How To Install VeraCrypt on CentOS Stream 10

In today’s digital landscape, securing sensitive data is no longer optional but essential for both individuals and organizations. VeraCrypt stands out as one of the most reliable open-source disk encryption solutions available for Linux users. This comprehensive guide focuses specifically on installing and configuring VeraCrypt on CentOS Stream 10, providing you with the knowledge to protect your valuable data effectively.
Understanding CentOS Stream 10
CentOS Stream 10, codenamed “Coughlan,” represents the latest iteration in the CentOS family, positioned as the upstream development platform for Red Hat Enterprise Linux (RHEL). Released as the successor to CentOS Stream 9, this version brings significant enhancements and features that make it a robust choice for enterprise environments and personal use alike.
CentOS Stream 10 introduces several notable improvements, including Kernel 6.12 which offers enhanced hardware support and security features. The distribution comes with updated programming language support and desktop technologies that provide a more modern computing experience. Its architecture is built around three main repositories: BaseOS (for core OS components), AppStream (for applications and utilities), and CRB (Code Ready Builder, for development tools).
The distribution supports multiple architectures including AMD/Intel 64-bit (x86_64_v3), ARM 64-bit, IBM Power, and IBM Z, making it versatile across different hardware platforms. Package management in CentOS Stream 10 is handled by DNF 4.20 and RPM 4.19, offering efficient software installation and management capabilities. With maintenance promised until 2030, CentOS Stream 10 provides a stable and long-term platform for your encryption needs.
What is VeraCrypt and Why Use It
VeraCrypt emerged as the spiritual successor to TrueCrypt after the latter was discontinued. It has since established itself as a leading disk encryption solution with continuous development and security improvements. As a cross-platform, open-source encryption tool, VeraCrypt offers robust protection for your sensitive data across various operating systems.
The core functionality of VeraCrypt revolves around on-the-fly encryption, meaning files are automatically encrypted or decrypted as they are loaded or saved. This seamless operation ensures your data remains protected without sacrificing usability. One of VeraCrypt’s standout features is its support for hidden volumes, providing plausible deniability in situations where you might be forced to reveal your encryption password.
VeraCrypt employs multiple strong encryption algorithms including AES, Serpent, and Twofish, which can be used individually or in cascading combinations for enhanced security. This flexibility allows users to balance security needs with performance considerations based on their specific requirements.
For CentOS Stream 10 users, VeraCrypt offers an ideal solution for protecting sensitive data in enterprise environments, securing personal information, or meeting compliance requirements for data protection. Its ability to create encrypted containers, partition encryption, and full disk encryption makes it versatile for various security scenarios.
Prerequisites for Installation
Before proceeding with VeraCrypt installation on CentOS Stream 10, ensure your system meets the necessary requirements and has the appropriate environment configured:
System Requirements:
- CentOS Stream 10 (64-bit recommended for optimal performance)
- At least 100MB of free disk space for the VeraCrypt installation
- Minimum 2GB RAM (4GB or more recommended for creating and working with large encrypted volumes)
- Admin privileges or sudo access for installation
Required Dependencies:
- Basic development tools (for compilation if installing from source)
- FUSE (Filesystem in Userspace) libraries for mounting encrypted volumes
- wxGTK libraries for the graphical user interface
Before installation, it’s advisable to update your system to ensure all packages are current:
sudo dnf updateCheck for any existing encryption software that might conflict with VeraCrypt or cause system instability when used simultaneously. While not strictly necessary, backing up your important data before working with any encryption software is always a prudent measure.
Verify that your user account has sudo privileges by running:
sudo whoamiIf this command returns your username, you have the necessary permissions to proceed with the installation.
Method 1: Installing VeraCrypt Using RPM Package
Installing VeraCrypt via RPM is the most straightforward method for CentOS Stream 10 users. This approach leverages the native package management system and ensures proper integration with your operating system.
Step 1: Download the VeraCrypt RPM Package
First, visit the official VeraCrypt website to obtain the latest RPM package compatible with CentOS Stream 10. Since CentOS Stream 10 is relatively new, you might need to use a package designed for RHEL or CentOS 8/9 and adapt as necessary.
You can download the package using wget:
wget https://launchpad.net/veracrypt/trunk/1.26.20/+download/veracrypt-1.26.20-CentOS-8-x86_64.rpm -O /tmp/veracrypt-1.26.20-CentOS-8-x86_64.rpmNote: Replace “latest-version” with the actual version number available at the time of installation.
Step 2: Verify Package Integrity
It’s crucial to verify the integrity of security software before installation. VeraCrypt provides PGP signatures for their packages:
wget https://www.idrix.fr/VeraCrypt/VeraCrypt_PGP_public_key.asc
gpg --import VeraCrypt_PGP_public_key.asc
gpg --verify /tmp/veracrypt-1.26.20-CentOS-8-x86_64.rpm.sig /tmp/veracrypt-1.26.20-CentOS-8-x86_64.rpmStep 3: Install the RPM Package
Now that you’ve verified the package, install it using the DNF package manager:
sudo dnf install /tmp/veracrypt-1.26.20-CentOS-8-x86_64.rpmDNF will automatically resolve and install any dependencies required by VeraCrypt. If you encounter any dependency issues, you can install them manually:
sudo dnf install fuse-libs wxGTK3Step 4: Verify Installation
After installation completes, verify that VeraCrypt was installed correctly:
veracrypt --versionThis command should display the installed version number. You can also check if the graphical interface launches properly:
veracrypt &If you encounter any permission issues or errors at this stage, it might be necessary to adjust your system’s security settings or install additional dependencies.
Method 2: Installing VeraCrypt via Script
For a more automated approach, especially useful for system administrators deploying VeraCrypt across multiple systems, a script-based installation provides efficiency and consistency.
Step 1: Create the Installation Script
Create a new file named veracrypt-installer.sh using your preferred text editor:
nano veracrypt-installer.shAdd the following content to the script:
#!/bin/bash
TEAM="$1"
function check_latest_version() {
# Get latest version from VeraCrypt website
LATEST_VERSION=$(curl -s https://www.veracrypt.fr/en/Downloads.html | grep -o 'VeraCrypt_[0-9.]*' | sort -u | head -n 1 | cut -d'_' -f2)
echo "Latest VeraCrypt version: $LATEST_VERSION"
# Check installed version if VeraCrypt is already installed
if command -v veracrypt >/dev/null 2>&1; then
INSTALLED_VERSION=$(veracrypt --version | grep -o '[0-9.]*')
echo "Installed VeraCrypt version: $INSTALLED_VERSION"
else
echo "VeraCrypt is not installed on this system."
fi
}
function install_veracrypt() {
# Get latest version
LATEST_VERSION=$(curl -s https://www.veracrypt.fr/en/Downloads.html | grep -o 'VeraCrypt_[0-9.]*' | sort -u | head -n 1 | cut -d'_' -f2)
# Create temporary directory
mkdir -p /tmp/veracrypt-installer
cd /tmp/veracrypt-installer
# Download appropriate package
echo "Downloading VeraCrypt $LATEST_VERSION..."
wget -q "https://launchpad.net/veracrypt/trunk/$LATEST_VERSION/+download/veracrypt-$LATEST_VERSION-CentOS-x86_64.rpm"
# Install VeraCrypt
echo "Installing VeraCrypt..."
sudo dnf install -y "./veracrypt-$LATEST_VERSION-CentOS-x86_64.rpm"
# Cleanup
cd ~
rm -rf /tmp/veracrypt-installer
echo "VeraCrypt $LATEST_VERSION has been installed successfully!"
}
function uninstall_veracrypt() {
echo "Uninstalling VeraCrypt..."
sudo dnf remove -y veracrypt
echo "VeraCrypt has been uninstalled."
}
# Main script execution
case "$TEAM" in
"install")
install_veracrypt
;;
"uninstall")
uninstall_veracrypt
;;
"check")
check_latest_version
;;
*)
echo "Usage: $0 [TEAM]"
echo " TEAM options:"
echo " install - Install the latest version of VeraCrypt"
echo " uninstall - Remove VeraCrypt from your system"
echo " check - Check the latest available and installed VeraCrypt versions"
;;
esacStep 2: Make the Script Executable
Change the permissions to make the script executable:
chmod +x veracrypt-installer.shStep 3: Run the Installation Script
Execute the script to install VeraCrypt:
./veracrypt-installer.sh installThe script will automatically determine the latest version of VeraCrypt, download it from the official source, and handle the installation process. This approach is particularly useful for automated deployments or when you need to regularly update VeraCrypt to the latest version.
Step 4: Verify the Installation
After the script completes, verify that VeraCrypt was installed correctly:
./veracrypt-installer.sh checkThis command will display both the latest available version and the installed version of VeraCrypt, confirming a successful installation.
Method 3: Building VeraCrypt from Source
Compiling VeraCrypt from source provides the greatest flexibility and ensures compatibility with your specific CentOS Stream 10 configuration. This method is particularly useful for advanced users who require customization options or when pre-built packages are not available.
Step 1: Install Required Build Dependencies
Before compiling, you’ll need to install several development tools and libraries:
sudo dnf install -y git make gcc-c++ yasm pkg-config fuse-devel wxGTK3-devel pcsclite-develStep 2: Download VeraCrypt Source Code
Clone the official VeraCrypt repository from GitHub:
git clone https://github.com/veracrypt/VeraCrypt.git
cd VeraCrypt/srcStep 3: Compile VeraCrypt
Start the compilation process with the make command:
makeFor a console-only version without the GUI, you can use:
make NOGUI=1If you prefer a statically linked version with wxWidgets, first download the wxWidgets source and then compile with:
make WXSTATIC=1 WX_ROOT=/path/to/wxWidgetsSources wxbuild
make WXSTATIC=1 WX_ROOT=/path/to/wxWidgetsSourcesStep 4: Install the Compiled Package
After successful compilation, install VeraCrypt:
sudo make installThis command will install the VeraCrypt binary and necessary files to the appropriate system directories.
Step 5: Verify the Installation
Verify that the installation was successful:
veracrypt --versionBuilding from source gives you the advantage of having the latest features and security patches, even before they’re available in pre-packaged formats. It also allows for customization of build options to suit specific requirements or hardware configurations.
Initial VeraCrypt Configuration
After successfully installing VeraCrypt on your CentOS Stream 10 system, the next step is configuring it for optimal use. This initial setup ensures that VeraCrypt operates securely and according to your specific needs.
First-Time Launch
Launch VeraCrypt either from the applications menu or by typing veracrypt in the terminal. Upon first launch, you might see a welcome dialog providing basic information about the software. Take a moment to review this information as it contains important notes about security practices.
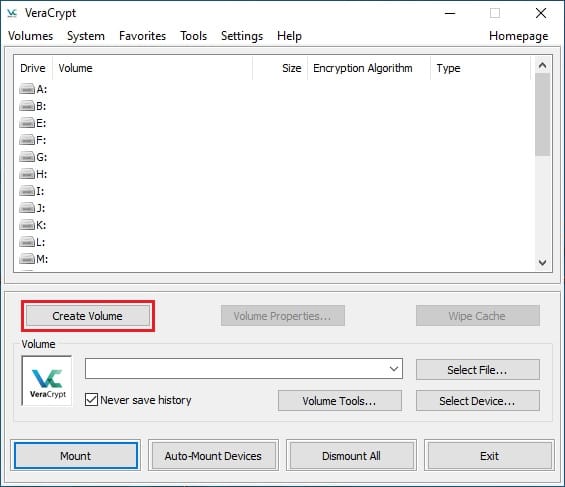
Understanding the Interface
The VeraCrypt main window consists of several key components:
- Drive selection list at the top (showing slots where encrypted volumes can be mounted)
- Button panel for operations like “Create Volume,” “Mount,” and “Dismount”
- Volume selection and password entry fields
- Status area showing mounted volumes and their properties
Familiarize yourself with these elements as they’ll be essential for your daily interaction with VeraCrypt.
Configuring Preferences
Access the preferences dialog by navigating to “Settings” > “Preferences” in the menu. Here, you can customize various aspects of VeraCrypt’s behavior:
- Security: Configure auto-dismount options, which automatically unmount volumes after a period of inactivity or when the system enters sleep mode
- Mount Options: Set default mount parameters and filesystem preferences
- Performance: Adjust cache settings for optimal performance on your hardware
- File System: Configure how VeraCrypt interacts with different file systems
For CentOS Stream 10, it’s particularly important to properly configure the FUSE options if you’re experiencing any mounting issues. You might need to ensure that your user has the proper permissions to use FUSE devices.
Running VeraCrypt with Elevated Privileges
Some operations in VeraCrypt require elevated privileges. You can launch VeraCrypt with sudo for these operations:
sudo veracryptHowever, this approach can sometimes lead to permission issues with files created within mounted volumes. A better practice is to configure PolicyKit to allow VeraCrypt to perform privileged operations without requiring full root access for the application.
Creating Your First Encrypted Volume
Creating an encrypted volume is the essential first step to securing your data with VeraCrypt. CentOS Stream 10 provides a stable platform for this process, and the following steps will guide you through creating a secure container for your sensitive files.
Step 1: Launch Volume Creation Wizard
Open VeraCrypt and click on “Create Volume” to start the Volume Creation Wizard. This will guide you through the entire process of creating an encrypted container.
Step 2: Choose Volume Type
Select “Create an encrypted file container” if you want to create a portable encrypted file that can be moved between systems. Alternatively, choose “Encrypt a non-system partition/drive” if you want to encrypt an entire partition or USB drive.
Step 3: Select Volume Type
Choose between a “Standard VeraCrypt volume” or a “Hidden VeraCrypt volume.” The standard option creates a regular encrypted container, while the hidden option creates a container with plausible deniability-a feature that allows you to have two separate encrypted areas with different passwords.
Step 4: Specify Volume Location
Click “Select File” to choose where your encrypted container will be saved and what it will be named. Remember not to select an existing file as it will be overwritten.
Step 5: Encryption Options
Select your preferred encryption algorithm. AES (Advanced Encryption Standard) is recommended for most users due to its balance of security and performance. For the hash algorithm, SHA-512 provides excellent security.
VeraCrypt offers various encryption algorithms:
- AES: Fast and secure, suitable for most users
- Serpent: Slower but potentially more secure against certain attacks
- Twofish: A good balance between AES and Serpent
- Combinations (e.g., AES-Twofish-Serpent): Maximum security but slower performance
Step 6: Volume Size
Specify the size of your encrypted container. Consider your storage needs carefully, as this cannot be easily changed later without creating a new container.
Step 7: Volume Password
Create a strong password for your volume. A strong password should:
- Be at least 20 characters long
- Include a mix of uppercase and lowercase letters, numbers, and special characters
- Not contain personal information or dictionary words
- Be unique and not used for other services
You can optionally use keyfiles as an additional security layer. Keyfiles are regular files that function as physical keys-without the correct keyfile, the volume cannot be mounted even with the correct password.
Step 8: Format Options
Choose the filesystem format for your volume. For CentOS Stream 10, ext4 is recommended for containers that will only be used in Linux environments. Use FAT if you need cross-platform compatibility with Windows systems.
Step 9: Volume Generation
VeraCrypt will now create your encrypted volume. Move your mouse randomly within the window to generate cryptographic entropy, which improves the randomness and security of your encryption keys.
Step 10: Completion
Once the process completes, your encrypted volume is ready to use. To mount it, return to the main VeraCrypt window, select a slot, choose your volume file, enter your password, and click “Mount.”
Advanced Usage Features
VeraCrypt offers several advanced features that provide enhanced security and flexibility for CentOS Stream 10 users with more specialized needs.
System Encryption
While VeraCrypt supports full system encryption on Windows, this feature has limitations on Linux systems including CentOS Stream 10. You can, however, encrypt non-system partitions containing sensitive data. To do this:
- Select “Encrypt a non-system partition/drive” in the Volume Creation Wizard
- Choose the partition you want to encrypt
- Follow the standard encryption process
Note that encrypting partitions that contain system files or that are mounted at boot time requires additional configuration to ensure your system remains bootable.
Hidden Volumes
Hidden volumes provide plausible deniability-a powerful feature for situations where you might be compelled to reveal your encryption password:
- Create a standard VeraCrypt volume with decoy data
- Create a hidden volume within that standard volume
- Use different passwords for the outer and hidden volumes
When you provide the password for the standard volume, only the decoy data is accessible. The hidden volume remains invisible and can only be accessed with its specific password.
Keyfile Creation and Usage
Keyfiles add an additional layer of security by requiring both a password and a specific file to unlock your encrypted volume:
- In the VeraCrypt main window, go to “Tools” > “Keyfile Generator”
- Generate a random keyfile or select an existing file
- When creating or mounting volumes, check “Use keyfiles” and select your keyfile
Store keyfiles separately from your encrypted volumes, preferably on a removable device like a USB drive that you keep secure.
Automating Volume Mounting
For volumes you access frequently, you can create scripts to automate the mounting process:
#!/bin/bash
veracrypt --non-interactive --mount /path/to/volume.tc /media/veracrypt1 -p "password"For better security, avoid storing passwords in plain text. Instead, use the Linux keyring or a secure password manager.
To automatically mount volumes at login, add your script to the startup applications in your desktop environment, or create a systemd user service:
[Unit]
Description=Mount VeraCrypt volume
After=network.target
[Service]
Type=oneshot
ExecStart=/path/to/your/mount-script.sh
RemainAfterExit=yes
ExecStop=veracrypt -d
[Install]
WantedBy=default.targetPerformance Optimizations
To improve VeraCrypt’s performance on CentOS Stream 10:
- Use AES encryption for the best performance/security balance
- Adjust the cache size in VeraCrypt preferences
- Consider using hardware that supports AES-NI instruction set for accelerated encryption
- For frequently accessed files, consider using a RAM disk within an encrypted volume for maximum speed
Troubleshooting Common Issues
Even with careful installation and configuration, you may encounter issues when using VeraCrypt on CentOS Stream 10. Here are solutions to common problems:
Dependency Conflicts
If you encounter dependency issues during installation:
sudo dnf install --skip-broken veracrypt-latest.rpmAlternatively, identify the specific missing dependencies:
rpm -qpR veracrypt-latest.rpmThen install them manually before attempting to install VeraCrypt again.
Mounting Problems
If you have trouble mounting volumes:
1. Permission denied errors: These often occur when VeraCrypt can’t access the volume file or mount point. Ensure your user has the necessary permissions.
sudo chown yourusername:yourusername /path/to/volume.tc
sudo chmod 600 /path/to/volume.tc2. FUSE-related issues: If you encounter errors related to FUSE, verify that your user is in the ‘fuse’ group:
sudo usermod -a -G fuse yourusername3. Volume appears mounted but not accessible: This issue is often related to the mounting point. Try dismounting with:
sudo umount /media/veracrypt1And then remount using VeraCrypt.
GUI Rendering Problems
If the VeraCrypt GUI displays incorrectly or crashes:
1. Try running it with different parameters:
veracrypt --text # For text mode interface2. Verify that all required GUI libraries are installed:
sudo dnf install wxGTK3 wxBase3SELinux Conflicts
CentOS Stream 10 uses SELinux by default, which can sometimes interfere with VeraCrypt operations:
1. Check if SELinux is blocking VeraCrypt:
sudo ausearch -m avc -ts recent | grep veracrypt2. Create a custom SELinux policy for VeraCrypt or temporarily set SELinux to permissive mode:
sudo setenforce 0 # Temporary solution until rebootFor a permanent solution, consider creating a custom policy that specifically allows VeraCrypt operations.
Volume Dismounting Issues
If you can’t dismount volumes properly:
- Make sure no files on the volume are in use
- Force close any applications that might be accessing the volume
- As a last resort, use:
sudo killall veracryptRemember to always check the VeraCrypt log files for more detailed error information:
veracrypt --debugThis will provide more verbose output that can help identify the root cause of issues.
Security Best Practices
Implementing strong security practices with VeraCrypt on CentOS Stream 10 ensures your data remains protected against various threats:
Password Management
Create strong, unique passwords for each VeraCrypt volume:
- Use passwords of at least 20 characters
- Combine uppercase and lowercase letters, numbers, and special characters
- Consider using a password manager to generate and store complex passwords
- Change passwords periodically, especially for highly sensitive data
Backup Strategies
Always maintain backups of critical elements:
- Create and securely store backup header files for each volume (Tools > Backup Volume Header)
- Store backups in physically separate locations
- Test restoration procedures regularly to ensure backups are viable
- Consider encrypting your backups as well to maintain security
Regular Updates
Keep your VeraCrypt installation current:
- Check for updates monthly
- Subscribe to the VeraCrypt security mailing list for vulnerability announcements
- Update both VeraCrypt and your CentOS Stream 10 system regularly to patch security vulnerabilities
Enterprise Deployment Considerations
For organizational use of VeraCrypt:
- Implement a key escrow system to prevent data loss when employees leave
- Document encryption procedures and emergency access protocols
- Consider central management of encryption policies
- Provide training for users on proper encryption practices
Recovery Options
Plan for potential recovery scenarios:
- Keep rescue disks or USB drives with VeraCrypt portable installation
- Document recovery procedures for various failure scenarios
- Test recovery procedures periodically
- For critical data, consider implementing redundant encryption measures
Integrating with CentOS Stream 10 Specifics
CentOS Stream 10 has particular characteristics that affect how VeraCrypt operates on the system:
SELinux Considerations
SELinux provides additional security but requires proper configuration for VeraCrypt:
- Create custom SELinux policies for VeraCrypt operations
- Use
semanageto define appropriate contexts for VeraCrypt files and operations - Consider running
audit2allowto generate policies based on denied actions
Firewall Configuration
If you’re using VeraCrypt with network shares or remote volumes:
- Configure the CentOS firewall (firewalld) to allow necessary traffic
- For SMB/CIFS shares, special considerations may be needed as VeraCrypt must run as root to mount network volumes
sudo mount -t cifs //server/share /local/mountpoint -o user=username,password=passwordThen use VeraCrypt on the locally mounted share rather than directly on the network path.
Boot Process Implications
When using encrypted partitions that need to be available early in the boot process:
- Create appropriate entries in
/etc/crypttaband/etc/fstab - Consider using dracut modules if encryption must be available during early boot
- Test boot procedures thoroughly after configuration changes
UEFI/Secure Boot Considerations
CentOS Stream 10 uses UEFI and may have Secure Boot enabled:
- VeraCrypt operates at the user level and generally doesn’t conflict with Secure Boot
- For system partition encryption, additional configuration may be required
- Note that CentOS Stream 10 has some limitations with Secure Boot that may affect encryption of system partitions
Congratulations! You have successfully installed VeraCrypt. Thanks for using this tutorial for installing VeraCrypt on your CentOS Stream 10 system. For additional help or useful information, we recommend you check the official VeraCrypt website.