How To Set Up Two-Factor Authentication on Ubuntu 24.04 LTS

In today’s digital landscape, protecting your Linux systems from unauthorized access is more critical than ever. Ubuntu 24.04 LTS, the latest long-term support release, offers robust security features that users can leverage to safeguard their systems. Two-factor authentication (2FA) stands as one of the most effective security enhancements you can implement, adding an essential layer of protection beyond traditional passwords.
Research shows that implementing 2FA can prevent up to 99.9% of automated attacks and significantly reduce account compromise risks. This comprehensive guide walks you through the complete process of setting up 2FA on your Ubuntu 24.04 LTS system, covering everything from basic concepts to advanced configurations and troubleshooting.
Understanding Two-Factor Authentication Basics
Two-factor authentication operates on a fundamental security principle: combining “something you know” (like a password) with “something you have” (like a physical device generating codes). This multi-layered approach dramatically enhances security compared to password-only authentication.
Authentication factors generally fall into three categories:
- Knowledge factors: Something you know (passwords, PINs)
- Possession factors: Something you have (mobile device, hardware token)
- Inherence factors: Something you are (fingerprint, facial recognition)
In Ubuntu systems, 2FA typically implements the first two factors, requiring both your password and a time-based one-time password (TOTP) generated by an authenticator app. This approach prevents attackers from gaining access even if they somehow obtain your password.
Many users mistakenly believe implementing 2FA on Linux systems is overly complex or disruptive. However, modern Ubuntu releases, including 24.04 LTS, have streamlined the process considerably. You have several options, including Google Authenticator, Authy, FreeOTP, and hardware solutions like YubiKey, allowing you to choose the method that best fits your security requirements and workflow.
Prerequisites and Preparation
Before beginning the 2FA setup process, ensure your system meets these requirements:
- Ubuntu 24.04 LTS installed and updated (run
sudo apt update && sudo apt upgrade) - Administrative (sudo) privileges on your system
- A stable internet connection for package installation
- A smartphone with an authenticator app installed (Google Authenticator, Authy, etc.)
- Basic familiarity with terminal commands
It’s crucial to create a system backup before making any security modifications. Use Ubuntu’s built-in Backup tool or run a manual backup of critical configuration files, especially those in the /etc/pam.d/ directory.
For remote systems, maintain an active session in a separate terminal throughout the configuration process. This precaution ensures you won’t be locked out if configuration issues arise.
Available 2FA Methods for Ubuntu 24.04
Ubuntu 24.04 LTS supports various 2FA implementation methods, each with distinct advantages:
- Google Authenticator remains the most popular choice due to its simplicity, reliability, and wide adoption. It generates time-based one-time passwords (TOTP) that refresh every 30 seconds.
- Authy offers additional features like multi-device synchronization and encrypted backups, making it ideal for users who want added convenience without sacrificing security.
- FreeOTP provides an open-source alternative that functions similarly to Google Authenticator but appeals to users who prefer fully open solutions.
- Hardware tokens like YubiKey offer the highest security level by providing physical authentication devices that generate codes or respond to cryptographic challenges. These tokens particularly benefit systems requiring top-tier security.
While SMS-based authentication exists, security experts generally don’t recommend it for Ubuntu systems due to vulnerabilities in the SMS protocol. Time-based authenticator apps provide significantly stronger protection.
When selecting your 2FA method, consider factors like security requirements, user convenience, and whether you need multi-device support. For most Ubuntu users, Google Authenticator offers the best balance of security and simplicity.
Installing Google Authenticator PAM Module
The first step in implementing 2FA on Ubuntu 24.04 LTS involves installing the Google Authenticator PAM (Pluggable Authentication Modules) module. This component integrates the authentication mechanism with Ubuntu’s login system.
Open your terminal and execute:
sudo apt update
sudo apt install libpam-google-authenticatorThis command installs the necessary packages and dependencies. Verify the installation completed successfully by checking the installed version:
apt show libpam-google-authenticatorThe package installation creates the necessary PAM module files in the system. If you encounter any installation errors, ensure your package repositories are correctly configured and your system is up to date.
Ubuntu 24.04 LTS includes the latest version of the PAM module, which addresses previous bugs and security issues found in earlier versions. The installation process should complete quickly with minimal system impact.
Configuring PAM for Two-Factor Authentication
PAM (Pluggable Authentication Modules) provides the framework that enables 2FA integration with Ubuntu’s authentication system. You’ll need to modify several PAM configuration files to enable 2FA properly.
Start by editing the common-auth file:
sudo nano /etc/pam.d/common-authAdd the following line at the end of the file:
auth required pam_google_authenticator.so nullokThe nullok parameter is important as it allows users who haven’t yet configured 2FA to continue logging in with just a password. This prevents accidental lockouts during the transition period.
Save the file and exit the editor (in nano, press Ctrl+O, then Enter, followed by Ctrl+X). This configuration tells PAM to require Google Authenticator verification during authentication attempts, forming the foundation of your 2FA implementation.
After making these changes, test the configuration by opening a new terminal session. If everything is configured correctly, you should still be able to log in normally, as we haven’t yet generated authentication keys or enabled 2FA for specific services.
Setting Up 2FA for SSH Access
Securing SSH access with 2FA provides excellent protection for servers accessible over the internet. This requires modifying the SSH daemon configuration to require both password and verification code authentication.
Edit the SSH daemon configuration file:
sudo nano /etc/ssh/sshd_configLocate or add these lines, ensuring they’re set as follows:
ChallengeResponseAuthentication yes
UsePAM yes
AuthenticationMethods keyboard-interactiveNext, modify the PAM configuration for SSH:
sudo nano /etc/pam.d/sshdAdd this line at the top of the file:
auth required pam_google_authenticator.so nullokAfter saving these changes, restart the SSH service to apply the new configuration:
sudo systemctl restart sshdTest your configuration by attempting an SSH connection to the server from another machine. The connection should now prompt for both your password and a verification code.
If you’re configuring this on a remote server, keep your current SSH session open until you’ve verified the new configuration works. This prevents lockouts if misconfiguration occurs. Common issues include typos in configuration files or incorrect PAM module parameters.
For servers with multiple users, consider implementing 2FA gradually, starting with administrative accounts before applying it system-wide. This phased approach minimizes disruption while strengthening your security posture.
Generating and Setting Up Your Authentication Keys
With the system configuration complete, each user who requires 2FA must generate their authentication keys. This process creates the secret key that links their authenticator app with the Ubuntu system.
Log in as the user who needs 2FA and run:
google-authenticatorThe system will present several configuration questions:
- “Do you want authentication tokens to be time-based?” – Answer y (yes) for standard time-based tokens.
- A QR code will display in your terminal. Scan this with your authenticator app.
- The system will show your secret key and emergency scratch codes. Write down the scratch codes and store them securely offline.
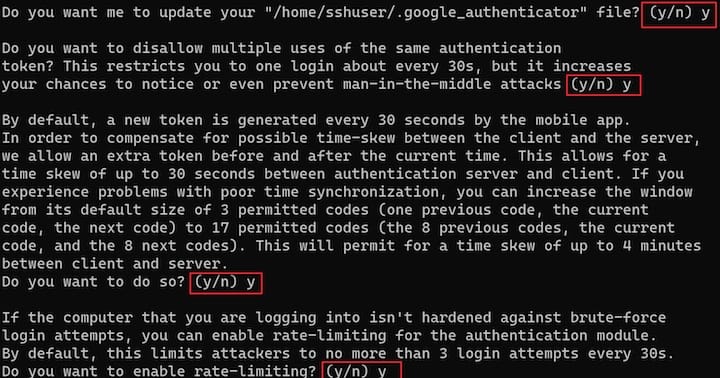
You’ll then be asked additional configuration questions:
- “Do you want me to update your ~/.google_authenticator file?” – Answer y.
- “Do you want to disallow multiple uses of the same authentication token?” – Answer y for better security.
- “Do you want to increase the original generation time limit?” – Answer n unless you have specific reasons.
- “Do you want to enable rate-limiting?” – Answer y to prevent brute-force attacks.
The configuration generates a .google_authenticator file in your home directory containing your secret key and preferences. Keep this file secure, as anyone with access to it could generate valid codes for your account.
If you’re setting up multiple devices (recommended as a backup), you can either scan the QR code with each device or manually enter the secret key displayed during setup.
Configuring 2FA for Local Logins
Securing local logins with 2FA adds protection against unauthorized physical access to your Ubuntu system. This requires additional PAM configuration beyond what we’ve already set up.
Edit the login PAM configuration:
sudo nano /etc/pam.d/loginAdd this line after the @include common-auth line:
auth required pam_google_authenticator.so nullokFor graphical logins, modify the gdm PAM configuration:
sudo nano /etc/pam.d/gdm-passwordAdd the same line as above after the common-auth inclusion.
After saving these changes, test your configuration by logging out and attempting to log back in. The system should now prompt for both your password and verification code.
Local login 2FA implementation varies slightly depending on your display manager (GDM, LightDM, SDDM, etc.). Ubuntu 24.04 LTS uses GDM by default, but if you’ve installed a different desktop environment, you may need to modify different configuration files.
If you encounter issues logging in, use a virtual console (Ctrl+Alt+F3) and log in with your emergency scratch codes to fix configuration problems.
Setting Up 2FA for Sudo Commands
Requiring 2FA verification for sudo commands adds an important security layer that prevents unauthorized escalation of privileges, even if someone gains access to your regular user account.
Edit the sudo PAM configuration:
sudo nano /etc/pam.d/sudoAdd this line at the top of the file:
auth required pam_google_authenticator.so nullokSave and exit the editor. Test the configuration by running a command with sudo:
sudo apt updateThe system should now prompt for both your password and a verification code before executing privileged commands.
This feature particularly benefits multi-user systems where different users have sudo access. It ensures that even if credentials are compromised, attackers can’t easily execute privileged commands without the second factor.
For systems where frequent sudo usage is necessary, the additional verification step might feel cumbersome. In such cases, consider implementing custom PAM rules that require 2FA only for specific high-risk commands or implement a reasonable timeout period where 2FA isn’t required for subsequent sudo commands within a certain timeframe.
Advanced Configuration Options
Ubuntu’s 2FA implementation offers several advanced configuration options to tailor the security measures to your specific needs.
Configuring time windows: By default, verification codes are valid for 30 seconds. You can adjust this with the window_size parameter:
auth required pam_google_authenticator.so window_size=3This example sets a 90-second window (3 × 30 seconds), which can help if time synchronization issues occur between devices.
Creating per-user exceptions: For systems where only certain users require 2FA, modify the PAM configuration to use the user parameter:
auth [success=1 default=ignore] pam_succeed_if.so user notingroup require2fa
auth required pam_google_authenticator.so nullokThis example skips 2FA for users not in the “require2fa” group. Create this group and add users who need 2FA:
sudo groupadd require2fa
sudo usermod -a -G require2fa usernameRate limiting: Fine-tune brute force protection by adjusting rate-limiting parameters:
auth required pam_google_authenticator.so nullok rate_limit=3 rate_time=30This limits authentication attempts to 3 tries within 30 seconds.
Directory service integration: For enterprise environments using LDAP or Active Directory, you can integrate 2FA with your directory service by configuring PAM modules in the correct order to validate both directory credentials and 2FA tokens.
These advanced configurations allow security teams to implement graduated security policies that balance protection with usability based on risk assessments and operational requirements.
Security Best Practices
Implementing 2FA is just one component of a comprehensive security strategy. Follow these additional best practices to maximize your Ubuntu 24.04 LTS security:
Emergency recovery planning: Store emergency scratch codes securely in an offline location, such as a physical safe. Document the recovery process for situations where authenticator devices are lost or damaged.
Regular secret rotation: Periodically regenerate your 2FA secrets (every 6-12 months) by running the google-authenticator command again and updating your devices.
Multi-device setup: Configure multiple authentication devices to prevent lockouts if your primary device fails or is lost. This redundancy is crucial for production systems.
Audit logging: Enable comprehensive authentication logging to monitor 2FA usage and alert on suspicious activities:
sudo nano /etc/pam.d/common-sessionAdd:
session required pam_unix.so auditPhysical security: Remember that 2FA doesn’t replace the need for physical security. Secure your hardware against unauthorized access, especially for servers in shared environments.
Update management: Keep your Ubuntu system updated with security patches by enabling automatic security updates:
sudo apt install unattended-upgrades
sudo dpkg-reconfigure unattended-upgradesUser training: Ensure all users understand the importance of 2FA and proper security procedures, including not sharing verification codes or storing them alongside passwords.
Implementing these practices creates a defense-in-depth security approach that significantly strengthens your overall security posture.
Troubleshooting Common 2FA Issues on Ubuntu 24.04
Even with careful configuration, issues can arise with 2FA implementation. Here are solutions to the most common problems:
Time synchronization issues: If verification codes are consistently rejected, your system or mobile device may have incorrect time settings. Enable automatic time synchronization:
sudo apt install chrony
sudo systemctl enable chrony
sudo systemctl start chronyVerify your smartphone also has automatic time synchronization enabled.
“Permission denied” errors: These typically indicate incorrect file permissions on the .google_authenticator file. Fix with:
chmod 600 ~/.google_authenticatorLost access to authenticator app: Use your emergency scratch codes to log in, then reset your 2FA configuration:
google-authenticator -fThe -f flag forces recreation of the configuration file.
SSH connection issues: If you can’t connect via SSH after enabling 2FA, check the SSH daemon configuration with:
sudo sshd -tThis tests the configuration for errors. Common issues include typos in the sshd_config file or missing PAM module entries.
PAM configuration errors: Review PAM logs for detailed error information:
sudo journalctl | grep pamThis helps identify specific PAM module issues or configuration mistakes.
Module loading failures: If you receive “module is unknown” errors, verify the Google Authenticator PAM module is correctly installed:
ls -la /lib/security/ | grep googleReinstall the package if necessary.
When troubleshooting, make incremental changes and test after each modification. This methodical approach helps isolate the specific cause of issues and avoids compounding problems with multiple simultaneous changes.
Congratulations! You have successfully configured two-factor authentication. Thanks for using this tutorial to set up two-factor authentication on Ubuntu 24.04 LTS system. For additional help or useful information, we recommend you check the official Ubuntu website.