How To Install Snipe-IT on AlmaLinux 10

Snipe-IT stands as one of the most robust open-source IT asset management systems available today, providing organizations with comprehensive tracking capabilities for laptops, software licenses, accessories, and other valuable IT resources. Built on the Laravel PHP framework, this powerful application offers an intuitive web interface that simplifies asset lifecycle management while maintaining detailed audit trails.
AlmaLinux 10 emerges as an excellent choice for hosting Snipe-IT due to its enterprise-grade stability, security features, and long-term support commitment. As a community-driven RHEL alternative, AlmaLinux provides the reliability needed for production environments while maintaining compatibility with modern web applications. This combination creates an ideal foundation for organizations seeking a dependable asset management solution.
This comprehensive guide walks you through every step of installing Snipe-IT on AlmaLinux 10, from initial system preparation to final configuration. Whether you’re a seasoned system administrator or new to Linux server management, these detailed instructions ensure a successful deployment.
Prerequisites and System Requirements
Hardware Requirements
Your AlmaLinux 10 server needs adequate resources to run Snipe-IT effectively. The minimum hardware specifications include 2GB of RAM, though 4GB or more provides better performance for larger deployments. Allocate at least 20GB of disk space for the operating system, application files, and database storage.
CPU requirements vary based on user load and asset database size. A dual-core processor handles small to medium deployments, while larger organizations benefit from quad-core or higher configurations. Consider network bandwidth requirements for file uploads, particularly when managing asset photos and documentation.
Software Prerequisites
Begin with a fresh AlmaLinux 10 installation featuring a minimal server configuration. Ensure you have root access or sudo privileges for system administration tasks. Network connectivity is essential for downloading packages and accessing repositories during the installation process.
Prepare a fully qualified domain name (FQDN) or public IP address for accessing your Snipe-IT installation. SSL certificates require a valid domain name, making this crucial for production deployments. Document your planned configuration details before beginning the installation process.
Snipe-IT System Requirements
Snipe-IT requires PHP 8.1.0 or higher for optimal functionality and security. The application supports both MySQL and MariaDB database systems, with MariaDB being the preferred choice for AlmaLinux environments. Apache or Nginx web servers provide adequate performance, though Apache offers simpler configuration for most administrators.
Essential PHP extensions include bcmath, mbstring, gd, curl, xml, and zip modules. These extensions handle mathematical calculations, string manipulation, image processing, HTTP requests, XML parsing, and file compression respectively. Missing extensions prevent proper application functionality.
System Preparation and Initial Setup
Updating AlmaLinux 10
Start by updating your AlmaLinux 10 system to ensure all security patches and package updates are applied. Execute the following commands to update the system:
sudo dnf update -y
sudo dnf install -y epel-release
sudo dnf update -yThe EPEL (Extra Packages for Enterprise Linux) repository provides additional packages not included in the base AlmaLinux repositories. This repository contains many dependencies required for modern web applications like Snipe-IT.
Reboot your system after major updates to ensure all kernel and system changes take effect properly. Monitor the update process for any errors or conflicts that might require manual intervention.
Firewall Configuration
Configure the firewall to allow web traffic while maintaining security. AlmaLinux 10 uses firewalld for firewall management:
sudo firewall-cmd --permanent --add-service=http
sudo firewall-cmd --permanent --add-service=https
sudo firewall-cmd --permanent --add-service=ssh
sudo firewall-cmd --reloadThese commands open ports 80 (HTTP), 443 (HTTPS), and 22 (SSH) permanently. Verify the configuration by listing active services:
sudo firewall-cmd --list-servicesConsider restricting SSH access to specific IP addresses for enhanced security in production environments. Document your firewall rules for future reference and compliance requirements.
SELinux Initial Configuration
SELinux (Security-Enhanced Linux) provides mandatory access controls that enhance system security. Configure initial SELinux settings to support web applications:
sudo setsebool -P httpd_unified 1
sudo setsebool -P httpd_can_network_connect_db 1These boolean settings allow Apache to access network resources and connect to databases. The -P flag makes these changes persistent across reboots. Verify SELinux status with:
sestatusInstalling LAMP Stack Components
Apache Web Server Installation
Install and configure Apache HTTP Server using the DNF package manager:
sudo dnf install -y httpd
sudo systemctl start httpd
sudo systemctl enable httpdThese commands install Apache, start the service immediately, and enable automatic startup on boot. Test the installation by accessing your server’s IP address in a web browser. You should see the default Apache welcome page.
Configure Apache for optimal Snipe-IT performance by editing the main configuration file. Basic Apache configuration includes setting the ServerName directive and adjusting resource limits based on your server specifications.
Create a backup of the original configuration before making changes:
sudo cp /etc/httpd/conf/httpd.conf /etc/httpd/conf/httpd.conf.backupMariaDB Database Installation and Configuration
Install MariaDB server and client packages:
sudo dnf install -y mariadb-server mariadb
sudo systemctl start mariadb
sudo systemctl enable mariadbSecure your MariaDB installation using the built-in security script:
sudo mysql_secure_installationFollow the prompts to set a root password, remove anonymous users, disable remote root login, and remove test databases. These steps significantly improve database security.
Test MariaDB connectivity by logging in with the root account:
mysql -u root -pEnter your root password when prompted. Exit the MariaDB prompt with the exit command after confirming successful login.
PHP 8.x Installation and Extensions
Install PHP and the required extensions for Snipe-IT:
sudo dnf install -y php php-common php-bcmath php-mbstring php-gd php-curl php-xml php-zip php-mysql php-json php-openssl php-tokenizer php-fileinfoThese extensions provide essential functionality for Snipe-IT operations. The bcmath extension handles arbitrary precision arithmetic, while mbstring manages multibyte string functions. The gd extension processes images, and curl enables HTTP requests.
Configure PHP settings for optimal performance:
sudo nano /etc/php.iniAdjust the following settings:
memory_limit = 256Mupload_max_filesize = 10Mpost_max_size = 10Mmax_execution_time = 300
Restart Apache to apply PHP configuration changes:
sudo systemctl restart httpdDatabase Setup for Snipe-IT
Creating Snipe-IT Database
Log into MariaDB as the root user to create the Snipe-IT database:
mysql -u root -pExecute the following SQL commands to create the database:
CREATE DATABASE snipeit CHARACTER SET utf8mb4 COLLATE utf8mb4_unicode_ci;The utf8mb4 character set supports full Unicode, including emoji and special characters that might appear in asset descriptions or user names. This character set prevents encoding issues with international characters.
Verify database creation by listing all databases:
SHOW DATABASES;Database User Creation and Permissions
Create a dedicated database user for Snipe-IT with appropriate permissions:
CREATE USER 'snipeituser'@'localhost' IDENTIFIED BY 'strong_password_here';
GRANT ALL PRIVILEGES ON snipeit.* TO 'snipeituser'@'localhost';
FLUSH PRIVILEGES;
EXIT;Replace strong_password_here with a complex password containing uppercase letters, lowercase letters, numbers, and special characters. Document this password securely as you’ll need it during Snipe-IT configuration.
Test the new user account by connecting to the database:
mysql -u snipeituser -p snipeitInstalling Composer PHP Dependency Manager
Composer Download and Installation
Download and install Composer globally on your AlmaLinux 10 system:
curl -sS https://getcomposer.org/installer | php
sudo mv composer.phar /usr/local/bin/composer
sudo chmod +x /usr/local/bin/composerThis installation method places Composer in the system PATH, making it accessible from any directory. Composer manages PHP dependencies and autoloading for modern PHP applications like Snipe-IT.
Composer Verification and Testing
Verify Composer installation by checking the version:
composer --versionThe output should display the Composer version and build information. If you encounter permission errors, ensure the composer binary has execute permissions and is owned by root.
Test Composer functionality by running the help command:
composer helpSnipe-IT Download and Installation
Downloading Snipe-IT Source Code
Navigate to the web server document root and clone the Snipe-IT repository:
cd /var/www/
sudo git clone https://github.com/snipe/snipe-it.git
sudo chown -R apache:apache /var/www/snipe-itGit cloning downloads the latest stable version of Snipe-IT. The chown command sets proper ownership for the Apache web server to access the files.
Alternatively, download a specific release version for greater stability in production environments. Check the Snipe-IT GitHub releases page for the latest stable version number.
Installing Dependencies with Composer
Navigate to the Snipe-IT directory and install PHP dependencies:
cd /var/www/snipe-it
sudo -u apache composer install --no-dev --optimize-autoloaderThe --no-dev flag excludes development dependencies, reducing the installation size and potential security risks. The --optimize-autoloader option improves application performance by creating an optimized class map.
Monitor the installation progress as Composer downloads and installs dozens of PHP packages. This process may take several minutes depending on your internet connection speed.
Environment Configuration
Copy the example environment file and configure application settings:
sudo -u apache cp .env.example .env
sudo -u apache nano .envConfigure the following essential settings in the .env file:
APP_ENV=production
APP_DEBUG=false
APP_URL=http://your-domain.com
DB_DATABASE=snipeit
DB_USERNAME=snipeituser
DB_PASSWORD=your_database_passwordGenerate an application encryption key:
sudo -u apache php artisan key:generateThis key encrypts sensitive data within the application. Never share this key or use the same key across multiple installations.
Web Server Configuration
Apache Virtual Host Creation
Create a virtual host configuration file for Snipe-IT:
sudo nano /etc/httpd/conf.d/snipeit.confAdd the following virtual host configuration:
<VirtualHost *:80>
ServerName your-domain.com
DocumentRoot /var/www/snipe-it/public
<Directory /var/www/snipe-it/public>
AllowOverride All
Require all granted
</Directory>
ErrorLog /var/log/httpd/snipeit_error.log
CustomLog /var/log/httpd/snipeit_access.log combined
</VirtualHost>Replace your-domain.com with your actual domain name or server IP address. The DocumentRoot points to the public directory within the Snipe-IT installation.
File Permissions and Ownership
Set correct file permissions and ownership for security and functionality:
sudo chown -R apache:apache /var/www/snipe-it
sudo chmod -R 755 /var/www/snipe-it
sudo chmod -R 775 /var/www/snipe-it/storage
sudo chmod -R 775 /var/www/snipe-it/bootstrap/cacheThese permissions allow Apache to read application files while restricting write access to specific directories. The storage and bootstrap/cache directories require write permissions for logs, sessions, and cached data.
Test the configuration by restarting Apache:
sudo systemctl restart httpdSELinux Configuration for Web Applications
SELinux Boolean Settings
Configure additional SELinux booleans for web application functionality:
sudo setsebool -P httpd_can_network_connect 1
sudo setsebool -P httpd_execmem 1These settings allow Apache to make network connections and execute memory operations required by PHP applications. Monitor SELinux audit logs for any denials during initial testing.
Advanced SELinux Configuration
Set proper SELinux file contexts for the Snipe-IT directories:
sudo semanage fcontext -a -t httpd_exec_t "/var/www/snipe-it/public(/.*)?"
sudo restorecon -Rv /var/www/snipe-itThese commands establish proper SELinux contexts for web content and restore contexts recursively. SELinux contexts determine what operations processes can perform on files and directories.
Snipe-IT Web-Based Setup Wizard
Accessing the Installation Interface
Open your web browser and navigate to your server’s domain name or IP address. The Snipe-IT pre-flight check screen appears, displaying system requirements and their status.
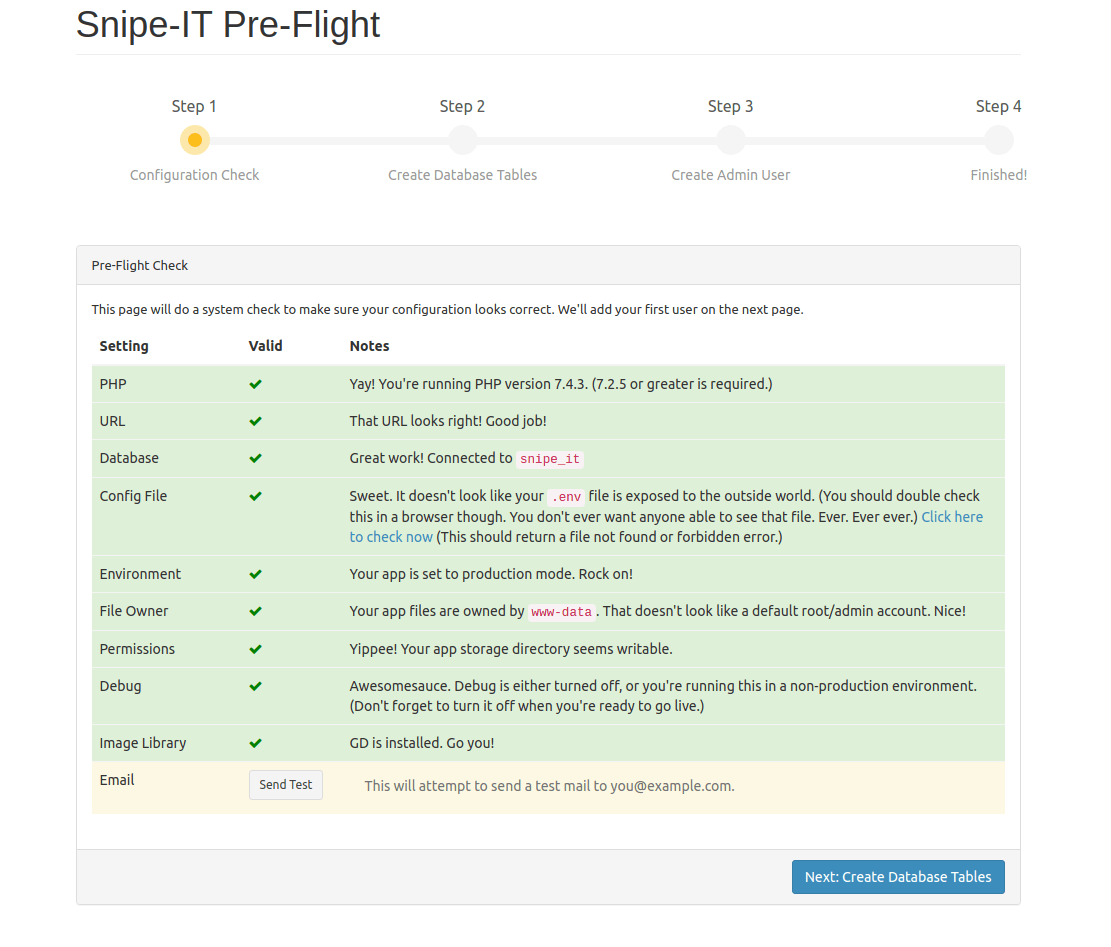
Review all requirements carefully. Green checkmarks indicate properly configured components, while red X marks highlight missing dependencies or configuration issues. Address any warnings before proceeding with the installation.
Common pre-flight check failures include missing PHP extensions, incorrect file permissions, or database connectivity issues. Refer to earlier sections to resolve these problems.
Completing the Setup Wizard
Follow the web-based setup wizard to complete the installation:
- Database Configuration: Enter your database details (snipeit, snipeituser, password)
- Administrator Account: Create your admin username, email, and password
- Company Information: Enter your organization name and other details
- Email Configuration: Configure SMTP settings for notifications (optional)
Click “Next” after each step to proceed. The wizard validates each configuration before advancing to the next step.
After completing all steps, the installation process creates database tables and finalizes the setup. This process may take a few minutes depending on server performance.
Post-Installation Configuration and Security
SSL/TLS Certificate Setup
Secure your Snipe-IT installation with SSL/TLS encryption. Install Certbot for Let’s Encrypt certificates:
sudo dnf install -y certbot python3-certbot-apache
sudo certbot --apache -d your-domain.comFollow the prompts to obtain and install SSL certificates. Certbot automatically configures Apache for HTTPS and sets up automatic certificate renewal.
Test certificate installation by accessing your site with HTTPS. The browser should display a lock icon indicating a secure connection.
Backup Strategy Configuration
Implement regular backups for both database and application files:
#!/bin/bash
# Create backup script
sudo nano /usr/local/bin/snipeit-backup.shAdd the following backup script content:
#!/bin/bash
BACKUP_DIR="/backup/snipeit"
DATE=$(date +%Y%m%d_%H%M%S)
# Create backup directory
mkdir -p $BACKUP_DIR
# Database backup
mysqldump -u snipeituser -p'password' snipeit > $BACKUP_DIR/snipeit_db_$DATE.sql
# File backup
tar -czf $BACKUP_DIR/snipeit_files_$DATE.tar.gz /var/www/snipe-itConfigure the script to run daily via cron for automated backups.
Troubleshooting Common Issues
Installation Problems
Common installation issues include PHP extension errors, database connection failures, and permission problems. Missing PHP extensions display clear error messages during the pre-flight check. Install missing extensions using DNF and restart Apache.
Database connection failures typically result from incorrect credentials or database server issues. Verify database credentials in the .env file and test manual database connections using the mysql command line client.
Permission-related issues manifest as file access errors or blank pages. Review file ownership and permissions, ensuring Apache can read application files and write to storage directories.
Performance Optimization
Optimize PHP memory limits based on your asset database size and user load. Large asset databases with many images require higher memory limits. Monitor PHP error logs for memory exhaustion errors.
Database query optimization becomes important as your asset database grows. Enable MySQL slow query logging to identify performance bottlenecks. Consider adding database indexes for frequently searched fields.
Apache performance tuning includes adjusting worker processes and connection limits. Monitor server resources during peak usage to identify optimization opportunities.
Maintenance and Updates
Updating Snipe-IT
Keep your Snipe-IT installation current with regular updates. Before updating, always create a complete backup of both database and files:
cd /var/www/snipe-it
sudo -u apache git pull origin master
sudo -u apache composer install --no-dev --optimize-autoloader
sudo -u apache php artisan migrateTest the updated installation thoroughly before announcing the maintenance completion to users.
System Maintenance
Perform regular system maintenance including security updates, log rotation, and performance monitoring. Schedule maintenance windows during low-usage periods to minimize user impact.
Monitor system logs for security events, application errors, and performance issues. Implement monitoring solutions to alert administrators of critical problems.
Congratulations! You have successfully installed Snipe-IT. Thanks for using this tutorial for installing the Snipe-IT asset management system on your AlmaLinux OS 10 system. For additional help or useful information, we recommend you check the official Snipe-IT website.