How To Install Wireshark on Fedora 42

Wireshark stands as one of the most powerful and widely-used network protocol analyzers available today. This open-source tool enables network administrators, security professionals, and developers to capture and analyze network traffic in real-time, providing invaluable insights into network behavior, security vulnerabilities, and performance issues. Whether you’re troubleshooting connectivity problems, examining security threats, or learning about network protocols, Wireshark offers comprehensive functionality that makes network analysis accessible and effective.
Installing Wireshark on Fedora 42 is straightforward thanks to the distribution’s robust package management system. This guide walks through every step of the installation process, from system preparation to advanced configuration. You’ll learn how to properly set up user permissions for security, launch the application, and perform your first packet capture. The article covers both the graphical user interface (GUI) and command-line interface (CLI) options, ensuring you have complete control over your network analysis environment.
What is Wireshark and Why Use It?
Wireshark is an open-source network packet analyzer that captures and displays network traffic at the packet level. Originally known as Ethereal, this tool has become the industry standard for network troubleshooting and protocol analysis. It supports over 1,000 protocols and provides deep inspection capabilities that allow you to examine every detail of network communications.
Network professionals use Wireshark for multiple purposes. Security analysts rely on it to detect intrusions, identify malware communications, and investigate security incidents. Network administrators troubleshoot connectivity issues, analyze bandwidth usage, and optimize network performance. Developers use it to debug network applications and verify protocol implementations. Educational institutions incorporate it into networking courses to help students understand how protocols work in practice.
The tool offers several key advantages. Its comprehensive protocol support means you can analyze virtually any network traffic. The intuitive interface makes complex data accessible, while powerful filtering capabilities help you focus on relevant information. Wireshark can capture live traffic from multiple interfaces or analyze previously captured files in various formats including pcap, pcapng, and many others.
System Requirements for Fedora 42
Before installing Wireshark on your Fedora 42 system, verify that your hardware meets the minimum requirements. Wireshark needs at least 500MB of RAM to run effectively, though more memory is recommended when analyzing large capture files. The application requires approximately 500MB of disk space for installation, plus additional space for storing captured packet files.
Your display should support a resolution of 1280×1024 or higher for optimal viewing of the interface. Wireshark works on 64-bit AMD64/x86-64 architectures, which covers most modern systems. For capturing network traffic, you’ll need at least one functional network interface, whether wired Ethernet, wireless, or virtual.
Fedora 42 includes Wireshark version 4.4.7 in its official repositories, ensuring you get a recent and well-maintained release. This version includes important security updates and bug fixes that enhance stability and performance. The system requirements remain modest, allowing Wireshark to run efficiently even on older hardware.
Prerequisites Before Installation
Several prerequisites must be in place before beginning the installation. You need root or sudo privileges to install packages and modify system configurations. An active internet connection is essential for downloading Wireshark and its dependencies from Fedora’s repositories.
Ensure your Fedora 42 system is up to date. Running system updates before installing new software prevents compatibility issues and ensures you have the latest security patches. Basic familiarity with the Linux command line proves helpful, as many configuration steps use terminal commands.
Understanding your system’s network interfaces helps when configuring Wireshark. Use commands like ip link or nmcli device status to view available interfaces. While not mandatory, creating a system backup before making significant changes provides peace of mind and enables recovery if issues arise.
Step 1: Update Fedora System Packages
Updating your system packages is the critical first step. This ensures compatibility between Wireshark and existing system libraries. Open a terminal and execute the following command:
sudo dnf upgrade --refreshThe --refresh flag forces DNF to download fresh repository metadata, ensuring you get the latest package information. This command updates all installed packages to their newest versions available in the configured repositories.
You’ll see DNF checking for updates and downloading package metadata. The system displays a list of packages to be updated and asks for confirmation. Type ‘y’ and press Enter to proceed. The update process typically takes several minutes depending on your internet speed and the number of packages requiring updates.
During the update, DNF automatically resolves dependencies and downloads necessary files. If any conflicts arise, DNF provides information about the issue and suggests solutions. After completing the updates, your system is ready for the Wireshark installation.
Step 2: Install Wireshark Using DNF Package Manager
Wireshark is available directly from Fedora’s AppStream repository, making installation simple and reliable. The repository includes both the graphical and command-line versions of Wireshark. Execute this command to install Wireshark:
sudo dnf install wiresharkThis command installs the complete Wireshark package, including wireshark-qt (the Qt-based GUI), wireshark-cli (command-line tools), and TShark (terminal-based packet analyzer). DNF automatically identifies and installs all required dependencies, including Qt libraries, protocol dissectors, and capture utilities.
The package manager displays the download size and installed size before proceeding. Confirm the installation by typing ‘y’ when prompted. DNF downloads the packages from Fedora’s mirrors and installs them to your system. The installation typically completes in a few minutes.
For developers who need header files and development libraries, an optional development package is available:
sudo dnf install wireshark-develThis package provides the necessary files for compiling applications that use Wireshark’s libraries. Most users don’t need this package unless they’re developing software that integrates with Wireshark.
Step 3: Verify Wireshark Installation
After installation completes, verify that Wireshark installed correctly and check the version. Run this command:
wireshark --versionThe output displays detailed version information including the Wireshark version number, build date, and supported features. For Fedora 42, you should see Wireshark 4.4.7 or a similar recent version. The output also lists compiled-in features, available plugins, and supported file formats.
Alternatively, use the short version flag:
wireshark -vTo confirm all Wireshark-related packages are installed, use:
dnf list installed | grep wiresharkThis command shows all installed packages with “wireshark” in their name, including the main package, Qt GUI components, CLI tools, and any optional packages you installed. The output confirms successful installation and helps identify which components are available on your system.
You can also verify TShark installation, the command-line packet analyzer:
tshark --versionTShark provides powerful packet capture and analysis capabilities without requiring a graphical interface, making it perfect for remote servers or automated analysis tasks.
Step 4: Configure Wireshark User Permissions
Running Wireshark as root presents significant security risks. Malicious packets could potentially exploit vulnerabilities and compromise your entire system. Fedora addresses this concern through proper permission configuration that allows regular users to capture packets safely.
During installation, DNF creates a system group named “wireshark”. Members of this group can capture network traffic without root privileges. Add your user account to this group with the following command:
sudo usermod -a -G wireshark $USERReplace $USER with your actual username if running the command for a different user. The -a flag appends the new group to the user’s existing group memberships, and -G specifies the group name.
Wireshark uses a utility called dumpcap for packet capture. This program needs special capabilities to access network interfaces. Grant these capabilities with:
sudo setcap cap_net_raw,cap_net_admin=eip /usr/bin/dumpcapThis command assigns two Linux capabilities: cap_net_raw allows raw socket access for packet capture, while cap_net_admin enables network interface administration. The =eip notation sets these capabilities as effective, inheritable, and permitted.
Group membership changes don’t take effect immediately in your current session. You must log out and log back in for the changes to apply. Alternatively, start a new shell session with your updated groups:
su - $USERVerify your group membership with:
groupsThe output should include “wireshark” among your groups. You can also use the id command for detailed user and group information:
idStep 5: Launch Wireshark
Once configuration is complete, launch Wireshark using several methods. The simplest approach from the command line is:
wiresharkThis command starts the Qt-based graphical interface. The application opens in a new window, displaying the main Wireshark interface with available network interfaces listed.
To run Wireshark in the background, allowing continued use of your terminal:
wireshark &The ampersand character runs the process in the background, returning you to the command prompt immediately.
Desktop environment users can launch Wireshark through the graphical interface. Click “Activities” in the top-left corner of your GNOME desktop. Type “wireshark” in the search box and click the Wireshark icon when it appears. This method is convenient for users who prefer graphical navigation.
For systems running in headless mode or when GUI access isn’t available, use TShark instead:
tsharkTShark provides full packet capture and analysis capabilities from the command line, making it ideal for remote servers, automated scripts, or situations where a graphical interface isn’t necessary or available.
Understanding Wireshark Interface
Wireshark’s interface uses a three-pane layout that efficiently organizes captured network data. The top pane, called the packet list, displays all captured packets in chronological order. Each row represents a single packet with columns showing key information like packet number, timestamp, source and destination addresses, protocol, and a brief description.
The middle pane, the packet details view, shows the selected packet’s protocol layers in a hierarchical tree structure. You can expand each protocol layer to examine specific fields and values. This detailed view helps you understand exactly how protocols encapsulate and process data.
The bottom pane displays the raw packet bytes in hexadecimal and ASCII formats. This view shows the actual data as it appears on the network, useful for analyzing proprietary protocols or identifying specific byte patterns.
The main toolbar provides quick access to common functions like starting and stopping captures, opening files, and applying display filters. The display filter toolbar sits prominently near the top, allowing you to filter visible packets based on complex criteria. This filtering doesn’t affect captured data; it only controls what you see.
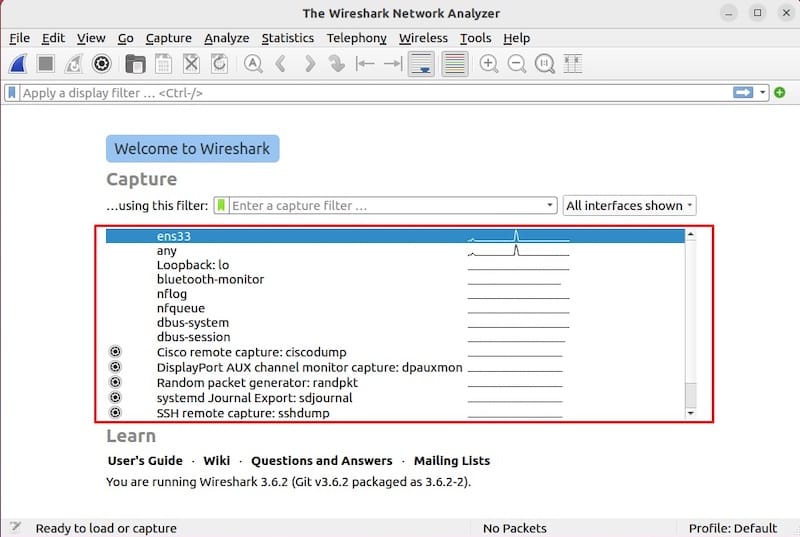
Network interface selection appears in the capture options dialog or the welcome screen. Each interface shows its name, current packet rate, and a miniature activity graph. The status bar at the bottom displays useful information about your capture, including packet counts, elapsed time, and profile information.
Performing Your First Packet Capture
Starting your first packet capture is straightforward. When you launch Wireshark, the welcome screen displays all available network interfaces. Each interface shows real-time activity indicators. Interfaces with active traffic display animated graphs, helping you identify which interface to capture.
Select your desired interface by double-clicking it or highlighting it and pressing Enter. Common interface names include “wlp3s0” for wireless adapters, “enp0s3” for Ethernet connections, and “lo” for the loopback interface. Choose the interface that carries the traffic you want to analyze.
For more control, click “Capture Options” or press Ctrl+K. This dialog provides extensive configuration options including multiple interface selection, capture filters, and buffer settings. You can specify how long to capture or how much data to collect before automatically stopping.
Click “Start” or press Enter to begin capturing. Wireshark immediately starts displaying packets in the packet list pane. You’ll see packets accumulating as network traffic flows through the selected interface. The interface remains responsive, allowing you to scroll through captured packets while capture continues.
Stop the capture by clicking the red square icon or pressing Ctrl+E. Wireshark finalizes the capture and displays the complete packet list. You can now analyze the captured traffic at your leisure.
Save your capture for later analysis or sharing with colleagues by selecting File > Save As. Choose the pcap or pcapng format for maximum compatibility. Name your file descriptively, including date and purpose, for easy organization. Wireshark can also export specific packets or filtered subsets of your capture.
Basic Wireshark Filters and Usage
Display filters are Wireshark’s most powerful feature for managing large captures. These filters determine which packets appear in the packet list without affecting the underlying captured data. The display filter toolbar accepts complex filter expressions.
Filter by IP address to focus on traffic to or from specific hosts:
ip.addr==192.168.1.1This shows all packets where either the source or destination address matches. Use ip.src or ip.dst to filter specifically on source or destination addresses.
Filter by protocol to examine specific types of traffic:
tcpThis displays only TCP packets, hiding all other protocols. Common protocol filters include udp, dns, http, https, ssh, and icmp.
Filter by port number to analyze specific services:
tcp.port==80This shows TCP traffic on port 80, typically HTTP web traffic. Use tcp.src.port or tcp.dst.port for source or destination-specific filtering.
Combine filters using logical operators. Use and (or &&) to require multiple conditions, or (or ||) for alternatives, and not (or !) for negation:
ip.addr==192.168.1.1 and tcp.port==443This displays only HTTPS traffic (port 443) to or from IP address 192.168.1.1.
Follow TCP streams to see complete conversations between hosts. Right-click any packet and select “Follow > TCP Stream”. Wireshark displays the entire conversation in a readable format, applying a filter automatically to show only packets in that stream.
Common Troubleshooting Issues
Permission Errors
The most common issue is “You don’t have permission to capture on that device” errors. This occurs when your user account lacks proper permissions. Verify group membership with the groups command. If “wireshark” doesn’t appear, add yourself to the group as described earlier and log out and back in.
Check dumpcap capabilities:
getcap /usr/bin/dumpcapThe output should show cap_net_admin,cap_net_raw=eip. If capabilities are missing, reapply them using the setcap command from the configuration section.
No Interfaces Visible
When Wireshark shows no available interfaces, verify that network interfaces are active. Use ip link show to list all interfaces and their states. Interfaces marked “DOWN” won’t appear in Wireshark. Bring interfaces up with:
sudo ip link set <interface-name> upCheck that required drivers are loaded. Some wireless adapters need specific drivers for monitor mode or packet capture. Consult your hardware documentation for driver requirements.
Boot Issues After Installation
Some users have reported boot problems after installing Wireshark on Fedora 40, potentially affecting Fedora 42 as well. This appears related to display manager configuration. If your system fails to boot after installation, access recovery mode from the GRUB menu.
Check the display manager status:
sudo systemctl status display-manager.serviceIf the service failed, review system logs for error messages:
sudo journalctl -xbReinstalling the display manager package often resolves the issue:
sudo dnf reinstall gdmUI Problems or Crashes
Display issues sometimes occur due to Qt library incompatibilities. Ensure all system libraries are current:
sudo dnf upgradeIf problems persist, try reinstalling Wireshark:
sudo dnf reinstall wireshark wireshark-qtClear Wireshark’s configuration files to reset to defaults:
rm -rf ~/.config/wiresharkThis removes your personal preferences but often resolves persistent UI issues.
Security Considerations
Packet capture capabilities present significant security implications. Wireshark can capture all network traffic on an interface, including potentially sensitive information like passwords, authentication tokens, and private communications. Understanding these risks is essential for responsible use.
Never run Wireshark as root except in emergency situations. Root privileges mean any vulnerability in Wireshark could compromise your entire system. The permission configuration described earlier provides necessary capabilities while minimizing risk through privilege separation.
Wireshark employs privilege separation architecture. The dumpcap utility performs actual packet capture with minimal elevated privileges, while the main Wireshark process runs with normal user permissions. This design limits potential damage if vulnerabilities are exploited.
Limit wireshark group membership to trusted users who need packet capture capabilities. System administrators should regularly audit group membership and remove users who no longer require access.
Consider legal and ethical implications. Capturing network traffic in many jurisdictions requires authorization. Only capture traffic on networks you own or have explicit permission to monitor. Respect privacy and confidentiality when analyzing captured data.
Protect captured files containing sensitive information. Use encryption when storing or transmitting capture files. Implement access controls to prevent unauthorized viewing. Delete capture files when analysis is complete rather than accumulating potentially sensitive data.
Updating Wireshark on Fedora 42
Regular updates are crucial for security and functionality. Fedora releases security updates promptly when vulnerabilities are discovered. Check for Wireshark updates regularly:
sudo dnf check-update wiresharkThis command queries repositories for available updates without installing them. If updates are available, the command displays version information.
Install available updates with:
sudo dnf upgrade wiresharkDNF downloads and installs the newest version, automatically handling dependencies. Alternatively, update all system packages:
sudo dnf upgradeThis comprehensive update ensures your entire system remains current with security patches and feature improvements.
View detailed information about available Wireshark versions:
dnf info wiresharkThe output shows the installed version, available version, repository source, and package description.
Fedora’s security team monitors for critical vulnerabilities. Security advisories are published through the Fedora Project security mailing list and Bugzilla. Subscribing to these resources helps you stay informed about important security updates.
DNF can be configured for automatic updates, though many administrators prefer manual control over system changes. Automatic updates ensure timely security patches but may occasionally introduce unexpected changes.
Uninstalling Wireshark (Optional)
If you need to remove Wireshark from your system, the process is straightforward. Remove the main package with:
sudo dnf remove wiresharkDNF removes Wireshark and packages that depend on it. The command prompts for confirmation before proceeding.
Remove unused dependencies that were installed for Wireshark:
sudo dnf autoremoveThis cleans up libraries and packages no longer needed by any installed software, freeing disk space.
Remove your user from the wireshark group:
sudo gpasswd -d $USER wiresharkReplace $USER with the appropriate username. This revokes packet capture permissions for the user.
Configuration files in your home directory persist after uninstallation. Remove them manually if desired:
rm -rf ~/.config/wiresharkVerify complete removal:
dnf list installed | grep wiresharkIf no packages appear, Wireshark is fully removed from your system.
Congratulations! You have successfully installed Wireshark. Thanks for using this tutorial for installing the Wireshark network analyzer on Fedora 42 Linux system. For additional help or useful information, we recommend you check the official Wireshark website.