How To Install ISPConfig on Fedora 42

ISPConfig stands as one of the most powerful open-source web hosting control panels available for Linux servers today. This comprehensive guide walks through the complete installation process on Fedora 42, providing detailed instructions that enable both beginners and experienced administrators to successfully deploy this versatile server management solution. By following these carefully outlined steps, you’ll transform your Fedora server into a fully-featured web hosting platform capable of managing websites, email accounts, DNS records, FTP users, and much more through a user-friendly web interface.
Understanding ISPConfig
ISPConfig is a robust web-based control panel designed specifically for Linux server administration. Unlike proprietary alternatives, ISPConfig offers a comprehensive solution for managing multiple services without licensing fees or hidden costs.
Key Features and Capabilities
ISPConfig provides centralized management for essential services including:
- Web Servers: Complete control over Apache and Nginx configurations
- Mail Services: Integrated management of Postfix, Dovecot, and spam filtering tools
- DNS Management: Administration of BIND or PowerDNS for domain name resolution
- Database Services: MySQL/MariaDB database creation and management
- FTP Access: PureFTPd configuration and user management
- Security Tools: Firewall configuration, SSL certificate management, and more
When compared to alternatives like cPanel, Plesk, or Webmin, ISPConfig stands out for its comprehensive feature set, minimal resource requirements, and excellent compatibility with various Linux distributions including Fedora 42. Originally developed in 2005, ISPConfig has evolved through multiple major versions, with the current ISPConfig 3 featuring a complete rewrite that supports multi-server environments and enhanced security protocols.
Prerequisites for Installation
Before proceeding with the ISPConfig installation on Fedora 42, ensure your system meets these fundamental requirements:
Hardware Requirements
For optimal performance, your server should have:
- CPU: Minimum dual-core processor (quad-core recommended for production)
- Memory: At least 2GB RAM (4GB or more recommended)
- Storage: Minimum 20GB (40GB+ recommended depending on expected website/email volume)
- Network: Stable internet connection with static IP address
Software Requirements
Your Fedora 42 installation should be:
- A clean, minimal installation of Fedora 42 Server edition
- Updated to the latest packages
- Configured with proper hostname and networking settings
Networking Prerequisites
Ensure these networking elements are properly configured:
- Properly configured hostname (FQDN)
- Static IP address
- Correctly set DNS records for your server
- Required ports accessible through your network/firewall
Having a basic understanding of Linux command line operations, service management, and networking concepts will greatly facilitate the installation process. Creating a full system backup before proceeding is strongly recommended to safeguard against potential issues.
Preparing Your Fedora 42 Server
Proper server preparation forms the foundation for a successful ISPConfig installation. Follow these essential steps to ensure your Fedora 42 environment is correctly configured.
Setting the Hostname
The hostname should be a fully qualified domain name (FQDN) that resolves to your server’s IP address:
hostnamectl set-hostname server1.yourdomain.comConfiguring the /etc/hosts File
Edit your hosts file to include proper entries for your server:
nano /etc/hostsEnsure it contains entries similar to:
127.0.0.1 localhost localhost.localdomain
127.0.1.1 server1.yourdomain.com server1
# IPv6 entries
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allroutersSystem Updates
Update all packages to the latest versions:
dnf update -yA system reboot is recommended after major updates:
systemctl rebootNetwork Configuration
Verify your network settings with:
ip addr showEnsure your primary network interface has a static IP configuration by editing the appropriate network configuration file:
nano /etc/sysconfig/network-scripts/ifcfg-ens33Configure with static IP settings similar to:
TYPE=Ethernet
BOOTPROTO=static
IPADDR=192.168.1.100
NETMASK=255.255.255.0
GATEWAY=192.168.1.1
DNS1=8.8.8.8
DNS2=8.8.4.4
ONBOOT=yesAfter making these changes, restart the network service:
systemctl restart NetworkManagerVerify hostname resolution with:
hostname
hostname -fThese commands should return your short hostname and fully qualified domain name respectively, confirming proper configuration.
Installing Required Dependencies
ISPConfig requires several packages and services to function correctly. This section covers the installation of all necessary components on your Fedora 42 system.
Development Tools and Utilities
First, install essential development packages and utilities:
dnf groupinstall 'Development Tools' -y
dnf install wget perl git net-tools unzip -yAdding Required Repositories
Enable the EPEL (Extra Packages for Enterprise Linux) repository to access additional packages:
dnf install epel-release -yDatabase Server Installation
Install MariaDB server, which provides the database backend for ISPConfig:
dnf install mariadb-server mariadb -y
systemctl enable mariadb
systemctl start mariadbSecure your MariaDB installation:
mysql_secure_installationFollow the prompts to:
- Set a root password
- Remove anonymous users
- Disallow root login remotely
- Remove test database and access
- Reload privilege tables
Web Server and PHP Installation
For Apache web server and PHP:
dnf install httpd mod_ssl -y
systemctl enable httpd
systemctl start httpd
dnf install php php-mysqlnd php-gd php-curl php-mbstring php-xml php-json php-zip php-fpm php-devel php-intl php-opcache php-soap php-imap -yTo use Nginx instead of Apache (optional alternative):
dnf install nginx -y
systemctl enable nginx
systemctl start nginx
dnf install php-fpm php-mysqlnd php-gd php-curl php-mbstring php-xml php-json php-zip php-devel php-intl php-opcache php-soap php-imap -yMail Server Components
Install Postfix, Dovecot, and related packages:
dnf install postfix dovecot dovecot-mysql dovecot-pigeonhole -y
dnf install amavisd-new spamassassin clamav-server clamav-data clamav-update clamav-filesystem clamav clamav-scanner-systemd clamav-devel clamav-lib clamav-server-systemd -yEnable these services:
systemctl enable postfix dovecot clamd@amavisd amavisd
systemctl start postfix dovecot clamd@amavisd amavisdFTP Server Setup
Install PureFTPd:
dnf install pure-ftpd -y
systemctl enable pure-ftpd
systemctl start pure-ftpdDNS Server Installation
Install BIND DNS server:
dnf install bind bind-utils -y
systemctl enable named
systemctl start namedThese installations create the foundation upon which ISPConfig will operate, providing all necessary services for a complete web hosting environment.
Configuring Firewall Settings
Proper firewall configuration is crucial for both security and functionality. Fedora 42 uses firewalld by default, which needs to be configured to allow traffic for all services managed by ISPConfig.
Required Ports for ISPConfig Services
Enable the following ports through firewalld:
# Web Services
firewall-cmd --permanent --add-port=80/tcp
firewall-cmd --permanent --add-port=443/tcp
# FTP Services
firewall-cmd --permanent --add-port=20-21/tcp
firewall-cmd --permanent --add-port=40110-40210/tcp
# Mail Services
firewall-cmd --permanent --add-port=25/tcp
firewall-cmd --permanent --add-port=110/tcp
firewall-cmd --permanent --add-port=143/tcp
firewall-cmd --permanent --add-port=465/tcp
firewall-cmd --permanent --add-port=587/tcp
firewall-cmd --permanent --add-port=993/tcp
firewall-cmd --permanent --add-port=995/tcp
# DNS Services
firewall-cmd --permanent --add-port=53/tcp
firewall-cmd --permanent --add-port=53/udp
# ISPConfig Panel
firewall-cmd --permanent --add-port=8080/tcp
firewall-cmd --permanent --add-port=8081/tcp
# SSH
firewall-cmd --permanent --add-port=22/tcp
# Apply changes
firewall-cmd --reloadTesting Firewall Configuration
After configuring the firewall, verify that all required ports are correctly opened:
firewall-cmd --list-allThe output should show all the ports you’ve enabled. If any service is not functioning correctly after ISPConfig installation, verifying firewall settings should be your first troubleshooting step.
SELinux Configuration
SELinux provides enhanced security but requires proper configuration to work with ISPConfig. You have several options for handling SELinux on your Fedora 42 server.
Understanding SELinux Modes
SELinux has three operational modes:
- Enforcing: All violations are blocked and logged
- Permissive: Violations are logged but not blocked
- Disabled: SELinux is completely turned off
Configuring SELinux for ISPConfig
For optimal security with ISPConfig, setting SELinux to permissive mode is often recommended:
setenforce 0To make this change permanent, edit the SELinux configuration:
nano /etc/selinux/configChange the SELINUX=enforcing line to:
SELINUX=permissiveAlternatively, if you prefer to keep SELinux in enforcing mode, you’ll need to create custom SELinux policies for ISPConfig components. This approach requires more advanced knowledge but provides the strongest security posture.
Verifying SELinux Status
Check the current SELinux status with:
sestatusThis will confirm whether your changes have been applied correctly.
Downloading and Extracting ISPConfig
With all prerequisites in place, it’s time to download and prepare the ISPConfig installation files.
Obtaining the Latest Version
Navigate to a temporary directory and download the latest ISPConfig installer:
cd /tmp
wget https://ispconfig.org/downloads/ISPConfig-3.3.0p1.tar.gzAlternatively, you can use the direct GitHub repository:
cd /tmp
wget --no-check-certificate -O installer.tgz "https://github.com/servisys/ispconfig_setup/tarball/master"Verifying Download Integrity
For security, verify the downloaded file’s checksum (if provided on the ISPConfig website):
sha256sum ISPConfig-3.3.0p1.tar.gzCompare this with the published checksum to ensure file integrity.
Extracting the Installation Files
Extract the downloaded archive:
tar xzf ISPConfig-3.3.0p1.tar.gzOr for the GitHub version:
tar zxvf installer.tgzNavigating to the Installation Directory
Enter the extracted directory:
cd ispconfig3_install/install/For the GitHub version:
cd *ispconfig*/The directory contains the installation scripts and configuration files needed for the next steps.
Running the Installation Script
The ISPConfig installation script will guide you through configuring all components of the system. Follow these steps carefully to ensure proper setup.
Starting the Installer
For the official ISPConfig installer:
php -q install.phpFor the GitHub automated installer:
bash install.shInstallation Modes
The installer offers two primary modes:
- Standard Installation: Recommended for beginners, using default values
- Expert Installation: Allows customization of all configuration options
When prompted, select the appropriate mode based on your needs and expertise level.
Database Configuration
During installation, you’ll be prompted to:
- Create a new MySQL/MariaDB database for ISPConfig
- Set a password for the database user
- Configure database connection settings
Use a strong, unique password and record it securely for future reference.
Web Server Selection
If you installed both Apache and Nginx, you’ll be prompted to choose which one to use with ISPConfig:
- Apache is more widely supported and offers excellent compatibility
- Nginx provides better performance for static content and high-traffic sites
Service Configuration
The installer will automatically configure:
- Mail server settings (Postfix and Dovecot)
- DNS server settings (BIND)
- FTP server settings (PureFTPd)
- Web server virtual host configuration
- PHP settings
Admin User Creation
At the end of the installation, you’ll create the initial administrator account:
- Choose a strong username (avoid “admin” for security)
- Set a complex password
- Record these credentials securely
When the installation completes, you’ll receive a confirmation message with the URL to access your new ISPConfig panel.
Mail Server Configuration
The mail server components require specific configuration within ISPConfig to function optimally. This section covers the essential settings.
Postfix and Dovecot Integration
ISPConfig automatically configures Postfix and Dovecot for basic functionality, but you may want to fine-tune settings through the ISPConfig interface:
- Log into ISPConfig
- Navigate to “System” → “Server Config” → “Mail”
- Adjust settings according to your requirements
Anti-Spam and Anti-Virus Configuration
ISPConfig integrates SpamAssassin and ClamAV for email filtering:
- Access “System” → “Server Config” → “Virus Scanner”
- Verify that ClamAV is properly configured
- Go to “System” → “Server Config” → “Spamfilter”
- Configure SpamAssassin settings, including threshold scores
IMAP/POP3 Settings
For secure email access:
- Navigate to “System” → “Server Config” → “Mail”
- Ensure SSL/TLS is enabled for IMAP and POP3
- Configure authentication mechanisms as needed
Testing Mail Server Functionality
After configuration, test email functionality:
- Create a test email domain and account through ISPConfig
- Send and receive emails to verify proper operation
- Check mail logs for any errors:
tail -f /var/log/maillog
Properly configured mail services are essential for server notifications and client email hosting.
DNS Server Setup
DNS configuration through ISPConfig enables domain name management for your hosted websites. This section covers BIND nameserver setup and management.
BIND Configuration
ISPConfig automatically configures BIND during installation, but verify these settings:
- Navigate to “System” → “Server Config” → “DNS”
- Confirm that the nameserver settings match your server’s information
- Verify that BIND is running with
systemctl status named
Creating DNS Zones
To add a new domain to your DNS server:
- Go to “DNS” → “Zones”
- Click “Add new zone”
- Enter domain information and select appropriate templates
- Add necessary records (A, MX, CNAME, etc.)
Primary and Secondary DNS Setup
For redundancy, configure secondary DNS servers:
- In “DNS” → “Secondary Zones”
- Add slave zones that will be replicated from primary DNS servers
- Ensure proper zone transfers are configured in firewall settings
DNSSEC Implementation
For enhanced security, enable DNSSEC:
- Go to “DNS” → “Zones” → select a zone
- Enable DNSSEC signing
- Configure DS records with your domain registrar
Proper DNS configuration ensures seamless domain resolution for websites hosted on your server.
FTP Server Installation
PureFTPd provides secure file transfer capabilities for your hosted websites. Configure it through ISPConfig for optimal operation.
PureFTPd Setup
ISPConfig manages PureFTPd configuration automatically, but verify these settings:
- Navigate to “System” → “Server Config” → “FTP”
- Confirm that PureFTPd is properly configured
- Verify passive port range settings (typically 40110-40210)
FTP User Management
Create and manage FTP users through ISPConfig:
- Go to “Sites” → select a website → “FTP Accounts”
- Add new FTP users with appropriate permissions
- Set strong passwords and directory restrictions
Passive FTP Configuration
For clients behind firewalls, ensure passive FTP works correctly:
- Verify that passive ports (40110-40210) are open in your firewall
- Configure NAT settings if your server is behind a router
- Test connectivity from external networks
TLS/SSL Configuration
For secure transfers, enable FTP over TLS:
- In “System” → “Server Config” → “FTP”
- Enable TLS/SSL encryption
- Generate or import appropriate certificates
Properly configured FTP services provide secure file management capabilities for website owners.
Web Server Optimization
Optimizing your web server ensures efficient performance for hosted websites. This section covers essential Apache or Nginx tuning steps.
Apache Performance Tuning
If using Apache, optimize these settings:
- Navigate to “System” → “Server Config” → “Web”
- Adjust MPM settings based on server resources
- Configure appropriate timeouts and connection limits
- Enable caching modules for better performance
Nginx Configuration
If using Nginx, optimize these parameters:
- Worker processes (match to CPU cores)
- Worker connections (based on available memory)
- Keepalive timeout settings
- Gzip compression for appropriate content types
PHP Configuration
Optimize PHP for improved performance:
- Adjust memory_limit based on server resources
- Configure appropriate max_execution_time
- Enable opcache for better PHP performance
- Set upload_max_filesize and post_max_size according to needs
Module Management
Enable only necessary modules for security and performance:
- Review and disable unnecessary Apache/Nginx modules
- Enable performance-enhancing modules like mod_cache
- Ensure security modules are properly configured
Regular monitoring of web server performance allows for ongoing optimization as traffic patterns change.
Database Management Setup
ISPConfig integrates MySQL/MariaDB management, allowing you to create and manage databases for hosted websites easily.
MySQL/MariaDB Optimization
Optimize database performance:
- Navigate to “System” → “Server Config” → “Database”
- Configure appropriate memory settings based on server resources
- Adjust innodb_buffer_pool_size for optimal performance
- Set appropriate connection limits
Database Backup Strategy
Implement regular database backups:
- Configure automated backups through ISPConfig
- Set appropriate retention policies
- Test backup restoration periodically
- Consider off-server backup storage for critical data
phpMyAdmin Installation
Access phpMyAdmin through ISPConfig:
- Navigate to “Tools” → “Database” in ISPConfig
- Access phpMyAdmin directly for advanced database management
- Ensure secure access controls are in place
Performance Monitoring
Monitor database performance regularly:
- Check slow query logs for optimization opportunities
- Monitor disk I/O for potential bottlenecks
- Adjust configuration parameters based on observed usage patterns
Proper database management ensures reliable storage and retrieval of website data.
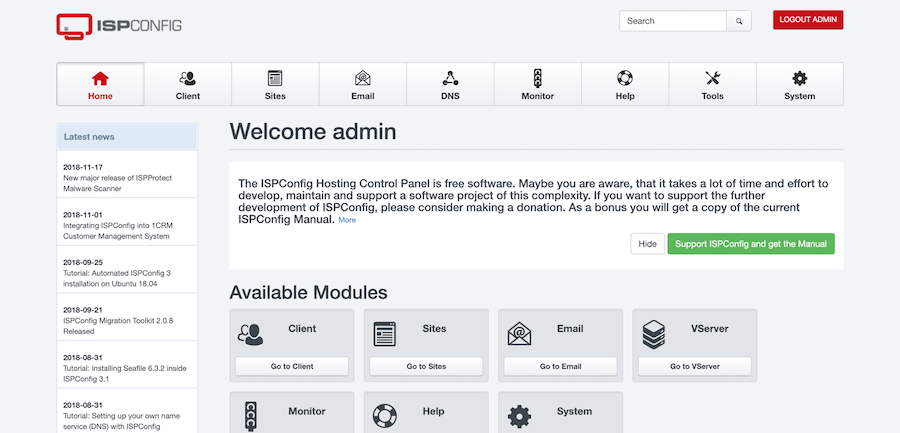
Accessing ISPConfig Control Panel
After installation completes, access the ISPConfig control panel to begin managing your server.
First Login Procedure
Access the ISPConfig panel through your web browser:
- Navigate to
https://your-server-ip:8080orhttps://your-server-hostname:8080 - Enter the administrator username and password created during installation
- Accept the self-signed SSL certificate (or replace with a trusted certificate)
HTTPS Configuration
For secure access to the control panel:
- Navigate to “System” → “Server Config” → “Web”
- Upload or generate SSL certificates for the panel
- Configure trusted certificates to avoid browser warnings
Multi-User Access
ISPConfig supports multiple user roles:
- Administrator: Full system access
- Reseller: Can create and manage clients
- Client: Can manage their own websites and services
- Email User: Limited access to email settings only
Create appropriate users with the minimum necessary permissions for security.
Post-Installation Tasks
After successful installation, perform these important tasks to complete your server setup.
System Verification
Verify that all services are running correctly:
systemctl status httpd mariadb postfix dovecot pure-ftpd namedAddress any services showing errors or warnings.
Creating Your First Website
Through the ISPConfig interface:
- Navigate to “Sites” → “Website”
- Click “Add new website”
- Enter domain information and select appropriate options
- Configure document root and PHP settings
- Enable desired features (SSL, statistics, etc.)
Setting Up Email Accounts
For your first domain:
- Go to “Email” → “Email Mailbox”
- Add new email accounts
- Configure forwarding or auto-responders as needed
- Test email delivery and reception
Adding DNS Records
Ensure proper DNS configuration:
- Navigate to “DNS” → “Zones”
- Add all necessary records for your domain
- Verify propagation with
digornslookupcommands
Configuring Backups
Implement a comprehensive backup strategy:
- Configure automated backups through ISPConfig
- Set appropriate backup schedules and retention
- Verify backup integrity regularly
- Implement off-server backup storage
Regular maintenance and monitoring will ensure continued optimal performance of your ISPConfig installation.
Updating and Maintaining ISPConfig
Regular updates are essential for security and functionality. This section covers the update procedures for ISPConfig.
Update Procedure
Update ISPConfig through the interface:
- Navigate to “System” → “ISPConfig Update”
- Check for available updates
- Apply updates following the on-screen instructions
- Review release notes for important changes
Alternatively, use the command line:
cd /tmp
wget https://www.ispconfig.org/downloads/ISPConfig-3.2-latest.tar.gz
tar xzf ISPConfig-3.2-latest.tar.gz
cd ispconfig3_install/install/
php -q update.phpSystem Maintenance
Regularly maintain the underlying system:
- Update Fedora packages:
dnf update -y - Restart services as needed after updates
- Monitor system logs for errors
- Perform regular security audits
Backup Procedures
Implement comprehensive backup strategies:
- Database backups:
mysqldump --all-databases > all_databases.sql - Configuration backups:
/etc/directory and service configurations - Website content: Regular backups of
/var/www/ - ISPConfig settings: Backup
/usr/local/ispconfig/
Version Upgrade Considerations
When upgrading to major new versions:
- Review compatibility notes carefully
- Test upgrades in a staging environment first
- Create complete system backups before upgrading
- Follow version-specific upgrade instructions
Regular maintenance ensures your ISPConfig installation remains secure and functional.
Troubleshooting Common Issues
Even with careful installation, issues may arise. This section addresses common problems and their solutions.
Installation Failures
For installation script errors:
- Check system requirements are met
- Review logs for specific error messages:
/tmp/ispconfig_setup/install.log - Ensure all required packages are installed
- Verify network connectivity and DNS resolution
Service Startup Problems
If services fail to start:
- Check service status:
systemctl status service-name - Review service logs:
journalctl -u service-name - Verify configuration file syntax
- Check for port conflicts with
netstat -tuln
Permission-Related Issues
For file permission problems:
- Verify ownership of web directories:
chown -R user:group /path - Check SELinux contexts if using enforcing mode
- Review directory permissions:
chmod -R 755 /path - Check service user permissions in configuration files
Network and Firewall Troubleshooting
For connectivity issues:
- Verify firewall settings:
firewall-cmd --list-all - Test port connectivity:
telnet hostname port - Check for IP binding issues in service configurations
- Verify DNS resolution for hostnames
Security Best Practices
Implement these security measures to protect your ISPConfig installation and hosted services.
Securing the Control Panel
Enhance ISPConfig panel security:
- Change default ports (8080/8081) to non-standard values
- Implement IP-based access restrictions
- Use strong, unique passwords for all accounts
- Install trusted SSL certificates for panel access
Password Policies
Enforce strong password requirements:
- Configure password complexity requirements in ISPConfig
- Implement regular password rotation for administrative accounts
- Use password managers for generating and storing complex passwords
- Enable two-factor authentication where available
SSL/TLS Implementation
Secure all services with encryption:
- Install Let’s Encrypt certificates through ISPConfig
- Configure appropriate cipher suites and protocols
- Implement HSTS for web services
- Regularly test SSL configuration with online tools
Brute Force Protection
Prevent unauthorized access attempts:
- Install and configure fail2ban through ISPConfig
- Set appropriate ban times and attempt thresholds
- Monitor authentication logs regularly
- Implement connection rate limiting
Regular Security Audits
Maintain ongoing security practices:
- Regularly scan for vulnerabilities with tools like Lynis
- Monitor system logs for suspicious activity
- Keep all software components updated
- Review user accounts and access permissions regularly
Congratulations! You have successfully installed ISPConfig. Thanks for using this tutorial for installing the ISPConfig on your Fedora 42 Linux system. For additional help or useful information, we recommend you check the official ISPConfig website.