Install]
WantedBy=multi-user.targetEnable and start the Redmine service:
sudo systemctl daemon-reload
sudo systemctl enable redmine --nowTest application accessibility by opening a web browser and navigating to your server’s IP address or domain name. The Redmine welcome page should display, indicating successful installation.
Initial Administration Setup
Log in using the default administrator credentials:
- Username: admin
- Password: admin
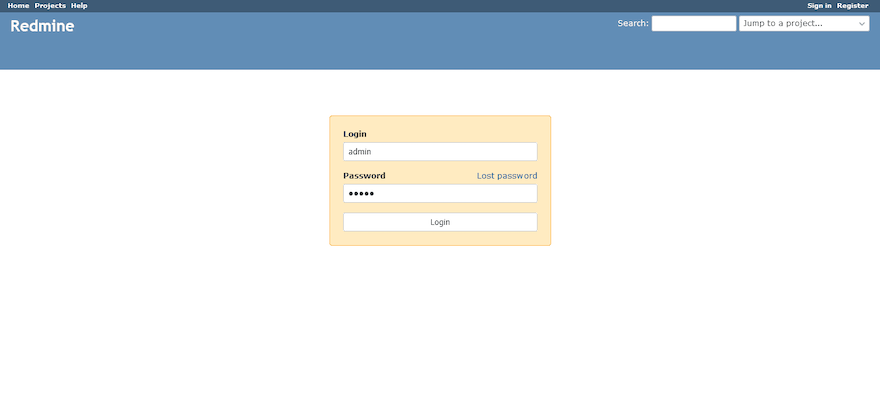
Immediately change the default password by navigating to “My account” in the top-right menu. Configure basic application settings through the Administration panel:
- Set the application title and description
- Configure authentication settings
- Set up email notifications
- Create the first project to test functionality
- Add users and assign appropriate roles
Test core functionality by creating issues, updating project information, and verifying email notifications work correctly.
Troubleshooting Common Issues
Installation Problems
Ruby gem installation failures often result from missing development packages or compilation errors. Install additional development dependencies:
sudo dnf install libffi-devel readline-devel sqlite-devel -yDatabase connection errors typically indicate configuration problems in database.yml. Verify database credentials and connectivity:
sudo -u redmine -H bash -l -c 'cd /opt/redmine/redmine && RAILS_ENV=production bundle exec rails runner "puts ActiveRecord::Base.connection.execute(\"SELECT 1\").first"'Permission denied errors often result from incorrect file ownership or SELinux policies. Reset file permissions and check SELinux contexts:
sudo chown -R redmine:redmine /opt/redmine/
sudo restorecon -R /opt/redmine/ 2>/dev/null || truePerformance and Configuration Issues
Port conflicts prevent service startup when other applications occupy required ports. Check port usage and modify configurations accordingly:
sudo ss -tulpn | grep :3000Memory-related issues manifest as slow response times or application crashes. Monitor resource usage and adjust system specifications:
sudo htop
sudo journalctl -u redmine -fLog file analysis provides detailed error information for troubleshooting:
sudo tail -f /opt/redmine/redmine/log/production.logCommon 500 errors often result from missing gems, database connectivity issues, or permission problems. Check the production log for specific error messages and stack traces.
Performance Optimization and Maintenance
Performance Tuning
Database optimization significantly impacts Redmine performance, especially for large installations. Configure PostgreSQL memory settings:
sudo nano /var/lib/pgsql/data/postgresql.confAdjust key parameters based on available system resources:
shared_buffers = 256MB
work_mem = 4MB
maintenance_work_mem = 64MB
effective_cache_size = 1GBWeb server optimization improves response times and concurrent user capacity. For Apache with Passenger, tune worker processes:
PassengerMaxPoolSize 6
PassengerMinInstances 2
PassengerMaxInstancesPerApp 4
PassengerPoolIdleTime 300Ruby application optimization includes enabling production-mode caching and asset precompilation:
sudo -u redmine -H bash -l -c 'cd /opt/redmine/redmine && RAILS_ENV=production bundle exec rake assets:precompile'Ongoing Maintenance
Establish regular backup procedures to protect project data and configurations:
#!/bin/bash
# Backup script
DATE=$(date +%Y%m%d_%H%M%S)
sudo -u redmine pg_dump redmine_production > /backup/redmine_db_$DATE.sql
sudo tar -czf /backup/redmine_files_$DATE.tar.gz /opt/redmine/redmine/files/Schedule automated backups through cron jobs and verify backup integrity regularly. Security update management requires monitoring Redmine releases and Ruby gem vulnerabilities:
sudo -u redmine -H bash -l -c 'cd /opt/redmine/redmine && bundle audit --update'Log rotation and cleanup prevent disk space exhaustion and maintain system performance. Monitor log file sizes and adjust rotation policies as needed.
Performance monitoring helps identify bottlenecks and capacity planning requirements. Implement monitoring solutions to track response times, database performance, and resource utilization.
Congratulations! You have successfully installed Redmine. Thanks for using this tutorial for installing the Redmine management web application on Fedora 42 Linux system. For additional help or useful information, we recommend you check the official Redmine website.