How To Install Xrdp Server on Debian 13

Remote desktop access has become essential for system administrators and users who need to manage Linux servers from anywhere. Xrdp, an open-source implementation of the Microsoft Remote Desktop Protocol (RDP) server, provides seamless remote access to Debian 13 systems using any standard RDP client. This powerful tool enables administrators to connect to their Debian machines through a graphical interface, making server management more intuitive and efficient.
Debian 13 Trixie, the latest stable release, fully supports Xrdp installation and configuration with various desktop environments. This comprehensive guide walks through every step of installing and configuring Xrdp server on Debian 13, from initial system preparation to advanced security hardening. Whether managing a single server or deploying remote access across multiple systems, this tutorial provides the knowledge needed to establish secure, reliable remote desktop connections.
What is Xrdp and Why Use It on Debian 13?
Xrdp is a free, open-source Remote Desktop Protocol server that allows Linux systems to accept connections from RDP clients. Unlike proprietary solutions, Xrdp provides a standardized way to access Linux desktops remotely without requiring additional licensing costs. The protocol operates on TCP port 3389 by default, the same port used by Microsoft’s native RDP implementation.
The primary advantage of Xrdp over alternatives like VNC is its native integration with Windows Remote Desktop clients. Users can connect to their Debian systems using the built-in Remote Desktop Connection tool available in every Windows installation. This eliminates the need for installing third-party software on client machines, streamlining the remote access experience.
Xrdp supports multiple concurrent user sessions, making it ideal for multi-user server environments. Each user can maintain their own independent desktop session with personalized settings and applications. The server also supports session reconnection, allowing users to disconnect and reconnect to existing sessions without losing their work.
On Debian 13 specifically, Xrdp benefits from improved stability and performance optimizations in the latest package versions. The Trixie release includes updated dependencies that enhance compatibility with modern desktop environments. Security patches and bug fixes ensure reliable operation for production deployments.
Prerequisites and System Requirements
Before beginning the Xrdp installation process, ensure your Debian 13 system meets the necessary requirements. A fresh or existing Debian 13 Trixie installation serves as the foundation. The system should have at least 2GB of RAM for basic operation, though 4GB or more is recommended for optimal performance when running graphical desktop sessions.
Root or sudo access is mandatory for installing packages and modifying system configurations. Standard user accounts cannot complete the installation without elevated privileges. Verify sudo access by running a simple command like sudo whoami, which should return “root” if properly configured.
Network connectivity is crucial for downloading packages from Debian repositories. The server must have internet access during installation, though this requirement can be relaxed after initial setup. For remote access, the system needs a static IP address or a reliable dynamic DNS service. Clients connecting from remote networks should know the server’s public IP address or hostname.
Check the current Debian version to confirm the system runs Trixie (version 13). The command cat /etc/debian_version displays the version number. Understanding user account requirements is essential since each remote desktop user needs a valid system account with appropriate permissions.
Storage requirements are modest, with approximately 500MB needed for the desktop environment and Xrdp packages. Additional space may be required depending on the applications and files users will access through remote sessions.
Step 1: Update and Upgrade Debian 13 System
Beginning with a fully updated system prevents compatibility issues and ensures all security patches are applied. Package updates often resolve bugs that could interfere with Xrdp installation and operation. The process involves refreshing the package repository cache and upgrading existing installed packages.
Execute the following command to update the package index:
sudo apt updateThis command contacts Debian’s package repositories and downloads the latest package information. The output displays the number of packages that can be upgraded. Wait for the process to complete before proceeding.
Next, upgrade all installed packages to their latest versions:
sudo apt upgrade -yThe -y flag automatically confirms the upgrade without prompting for user input. The system downloads and installs updated packages, which may take several minutes depending on internet speed and the number of packages requiring updates. Watch for any error messages during the upgrade process, though errors are uncommon on stable Debian releases.
If the kernel was updated during the upgrade process, reboot the system to ensure the new kernel loads properly:
sudo rebootAfter the reboot, verify the system is fully operational before continuing with the desktop environment installation.
Step 2: Install Desktop Environment (XFCE) on Debian 13
Xrdp requires a graphical desktop environment to function properly since it serves desktop sessions to remote users. Without a desktop environment, Xrdp has nothing to display when users connect. Debian 13 supports multiple desktop environments, but XFCE stands out as the optimal choice for Xrdp deployments.
XFCE is a lightweight desktop environment that balances functionality with resource efficiency. It consumes significantly less memory and CPU compared to heavier alternatives like GNOME or KDE Plasma. This efficiency translates to better remote desktop performance, especially over slower network connections. XFCE’s stability and mature codebase make it reliable for production server environments.
Install XFCE and required components with this comprehensive command:
sudo apt install xfce4 xfce4-goodies xorg dbus-x11 x11-xserver-utils -yBreaking down the package components reveals their individual purposes:
- xfce4: The core XFCE desktop environment including the panel, window manager, and essential utilities
- xfce4-goodies: Additional plugins and applications that enhance XFCE functionality
- xorg: The X Window System display server required for graphical applications
- dbus-x11: Message bus system for inter-application communication in X sessions
- x11-xserver-utils: Utility programs for X server configuration and management
The installation process downloads several hundred megabytes of packages and may take 10-20 minutes depending on system specifications and network speed. The installer automatically resolves dependencies and configures the desktop environment. Configuration prompts may appear for certain services like display managers—select default options or lightdm if asked.
After installation completes, reboot the system to ensure all desktop components initialize properly:
sudo rebootThe reboot allows the system to load the new graphical environment and start necessary display services. For servers without local display access, the graphical interface won’t be visible locally, but this is expected since Xrdp will provide remote access.
Alternative desktop environments like LXDE, MATE, or GNOME can also work with Xrdp. However, GNOME may present additional configuration challenges and requires more system resources. LXDE offers even lighter resource usage but with fewer features than XFCE.
Step 3: Install Xrdp Server on Debian 13
Debian 13’s default repositories include the Xrdp package, eliminating the need to add third-party sources or compile from source code. This simplifies the installation process and ensures compatibility with other system components. The packaged version receives regular security updates through Debian’s standard update channels.
Install the Xrdp server with a single command:
sudo apt install xrdp -yThe package manager downloads Xrdp along with its dependencies, including xorgxrdp for X server integration. During installation, the system automatically creates a dedicated xrdp system user for running the service. This user account enhances security by running the service with limited privileges rather than as root.
The Xrdp service starts automatically after installation completes. Debian’s systemd initialization system manages the service, ensuring it starts on boot and restarts automatically if it crashes. Configuration files are installed to /etc/xrdp/, where administrators can customize settings.
Verify the Xrdp installation succeeded by checking the service status:
sudo systemctl status xrdpThe output should display “active (running)” in green text, indicating the service is operational. Additional information includes the process ID, memory usage, and recent log entries. If the status shows “inactive” or “failed,” review the system logs for error messages using journalctl -xeu xrdp.
Enable the Xrdp service to start automatically at system boot if not already enabled:
sudo systemctl enable xrdpThis command creates the necessary systemd symlinks to launch Xrdp during the boot sequence. Even if the system reboots unexpectedly, Xrdp will start automatically without manual intervention.
The main configuration file /etc/xrdp/xrdp.ini contains settings for port numbers, encryption, and session parameters. The default configuration works for most scenarios, but advanced users can customize these settings for specific requirements.
Step 4: Configure SSL Certificate Permissions
Xrdp uses SSL certificates to encrypt remote desktop connections, protecting authentication credentials and session data from interception. By default, Debian generates a self-signed SSL certificate during installation, stored in /etc/ssl/. The Xrdp process needs read access to the private key file to establish encrypted connections.
The private key file /etc/ssl/private/ssl-cert-snakeoil.key has restricted permissions to prevent unauthorized access. Only members of the ssl-cert group can read this file. The xrdp user created during installation must be added to this group to function properly.
Add the xrdp user to the ssl-cert group with this command:
sudo adduser xrdp ssl-certThe system confirms the addition by displaying “Adding user ‘xrdp’ to group ‘ssl-cert'”. This modification grants the Xrdp service the necessary permissions to access the SSL certificate without compromising overall system security.
Verify the group membership change:
groups xrdpThe output should include “ssl-cert” among the listed groups. Group membership changes don’t take effect for running processes until they restart, so restart the Xrdp service:
sudo systemctl restart xrdpThe restart applies the new permissions and prepares Xrdp to handle encrypted connections. Without proper certificate access, clients may encounter connection errors or fail to establish sessions.
For production environments, consider replacing the self-signed certificate with a properly signed certificate from a trusted certificate authority. This eliminates certificate warnings when clients connect and provides stronger authentication. Commercial certificates or Let’s Encrypt certificates can be configured by updating the certificate paths in xrdp.ini.
Step 5: Configure Xrdp to Use XFCE Desktop
After installing both Xrdp and the XFCE desktop environment, they must be configured to work together. By default, Xrdp may try to launch a generic X session rather than specifically starting XFCE. The startwm.sh script controls which desktop environment loads when users connect via RDP.
Edit the Xrdp startup script:
sudo nano /etc/xrdp/startwm.shThis command opens the configuration file in the nano text editor. Users comfortable with vim or other editors can substitute their preferred tool. The file contains several lines that need modification.
Locate the following lines near the end of the file:
test -x /etc/X11/Xsession && exec /etc/X11/Xsession
exec /bin/sh /etc/X11/XsessionComment out these lines by adding a # character at the beginning of each line:
#test -x /etc/X11/Xsession && exec /etc/X11/Xsession
#exec /bin/sh /etc/X11/XsessionAdd the following line immediately after the commented lines:
startxfce4This command explicitly tells Xrdp to launch the XFCE desktop environment for user sessions. Save the changes by pressing Ctrl+O, then Enter, and exit nano with Ctrl+X.
Restart the Xrdp service to apply the configuration changes:
sudo systemctl restart xrdpThe modified startup script now directs all incoming RDP connections to XFCE sessions. Users connecting via remote desktop will see the familiar XFCE interface with its panel, desktop icons, and application menu.
Test the configuration by attempting a remote desktop connection before proceeding with firewall setup. If users encounter blank screens or login loops after this modification, double-check the startwm.sh file for syntax errors or typos.
Step 6: Configure Firewall for Xrdp Access
Network security begins with properly configured firewall rules that control which services are accessible from remote networks. Without firewall configuration, Xrdp remains inaccessible to remote clients even though the service runs correctly. Debian systems commonly use UFW (Uncomplicated Firewall) for managing iptables rules with a simplified syntax.
Install UFW if not already present on the system:
sudo apt install ufw -yEnable the UFW firewall service:
sudo systemctl enable ufw
sudo ufw enableThe system prompts for confirmation since enabling the firewall might disrupt existing SSH connections. Type ‘y’ to proceed. Before enabling the firewall, always ensure SSH access is permitted to avoid being locked out of remote servers.
Allow SSH connections before configuring other rules:
sudo ufw allow sshXrdp listens on TCP port 3389 by default, the standard RDP port. Firewall rules must permit incoming connections to this port for remote desktop access to function. Security best practices recommend restricting access to specific IP addresses or network ranges rather than opening the port to the entire internet.
For maximum security, allow connections only from a specific IP address or subnet:
sudo ufw allow from 192.168.1.0/24 to any port 3389Replace 192.168.1.0/24 with the appropriate network range for your environment. This rule permits RDP connections only from devices within the specified subnet, blocking access from all other sources.
For environments requiring access from any location, use the less restrictive rule:
sudo ufw allow 3389/tcpThis rule opens port 3389 to all incoming connections, which increases security risk. Organizations using this approach should implement additional security measures like strong passwords, multi-factor authentication, and intrusion detection systems.
Reload UFW to activate the new firewall rules:
sudo ufw reloadVerify the rules are active and correctly configured:
sudo ufw status verboseThe output displays all active firewall rules, including the newly added Xrdp rule. Check that port 3389 appears in the list with the expected source restrictions.
Network administrators managing cloud servers must also configure security groups or network ACLs at the cloud platform level. Cloud firewalls operate independently of the server’s local firewall and require separate configuration.
Step 7: Connect to Debian 13 via Remote Desktop
With Xrdp fully configured and the firewall opened, the system is ready to accept remote desktop connections. Different operating systems use various RDP clients, but the connection process remains similar across platforms.
Connecting from Windows
Windows includes a native Remote Desktop Connection client in all editions. Access the client by pressing Win+R to open the Run dialog, then type mstsc and press Enter. Alternatively, search for “Remote Desktop Connection” in the Start menu.
Enter the Debian server’s IP address or hostname in the Computer field. Click Show Options to configure additional settings like display resolution and local resource sharing. Click Connect to initiate the connection.
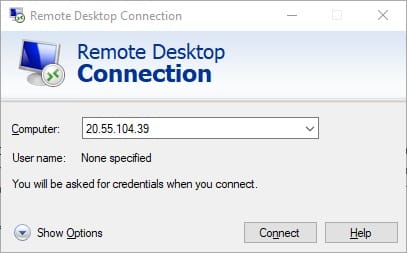
A security certificate warning appears because Debian uses a self-signed certificate. Select “Don’t ask me again for connections to this computer” and click Yes to proceed. This warning won’t appear if using a properly signed certificate from a trusted authority.
The Xrdp login screen displays with fields for Session, Username, and Password. Leave Session set to “Xorg” or “X11rdp”. Enter the username and password of a valid Debian user account. Click OK to authenticate and start the session.
Within seconds, the XFCE desktop environment appears in the Remote Desktop window. The desktop functions identically to a local session, with full access to applications, files, and system settings.
Connecting from Linux
Linux systems use FreeRDP or Remmina for RDP connections. Install FreeRDP on Debian or Ubuntu systems:
sudo apt install freerdp2-x11 -yConnect using the command line:
xfreerdp /u:username /p:password /v:server-ip:3389 /size:1920x1080Replace username, password, and server-ip with actual values. The /size parameter controls the remote desktop resolution.
Remmina provides a graphical interface for managing multiple RDP connections. Install it from the distribution’s package repository and configure connections through its intuitive interface.
Connecting from macOS
macOS users download Microsoft Remote Desktop from the Mac App Store. Launch the application, click Add PC, and enter the Debian server’s IP address. Configure display and device settings as needed, then connect with valid credentials.
Common Xrdp Issues and Troubleshooting
Remote desktop deployments occasionally encounter issues that prevent successful connections or cause session problems. Understanding common problems and their solutions reduces downtime and frustration.
Issue 1: Black Screen After Login
A black screen after entering credentials usually indicates desktop environment configuration problems. The Xrdp session starts successfully, but the desktop environment fails to launch.
Verify the xorgxrdp package is installed:
sudo apt install xorgxrdp -yCheck the startwm.sh configuration file for errors. Ensure the startxfce4 command is present and properly formatted. Restart Xrdp after making configuration changes.
Missing xserver-xorg packages can also cause black screens. Install the complete X server stack:
sudo apt install xserver-xorg-core xserver-xorg-video-dummy -yIssue 2: Disconnection Immediately After Password Entry
Sessions that disconnect immediately after authentication often result from multiple concurrent sessions. If the user is already logged in locally or through another RDP connection, Xrdp may refuse the new connection.
Log out of all other sessions before connecting via RDP. Check for active sessions:
whoTerminate conflicting sessions using the kill command on the appropriate process.
Issue 3: Authentication Failures
Repeated authentication failures despite correct credentials suggest permission or configuration issues. Verify the user account exists and has a valid password:
sudo passwd usernameCheck Xrdp logs for authentication error messages:
sudo tail -f /var/log/xrdp.logSSL certificate permission problems can prevent authentication. Confirm the xrdp user belongs to the ssl-cert group and restart the service.
Issue 4: Unable to Connect Through Firewall
Connection timeouts often indicate firewall configuration problems. Verify port 3389 is open in UFW:
sudo ufw status | grep 3389If the port isn’t listed, add the appropriate firewall rule and reload UFW. Test network connectivity from the client machine using telnet:
telnet server-ip 3389A successful connection displays “Connected to” followed by the server address. Connection refused errors indicate the firewall is blocking access or Xrdp isn’t running.
Issue 5: Xrdp Service Not Starting
Service startup failures prevent any remote desktop connections. Check the service status for error messages:
sudo systemctl status xrdp
sudo journalctl -xeu xrdpConfiguration file syntax errors often cause startup failures. Review recent configuration changes and restore original files if necessary. Enable the service to start automatically:
sudo systemctl enable xrdpCorrupted packages may require reinstallation:
sudo apt reinstall xrdpChecking Xrdp Logs
Xrdp maintains detailed logs for troubleshooting connection and session issues. The primary log file is located at /var/log/xrdp.log. View recent log entries:
sudo tail -100 /var/log/xrdp.logSession-specific logs appear in /var/log/xrdp-sesman.log. Monitor logs in real-time while attempting connections:
sudo tail -f /var/log/xrdp-sesman.logError messages in these logs provide specific information about authentication failures, connection problems, and session startup issues.
Optimizing Xrdp Performance on Debian 13
Remote desktop performance depends on numerous factors including network bandwidth, system resources, and configuration settings. Optimization techniques improve responsiveness and user experience, especially over slower connections.
Reduce color depth to decrease bandwidth requirements. Edit /etc/xrdp/xrdp.ini and modify the color depth setting:
max_bpp=16Lower color depth (16-bit vs 24-bit) significantly reduces data transmission without severely impacting visual quality.
Adjust TCP buffer sizes for improved network performance. Add the following lines to xrdp.ini under the [Globals] section:
tcp_send_buffer_bytes=4194304
tcp_recv_buffer_bytes=6291456These larger buffer sizes help maintain consistent performance during network congestion.
Disable unnecessary features that consume bandwidth and processing power. Turn off audio redirection if not needed:
audio_redirection=noSimilarly, disable printer mapping and drive redirection when not required. These features add overhead to every session.
Choose appropriate display resolutions based on network capabilities. Lower resolutions like 1280×720 perform better than 1920×1080 over limited bandwidth. Users can adjust resolution in their RDP client settings.
Hardware resources significantly impact performance. Systems with limited RAM benefit from lightweight desktop environments like XFCE or LXDE. Allocate sufficient CPU cores to handle multiple concurrent sessions in multi-user environments.
The H.264 codec provides substantial performance improvements for modern Xrdp installations. Compile Xrdp with H.264 support enabled or use newer distribution packages that include this feature.
Enable connection compression in the RDP client settings. Most RDP clients include compression options that reduce network traffic without server-side configuration.
Security Best Practices for Xrdp Server
Remote desktop services present attractive targets for attackers attempting unauthorized access. Implementing comprehensive security measures protects systems from intrusion attempts and data breaches.
Restrict access to specific IP addresses or networks rather than exposing Xrdp to the entire internet. Firewall rules limiting source addresses dramatically reduce attack surface. Organizations with remote workers should implement VPN access, allowing users to connect through a secure tunnel before accessing RDP.
Change the default RDP port from 3389 to a non-standard port number. While not a complete security solution, port changes reduce automated scanning and scripted attacks. Update the port in xrdp.ini:
port=13389Remember to update firewall rules and inform users of the new port number.
Enforce strong password policies for all user accounts with RDP access. Passwords should contain uppercase and lowercase letters, numbers, and special characters with minimum length of 12 characters. Consider implementing password expiration and complexity requirements through PAM configuration.
Deploy fail2ban to automatically block IP addresses after repeated failed login attempts. Install fail2ban:
sudo apt install fail2ban -yConfigure fail2ban with an Xrdp jail to monitor authentication logs and ban attacking IPs.
Enable TLS encryption for all RDP connections to protect session data. Xrdp uses TLS by default with self-signed certificates, but production environments should use properly signed certificates from trusted authorities.
Implement multi-factor authentication (MFA) for an additional security layer. Solutions like Google Authenticator integrate with Linux authentication systems through PAM modules. MFA prevents unauthorized access even if passwords are compromised.
Disable root account login via RDP entirely. Root access should only be available through local console or SSH with key-based authentication. Create administrative user accounts with sudo privileges for system management.
Monitor connection logs regularly for suspicious activity. Automated log analysis tools can alert administrators to unusual access patterns or repeated authentication failures. Review logs at least weekly in production environments.
Keep systems updated with the latest security patches. Enable automatic security updates to ensure critical vulnerabilities are addressed promptly:
sudo apt install unattended-upgrades -y
sudo dpkg-reconfigure -plow unattended-upgradesRegular security audits identify potential vulnerabilities before attackers exploit them. Penetration testing and vulnerability scanning should be conducted periodically on systems with remote access enabled.
Advanced Xrdp Configuration Options
The xrdp.ini configuration file contains numerous settings for customizing the remote desktop experience. Advanced users can modify these parameters to suit specific requirements and preferences.
Multiple session types allow users to choose different connection methods from the login screen. Define additional sessions in xrdp.ini:
[Xorg-custom]
name=Custom Session
lib=libxup.so
username=ask
password=ask
ip=127.0.0.1
port=-1
code=20Session reconnection options let users disconnect and reconnect to existing sessions without starting new ones. Configure reconnection behavior in sesman.ini:
Policy=Default
MaxSessions=10Customize the Xrdp login screen by modifying the logo and background images. Replace /usr/share/xrdp/xrdp_logo.bmp with a custom logo file maintaining the same dimensions.
Audio redirection allows sound from remote applications to play on the client machine. Enable the PulseAudio module for full audio support. Some desktop environments require additional configuration for proper audio functionality.
Clipboard sharing enables copy-paste operations between local and remote systems. The xrdp-chansrv component handles clipboard integration automatically for most desktop environments.
Drive mapping makes local drives accessible within remote sessions. Configure redirection in the RDP client rather than server-side settings. Windows RDP client provides detailed options for selecting which drives to share.
Congratulations! You have successfully installed Xrdp. Thanks for using this tutorial for installing the latest version of the Xrdp server on Debian 13 “Trixie” system. For additional help or useful information, we recommend you check the official Xrdp website.