How To Install Tor Browser on Fedora 42

In today’s digital age, online privacy has become increasingly crucial. With rising surveillance, data breaches, and tracking concerns, many users are turning to privacy-focused tools to protect their digital footprint. Tor Browser stands out as one of the most powerful solutions for maintaining anonymity online, and pairing it with Fedora 42’s security-focused environment creates an excellent combination for privacy-conscious users.
This comprehensive guide will walk you through various methods of installing Tor Browser on Fedora 42, from the simplest approaches suitable for beginners to more advanced options for users who require complete control over their installation. Whether you’re a journalist protecting sources, an activist avoiding censorship, or simply someone who values privacy, this guide has you covered.
Understanding Tor Browser
Tor Browser is far more than just another web browser—it’s a powerful privacy tool built on Mozilla Firefox that protects your online identity through a sophisticated network of relays. When you browse the internet using Tor, your traffic is encrypted in multiple layers and routed through at least three different servers (relays) operated by volunteers worldwide.
This layered encryption approach (called “onion routing”) means that no single relay knows both the origin and destination of your data. The first relay sees your IP address but not your destination, while the exit relay sees the destination but not your originating IP address. This separation provides strong anonymity protection against tracking and surveillance.
Key features that make Tor Browser valuable include:
- Circuit isolation: Creates different paths through the network for different websites
- Tracking protection: Blocks trackers and prevents fingerprinting techniques
- Fingerprinting resistance: Makes all Tor users look identical to websites
- Security enhancements: NoScript and other privacy extensions built-in
While Tor Browser offers exceptional privacy benefits, it does come with some trade-offs. Browsing speeds can be noticeably slower due to the multi-relay routing system. Additionally, some websites block Tor exit nodes or require CAPTCHAs to prevent abuse.
Preparing Your Fedora 42 System
Before installing Tor Browser, it’s important to ensure your Fedora 42 system is properly prepared. Make sure your system is up-to-date by running:
sudo dnf updateThis command refreshes your package repositories and upgrades all installed packages to their latest versions. Having an updated system ensures you have the latest security patches and necessary dependencies for Tor Browser to function correctly.
Verify your internet connection is working properly:
ping -c 4 google.comIf you receive responses, your connection is functional. If not, troubleshoot your network issues before proceeding with installation.
Installation Method 1: Using DNF Package Manager
The simplest and most straightforward method to install Tor Browser on Fedora 42 is through DNF, Fedora’s native package manager. This approach integrates Tor Browser seamlessly with your system and allows for easy updates through Fedora’s standard update mechanism.
To install Tor Browser using DNF, open a terminal and execute:
sudo dnf install torbrowser-launcherWhen prompted, type ‘y’ to confirm the installation. DNF will automatically handle downloading the package and all necessary dependencies. The installation typically completes within a minute or two, depending on your internet speed.
It’s important to understand that torbrowser-launcher is not the browser itself but a tool that downloads, verifies, and installs the official Tor Browser from the Tor Project. This approach ensures you receive an authentic version directly from the official source.
After installation completes, you can launch Tor Browser for the first time by:
- Searching for “Tor Browser” in your applications menu
- Running
torbrowser-launcherin terminal
On first launch, the launcher will download the actual Tor Browser package, verify its cryptographic signature, and set up the browser. This verification process is crucial as it confirms that the browser hasn’t been tampered with.
The primary advantages of this installation method include:
- Simple one-command installation process
- Integration with Fedora’s update system
- Automatic signature verification
- Straightforward access through application menu
Installation Method 2: Using Fedora Software Center
For users who prefer graphical interfaces over command-line operations, installing Tor Browser through Fedora’s Software Center provides a user-friendly alternative. This approach offers the same end result as the DNF method but with a point-and-click experience.
To install using Software Center:
- Open the Software application from your application menu
- Search for “Tor Browser” in the search bar
- Click on “Tor Browser Launcher” from the results
- Click the “Install” button and enter your password when prompted
- Wait for the installation to complete
Behind the scenes, the Software Center is using the same DNF package manager discussed in Method 1, but with a graphical interface. You’re still installing the official torbrowser-launcher package from Fedora’s repositories.
After installation, you’ll find Tor Browser in your applications menu. When launched for the first time, it will download and verify the actual Tor Browser exactly as in Method 1.
This method is particularly beneficial for:
- New Linux users unfamiliar with terminal commands
- Those who prefer visual interfaces for software management
- Users who want to browse available software categories visually
Installation Method 3: Official Tor Project Download
For users who want the most current version directly from the source, installing Tor Browser from the official Tor Project website provides maximum control and ensures you have the very latest release.
Here’s a detailed walkthrough:
- Open your regular browser and navigate to the official Tor browser download page.
- Click the “Download for Linux” button
- Save the .tar.xz file to your Downloads folder
For security purposes, verifying the downloaded file’s signature is strongly recommended:
- Download the signature file (.asc extension) from the same page
- Import the Tor Project’s GPG key:
gpg --auto-key-locate nodefault,wkd --locate-keys torproject@torproject.org - Verify the signature:
gpg --verify tor-browser-linux64-*.tar.xz.asc tor-browser-linux64-*.tar.xz - Look for “Good signature from ‘Tor Browser Developers'” in the output
After verification, extract the archive:
cd ~/Downloads
tar -xf tor-browser-linux64-*.tar.xzThis creates a tor-browser directory containing all necessary files. To make Tor Browser easily accessible:
- Move to the extracted directory:
cd tor-browser - Register it as a desktop application:
./start-tor-browser.desktop --register-app
This registers Tor Browser with your desktop environment, creating a shortcut in your applications menu. You can now launch Tor Browser from your applications menu or by running the start script directly.
The main advantages of this method include:
- Always getting the latest version directly from the Tor Project
- Complete control over the installation location
- No dependency on repository availability
- Direct verification with the developers’ cryptographic keys
Installation Method 4: Using Flatpak
Flatpak is a modern package format that provides enhanced security through sandboxing while ensuring compatibility across different Linux distributions. Installing Tor Browser via Flatpak offers additional protection by isolating the application from your system.
First, ensure Flatpak is installed on your Fedora 42 system (it should be by default):
sudo dnf install flatpakNext, add the Flathub repository if you haven’t already:
flatpak remote-add --if-not-exists flathub https://flathub.org/repo/flathub.flatpakrepoNow, install Tor Browser with:
flatpak install flathub com.github.micahflee.torbrowser-launcherAfter installation completes, you can launch Tor Browser either from your applications menu or by running:
flatpak run com.github.micahflee.torbrowser-launcherThe Flatpak version runs in a sandbox, which provides additional security benefits particularly relevant for privacy-focused applications like Tor Browser. This sandbox restricts what the application can access on your system, limiting potential attack vectors.
Advantages of using Flatpak include:
- Enhanced security through sandboxing
- No system dependency conflicts
- Same version works across different Linux distributions
- Easy updates through Flatpak’s update mechanism
Installation Method 5: Using COPR Repository
COPR (Cool Other Package Repositories) are community-maintained repositories that often provide specialized versions of software. For Tor Browser, certain COPR repositories offer enhanced installers with additional features.
To install Tor Browser using a COPR repository:
- Enable a specialized Tor Browser COPR repository:
sudo dnf copr enable youssefmsourani/linux-tor-browser-installer - Install the Tor Browser installer:
sudo dnf install linux-tor-browser-installer - Launch the installer from your applications menu or by running
linux-tor-browser-installerin terminal
This specialized installer offers a more guided experience with additional configuration options during installation. It’s particularly helpful for users wanting more control over their Tor Browser setup.
The main benefits of this method include:
- Enhanced installer with more configuration options
- Often more up-to-date than main repository versions
- Additional features and customizations
However, be aware that third-party repositories might not receive the same level of scrutiny as official ones, which could potentially introduce security risks.
Post-Installation Configuration
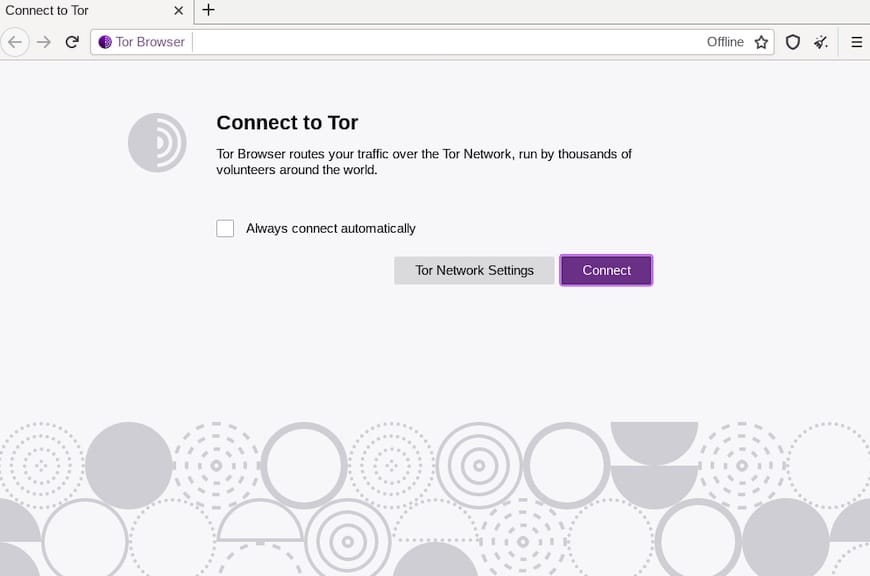
After successfully installing Tor Browser using any of the methods above, proper configuration is essential for optimal security and performance. When you first launch Tor Browser, you’ll see a connection screen with several options.
The default “Connect” option is sufficient for most users and will establish a direct connection to the Tor network. For users in countries with restricted internet or where Tor access is blocked, the “Configure” option allows you to set up bridges.
To configure bridges:
- Click “Configure” instead of “Connect”
- Select “Tor is blocked or censored in my location”
- Choose between built-in bridges or custom bridges
- Follow the prompts to complete the setup
After connecting to the Tor network, verify your connection is working correctly by visiting https://check.torproject.org. If everything is set up correctly, you’ll see a message confirming you’re connected to the Tor network.
For optimal privacy, adjust the security level in Tor Browser:
- Click on the shield icon in the toolbar
- Click “Advanced Security Settings”
- Choose your preferred security level:
- Standard: Basic protection with full website functionality
- Safer: Disables potentially dangerous features
- Safest: Maximum security with minimal website functionality
Enhancing Tor Security on Fedora
While Tor Browser provides excellent privacy protection out of the box, combining it with Fedora 42’s security features can further enhance your privacy and security.
Consider these Fedora-specific security enhancements:
- Configure the firewall to only allow Tor traffic:
sudo firewall-cmd --permanent --add-service=tor sudo firewall-cmd --reload - Use SELinux to confine Tor Browser:SELinux is enabled by default on Fedora and helps contain potential security breaches. Ensure it remains in enforcing mode:
sudo sestatus - Consider running Tor Browser in a separate user account dedicated only to Tor usage to further isolate your anonymous browsing.
- Avoid using a VPN with Tor unless you fully understand the implications. While it might seem like added protection, a VPN can sometimes reduce your anonymity by creating a permanent entry point to the Tor network.
Troubleshooting Common Issues
Even with careful installation, you might encounter issues with Tor Browser on Fedora 42. Here are solutions for common problems:
Connection Problems
If you can’t connect to the Tor network:
- Check your internet connection with a regular browser
- Verify your system time is accurate – Tor relies on accurate time for security certificates:
sudo dnf install chrony sudo systemctl enable --now chronyd - Try using bridges as your network might be blocking Tor connections
“Address Already in Use” Errors
If you see an error message about port 9050 or 9150 being in use:
- Check if another Tor process is running:
ps aux | grep tor - Stop conflicting processes:
sudo kill [process_id]
Permission Issues
If you encounter permission problems:
- For the official download method, ensure you have proper permissions:
chmod -R u+x ~/tor-browser - For Flatpak installations, reset permissions:
flatpak permission-reset com.github.micahflee.torbrowser-launcher
SELinux Related Problems
Fedora’s SELinux might restrict Tor Browser’s activities:
- Check for SELinux denials:
sudo ausearch -m avc -ts recent - Create a custom policy for Tor Browser or temporarily set SELinux to permissive mode for testing:
sudo setenforce 0 # Return to enforcing with sudo setenforce 1
Slow Connection Speeds
If Tor Browser is extremely slow:
- Try a new circuit: Click on the padlock icon next to the address bar, then “New Circuit for this Site”
- Restart Tor Browser completely
- Consider using a different bridge if you’re currently using one
Keeping Tor Browser Updated
Regular updates are crucial for security. How you update Tor Browser depends on your installation method:
For DNF Installation:
sudo dnf update torbrowser-launcherThen launch Tor Browser normally, and it will check for and download any browser updates.
For Flatpak Installation:
flatpak update com.github.micahflee.torbrowser-launcherFor Official Download Installation:
- Tor Browser will check for updates automatically when launched
- When prompted, click “Update” to download and install the new version
- Alternatively, download the latest version manually and replace your existing installation
Updates are crucial because they often contain security fixes for vulnerabilities that could compromise your anonymity. Ideally, update Tor Browser as soon as new versions are released. The Tor Project typically releases updates every few weeks, with more frequent updates when critical security issues are discovered.
Be aware that repository versions (DNF, Flatpak, COPR) might lag behind the official release by a few days while packagers verify and integrate the new version.
Congratulations! You have successfully installed Tor Browser. Thanks for using this tutorial for installing the Tor Browser on your Fedora 42 Linux system. For additional help or useful information, we recommend you check the official Tor Browser website.