How To Install Roundcube Webmail on Debian 13

Installing webmail software has become essential for organizations seeking secure, feature-rich email management solutions. Roundcube webmail stands out as a premier open-source email client that delivers professional-grade functionality with an intuitive interface. This comprehensive guide walks you through every step of installing Roundcube webmail on Debian 13, ensuring a smooth deployment process.
The installation process requires careful attention to system prerequisites, security configurations, and integration with existing mail infrastructure. Whether you’re setting up webmail for a small business or enterprise environment, proper installation and configuration ensure optimal performance and security. By following these detailed instructions, you’ll have a fully functional webmail system that provides users with seamless access to their email accounts through any web browser.
Understanding Roundcube Webmail
What is Roundcube Webmail?
Roundcube represents a sophisticated web-based IMAP email client developed using PHP technology. This modern application provides users with an Ajax-driven interface that mimics desktop email applications while maintaining browser-based accessibility. The software supports over 80 languages, making it suitable for international deployments and diverse user bases.
The architecture relies on standard web technologies including HTML5, CSS3, and JavaScript to deliver responsive performance across various devices and browsers. Roundcube’s modular design allows administrators to customize functionality through an extensive plugin ecosystem, enabling features ranging from calendar integration to advanced filtering capabilities.
Key Features and Benefits
Roundcube webmail offers comprehensive email management capabilities that rival commercial solutions. The find-as-you-type address book functionality streamlines contact management, while the drag-and-drop interface simplifies email organization. Advanced features include HTML message composition, spell checking in multiple languages, and robust search functionality across all email folders.
Security features encompass CSRF protection, input validation, and support for modern encryption protocols. The responsive design automatically adapts to mobile devices, tablets, and desktop computers, ensuring consistent user experience across platforms. Plugin architecture enables administrators to extend functionality with features such as two-factor authentication, calendar scheduling, and file management integration.
System Requirements and Prerequisites
Minimum System Requirements
Debian 13 installation requires a stable system foundation with adequate resources for webmail operations. The operating system should have at least 1GB of RAM, though 2GB or more is recommended for production environments handling multiple concurrent users. Storage requirements include 500MB for Roundcube files plus additional space for email data and system logs.
Web server compatibility encompasses Apache HTTP Server, Nginx, Lighttpd, Cherokee, or Hiawatha. Apache remains the most common choice due to extensive documentation and widespread support. PHP version 7.3 represents the minimum requirement, but PHP 8.x provides enhanced performance and security features that benefit Roundcube operations.
Database support includes MySQL 5.5+, MariaDB 10.1+, PostgreSQL 9.1+, SQLite 3, Microsoft SQL Server, or Oracle Database. MySQL and MariaDB offer the best combination of performance, reliability, and community support for most installations. The mail server must provide IMAP4 rev1 compliance for proper integration with Roundcube’s email handling mechanisms.
Required Services
A fully functional mail server infrastructure forms the backbone of any webmail deployment. Postfix combined with Dovecot provides a robust solution for SMTP and IMAP services respectively. These components handle mail delivery, storage, and retrieval operations that Roundcube depends on for core functionality.
Database server installation requires careful consideration of performance requirements and backup strategies. MySQL or MariaDB installations should include proper configuration for web application workloads, including appropriate connection limits and query optimization settings. SSL certificates from trusted certificate authorities ensure secure communication between users and the webmail interface.
Preparing the Debian 13 Environment
System Updates and Package Management
Begin by updating the Debian 13 system to ensure all packages reflect the latest security patches and feature improvements. Execute the update command sequence to refresh package repositories and upgrade existing installations:
sudo apt update && sudo apt upgrade -yEnable additional repositories if necessary for specific software versions or third-party packages. Install essential build tools and development libraries that support compilation and installation of various web application components:
sudo apt install software-properties-common apt-transport-https ca-certificates curl gnupg lsb-releaseInstalling Apache Web Server
Apache HTTP Server installation provides the web server foundation for Roundcube webmail operations. Install Apache along with PHP module support using the package manager:
sudo apt install apache2 libapache2-mod-php php php-mysql php-mbstring php-xml php-zip php-json php-curl php-gd php-intlStart and enable Apache service to ensure automatic startup during system boot cycles:
sudo systemctl start apache2
sudo systemctl enable apache2Configure firewall rules to allow HTTP and HTTPS traffic through the system firewall. Ubuntu’s Uncomplicated Firewall (UFW) simplifies this process:
sudo ufw allow 'Apache Full'
sudo ufw enableImplement basic Apache security hardening by disabling server signature information and configuring appropriate security headers. Edit the main Apache configuration file to enhance security posture:
sudo nano /etc/apache2/conf-available/security.confInstalling and Configuring PHP
PHP installation requires specific modules that Roundcube depends on for proper functionality. Install the complete PHP package set including required and recommended extensions:
sudo apt install php-dom php-json php-xml php-mbstring php-openssl php-pdo php-iconv php-fileinfo php-zip php-pspell php-ldap php-imagickConfigure PHP settings to optimize performance for webmail operations. Edit the PHP configuration file to adjust memory limits, execution timeouts, and file upload restrictions:
sudo nano /etc/php/8.2/apache2/php.iniKey configuration parameters include:
memory_limit = 256Mmax_execution_time = 300upload_max_filesize = 50Mpost_max_size = 50Mdate.timezone = "Your/Timezone"
Restart Apache to apply PHP configuration changes:
sudo systemctl restart apache2Database Setup and Configuration
Installing MySQL/MariaDB
MariaDB installation provides robust database services optimized for web applications. Install MariaDB server and client tools:
sudo apt install mariadb-server mariadb-clientSecure the MySQL installation by running the security script that removes default accounts, sets root passwords, and disables remote root access:
sudo mysql_secure_installationFollow the prompts to:
- Set root password
- Remove anonymous users
- Disallow remote root login
- Remove test databases
- Reload privilege tables
Start and enable MariaDB service for automatic startup:
sudo systemctl start mariadb
sudo systemctl enable mariadbCreating Roundcube Database and User
Connect to MySQL as the root user to create the Roundcube database and dedicated user account:
sudo mysql -u root -pCreate a dedicated database for Roundcube with UTF-8 character encoding:
CREATE DATABASE roundcube DEFAULT CHARACTER SET utf8 COLLATE utf8_general_ci;Create a database user with appropriate privileges for Roundcube operations:
CREATE USER 'roundcubeuser'@'localhost' IDENTIFIED BY 'strong_password_here';
GRANT ALL PRIVILEGES ON roundcube.* TO 'roundcubeuser'@'localhost';
FLUSH PRIVILEGES;
EXIT;Test database connectivity to verify proper configuration:
mysql -u roundcubeuser -p roundcubeDownloading and Installing Roundcube
Obtaining Roundcube Source Code
Download Roundcube from the official source to ensure authenticity and access to the latest stable release. Navigate to the temporary directory for download operations:
cd /tmpCheck the latest version available on the Roundcube website or GitHub repository. Download the complete package using wget:
wget https://github.com/roundcube/roundcubemail/releases/download/1.6.4/roundcubemail-1.6.4-complete.tar.gzVerify download integrity using SHA-256 checksum verification. Compare the downloaded file checksum against the official checksum published on the Roundcube website:
sha256sum roundcubemail-1.6.4-complete.tar.gzUnderstanding version numbering helps identify stable releases versus development versions. Stable releases use standard semantic versioning (e.g., 1.6.4), while development versions include additional identifiers.
Extracting and Setting Up Files
Extract the Roundcube archive to the web server document root directory:
sudo tar -xzf roundcubemail-1.6.4-complete.tar.gz -C /var/www/html/
sudo mv /var/www/html/roundcubemail-1.6.4 /var/www/html/roundcubeSet appropriate file ownership and permissions for security and functionality:
sudo chown -R www-data:www-data /var/www/html/roundcube
sudo chmod -R 755 /var/www/html/roundcubeConfigure specific permissions for sensitive directories:
sudo chmod -R 775 /var/www/html/roundcube/temp
sudo chmod -R 775 /var/www/html/roundcube/logsThe Roundcube directory structure includes several important components:
/bin/– Command-line utilities/config/– Configuration files/logs/– Application log files/temp/– Temporary files and cache/public_html/– Web-accessible files
Configuring Apache Virtual Host
Creating Apache Configuration
Create a dedicated virtual host configuration for Roundcube webmail. This approach provides better security isolation and configuration flexibility:
sudo nano /etc/apache2/sites-available/roundcube.confConfigure the virtual host with appropriate security settings:
<VirtualHost *:80>
ServerName mail.yourdomain.com
DocumentRoot /var/www/html/roundcube
<Directory /var/www/html/roundcube>
Options -Indexes
AllowOverride All
Require all granted
DirectoryIndex index.php
</Directory>
<Directory /var/www/html/roundcube/config>
Require all denied
</Directory>
<Directory /var/www/html/roundcube/temp>
Require all denied
</Directory>
<Directory /var/www/html/roundcube/logs>
Require all denied
</Directory>
ErrorLog ${APACHE_LOG_DIR}/roundcube_error.log
CustomLog ${APACHE_LOG_DIR}/roundcube_access.log combined
</VirtualHost>For SSL configuration, create an additional virtual host listening on port 443:
<VirtualHost *:443>
ServerName mail.yourdomain.com
DocumentRoot /var/www/html/roundcube
SSLEngine on
SSLCertificateFile /path/to/your/certificate.crt
SSLCertificateKeyFile /path/to/your/private.key
SSLCertificateChainFile /path/to/your/chain.crt
# Include the same directory configurations as above
</VirtualHost>Enabling Configuration and Testing
Enable the new site configuration and required Apache modules:
sudo a2ensite roundcube.conf
sudo a2enmod rewrite ssl
sudo systemctl restart apache2Test Apache configuration syntax to identify any configuration errors:
sudo apache2ctl configtestVerify web server functionality by accessing the server through a web browser. Check Apache error logs for any issues:
sudo tail -f /var/log/apache2/roundcube_error.logMonitor access logs to verify successful connections:
sudo tail -f /var/log/apache2/roundcube_access.logRoundcube Initial Configuration
Database Schema Installation
Import the Roundcube database schema using the provided SQL scripts. Navigate to the Roundcube directory and locate the database initialization files:
cd /var/www/html/roundcube/SQLImport the MySQL schema into the previously created database:
mysql -u roundcubeuser -p roundcube < mysql.initial.sqlVerify successful table creation by connecting to the database and listing tables:
mysql -u roundcubeuser -p roundcube -e "SHOW TABLES;"The Roundcube database includes tables for user management, contacts, messages, and system configuration. Understanding this structure helps with troubleshooting and maintenance operations.
Using the Web Installer
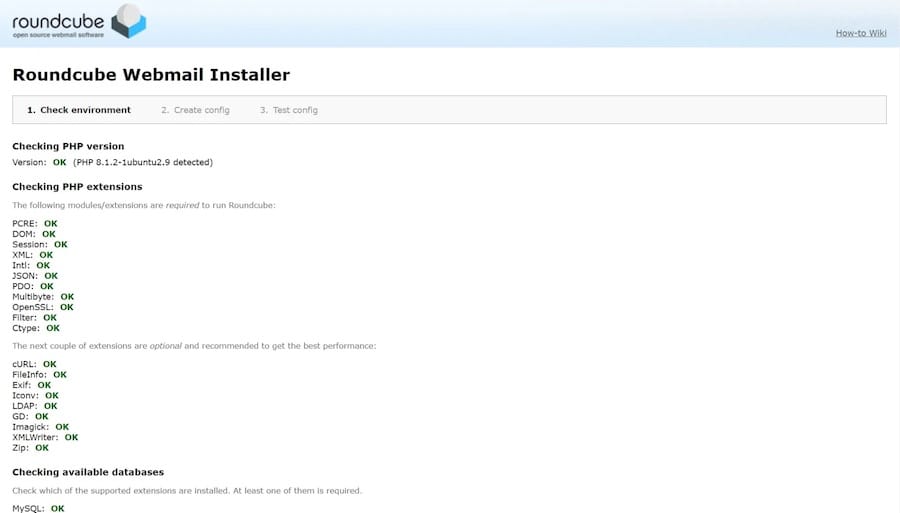
Access the Roundcube web installer through your browser by navigating to http://yourdomain.com/roundcube/installer/. The installer provides a step-by-step configuration wizard that simplifies initial setup.
The first installer step checks system requirements and displays any missing dependencies. Address any warnings or errors before proceeding to configuration steps. Common issues include missing PHP extensions or incorrect file permissions.
Database configuration requires entering the connection details established earlier:
- Database type: MySQL
- Database server: localhost
- Database name: roundcube
- Database username: roundcubeuser
- Database password: [your password]
IMAP and SMTP server configuration depends on your mail server setup. For local mail servers:
- IMAP server: localhost:143 (or 993 for SSL)
- SMTP server: localhost:587 (or 465 for SSL)
Configure additional settings including:
- Support email address
- Default language
- Skin selection
- Plugin activation
Manual Configuration File Setup
For advanced users or automated deployments, manual configuration provides greater control. Copy the sample configuration file:
sudo cp /var/www/html/roundcube/config/config.inc.php.sample /var/www/html/roundcube/config/config.inc.phpEdit the configuration file with appropriate settings:
sudo nano /var/www/html/roundcube/config/config.inc.phpKey configuration parameters include:
// Database configuration
$config['db_dsnw'] = 'mysql://roundcubeuser:password@localhost/roundcube';
// IMAP configuration
$config['default_host'] = 'localhost';
$config['default_port'] = 143;
$config['imap_conn_options'] = [
'ssl' => ['verify_peer' => false, 'verify_peer_name' => false],
];
// SMTP configuration
$config['smtp_server'] = 'localhost';
$config['smtp_port'] = 587;
$config['smtp_user'] = '%u';
$config['smtp_pass'] = '%p';
// Security settings
$config['des_key'] = 'your_24_character_des_key_here';
$config['force_https'] = true;
$config['use_https'] = true;Secure the configuration file with restrictive permissions:
sudo chmod 640 /var/www/html/roundcube/config/config.inc.php
sudo chown www-data:www-data /var/www/html/roundcube/config/config.inc.phpMail Server Integration
IMAP Server Configuration
Dovecot IMAP server integration requires proper authentication and security configuration. Edit the Dovecot configuration to enable webmail access:
sudo nano /etc/dovecot/dovecot.confConfigure IMAP listener settings:
listen = *, ::
protocols = imap lmtpSet up SSL/TLS encryption for secure connections:
sudo nano /etc/dovecot/conf.d/10-ssl.confConfigure SSL settings:
ssl = required
ssl_cert = </etc/ssl/certs/ssl-cert-snakeoil.pem
ssl_key = </etc/ssl/private/ssl-cert-snakeoil.key
ssl_cipher_list = HIGH:!SSLv2:!aNULL:!eNULL:!EXPORT:!DES:!MD5:!PSK:!SRP
ssl_protocols = !SSLv2 !SSLv3Configure authentication mechanisms:
sudo nano /etc/dovecot/conf.d/10-auth.confEnable appropriate authentication:
auth_mechanisms = plain login
disable_plaintext_auth = yesRestart Dovecot to apply configuration changes:
sudo systemctl restart dovecotSMTP Server Configuration
Postfix SMTP integration enables Roundcube to send outgoing messages. Configure Postfix for webmail authentication:
sudo nano /etc/postfix/main.cfAdd or modify SMTP authentication settings:
smtpd_sasl_auth_enable = yes
smtpd_sasl_type = dovecot
smtpd_sasl_path = private/auth
smtpd_recipient_restrictions = permit_sasl_authenticated,permit_mynetworks,reject_unauth_destinationConfigure submission port for authenticated sending:
sudo nano /etc/postfix/master.cfEnable submission service:
submission inet n - y - - smtpd
-o smtpd_tls_security_level=encrypt
-o smtpd_sasl_auth_enable=yes
-o smtpd_client_restrictions=permit_sasl_authenticated,rejectRestart Postfix to implement changes:
sudo systemctl restart postfixTest email functionality by sending a test message through the Roundcube interface and verifying successful delivery.
Security Hardening and Best Practices
File System Security
Implement comprehensive file system security to protect against unauthorized access and potential vulnerabilities. Set restrictive permissions on configuration directories:
sudo chmod 750 /var/www/html/roundcube/config
sudo chmod 640 /var/www/html/roundcube/config/config.inc.phpRemove the installer directory after completing configuration to prevent unauthorized access:
sudo rm -rf /var/www/html/roundcube/installerConfigure log rotation to manage disk space and maintain system performance:
sudo nano /etc/logrotate.d/roundcubeCreate log rotation configuration:
/var/www/html/roundcube/logs/*.log {
daily
missingok
rotate 52
compress
delaycompress
notifempty
create 644 www-data www-data
}Implement regular security updates through automated package management and monitoring of security advisories for Roundcube and related components.
Web Server Security
Configure Apache security headers to protect against common web vulnerabilities. Create a security configuration file:
sudo nano /etc/apache2/conf-available/security-headers.confAdd comprehensive security headers:
Header always set X-Content-Type-Options nosniff
Header always set X-Frame-Options DENY
Header always set X-XSS-Protection "1; mode=block"
Header always set Strict-Transport-Security "max-age=63072000; includeSubDomains; preload"
Header always set Referrer-Policy strict-origin-when-cross-origin
Header always set Content-Security-Policy "default-src 'self'; script-src 'self' 'unsafe-inline'; style-src 'self' 'unsafe-inline'"Enable the security headers configuration:
sudo a2enconf security-headers
sudo systemctl restart apache2Implement rate limiting to prevent brute force attacks and abuse:
sudo apt install libapache2-mod-security2 libapache2-mod-evasive
sudo a2enmod security2 evasiveConfigure ModSecurity for additional protection against web application attacks.
Testing and Verification
Basic Functionality Testing
Comprehensive testing ensures all Roundcube components function correctly. Access the webmail interface through your configured domain and verify the login process works with existing email accounts.
Test core email functionality including:
- Sending messages to internal and external recipients
- Receiving and reading incoming messages
- Attachment handling for various file types
- Folder management and message organization
- Search functionality across different message attributes
Verify address book functionality by adding contacts and testing auto-completion features during message composition. Test the spell-check feature with different languages if multilingual support is required.
Performance and Troubleshooting
Monitor system performance during peak usage periods to identify potential bottlenecks. Use system monitoring tools to track:
- Memory usage patterns
- CPU utilization during message processing
- Database query performance
- Disk I/O for message storage operations
Common installation issues and solutions include:
Database Connection Errors: Verify database credentials, network connectivity, and service status. Check MySQL error logs for specific connection issues.
Permission Denied Errors: Ensure proper file ownership and permissions for web server access. Verify SELinux policies if applicable.
IMAP/SMTP Connection Failures: Test mail server connectivity independently using telnet or openssl tools. Verify firewall rules and service configurations.
Session Management Issues: Check PHP session configuration and ensure adequate disk space for session storage.
Analyze log files regularly for error patterns:
sudo tail -f /var/www/html/roundcube/logs/errors.log
sudo tail -f /var/log/apache2/roundcube_error.logPost-Installation Configuration
User Management and Plugins
Roundcube’s plugin architecture enables extensive functionality customization. Popular plugins enhance user experience and administrative capabilities:
Calendar Plugin: Provides scheduling and event management capabilities integrated with the webmail interface. Install using Composer or manual download:
cd /var/www/html/roundcube
sudo composer require kolab/calendarDesktop Notifications Plugin: Enables browser notifications for new messages, improving user awareness of incoming email.
Two-Factor Authentication: Enhances security through additional authentication factors using Google Authenticator or similar applications.
Configure plugins by editing the main configuration file:
$config['plugins'] = array('calendar', 'desktop_notification', 'twofactor_auth');Theme customization allows organizations to maintain brand consistency. Install custom themes by placing files in the skins directory and updating configuration settings.
Maintenance and Updates
Establish regular maintenance procedures to ensure optimal performance and security. Implement automated backup strategies for configuration files and user data:
#!/bin/bash
# Roundcube backup script
BACKUP_DIR="/backup/roundcube"
DATE=$(date +%Y%m%d_%H%M%S)
# Backup database
mysqldump -u roundcubeuser -p roundcube > $BACKUP_DIR/roundcube_db_$DATE.sql
# Backup configuration
tar -czf $BACKUP_DIR/roundcube_config_$DATE.tar.gz /var/www/html/roundcube/configConfigure automatic cleanup scripts to manage temporary files and logs:
#!/bin/bash
# Cleanup temporary files older than 7 days
find /var/www/html/roundcube/temp -type f -mtime +7 -delete
# Compress old log files
find /var/www/html/roundcube/logs -name "*.log" -mtime +30 -exec gzip {} \;Monitor system updates and Roundcube releases for security patches and feature improvements. Establish a testing environment for validating updates before production deployment.
Set up monitoring and alerting systems to track service availability and performance metrics. Tools like Nagios, Zabbix, or modern solutions like Prometheus provide comprehensive monitoring capabilities.
Congratulations! You have successfully installed Roundcube. Thanks for using this tutorial for installing Roundcube Webmail on your Debian 13 “Trixie” system. For additional help or useful information, we recommend you check the official Roundcube Webmail website.