How To Install GlassFish on Fedora 42

GlassFish is an open-source Jakarta EE platform application server that provides developers with a complete runtime environment for building, deploying, and managing enterprise-grade Java applications. As the official reference implementation for Jakarta EE 10 specifications, this powerful platform enables developers to leverage cutting-edge enterprise technologies including Servlets, JavaServer Pages (JSP), JavaServer Faces (JSF), Enterprise JavaBeans (EJB), and Java Persistence API (JPA). Originally developed by Sun Microsystems and later acquired by Oracle Corporation, Eclipse GlassFish is now maintained by the Eclipse Foundation, ensuring continued development and community support.
Eclipse GlassFish 7 stands out as a lightweight yet modular server that supports comprehensive authentication methods such as file-based, LDAP, certificate, JDBC, digest, PAM, Solaris, and custom realms. The platform includes robust features like high availability clustering, automatic load balancing, and an intuitive web-based administration console. Additionally, GlassFish 7 brings support for MicroProfile specifications including MicroProfile Config, MicroProfile JWT Propagation, and MicroProfile REST Client APIs. Running on JDK 11 or higher, with full compatibility up to JDK 17, GlassFish 7 delivers optimal performance for modern cloud-native applications.
This comprehensive tutorial guides you through installing and configuring GlassFish 7 on Fedora 42. You’ll learn prerequisite requirements, Java installation procedures, server deployment, systemd service configuration, security hardening, firewall setup, and production optimization techniques. By the end of this guide, you’ll have a fully functional, production-ready GlassFish application server capable of hosting sophisticated Jakarta EE applications on your Fedora 42 system.
Prerequisites and System Requirements
Before beginning the GlassFish installation on Fedora 42, verify that your system meets the minimum hardware and software specifications. GlassFish 7 requires at least 200MB of free disk space for the server installation itself, though actual production deployments typically need 2-5GB to accommodate applications, logs, and temporary files. Memory requirements start at 512MB RAM for basic installations, but production environments should allocate at least 2-4GB for optimal application performance.
Processor requirements include an 800MHz CPU as the bare minimum, though modern multi-core processors (quad-core or higher) deliver significantly better performance for concurrent user loads. Your Fedora 42 installation must have network connectivity to download GlassFish packages and dependencies from official repositories. Root or sudo privileges are essential for executing system-level commands, installing packages, and configuring services.
Port availability is critical for GlassFish operations. Ensure ports 4848 (admin console), 8080 (HTTP listener), and 8181 (HTTPS listener) are free and not occupied by other services. Execute netstat -tuln or ss -tuln to identify port usage before installation. It’s highly recommended to perform a complete system update before starting the installation process to eliminate potential package conflicts. A fresh Fedora 42 installation minimizes compatibility issues with existing software configurations.
Understanding GlassFish Architecture and Components
GlassFish operates on a modular architecture built atop the OSGi framework, providing a flexible and extensible runtime environment for Jakarta EE applications. The server’s core architecture revolves around several fundamental components that work in harmony to deliver enterprise application services. The Domain Administration Server (DAS) serves as the central management component, orchestrating server instances, configurations, resources, and deployed applications.
Each GlassFish installation can contain multiple domains, where each domain functions as an independent server instance with isolated configuration, deployed applications, and resource definitions. The default domain, automatically created during installation and named “domain1,” serves as the primary administrative domain for most deployments. This domain-based architecture enables administrators to run multiple GlassFish instances on the same physical server with complete isolation between environments.
The administrative infrastructure includes two primary tools. The web-based administrative console, accessible through port 4848, provides a comprehensive graphical interface for managing all aspects of the server. The asadmin command-line utility offers powerful administrative capabilities ideal for automation, scripting, and remote management scenarios. GlassFish supports both standalone server deployments for single-instance applications and sophisticated clustered configurations for high-availability production environments requiring load distribution and failover capabilities.
Understanding this architectural foundation helps in making informed decisions about server configuration, resource allocation, and deployment strategies tailored to specific application requirements.
Step 1: Update Fedora 42 System Packages
Begin the installation process by ensuring your Fedora 42 system runs the latest packages and security updates. Open a terminal window using Ctrl+Alt+T or access the system through SSH if managing a remote server. Execute the following DNF command to update all installed packages:
sudo dnf update -yThis command refreshes the package repository metadata from Fedora mirrors and upgrades all installed packages to their current versions. The -y flag automatically confirms prompts, streamlining the update process. System updates typically include kernel patches, security fixes, library updates, and application improvements that enhance stability and performance.
The update process duration varies based on your internet connection speed and the number of packages requiring updates. Fresh installations might take 10-15 minutes, while regularly maintained systems complete updates in just a few minutes. Monitor the terminal output for any errors or warnings that might indicate repository connectivity issues.
After completing the update, check if kernel updates were installed by comparing your current kernel version with the newly installed version. If kernel updates were applied, reboot the system to ensure all changes take effect:
sudo systemctl rebootWait for the system to restart completely before proceeding with the next steps. This preparation establishes a stable foundation for GlassFish installation, minimizing potential conflicts with outdated system libraries.
Step 2: Install Java Development Kit
GlassFish is fundamentally a Java-based application server requiring a compatible Java Development Kit to function. Fedora 42 repositories provide several OpenJDK versions, including OpenJDK 11, 17, and 21, all of which are compatible with GlassFish 7. For GlassFish 7, JDK 11 or higher is mandatory, with JDK 17 recommended for long-term support and optimal performance.
Install OpenJDK 17 using Fedora’s DNF package manager, which automatically handles all dependencies:
sudo dnf install java-17-openjdk java-17-openjdk-devel -yThe command installs both the Java Runtime Environment (JRE) for executing Java applications and the development tools necessary for compilation and debugging. Installation typically completes within 2-3 minutes, downloading approximately 200MB of packages.
After successful installation, verify the Java version to confirm proper installation and ensure the correct version is active:
java -versionExpected output displays version information similar to:
openjdk version "17.0.x" 2023-xx-xx
OpenJDK Runtime Environment (build 17.0.x+x)
OpenJDK 64-Bit Server VM (build 17.0.x+x, mixed mode, sharing)Configure the JAVA_HOME environment variable, considered best practice for Java applications. Edit your user’s .bashrc file:
echo 'export JAVA_HOME=/usr/lib/jvm/java-17-openjdk' >> ~/.bashrc
echo 'export PATH=$PATH:$JAVA_HOME/bin' >> ~/.bashrc
source ~/.bashrcVerify JAVA_HOME configuration:
echo $JAVA_HOMEThis environment variable helps GlassFish and other Java applications locate the JDK installation directory consistently. Proper Java configuration ensures smooth GlassFish deployment and operation.
Step 3: Create Dedicated GlassFish System User
Running GlassFish as a non-privileged user represents a fundamental security best practice, significantly reducing potential system exposure if the server is compromised. Create a dedicated system user specifically for GlassFish operations rather than using the root account or personal user accounts.
Create the glassfish user with a designated home directory:
sudo useradd -m -d /opt/glassfish7 -U -s /bin/false glassfishThis command creates a system user named “glassfish” with the following characteristics:
-m: Creates the home directory if it doesn’t exist-d /opt/glassfish7: Sets the home directory path-U: Creates a group with the same name as the user-s /bin/false: Disables shell login for security
The /opt directory serves as the standard Linux location for optional application software not managed by the system package manager. This approach isolates GlassFish from system directories, simplifying backup procedures and permission management.
Verify user creation:
id glassfishThe output confirms user and group IDs, validating successful creation. This dedicated user configuration provides several security advantages:
- Limits GlassFish’s access to system resources
- Prevents unauthorized login attempts
- Enables permission-based access control
- Facilitates multi-administrator management through group membership
Shell access is deliberately disabled to prevent direct login, though the account can still execute GlassFish processes and own server files. This configuration aligns with production security standards and Linux system administration best practices.
Step 4: Download GlassFish Server Distribution
Download the latest GlassFish 7 release from the official Eclipse GlassFish website to ensure authenticity and integrity. GlassFish distributions come in two variants: Full Profile and Web Profile. The Full Profile includes complete Jakarta EE 10 specifications, supporting comprehensive enterprise features including EJB, JMS, and batch processing. The Web Profile provides a lighter distribution focused on web application development with Servlet, JSF, CDI, and EJB Lite capabilities.
For comprehensive enterprise application development, download the Full Profile version. Navigate to the /tmp directory for temporary file storage:
cd /tmpDownload GlassFish 7 using wget:
wget https://download.eclipse.org/ee4j/glassfish/glassfish-7.0.25.zipReplace “7.0.25” with the latest version number available on the Eclipse GlassFish downloads page. The ZIP archive typically ranges from 120-150MB depending on the profile and version. Download time varies based on internet speed, usually completing within 2-5 minutes.
Verify the download completed successfully by checking the file size:
ls -lh glassfish-7.0.25.zipThe output displays file size and permissions. Compare the size with the official download page to confirm integrity. Always download from official Eclipse sources (download.eclipse.org) to avoid potentially compromised or outdated versions.
For additional security, verify the SHA-256 checksum if provided on the download page:
sha256sum glassfish-7.0.25.zipCompare the output with the published checksum to ensure file authenticity. This verification step protects against corrupted downloads or malicious file substitution.
Step 5: Extract and Install GlassFish Files
Extract the downloaded GlassFish ZIP archive to prepare files for installation. First, verify the unzip utility is installed on your Fedora 42 system:
which unzipIf unzip is not found, install it using DNF:
sudo dnf install unzip -yExtract the GlassFish archive to the /tmp directory:
unzip glassfish-7.0.25.zip -d /tmp/The extraction creates a directory named “glassfish7” containing all server components, binaries, libraries, configuration files, and documentation. Extraction completes within 30-60 seconds, creating hundreds of files and directories.
Move the extracted directory to its permanent location in /opt:
sudo mv /tmp/glassfish7 /opt/The /opt directory provides several advantages for application installations including separation from system directories, simplified backup and migration, and improved permission management. Change ownership of the entire GlassFish directory to the dedicated glassfish user:
sudo chown -R glassfish:glassfish /opt/glassfish7This recursive ownership change ensures the GlassFish server runs with appropriate permissions and prevents unauthorized modifications. Set executable permissions on GlassFish binary files:
sudo chmod -R +x /opt/glassfish7/bin/*The asadmin utility located in the bin directory requires executable permissions to function as the primary administrative tool. Verify the installation structure:
ls -la /opt/glassfish7/Expected directories include bin/, glassfish/, javadb/, and mq/, confirming successful extraction and installation. The installation is now ready for configuration and startup.
Step 6: Configure Environment Variables for Easy Access
Configure system environment variables to streamline GlassFish administration and enable convenient command-line access. Adding the GlassFish bin directory to the PATH variable allows executing administrative commands like asadmin from any location without specifying full paths.
Edit the glassfish user’s .bashrc file:
sudo -u glassfish nano /opt/glassfish7/.bashrcAdd the following lines to configure GlassFish environment variables:
export GLASSFISH_HOME=/opt/glassfish7
export PATH=$PATH:$GLASSFISH_HOME/binSave and exit the editor (Ctrl+X, then Y, then Enter in nano). The GLASSFISH_HOME variable provides a convenient reference to the installation directory for scripts and applications. Reload the bash configuration to apply changes:
sudo -u glassfish bash
source /opt/glassfish7/.bashrcFor system-wide access, add GlassFish to the global PATH by creating a profile script:
sudo nano /etc/profile.d/glassfish.shAdd these lines:
export GLASSFISH_HOME=/opt/glassfish7
export PATH=$PATH:$GLASSFISH_HOME/binSave the file and make it executable:
sudo chmod +x /etc/profile.d/glassfish.sh
source /etc/profile.d/glassfish.shTest the configuration by executing the asadmin command from any directory:
asadmin versionExpected output displays the GlassFish version information, confirming successful PATH configuration. This setup significantly improves administrative workflow efficiency by eliminating the need for full path specifications.
Step 7: Start GlassFish Domain and Verify Operation
Launch the GlassFish server by starting the default domain using the asadmin command-line utility. Switch to the glassfish user for proper permissions:
sudo -u glassfish /opt/glassfish7/bin/asadmin start-domain domain1The default domain “domain1” is automatically created during extraction with pre-configured settings suitable for initial deployment. GlassFish performs several startup procedures including initializing the Jakarta EE runtime environment, loading configurations, and binding to network ports.
Startup output displays progress messages:
Waiting for domain1 to start ...
Successfully started the domain : domain1
domain Location: /opt/glassfish7/glassfish/domains/domain1
Log File: /opt/glassfish7/glassfish/domains/domain1/logs/server.log
Admin Port: 4848
Command start-domain executed successfully.The startup process typically completes within 30-90 seconds depending on system resources. Successful startup confirms HTTP listener binding and administrative console availability.
Verify the server is running by checking domain status:
sudo -u glassfish /opt/glassfish7/bin/asadmin list-domainsOutput shows “domain1 running,” confirming operational status. Check network port bindings:
sudo netstat -tuln | grep -E '4848|8080|8181'Expected output displays GlassFish listening on ports 4848 (admin), 8080 (HTTP), and 8181 (HTTPS). These verifications confirm GlassFish is properly installed and operational, ready for administrative access and configuration.
Step 8: Configure GlassFish Admin Password and Secure Admin
Secure the GlassFish administrative interface by setting a strong admin password immediately after initial startup. Default installations have a blank admin password, creating significant security vulnerabilities. Execute the change-admin-password command:
sudo -u glassfish /opt/glassfish7/bin/asadmin --port 4848 change-admin-passwordThe interactive wizard prompts for the admin username:
Enter admin user name [default: admin]>Press Enter to accept the default “admin” username. Enter the current password:
Enter the admin password>Press Enter since the default password is blank. Provide your new strong password:
Enter the new admin password>
Enter the new admin password again>Create a password with at least 12 characters combining uppercase letters, lowercase letters, numbers, and special characters. Avoid common words, dictionary terms, or predictable patterns. Successful password change displays:
Command change-admin-password executed successfully.Enable secure administration to allow remote administrative access over encrypted HTTPS connections:
sudo -u glassfish /opt/glassfish7/bin/asadmin --port 4848 enable-secure-adminProvide the admin username and newly set password when prompted. Secure admin configures SSL/TLS encryption for administrative communications, preventing password interception and protecting operations from network eavesdropping.
Restart the GlassFish domain to activate security changes:
sudo -u glassfish /opt/glassfish7/bin/asadmin restart-domain domain1Wait for the domain to stop and restart completely. Secure admin requires all administrator accounts to have non-empty passwords, which is why password configuration must precede this step. These security measures significantly harden the administrative interface against unauthorized access.
Step 9: Configure Firewall Rules for Network Access
Configure Fedora 42’s firewalld firewall to permit incoming connections to GlassFish server ports, enabling external access to deployed applications and the administrative console. Fedora uses firewalld as its default dynamic firewall management system.
First, verify firewalld is running:
sudo systemctl status firewalldIf firewalld is not active, start and enable it:
sudo systemctl start firewalld
sudo systemctl enable firewalldOpen port 4848 for the GlassFish administrative console:
sudo firewall-cmd --permanent --add-port=4848/tcpConfigure port 8080 for HTTP application traffic:
sudo firewall-cmd --permanent --add-port=8080/tcpAdd port 8181 for HTTPS connections if SSL/TLS is enabled:
sudo firewall-cmd --permanent --add-port=8181/tcpThe --permanent flag ensures rules persist across system reboots. Reload firewalld to apply the configuration changes:
sudo firewall-cmd --reloadVerify the rules are active:
sudo firewall-cmd --list-portsExpected output displays:
4848/tcp 8080/tcp 8181/tcpFor production environments, implement more restrictive rules limiting access to specific IP addresses or networks:
sudo firewall-cmd --permanent --add-rich-rule='rule family="ipv4" source address="192.168.1.0/24" port port="4848" protocol="tcp" accept'
sudo firewall-cmd --reloadThis rich rule restricts administrative console access to the 192.168.1.0/24 network only. Security best practices recommend closing unnecessary ports and enabling only those required for your specific deployment. Document firewall configurations for reference and troubleshooting procedures.
Step 10: Create Systemd Service for Automatic Startup
Create a systemd service configuration enabling automatic GlassFish startup during system boot and providing standardized service management. Systemd is Fedora 42’s default init system, offering robust process management and dependency handling.
Create a service unit file in the systemd directory:
sudo nano /etc/systemd/system/glassfish.serviceAdd the following configuration:
[Unit]
Description=Eclipse GlassFish Server v7
After=syslog.target network.target
[Service]
Type=forking
User=glassfish
Group=glassfish
ExecStart=/opt/glassfish7/bin/asadmin start-domain domain1
ExecReload=/opt/glassfish7/bin/asadmin restart-domain domain1
ExecStop=/opt/glassfish7/bin/asadmin stop-domain domain1
Restart=on-failure
RestartSec=10s
[Install]
WantedBy=multi-user.targetThis configuration defines several key parameters:
Type=forking: Indicates GlassFish spawns background processes during startupUser=glassfish: Runs the service as the dedicated glassfish userExecStart: Command to start the domainExecStop: Command for graceful shutdownRestart=on-failure: Automatically restarts GlassFish if it crashesAfter: Ensures network services are available before starting
Save and close the file. Reload the systemd daemon to recognize the new service:
sudo systemctl daemon-reloadEnable the service to start automatically at boot:
sudo systemctl enable glassfish.serviceStop the manually started GlassFish instance first:
sudo -u glassfish /opt/glassfish7/bin/asadmin stop-domain domain1Start GlassFish using systemd:
sudo systemctl start glassfishVerify service status:
sudo systemctl status glassfishExpected output shows “active (running)” status with recent log entries. Test automatic startup by rebooting the system and checking GlassFish status after reboot. This systemd integration provides professional service management aligned with modern Linux system administration practices.
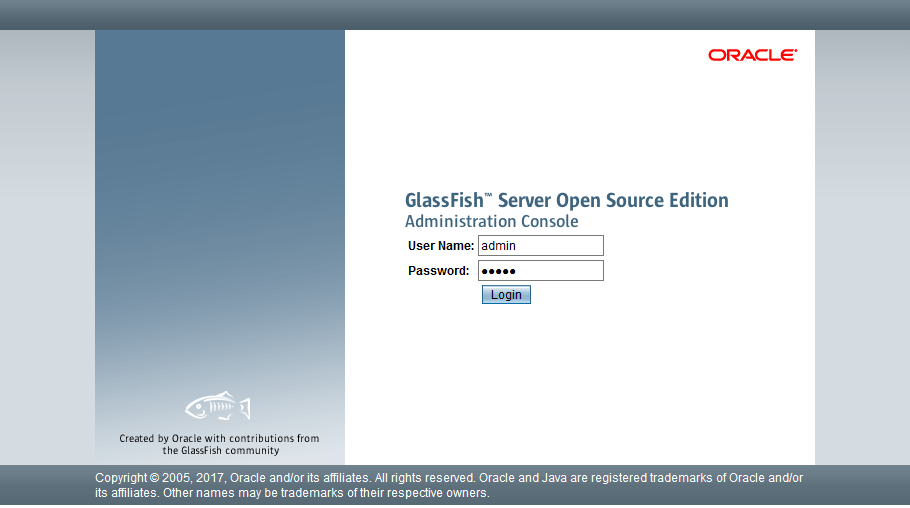
Step 11: Access GlassFish Administrative Console
Access the GlassFish administrative console through a web browser to verify installation success and explore server management capabilities. Open your preferred browser (Firefox, Chrome, or Edge) and navigate to:
https://your-server-ip:4848Replace “your-server-ip” with the actual IP address or hostname of your Fedora 42 server. Use HTTPS protocol since secure admin was enabled earlier. The browser displays a security warning about an untrusted SSL certificate because GlassFish uses a self-signed certificate by default.
Click “Advanced” or “Details” and accept the security exception to proceed. Production deployments should replace self-signed certificates with trusted CA-issued certificates. The GlassFish login page appears, prompting for credentials.
Enter the following credentials:
- Username: admin
- Password: (the password you set in Step 8)
Click “Login” to authenticate. Upon successful authentication, the GlassFish administrative console dashboard displays, showing:
- Server status and uptime
- JVM memory utilization graphs
- Deployed applications list
- Quick access links to common tasks
The left navigation panel contains expandable sections:
- Applications: Deploy and manage web applications
- Resources: Configure JDBC, JMS, and other resources
- Configurations: Server and network settings
- Server: Monitoring and logging controls
Explore the interface to familiarize yourself with available administrative functions. The dashboard provides real-time resource utilization metrics including heap memory usage, thread counts, and HTTP request statistics. Bookmark the admin console URL for convenient future access.
Step 12: Test GlassFish Installation with Default Page
Verify GlassFish HTTP listener functionality by accessing the default welcome page. Open a new browser tab and navigate to:
http://your-server-ip:8080The GlassFish welcome page loads, displaying the Eclipse GlassFish logo and version information. This page confirms:
- HTTP listener is properly configured
- Port 8080 is accessible through the firewall
- Application deployment infrastructure is functional
Test both local and remote access to verify network configuration:
Local access (from the server itself):
curl http://localhost:8080Remote access (from another machine): Navigate to http://server-ip:8080 in a browser
If the test page fails to load, troubleshoot using these steps:
1. Verify GlassFish is running:
sudo systemctl status glassfish2. Check port bindings:
sudo ss -tuln | grep 80803. Review firewall rules:
sudo firewall-cmd --list-ports4. Examine server logs:
sudo tail -f /opt/glassfish7/glassfish/domains/domain1/logs/server.logServer logs provide detailed diagnostic information for troubleshooting connectivity or configuration issues. Successful access to both the welcome page and administrative console confirms GlassFish is properly installed, configured, and operational, ready for application deployment.
Advanced Configuration: JDBC Connection Pools
Configure JDBC connection pools to enable database connectivity for Jakarta EE applications. Connection pools provide efficient database resource management by maintaining reusable database connections rather than creating new connections for each request, significantly improving application performance.
Access the admin console and navigate to Resources > JDBC > JDBC Connection Pools in the left panel. Click “New” to create a connection pool. Provide the following configuration:
- Pool Name: myAppPool
- Resource Type: javax.sql.DataSource
- Database Driver Vendor: (Select your database, e.g., PostgreSQL, MySQL, Oracle)
Click “Next” to proceed to detailed configuration. Configure essential properties:
- Database Name: your_database_name
- Server Name: localhost or database_server_ip
- Port Number: 5432 (PostgreSQL), 3306 (MySQL), or appropriate port
- User: database_username
- Password: database_password
Set pool sizing parameters:
- Initial Pool Size: 8
- Minimum Pool Size: 8
- Maximum Pool Size: 32
- Pool Resize Quantity: 2
Enable connection validation:
- Connection Validation: Required
- Validation Method: auto-commit
- Validation Table Name: (optional)
Click “Finish” to create the pool. Test database connectivity using the “Ping” button on the connection pool configuration page. Successful ping confirms proper database connection configuration.
Create a JDBC resource referencing this pool. Navigate to Resources > JDBC > JDBC Resources and click “New”:
- JNDI Name: jdbc/myAppDB
- Pool Name: myAppPool
Applications use the JNDI name to lookup database connections. Monitor connection pool statistics in the admin console to identify performance bottlenecks or connection leaks.
Performance Optimization: JVM Settings
Optimize Java Virtual Machine settings to improve GlassFish performance based on available hardware and application requirements. JVM configuration significantly impacts memory management, garbage collection efficiency, and overall application responsiveness.
Access JVM settings in the admin console: Navigate to Configurations > server-config > JVM Settings. Click the “JVM Options” tab to view and modify JVM arguments.
Configure Heap Memory
Remove or modify existing -Xmx and -Xms options. Add optimized heap settings based on available RAM:
-Xms2048m
-Xmx4096mFor servers with 8GB RAM, allocating 4GB for heap memory is recommended, though requirements vary by application load. Setting -Xms equal to -Xmx allocates all memory at startup, avoiding runtime allocation overhead.
Configure Metaspace
Metaspace replaces PermGen in Java 8+:
-XX:MetaspaceSize=256m
-XX:MaxMetaspaceSize=512mMetaspace holds class metadata and requires sufficient space for large applications with many classes.
Enable Server Mode
Ensure the -server flag is present (remove -client if found):
-serverServer mode optimizes for long-running applications with continuous code analysis and performance optimization.
Configure Garbage Collection
Add G1 garbage collector for optimal performance:
-XX:+UseG1GC
-XX:MaxGCPauseMillis=200G1GC is recommended for most GlassFish deployments, balancing throughput and latency.
Enable GC Logging
-Xlog:gc*:file=/opt/glassfish7/glassfish/domains/domain1/logs/gc.log:time,uptime,level,tagsGC logs help monitor memory management performance and identify optimization opportunities. After modifying JVM settings, restart the GlassFish domain:
sudo systemctl restart glassfishMonitor server performance using the admin console’s monitoring tools under Server > Monitoring and adjust settings based on observed behavior.
Security Best Practices and Hardening
Implement comprehensive security measures to protect GlassFish from unauthorized access and vulnerabilities. Security should be layered, addressing multiple attack vectors.
Change Master Password
The master password encrypts sensitive configuration data. Change from the default “changeit”:
sudo -u glassfish /opt/glassfish7/bin/asadmin change-master-passwordConfigure SSL/TLS Certificates
Replace self-signed certificates with trusted CA-issued certificates for production:
sudo -u glassfish /opt/glassfish7/bin/asadmin create-ssl --type http-listener --certname your-cert s1-http-listener-2Implement Role-Based Access Control
Create separate admin accounts for different administrators:
sudo -u glassfish /opt/glassfish7/bin/asadmin create-file-user --groups asadmin --passwordfile /path/to/password.txt administrator2Enable Audit Logging
Configure audit logging in the admin console under Configurations > server-config > Security > Audit Modules. Enable DefaultAuditModule to track administrative actions.
Remove Unused Applications
Undeploy sample applications and unused components:
sudo -u glassfish /opt/glassfish7/bin/asadmin list-applications
sudo -u glassfish /opt/glassfish7/bin/asadmin undeploy application-nameRegular Updates
Monitor Eclipse GlassFish release announcements and apply security patches promptly. Subscribe to security mailing lists for vulnerability notifications.
Network Segmentation
Deploy GlassFish in a protected network zone, isolated from untrusted networks. Use firewall rules to restrict access to administrative ports from management networks only.
Troubleshooting Common Installation Issues
Address frequent problems encountered during GlassFish installation and configuration.
Port Conflicts
If GlassFish fails to start due to port binding errors, identify the conflicting process:
sudo ss -tulnp | grep -E '4848|8080|8181'Either stop the conflicting service or reconfigure GlassFish to use alternative ports. Edit /opt/glassfish7/glassfish/domains/domain1/config/domain.xml to change port numbers.
Permission Errors
Verify glassfish user owns all installation files:
sudo chown -R glassfish:glassfish /opt/glassfish7
sudo chmod -R +x /opt/glassfish7/bin/*Java Version Issues
Confirm correct Java version is active:
java -version
javac -versionIf multiple Java versions exist, set the default using alternatives:
sudo alternatives --config javaMemory Errors
If GlassFish fails with OutOfMemoryError, increase heap allocation in JVM settings. Review server logs for specific error messages:
tail -100 /opt/glassfish7/glassfish/domains/domain1/logs/server.logDatabase Connection Failures
Test database connectivity independently before configuring connection pools:
psql -h localhost -U username -d database_nameVerify JDBC driver is placed in /opt/glassfish7/glassfish/domains/domain1/lib/ directory.
Network Access Problems
Verify firewall rules allow required ports and SELinux isn’t blocking connections:
sudo getenforce
sudo semanage port -l | grep -E '4848|8080|8181'Monitoring and Ongoing Maintenance
Establish regular monitoring and maintenance procedures for optimal GlassFish reliability. Enable comprehensive monitoring in the admin console under Server > Monitoring. Set monitoring level to HIGH for production environments:
sudo -u glassfish /opt/glassfish7/bin/asadmin set server.monitoring-service.module-monitoring-levels.jvm=HIGH
sudo -u glassfish /opt/glassfish7/bin/asadmin set server.monitoring-service.module-monitoring-levels.http-service=HIGHReview server logs regularly to identify errors, warnings, or unusual patterns:
sudo tail -f /opt/glassfish7/glassfish/domains/domain1/logs/server.logImplement log rotation to prevent excessive disk consumption. Configure rotation in /etc/logrotate.d/glassfish:
/opt/glassfish7/glassfish/domains/domain1/logs/*.log {
daily
rotate 14
compress
delaycompress
missingok
notifempty
}Schedule regular backups of critical GlassFish components:
sudo tar -czf /backup/glassfish-backup-$(date +%F).tar.gz /opt/glassfish7/glassfish/domains/domain1/Test backup restoration procedures periodically to verify integrity. Monitor disk space usage:
df -h /optUpdate GlassFish when new versions are released. Check the Eclipse GlassFish website for announcements and release notes. Monitor system resources using tools like htop or glances to identify capacity planning needs.
Congratulations! You have successfully installed GlassFish. Thanks for using this tutorial for installing GlassFish on your Fedora 42 Linux system. For additional help or useful information, we recommend you check the official GlassFish website.