How To Install XRDP on AlmaLinux 10

Remote desktop access has become essential for modern server management and administration. XRDP (X Remote Desktop Protocol) stands as the premier open-source solution for providing RDP server functionality on Linux systems, including AlmaLinux 10. This comprehensive guide will walk you through every aspect of installing, configuring, and optimizing XRDP on your AlmaLinux 10 server.
XRDP enables seamless remote desktop connections from any RDP-compatible client, including Windows Remote Desktop Connection, Linux-based Remmina, and macOS RDP clients. Unlike proprietary solutions, XRDP offers cross-platform compatibility while maintaining excellent performance and security standards. The protocol supports multiple desktop environments and provides encrypted connections for secure remote access.
AlmaLinux 10 represents the latest evolution of this enterprise-grade Linux distribution, offering enhanced security features, improved performance, and extended hardware support. Installing XRDP on AlmaLinux 10 creates a powerful remote desktop solution suitable for both individual users and enterprise environments.
This article covers everything from initial system preparation to advanced security hardening. You’ll learn to configure desktop environments, optimize performance, troubleshoot common issues, and implement security best practices that protect your remote desktop infrastructure.
Prerequisites and System Requirements
Before beginning the XRDP installation process, ensure your AlmaLinux 10 system meets the necessary requirements for optimal performance and functionality.
System Specifications for Optimal Performance
Your AlmaLinux 10 server should have minimum 2GB RAM for basic XRDP functionality, though 4GB or more is recommended for smooth desktop environment operation. CPU requirements vary depending on the chosen desktop environment, with dual-core processors providing adequate performance for most scenarios. Storage requirements include at least 10GB free space for desktop environment installation and XRDP components.
Network connectivity plays a crucial role in XRDP performance. Ensure stable network connections with sufficient bandwidth for remote desktop sessions. Gigabit Ethernet connections provide optimal performance for local network access, while internet connections should maintain consistent speeds for remote access scenarios.
User Privileges and Access Requirements
XRDP installation requires root privileges or sudo access for system-level modifications. Verify your user account has appropriate permissions by running sudo -l to display available sudo commands. Create dedicated user accounts for XRDP access rather than using root accounts for enhanced security.
Consider implementing user group management for XRDP access control. Create specific groups for remote desktop users and configure appropriate permissions for desktop environment access and system resource utilization.
Initial Server Setup Checklist
Verify your AlmaLinux 10 installation is current and functional. Check system status using systemctl status and ensure all essential services are running properly. Confirm SSH access is working correctly, as this provides an alternative access method during XRDP configuration.
Establish baseline security configurations including firewall settings, SELinux policies, and user account management. Document current system configurations before making changes to enable easy rollback if needed.
Preparing AlmaLinux 10 System
Proper system preparation ensures a smooth XRDP installation process and prevents potential compatibility issues.
Updating the System Packages
Begin by updating all system packages to their latest versions using the DNF package manager:
sudo dnf update -yThis command downloads and installs all available package updates, including security patches and bug fixes. The -y flag automatically confirms installation prompts, streamlining the update process.
Monitor the update process for any error messages or dependency conflicts. Large system updates may require significant time depending on your internet connection speed and the number of packages requiring updates.
Installing Essential Development Tools
Install the Development Tools group package to ensure all necessary compilation tools and libraries are available:
sudo dnf groupinstall "Development Tools" -yThis package group includes GCC compiler, make utilities, and various development libraries required for building software from source code. Some XRDP components or desktop environment packages may require these tools during installation or configuration.
Additionally, install essential system utilities:
sudo dnf install -y wget curl vim net-toolsThese utilities provide network troubleshooting capabilities, text editing tools, and download utilities that prove valuable during XRDP configuration and maintenance.
System Reboot and Verification
After completing system updates, reboot your AlmaLinux 10 server to ensure all kernel updates and system changes take effect:
sudo rebootFollowing the reboot, verify system functionality by checking service status, network connectivity, and available system resources. Use free -h to verify memory availability and df -h to check disk space utilization.
Desktop Environment Installation
XRDP requires a graphical desktop environment to provide remote desktop functionality. AlmaLinux 10 supports multiple desktop environments, each offering different features and resource requirements.
Choosing the Right Desktop Environment
GNOME Desktop Environment serves as the default choice for AlmaLinux 10, providing a modern, feature-rich desktop experience. GNOME offers excellent integration with AlmaLinux systems and provides comprehensive application support. However, GNOME requires significant system resources, making it suitable for servers with adequate RAM and CPU capacity.
XFCE Desktop Environment presents a lightweight alternative that consumes fewer system resources while maintaining functionality. XFCE is ideal for servers with limited resources or environments where performance optimization is critical. The desktop environment provides essential features without the resource overhead of more complex environments.
KDE Plasma Desktop Environment offers advanced features and extensive customization options. While resource-intensive, KDE Plasma provides excellent functionality for users requiring advanced desktop capabilities and application integration.
Installing GNOME Desktop Environment
Install the GNOME desktop environment using the “Server with GUI” package group:
sudo dnf groupinstall "Server with GUI" -yThis installation process downloads and installs hundreds of packages, requiring significant time and bandwidth. The package group includes the GNOME desktop environment, essential applications, and system integration components.
Configure the system to boot into graphical mode by default:
sudo systemctl set-default graphical.targetThis command modifies the system’s default boot target from multi-user (text mode) to graphical mode, enabling desktop environment startup during system boot.
Verify the installation by checking the default target:
sudo systemctl get-defaultThe output should display “graphical.target” confirming successful configuration.
Alternative Desktop Environment Setup
For XFCE installation, use the following commands:
sudo dnf install -y @xfce-desktop-environment
sudo dnf install -y xrdp-selinuxXFCE provides a lightweight desktop experience with lower resource requirements than GNOME. The xrdp-selinux package ensures proper SELinux integration for XFCE desktop sessions.
KDE Plasma installation requires:
sudo dnf install -y @kde-desktop-environmentEach desktop environment requires specific configuration adjustments for optimal XRDP integration, which we’ll address in later sections.
EPEL Repository Configuration
The Extra Packages for Enterprise Linux (EPEL) repository provides additional software packages not included in the standard AlmaLinux repositories, including XRDP.
Understanding EPEL Repository Importance
EPEL extends AlmaLinux package availability by providing community-maintained packages that complement the base distribution. For AlmaLinux 10, EPEL provides access to XRDP packages and related dependencies not available in standard repositories.
AlmaLinux maintains its own EPEL builds for x86_64_v2 architecture support, ensuring compatibility with older hardware while maintaining feature parity with upstream EPEL packages.
Installing and Enabling EPEL Release
Install the EPEL repository configuration:
sudo dnf install -y epel-releaseThis command adds the EPEL repository configuration to your system, enabling access to additional packages. The installation process downloads repository metadata and configures package manager settings.
Verify EPEL repository availability:
sudo dnf repolist | grep epelThe output should display active EPEL repositories, confirming successful installation and configuration.
Updating Package Cache
Refresh the DNF package cache to include newly available EPEL packages:
sudo dnf makecacheThis command downloads the latest package metadata from all configured repositories, including the newly added EPEL repository. The process ensures your system has current information about available packages and their versions.
XRDP Installation Process
With the desktop environment and EPEL repository configured, proceed with XRDP installation and initial configuration.
Installing XRDP Packages
Install XRDP and its dependencies using DNF:
sudo dnf install -y xrdpThe installation process downloads XRDP server components, session management tools, and required libraries. Additional packages may be installed automatically to satisfy dependencies.
Verify the installation by checking the XRDP version:
xrdp --versionThis command displays the installed XRDP version and confirms successful installation.
XRDP Service Configuration
Start the XRDP service and enable automatic startup:
sudo systemctl start xrdp
sudo systemctl enable xrdpThe first command starts the XRDP service immediately, while the second ensures the service starts automatically during system boot.
Verify service status:
sudo systemctl status xrdpThe output should indicate the service is “active (running)” and display recent log entries. Look for any error messages that might indicate configuration issues.
Check XRDP listening ports:
sudo netstat -tlnp | grep xrdpXRDP should be listening on port 3389 (TCP) for incoming RDP connections.
Initial Configuration File Overview
XRDP configuration files are located in /etc/xrdp/ directory. The primary configuration file xrdp.ini contains server settings, port configurations, and session management parameters.
Key configuration files include:
- xrdp.ini: Main server configuration
- sesman.ini: Session manager configuration
- startwm.sh: Desktop environment startup script
Review the default configuration before making modifications:
sudo cat /etc/xrdp/xrdp.ini | grep -E "^[^#]"This command displays active configuration lines, excluding comments.
Firewall Configuration
Proper firewall configuration is essential for XRDP functionality while maintaining system security.
Understanding XRDP Port Requirements
XRDP uses port 3389 (TCP) by default for RDP connections. This port must be accessible from client machines requiring remote desktop access. Understanding port requirements helps implement appropriate security measures while maintaining functionality.
Consider the security implications of exposing port 3389 to networks or the internet. This port is commonly targeted by attackers attempting unauthorized access to remote desktop services.
Configuring Firewall Rules
Configure firewall rules to allow XRDP connections:
sudo firewall-cmd --permanent --add-port=3389/tcp
sudo firewall-cmd --reloadThese commands add a permanent firewall rule allowing TCP traffic on port 3389 and reload the firewall configuration to apply changes immediately.
For enhanced security, restrict access to specific IP addresses or networks:
sudo firewall-cmd --permanent --add-rich-rule="rule family='ipv4' source address='192.168.1.0/24' port protocol='tcp' port='3389' accept"
sudo firewall-cmd --reloadReplace the IP address range with your specific network requirements.
Verify firewall rules:
sudo firewall-cmd --list-allThe output should display the configured XRDP port access rules.
Advanced Firewall Security
Implement additional security measures by creating custom firewall zones for XRDP access. This approach provides granular control over network access and enhances security posture.
Consider implementing fail2ban integration to automatically block IP addresses showing suspicious activity patterns. This additional security layer helps prevent brute-force attacks against XRDP services.
SELinux Configuration
Security-Enhanced Linux (SELinux) provides mandatory access control for AlmaLinux systems and requires specific configuration for XRDP functionality.
SELinux and XRDP Compatibility
SELinux policies control process access to system resources, including network ports and file systems. XRDP requires specific SELinux boolean settings to function properly with desktop environments.
Understanding SELinux contexts and policies helps troubleshoot access denials and ensures proper XRDP functionality without compromising system security.
Configuring SELinux for XRDP
Enable the necessary SELinux boolean for XRDP:
sudo setsebool -P xrdp_connect_all_unconfined 1This command allows XRDP to connect to various system services required for desktop environment functionality. The -P flag makes the setting persistent across system reboots.
Check current SELinux booleans related to XRDP:
sudo getsebool -a | grep xrdpVerify the boolean is enabled and persistent.
Verifying SELinux Configuration
Monitor SELinux audit logs for XRDP-related denials:
sudo ausearch -m avc -ts recent | grep xrdpThis command searches for recent SELinux access vector cache (AVC) denials related to XRDP services. Address any denials by creating custom policies or adjusting existing configurations.
Check SELinux status:
sudo sestatusEnsure SELinux is in “Enforcing” mode for optimal security while maintaining XRDP functionality.
XRDP Configuration and Customization
Customize XRDP settings to optimize performance, security, and user experience for your specific environment.
Main Configuration File (xrdp.ini) Setup
Edit the primary XRDP configuration file:
sudo nano /etc/xrdp/xrdp.iniKey configuration parameters include:
Port Configuration: Modify the default port for enhanced security:
port=3390Session Management: Configure session handling:
max_sessions=10
session_timeout=300Security Settings: Adjust encryption and authentication:
crypt_level=high
security_layer=rdpPerformance Optimization: Configure display settings:
max_bpp=16
use_compression=yesThese settings balance performance with visual quality, particularly important for slower network connections.
Desktop Environment Integration
Configure the desktop environment startup script:
sudo nano /etc/xrdp/startwm.shFor GNOME desktop, ensure the script contains:
exec gnome-sessionFor XFCE desktop:
exec startxfce4For KDE Plasma:
exec startkdeMake the script executable:
sudo chmod +x /etc/xrdp/startwm.shUser Session Configuration
Create user-specific session configuration by editing .xsession files in user home directories:
echo "exec gnome-session" > ~/.xsession
chmod +x ~/.xsessionThis configuration ensures consistent desktop environment startup for individual users.
Restart XRDP services to apply configuration changes:
sudo systemctl restart xrdpTesting XRDP Connection
Verify XRDP functionality by testing connections from various client platforms.
Connecting from Windows Clients
Open Windows Remote Desktop Connection and configure connection parameters:
- Computer: Enter your AlmaLinux 10 server IP address
- User name: Specify a valid user account
- Connection settings: Configure display and performance options
Click “Connect” and enter authentication credentials when prompted. The GNOME desktop environment should load successfully, providing full remote desktop functionality.
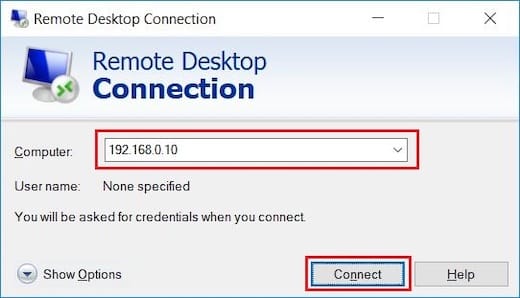
Configure connection options for optimal performance:
- Display: Set appropriate resolution and color depth
- Experience: Select connection speed matching your network
- Local Resources: Configure clipboard and drive sharing as needed
Connecting from Linux Clients
Install Remmina RDP client on Linux systems:
sudo dnf install -y remmina remmina-plugins-rdpConfigure Remmina connection:
- Server: AlmaLinux 10 IP address
- Username/Password: Valid user credentials
- Color depth: 16-bit for performance optimization
- Quality: Adjust based on network conditions
Alternative command-line RDP clients include xfreerdp:
xfreerdp /v:192.168.1.100 /u:username /p:password /w:1280 /h:1024Verifying Successful Connection
Test desktop environment functionality by:
- Opening applications and verifying responsiveness
- Testing file manager and system settings access
- Verifying network connectivity within the desktop session
- Checking audio and clipboard functionality if configured
Monitor XRDP logs during connection testing:
sudo tail -f /var/log/xrdp.logThis command displays real-time XRDP log entries, helping identify connection issues or performance problems.
Security Hardening and Best Practices
Implement comprehensive security measures to protect your XRDP installation from unauthorized access and potential attacks.
Changing Default Port Configuration
Modify the default XRDP port to reduce automated attack exposure:
sudo sed -i 's/port=3389/port=3390/g' /etc/xrdp/xrdp.iniUpdate firewall rules for the new port:
sudo firewall-cmd --permanent --remove-port=3389/tcp
sudo firewall-cmd --permanent --add-port=3390/tcp
sudo firewall-cmd --reloadRestart XRDP service:
sudo systemctl restart xrdpUsing non-standard ports significantly reduces automated attack attempts while maintaining full functionality.
Implementing SSH Tunneling
Configure SSH tunneling for enhanced security:
ssh -L 3389:localhost:3389 username@almalinux-serverThis approach encrypts XRDP traffic through SSH, providing additional security layers. Connect RDP clients to localhost:3389 instead of direct server connections.
User Access Control
Create dedicated user groups for XRDP access:
sudo groupadd xrdp-users
sudo usermod -a -G xrdp-users usernameConfigure user account policies including password complexity requirements, account lockout policies, and session timeout settings.
Implement strong password policies for all accounts used with XRDP access. Use complex passwords combining uppercase, lowercase, numbers, and special characters.
Additional Security Measures
Install and configure fail2ban for automated threat response:
sudo dnf install -y fail2ban
sudo systemctl enable --now fail2banCreate XRDP-specific fail2ban jail configuration:
sudo nano /etc/fail2ban/jail.localAdd XRDP protection:
[xrdp]
enabled = true
port = 3389
filter = xrdp
logpath = /var/log/xrdp.log
maxretry = 3
bantime = 3600This configuration automatically blocks IP addresses after three failed login attempts.
Performance Optimization
Optimize XRDP performance for various network conditions and hardware configurations.
Network Performance Tuning
Configure compression and quality settings for optimal network performance:
sudo nano /etc/xrdp/xrdp.iniAdd performance optimization settings:
use_compression=yes
max_bpp=16
xserverbpp=16These settings reduce bandwidth usage while maintaining acceptable visual quality.
For RDP clients, configure appropriate connection speeds in the Experience tab. Select “LAN (10Mbits or higher)” for local network connections to enable advanced codecs.
Server Resource Optimization
Monitor system resource usage during XRDP sessions:
htopOptimize memory usage by:
- Disabling unnecessary desktop effects and animations
- Using lightweight applications when possible
- Configuring appropriate swap space for memory management
Disable GNOME animations for improved performance:
gsettings set org.gnome.desktop.interface enable-animations falseClient-Side Optimizations
Configure RDP client settings for optimal performance:
- Color depth: Use 15-bit or 16-bit color for better performance
- Desktop composition: Disable compositor effects when possible
- Resolution: Use appropriate screen resolution for network conditions
- Experience settings: Match connection speed to actual network performance
For Windows RDP clients, disable unnecessary features:
- Printer redirection
- Audio redirection (if not needed)
- Drive redirection (unless required)
Troubleshooting Common Issues
Address frequent XRDP problems with systematic troubleshooting approaches.
Connection Problems
“Connection refused” errors typically indicate service or firewall issues:
- Verify XRDP service status:
sudo systemctl status xrdp - Check firewall rules:
sudo firewall-cmd --list-all - Verify port accessibility:
sudo netstat -tlnp | grep 3389 - Review XRDP logs:
sudo journalctl -u xrdp -f
Authentication failures often result from user account or SELinux issues:
- Verify user account status:
sudo passwd -S username - Check SELinux denials:
sudo ausearch -m avc -ts recent - Review session manager logs:
sudo tail /var/log/xrdp-sesman.log
Session and Display Issues
Black screen after login indicates desktop environment problems:
- Check startwm.sh configuration:
sudo cat /etc/xrdp/startwm.sh - Verify desktop environment installation:
rpm -qa | grep gnome - Test user session startup:
sudo -u username startx - Review user-specific configurations:
ls -la ~/.xsession
Desktop environment not loading requires session configuration verification:
- Ensure proper startwm.sh permissions:
ls -l /etc/xrdp/startwm.sh - Check desktop environment packages:
dnf list installed | grep desktop - Verify display manager configuration:
sudo systemctl status gdm
Performance and Stability Issues
High resource usage problems require systematic optimization:
- Monitor CPU usage:
top -p $(pgrep xrdp) - Check memory utilization:
free -h - Review disk I/O:
iotop - Optimize desktop environment settings
Session disconnection issues often relate to network or configuration problems:
- Check network stability:
ping -c 10 client-ip - Review timeout settings in xrdp.ini
- Monitor system logs:
sudo journalctl -f - Verify client-side network configuration
Maintenance and Updates
Establish regular maintenance procedures to ensure optimal XRDP performance and security.
Regular Maintenance Tasks
Log file management prevents disk space issues:
sudo logrotate -f /etc/logrotate.d/xrdpCreate custom logrotate configuration for XRDP logs:
sudo nano /etc/logrotate.d/xrdpConfigure automatic log rotation:
/var/log/xrdp*.log {
weekly
rotate 4
compress
delaycompress
missingok
notifempty
create 0640 xrdp xrdp
}Service monitoring ensures continued availability:
sudo systemctl is-active xrdpImplement automated monitoring using system monitoring tools or custom scripts.
Updating XRDP and Dependencies
Perform regular system updates while maintaining XRDP functionality:
sudo dnf update xrdp
sudo systemctl restart xrdpTest XRDP functionality after updates to ensure continued operation. Create system snapshots or backups before major updates to enable quick recovery if issues arise.
Monitoring and Alerting
Configure system monitoring for XRDP services:
sudo nano /etc/systemd/system/xrdp-monitor.serviceCreate monitoring service for automated alerts and status checks. Implement log analysis tools to identify potential issues before they impact users.
Congratulations! You have successfully installed XRDP. Thanks for using this tutorial for installing the XRDP (Remote Desktop) on AlmaLinux OS 10 system. For additional help or useful information, we recommend you check the official XRDP website.