How To Install Squid Proxy Cache on Fedora 42

In this tutorial, we will show you how to install Squid Proxy Cache on Fedora 42. Squid proxy cache stands as one of the most reliable and feature-rich caching proxy solutions available for Linux systems. This comprehensive guide walks you through installing and configuring Squid proxy cache on Fedora 42, providing detailed instructions that ensure optimal performance and security for your network infrastructure.
Modern organizations face increasing demands for efficient bandwidth utilization and network performance optimization. Squid proxy cache addresses these challenges by serving as an intermediary between client devices and web servers, dramatically reducing response times and conserving valuable network resources. Fedora 42, with its cutting-edge package management and robust security features, provides an excellent foundation for deploying enterprise-grade proxy solutions.
Whether you’re managing a corporate network, educational institution, or home lab environment, this tutorial delivers practical expertise gained from years of Linux administration and proxy server deployment. The following sections cover everything from initial system preparation to advanced configuration options, ensuring you can successfully implement a production-ready Squid proxy installation.
Understanding Squid Proxy Cache Fundamentals
Squid operates as a high-performance HTTP and HTTPS caching proxy server that sits between client applications and destination web servers. When clients request web content, Squid intercepts these requests and checks its local cache for previously downloaded resources. If cached content exists and remains valid, Squid delivers it directly to the client without contacting the origin server.
This caching mechanism provides substantial benefits for network administrators. Bandwidth consumption decreases significantly as frequently accessed content gets served locally rather than downloaded repeatedly from external sources. Response times improve dramatically for cached resources, enhancing user experience across the organization. Additionally, Squid offers sophisticated access control features, allowing administrators to implement content filtering, user authentication, and usage monitoring.
Fedora 42 enhances Squid’s capabilities through its modern kernel architecture and optimized package management system. The DNF package manager ensures clean installations with proper dependency resolution, while systemd integration provides reliable service management and monitoring capabilities.
System Prerequisites and Requirements
Before beginning the Squid installation process, verify that your Fedora 42 system meets the necessary requirements. A minimum of 2GB RAM is recommended for basic proxy operations, though organizations with heavy traffic should allocate 4GB or more. Storage requirements depend on your caching strategy – allocate at least 10GB for cache storage, with larger allocations providing better cache hit rates.
Network connectivity requirements include a stable internet connection and properly configured network interfaces. Your system should have a static IP address or reliable DHCP reservation to ensure consistent proxy service availability. Firewall configuration will be addressed during the installation process, but ensure you have administrative access to modify firewall rules.
Administrative privileges are essential for Squid installation and configuration. You’ll need either root access or sudo privileges to install packages, modify system configurations, and manage services. Security best practices recommend using sudo rather than logging in as root directly.
Create a comprehensive pre-installation checklist to ensure smooth deployment. Update your system’s package repositories, verify network connectivity, and document your current firewall configuration. This preparation prevents common installation issues and provides a rollback reference if needed.
Installing Squid Proxy on Fedora 42
Begin the installation process by updating your Fedora 42 system to ensure all packages and security patches are current. Open a terminal and execute the following command:
sudo dnf update -yThis command downloads and installs all available updates for your system. The process may take several minutes depending on your internet connection and the number of available updates. If kernel updates are included, you may need to reboot your system before proceeding with the Squid installation.
After completing system updates, install the Squid package using DNF:
sudo dnf install squid -yThe DNF package manager automatically resolves dependencies and downloads the latest stable version of Squid available in Fedora 42 repositories. This process typically completes within a few minutes, depending on your internet connection speed.
Verify the installation by checking the Squid package version:
squid -vThis command displays detailed version information and compile-time options, confirming successful installation. The output includes important details about supported features and authentication methods.
Start the Squid service using systemd:
sudo systemctl start squidEnable automatic startup at boot time:
sudo systemctl enable squidVerify that Squid is running correctly:
sudo systemctl status squidThe status command should display “active (running)” along with recent log entries. If the service fails to start, check the error messages for troubleshooting guidance.
Confirm that Squid is listening on the default port 3128:
sudo ss -antpl | grep :3128This command should show Squid listening on port 3128, indicating successful service initialization.
Basic Squid Configuration Setup
Squid’s main configuration file resides at /etc/squid/squid.conf. This file contains hundreds of configuration options, but most installations require only basic modifications to function properly. Before making any changes, create a backup of the original configuration:
sudo cp /etc/squid/squid.conf /etc/squid/squid.conf.backupOpen the configuration file using your preferred text editor:
sudo nano /etc/squid/squid.confThe default configuration includes extensive documentation and examples. Key sections include ACL definitions, HTTP access rules, and cache configuration options. Understanding the basic structure helps navigate this comprehensive file effectively.
Locate the http_port directive, which defines the port number for proxy connections. The default configuration uses port 3128:
http_port 3128For basic installations, this default setting works perfectly. Advanced configurations might require multiple ports or specific interface bindings.
Network access configuration determines which clients can use your proxy server. Find the ACL definitions section and locate lines similar to:
acl localnet src 10.0.0.0/8
acl localnet src 172.16.0.0/12
acl localnet src 192.168.0.0/16These lines define local network ranges that are allowed to access the proxy. Modify these entries to match your network topology. For example, if your local network uses the 192.168.1.0/24 subnet, ensure this range is included:
acl localnet src 192.168.1.0/24The http_access rules determine which requests Squid allows or denies. The default configuration includes:
http_access allow localnet
http_access allow localhost
http_access deny allThis configuration allows access from defined local networks and localhost while denying all other requests. The order of these rules matters – Squid processes them sequentially and applies the first matching rule.
After making configuration changes, validate the syntax:
sudo squid -k parseThis command checks for syntax errors without starting the service. If errors are found, correct them before proceeding.
Restart the Squid service to apply your changes:
sudo systemctl restart squidMonitor the service logs during restart to ensure no errors occur:
sudo journalctl -u squid -fUser Authentication Configuration
Many environments require user authentication for proxy access. Squid supports various authentication methods, with basic HTTP authentication being the most common for small to medium deployments.
Install the Apache utilities package, which provides the htpasswd tool for managing password files:
sudo dnf install httpd-tools -yCreate a password file for Squid users:
sudo touch /etc/squid/squid_passwd
sudo chown squid:squid /etc/squid/squid_passwd
sudo chmod 640 /etc/squid/squid_passwdThese commands create the password file and set appropriate ownership and permissions. The squid user must be able to read this file, but other users should not have access to the password hashes.
Add users to the password file using htpasswd:
sudo htpasswd /etc/squid/squid_passwd username1You’ll be prompted to enter and confirm a password for the user. Repeat this process for additional users:
sudo htpasswd /etc/squid/squid_passwd username2Configure Squid to use basic authentication by adding these lines to /etc/squid/squid.conf:
auth_param basic program /usr/lib64/squid/basic_ncsa_auth /etc/squid/squid_passwd
auth_param basic children 5 startup=5 idle=1
auth_param basic realm Squid Proxy Server
auth_param basic credentialsttl 2 hoursCreate an ACL for authenticated users:
acl authenticated_users proxy_auth REQUIREDModify the access rules to require authentication:
http_access allow authenticated_users
http_access deny allSave the configuration file and restart Squid:
sudo systemctl restart squidTest authentication by configuring a browser to use your proxy and attempting to access a website. The browser should prompt for credentials.
Security Configuration and Access Control
Proper security configuration protects your proxy server from unauthorized access and potential abuse. Fedora 42’s firewall requires explicit configuration to allow proxy connections.
Configure the firewall to allow Squid traffic:
sudo firewall-cmd --permanent --add-port=3128/tcp
sudo firewall-cmd --reloadVerify the firewall rule:
sudo firewall-cmd --list-portsImplement additional ACL rules for enhanced security. Define safe ports that clients are allowed to connect to:
acl Safe_ports port 80 # HTTP
acl Safe_ports port 21 # FTP
acl Safe_ports port 443 # HTTPS
acl Safe_ports port 70 # Gopher
acl Safe_ports port 210 # WAIS
acl Safe_ports port 1025-65535 # Unregistered ports
acl Safe_ports port 280 # HTTP-MGMT
acl Safe_ports port 488 # GSS-HTTP
acl Safe_ports port 591 # FileMaker
acl Safe_ports port 777 # Multiling HTTPDefine the CONNECT method ACL for HTTPS traffic:
acl CONNECT method CONNECTAdd security rules to deny access to unsafe ports:
http_access deny !Safe_ports
http_access deny CONNECT !Safe_portsConfigure Squid to hide client information from destination servers:
forwarded_for off
request_header_access Referer deny all
request_header_access X-Forwarded-For deny all
request_header_access Via deny all
request_header_access Cache-Control deny allThese settings enhance privacy by preventing destination servers from identifying proxy usage and client information.
Implement time-based access controls if needed:
acl business_hours time MTWHF 08:00-17:00
http_access allow authenticated_users business_hoursThis example restricts access to business hours on weekdays.
Testing and Verification Procedures
Thorough testing ensures your Squid installation functions correctly and meets security requirements. Begin with command-line testing using curl:
curl -x http://localhost:3128 http://www.example.comIf authentication is configured, include credentials:
curl -x http://username:password@localhost:3128 http://www.example.comTest HTTPS connections:
curl -x http://localhost:3128 https://www.example.comMonitor Squid access logs during testing:
sudo tail -f /var/log/squid/access.logThe access log shows detailed information about each request, including client IP, request method, URL, response code, and data transfer amounts.
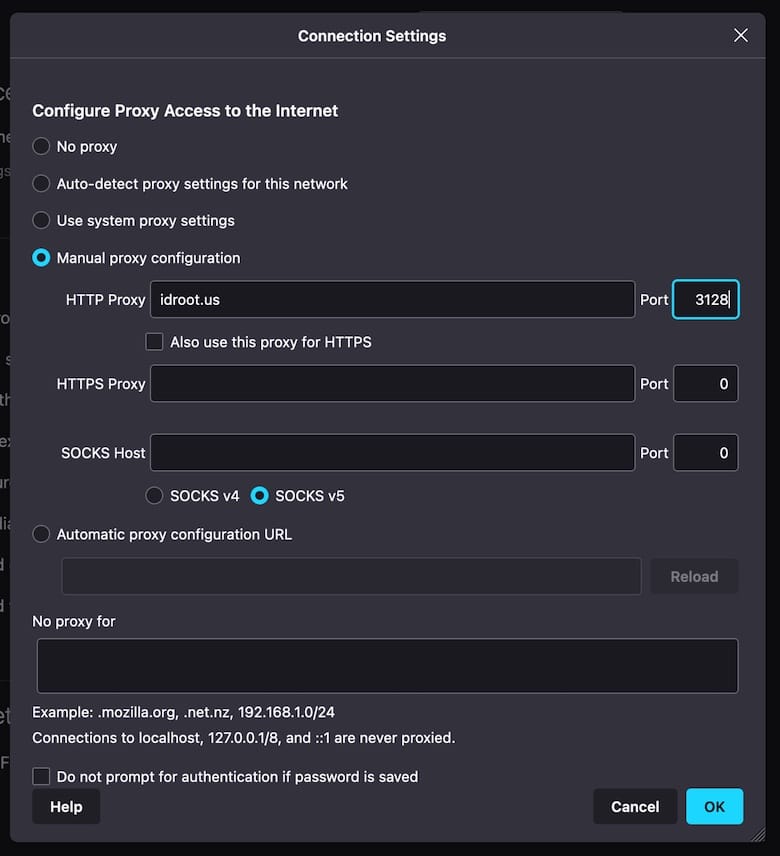
Configure web browsers for comprehensive testing. In Firefox, navigate to Settings > General > Network Settings and configure manual proxy settings:
- HTTP Proxy: your-server-ip
- Port: 3128
- Use this proxy server for all protocols (check this box)
Test various websites to ensure proper functionality. Verify that both HTTP and HTTPS sites load correctly. If authentication is configured, browsers should prompt for credentials.
Test from multiple client devices to verify network connectivity and access controls. Mobile devices provide additional testing scenarios and help identify potential compatibility issues.
Troubleshooting Common Installation Issues
Squid installation and configuration can encounter various issues. Understanding common problems and their solutions streamlines the deployment process.
Service startup failures often result from configuration syntax errors. Check the Squid error log:
sudo tail -f /var/log/squid/cache.logConfiguration syntax errors appear in this log with specific line numbers and error descriptions. Use the syntax checker to identify problems:
sudo squid -k parsePermission issues frequently prevent Squid from accessing configuration files or cache directories. Verify file ownership:
sudo ls -la /etc/squid/
sudo ls -la /var/spool/squid/Correct ownership problems:
sudo chown -R squid:squid /var/spool/squid/
sudo chown squid:squid /etc/squid/squid_passwdPort conflicts occur when another service uses port 3128. Identify conflicting processes:
sudo ss -antpl | grep :3128Either stop the conflicting service or configure Squid to use an alternative port.
Authentication failures require careful verification of password file configuration. Test the authentication helper manually:
echo "username password" | /usr/lib64/squid/basic_ncsa_auth /etc/squid/squid_passwdThis command should return “OK” for valid credentials or “ERR” for invalid ones.
DNS resolution problems can prevent Squid from connecting to destination servers. Test DNS functionality:
nslookup www.example.comConfigure alternative DNS servers in /etc/squid/squid.conf if needed:
dns_nameservers 8.8.8.8 8.8.4.4Cache directory initialization issues require manual cache creation:
sudo squid -zThis command initializes the cache directory structure.
Advanced Configuration and Optimization
Advanced Squid configurations unlock powerful features for enterprise environments. Cache management optimization significantly impacts performance and storage utilization.
Configure cache directories with appropriate sizing:
cache_dir ufs /var/spool/squid 1000 16 256This configuration creates a 1GB cache using the UFS storage scheme with optimized directory structure.
Implement cache object size limits:
maximum_object_size 100 MB
minimum_object_size 0 KBConfigure memory usage parameters:
cache_mem 256 MB
maximum_object_size_in_memory 512 KBThese settings balance memory usage with performance, keeping frequently accessed small objects in RAM.
Enable access logging with custom formats:
access_log daemon:/var/log/squid/access.log squidImplement bandwidth limitations:
delay_pools 1
delay_class 1 2
delay_access 1 allow all
delay_parameters 1 -1/-1 8000/8000This configuration limits individual client connections to 8KB/s while allowing unlimited aggregate bandwidth.
Configure parent proxy relationships for hierarchical deployments:
cache_peer parent.proxy.com parent 3128 0 no-query default
never_direct allow allIntegrate with external authentication systems using LDAP:
auth_param basic program /usr/lib64/squid/basic_ldap_auth -R -b "dc=company,dc=com" -D "cn=squid,dc=company,dc=com" -w password -f sAMAccountName=%s -h ldap.company.comPerformance Monitoring and Maintenance
Regular monitoring ensures optimal Squid performance and identifies potential issues before they impact users. Implement comprehensive monitoring procedures to track key performance indicators.
Monitor resource usage regularly:
sudo systemctl status squidCheck memory and CPU utilization:
top -p $(pgrep squid)Analyze cache statistics using Squid’s built-in reporting:
sudo squidclient -h localhost -p 3128 mgr:infoThis command displays detailed statistics including cache hit rates, object counts, and performance metrics.
Configure log rotation to prevent disk space issues:
sudo nano /etc/logrotate.d/squidAdd appropriate rotation settings:
/var/log/squid/*.log {
weekly
rotate 5
compress
notifempty
missingok
postrotate
/bin/systemctl reload squid > /dev/null 2>&1 || true
endscript
}Schedule regular cache maintenance:
sudo crontab -eAdd entries for automated maintenance tasks:
0 2 * * * /usr/sbin/squid -k rotate
0 3 * * 0 /usr/sbin/squid -k reconfigureMonitor disk space usage for cache directories:
df -h /var/spool/squidImplement capacity planning by tracking cache growth rates and client usage patterns. This data helps determine when hardware upgrades or configuration adjustments are necessary.
Congratulations! You have successfully installed Squid proxy. Thanks for using this tutorial for installing the Squid Proxy Cache on your Fedora 42 Linux system. For additional Apache or useful information, we recommend you check the official Squid Proxy website.