
In this tutorial, we will show you how to protect a directory with a password on Nginx. Securing sensitive web content is essential for maintaining privacy and preventing unauthorized access to critical areas of your website. While many web applications come with built-in authentication mechanisms, sometimes you need a simple, server-level solution to restrict access to specific directories or files. Nginx, one of the most popular web servers, offers robust directory password protection capabilities that are different from Apache’s widely-known .htaccess approach.
Unlike Apache which relies on .htaccess files, Nginx uses a different methodology for implementing password protection. This fundamental difference often confuses webmasters who migrate from Apache to Nginx. However, once you understand the basic concepts and configuration syntax, setting up password protection in Nginx becomes straightforward and highly effective for securing your web directories.
In this comprehensive guide, we’ll walk through everything you need to know about implementing password protection for your directories in Nginx. From understanding the underlying authentication mechanisms to advanced configuration options, you’ll learn how to secure your sensitive content effectively while maintaining optimal server performance.
Understanding Basic Authentication in Nginx
How Nginx Authentication Works
Nginx implements basic HTTP authentication through its core module called auth_basic. This authentication method follows the standard HTTP protocol for authentication, where credentials are transmitted in the request header after being encoded using Base64. When a user attempts to access a protected resource, Nginx checks these credentials against a password file and either grants or denies access based on the authentication result.
The basic authentication flow in Nginx works like this: when a user tries to access a protected directory, the server responds with a 401 (Unauthorized) status code along with a WWW-Authenticate header, prompting the browser to display a login dialog. Once the user enters their credentials, these are sent to the server where Nginx verifies them against the password file before granting access to the requested resource.
Prerequisites for Implementation
Before implementing password protection in Nginx, you’ll need:
- Administrative access to your Nginx server with the ability to modify configuration files
- Command-line access to generate password files
- Basic understanding of Nginx configuration structure and syntax
- Nginx installed and running on your server (this guide assumes you already have Nginx set up)
You’ll also need to ensure that your Nginx installation includes the auth_basic module, which is typically included by default in standard Nginx installations. To use some of the password file creation utilities, you may need to install additional packages on your server, which we’ll cover in the next section.
Password File Creation Methods
Using the htpasswd Utility
The most common and straightforward method to create password files for Nginx is using the htpasswd utility, which is included in the apache2-utils package. Despite its Apache origins, this tool creates password files in a format that Nginx can interpret perfectly.
To install the utility on Debian/Ubuntu systems:
sudo apt-get update
sudo apt-get install apache2-utilsFor CentOS/RHEL systems:
sudo yum install httpd-toolsOnce installed, you can create a new password file using:
sudo htpasswd -c /etc/nginx/.htpasswd usernameThe -c flag indicates that a new file should be created. After executing this command, you’ll be prompted to enter and confirm a password for the specified username.
To add additional users to an existing password file, simply omit the -c flag:
sudo htpasswd /etc/nginx/.htpasswd another_userTo remove a user from the password file:
sudo htpasswd -D /etc/nginx/.htpasswd usernameAlternative Password Generation Methods
If you don’t have access to the htpasswd utility, you can use several alternative methods to create compatible password files:
1. Using OpenSSL:
openssl passwd -crypt your_passwordThen manually add the username and encrypted password to the file:
username:encrypted_password2. Using Perl:
perl -le 'print crypt("your-password", "salt-hash")'Then add the resulting hash to your password file with the username.
3. Using Ruby:
"your-password".crypt("salt-hash")Run this in the interactive Ruby console (irb) and add the output to your password file.
Each of these methods produces compatible encrypted passwords that can be used in your Nginx authentication setup, giving you flexibility based on the tools available in your environment.
Password File Security Considerations
Strategic File Placement
Where you store your password file is just as important as how you create it. To maximize security:
1. Avoid web-accessible locations: Store the password file outside your web root directory whenever possible to prevent direct access from the web.
2. Use restricted directories: If you must store the password file within the web root, use Nginx location blocks to deny access to hidden files:
location ~ /\. {
deny all;
}3. Consider using /etc/nginx/: This directory is a common and secure location for password files since it’s typically not accessible via the web server and has restricted permissions.
Password File Format and Maintenance
The password file format is simple but must be strictly followed. Each line contains a username and an encrypted password separated by a colon:
username:encrypted_passwordFor security and maintenance:
1. Regular audits: Periodically review your password files to remove accounts that are no longer needed.
2. Backup procedures: Include password files in your regular backup routine, but ensure they’re encrypted or secured during the backup process.
3. Permissions: Set restrictive file permissions on your password files:
sudo chmod 600 /etc/nginx/.htpasswd
sudo chown www-data:www-data /etc/nginx/.htpasswd4. Password rotation: Implement a policy to update passwords regularly, especially for sensitive directories.
Properly managing these files prevents unauthorized access and ensures that your authentication system remains effective and secure.
Nginx Configuration Fundamentals
Essential Configuration Directives
To implement password protection in Nginx, you need to understand two critical directives:
1. auth_basic: This directive enables basic authentication and sets the realm text (the message shown in the authentication dialog). The syntax is:
auth_basic "Authentication Required";Where the text in quotes is displayed to users when prompted for credentials.
2. auth_basic_user_file: This directive specifies the path to the password file containing user credentials:
auth_basic_user_file /etc/nginx/.htpasswd;This path must be accessible to the Nginx process and contain properly formatted credentials.
These directives are typically placed within location blocks in your Nginx configuration to control which directories or paths require authentication.
Server Block Organization
Nginx configurations are organized in server blocks, which define settings for specific domains or IP addresses. Within these server blocks, location directives determine how Nginx processes requests for different URI paths.
To find and edit the correct configuration files:
1. On Debian/Ubuntu: Look in /etc/nginx/sites-available/ with symlinks in /etc/nginx/sites-enabled/
2. On CentOS/RHEL: Check /etc/nginx/conf.d/ directory
3. The main configuration file is typically at /etc/nginx/nginx.conf
Always validate your configuration after making changes:
sudo nginx -tThis command checks syntax errors before you apply the new configuration.
Configuration Examples for Different Scenarios
Site-wide protection:
server {
listen 80;
server_name example.com;
location / {
auth_basic "Restricted Area";
auth_basic_user_file /etc/nginx/.htpasswd;
root /var/www/html;
index index.html;
}
}Single directory protection:
server {
listen 80;
server_name example.com;
location / {
root /var/www/html;
index index.html;
}
location /admin {
auth_basic "Admin Area";
auth_basic_user_file /etc/nginx/.htpasswd;
root /var/www/html;
index index.html;
}
}Multiple directories with different credentials:
server {
listen 80;
server_name example.com;
location /staff {
auth_basic "Staff Area";
auth_basic_user_file /etc/nginx/.htpasswd-staff;
root /var/www/html;
index index.html;
}
location /management {
auth_basic "Management Only";
auth_basic_user_file /etc/nginx/.htpasswd-management;
root /var/www/html;
index index.html;
}
}Understanding these configuration patterns allows you to implement flexible authentication strategies across your website.
Step-by-Step Implementation Guide
Preliminary Setup
Before implementing password protection, complete these preparatory steps:
1. Ensure necessary packages are installed:
sudo apt-get update
sudo apt-get install nginx apache2-utils2. Create test directories (if needed):
sudo mkdir -p /var/www/html/protected
sudo touch /var/www/html/protected/index.html
sudo echo "Protected content" > /var/www/html/protected/index.html3. Backup existing configurations:
sudo cp /etc/nginx/sites-available/default /etc/nginx/sites-available/default.bakThis ensures you have a clean environment and can restore your original configuration if needed.
Password File Creation Process
Now, create the password file for authentication:
1. Generate a new password file:
sudo htpasswd -c /etc/nginx/.htpasswd adminYou’ll be prompted to enter and confirm a password for the “admin” user.
2. Verify the file was created:
sudo cat /etc/nginx/.htpasswdYou should see the username followed by an encrypted password hash.
3. Add additional users (if needed):
sudo htpasswd /etc/nginx/.htpasswd user24. Secure the password file:
sudo chmod 640 /etc/nginx/.htpasswd
sudo chown www-data:www-data /etc/nginx/.htpasswdThis creates a properly formatted and secured password file ready for use by Nginx.
Nginx Configuration Implementation
Next, configure Nginx to use the password file:
1. Edit your site configuration:
sudo nano /etc/nginx/sites-available/default2. Add authentication to the desired location:
server {
listen 80 default_server;
server_name _;
# Existing configuration...
location /protected {
auth_basic "Restricted Content";
auth_basic_user_file /etc/nginx/.htpasswd;
root /var/www/html;
index index.html;
}
# Protect hidden files
location ~ /\. {
deny all;
}
}3. Test the configuration:
sudo nginx -t4. Apply the changes:
sudo systemctl reload nginxor
sudo service nginx reloadYour protected directory should now require authentication before access is granted.
Testing and Troubleshooting Authentication
Verification Methods
After implementing password protection, thorough testing is essential:
1. Browser testing:
- Open a new browser window (or private/incognito mode)
- Navigate to your protected URL (e.g.,
http://yourdomain.com/protected/) - Verify that a login prompt appears
- Test valid credentials (should grant access)
- Test invalid credentials (should deny access)
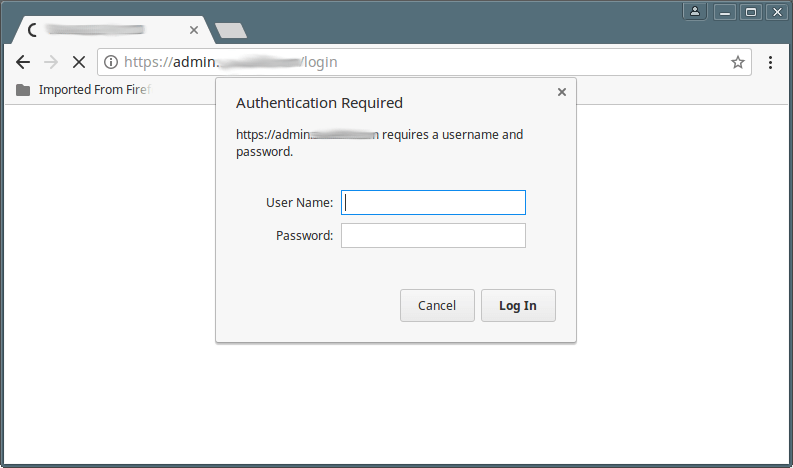
2. Command-line testing with curl:
# Test without credentials (should fail)
curl -I http://yourdomain.com/protected/
# Test with valid credentials
curl -I --user username:password http://yourdomain.com/protected/The first command should return a 401 status, while the second should return a 200 status if authentication is working correctly.
Common Issues and Solutions
Problem: Authentication prompt not appearing
- Check if the location block is correctly defined
- Verify that the auth_basic directive is properly set
- Ensure the configuration file is included in the main Nginx configuration
Solution:
# Check if your site configuration is enabled
ls -l /etc/nginx/sites-enabled/
# Verify Nginx is reading the correct configuration
sudo nginx -T | grep auth_basicProblem: “Authentication failed” errors with correct credentials
- Incorrect file path in
auth_basic_user_filedirective - Permission issues with the password file
Solution:
# Check file permissions
ls -la /etc/nginx/.htpasswd
# Verify file contents
cat /etc/nginx/.htpasswd
# Update permissions if needed
sudo chmod 640 /etc/nginx/.htpasswd
sudo chown www-data:www-data /etc/nginx/.htpasswdProblem: Multiple authentication prompts
- If you’re using Nginx as a proxy, you might be experiencing double authentication
Solution:
# Remove authentication headers in proxy configuration
proxy_set_header Authorization "";This prevents Nginx from forwarding the authentication headers to your backend service, avoiding duplicate prompts.
Advanced Configuration Options
IP-Based Access Restrictions
You can combine password protection with IP-based restrictions for enhanced security:
location /admin {
# Allow specific IPs without password
satisfy any;
allow 192.168.1.0/24;
deny all;
# Password protection as fallback
auth_basic "Administrator Login";
auth_basic_user_file /etc/nginx/.htpasswd;
}This configuration allows access from the specified IP range without requiring a password, while enforcing password authentication for all other IP addresses.
Custom Authentication Messaging
Customize the authentication experience:
# Custom realm text (shown in the login prompt)
auth_basic "Company XYZ Internal Portal";
# Custom error page for failed authentication
error_page 401 /custom_401.html;
location = /custom_401.html {
root /var/www/html;
internal;
}The auth_basic text serves as the realm name displayed in the browser’s authentication dialog. A custom error page improves user experience when authentication fails.
Protecting Specific Content Types
You can selectively protect content based on file types or patterns:
# Protect all PHP files
location ~ \.php$ {
auth_basic "Protected PHP Scripts";
auth_basic_user_file /etc/nginx/.htpasswd;
# PHP-FPM configuration...
}
# Protect a specific pattern
location ~ /reports/.*\.pdf$ {
auth_basic "Confidential Reports";
auth_basic_user_file /etc/nginx/.htpasswd-reports;
}This allows for fine-grained protection of specific content while leaving other resources freely accessible.
Security Best Practices
HTTPS Implementation
Password protection should always be implemented alongside HTTPS to prevent credential interception:
server {
listen 443 ssl;
server_name example.com;
ssl_certificate /etc/nginx/ssl/certificate.crt;
ssl_certificate_key /etc/nginx/ssl/private.key;
ssl_protocols TLSv1.2 TLSv1.3;
location /protected {
auth_basic "Restricted Content";
auth_basic_user_file /etc/nginx/.htpasswd;
# Other directives...
}
}Without HTTPS, basic authentication credentials are transmitted in an easily decodable format, making them vulnerable to interception.
Authentication Hardening Techniques
Strengthen your authentication implementation:
1. Set strong password requirements:
- Use complex passwords with minimum length requirements
- Implement regular password rotation policies
- Consider using a password manager to generate and store credentials
2. Implement request limiting:
# Rate limiting to prevent brute force attacks
limit_req_zone $binary_remote_addr zone=auth:10m rate=1r/s;
location /protected {
limit_req zone=auth burst=5;
auth_basic "Restricted Content";
auth_basic_user_file /etc/nginx/.htpasswd;
}3. Configure proper logging:
# Enhanced logging for authentication attempts
log_format auth '$remote_addr - $remote_user [$time_local] '
'"$request" $status $body_bytes_sent '
'"$http_referer" "$http_user_agent"';
access_log /var/log/nginx/auth.log auth;These measures help protect against brute force attacks and provide audit trails for security investigations.
Integration with Other Nginx Features
Working with Reverse Proxy Setups
When using Nginx as a reverse proxy, special considerations apply for authentication:
server {
listen 80;
server_name example.com;
location /app {
auth_basic "Restricted Application";
auth_basic_user_file /etc/nginx/.htpasswd;
proxy_pass http://backend_server;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
# Remove Authorization header to prevent double authentication
proxy_set_header Authorization "";
}
}The proxy_set_header Authorization ""; directive prevents Nginx from forwarding authentication headers to the backend, avoiding potential conflicts with application-level authentication.
Application-Specific Configurations
Different applications may require specific authentication configurations:
WordPress Admin Protection:
location /wp-admin {
auth_basic "WordPress Admin";
auth_basic_user_file /etc/nginx/.htpasswd;
# Standard WordPress PHP handling
include fastcgi_params;
fastcgi_pass unix:/var/run/php/php7.4-fpm.sock;
}Node.js Application:
location /nodejs-app {
auth_basic "Node.js Application";
auth_basic_user_file /etc/nginx/.htpasswd;
proxy_pass http://localhost:3000;
proxy_http_version 1.1;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection 'upgrade';
}These examples show how to integrate authentication with different application environments while maintaining security and functionality.
Real-World Implementation Examples
Protecting Admin Areas
Administrative interfaces are prime candidates for password protection:
# Protect multiple admin areas with the same credentials
location ~ ^/(admin|dashboard|control) {
auth_basic "Administrative Access";
auth_basic_user_file /etc/nginx/.htpasswd-admin;
# Additional security measures
allow 10.0.0.0/8;
allow 192.168.0.0/16;
deny all;
}This configuration protects multiple administrative paths while also restricting access by IP address ranges, creating a multi-layered security approach.
API Access Protection
For APIs, especially in development environments:
# Protect development API
server {
listen 80;
server_name api-dev.example.com;
location / {
auth_basic "Development API";
auth_basic_user_file /etc/nginx/.htpasswd-api;
proxy_pass http://localhost:8080;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
}
# Allow health checks without authentication
location = /health {
proxy_pass http://localhost:8080/health;
}
}This example shows how to protect an entire API while allowing specific endpoints (like health checks) to remain accessible without authentication.