How To Install ISPConfig on Rocky Linux 10

ISPConfig stands as one of the most powerful open-source hosting control panels available today. This comprehensive web hosting control panel simplifies the complex task of managing web servers, email systems, DNS records, and client hosting services through an intuitive web interface. Rocky Linux 10, as a stable enterprise-grade distribution and CentOS successor, provides an excellent foundation for hosting environments that demand reliability and long-term support.
This detailed guide will walk system administrators, web hosting professionals, and IT enthusiasts through the complete process of installing ISPConfig on Rocky Linux 10. From initial system preparation to advanced security configuration, every step is covered to ensure a successful deployment. By the end of this tutorial, you’ll have a fully functional ISPConfig installation capable of managing multiple websites, email accounts, databases, and DNS records with professional-grade capabilities.
The installation process involves setting up a complete LAMP stack (Linux, Apache, MySQL/MariaDB, PHP), configuring essential services like Postfix and Dovecot for email functionality, and implementing proper security measures. ISPConfig’s 2025 roadmap includes official Rocky Linux support, validating this installation approach and ensuring future compatibility.
Prerequisites and System Requirements
Hardware Requirements
Before beginning the ISPConfig installation on Rocky Linux 10, ensuring adequate hardware resources is crucial for optimal performance. The minimum hardware specifications include 1 GB RAM, though 2 GB or more is strongly recommended for production environments. Disk space requirements start at 10 GB free space, but 20 GB or more provides comfortable room for system growth and client data.
A 64-bit CPU architecture (x86_64 or AMD64) is mandatory for Rocky Linux 10 compatibility. These baseline specifications support basic hosting needs with a few websites and email accounts. Production environments serving multiple clients should consider significantly higher specifications based on expected traffic volumes and concurrent user counts.
Rocky Linux 10 documentation specifies 40 GB+ for GUI installations, though server installations require less space. Insufficient hardware resources commonly lead to poor performance, installation failures, and service instability. Virtual private servers (VPS) or dedicated servers meeting these requirements work excellently for ISPConfig deployments.
Software Prerequisites
A clean Rocky Linux 10 installation provides the optimal starting point for ISPConfig deployment. Root access or sudo privileges are essential for system configuration and service management throughout the installation process. Stable internet connectivity enables package downloads and repository access during installation.
The complete LAMP stack forms the foundation of ISPConfig functionality. Apache web server handles HTTP requests and virtual host management. MariaDB database server stores ISPConfig configuration data and client website databases. PHP with essential modules provides scripting capabilities for the control panel and hosted websites.
Additional services integrate seamlessly with ISPConfig for comprehensive hosting functionality. Postfix mail server manages email delivery and routing. Dovecot IMAP/POP3 server enables email retrieval for clients. Pure-FTPD provides secure file transfer capabilities. BIND DNS server handles domain name resolution and DNS record management.
Starting with a fresh, minimal Rocky Linux 10 installation prevents conflicts with existing services and ensures clean dependency resolution. Previously configured services may interfere with ISPConfig’s automated setup process.
System Preparation and Initial Setup
Updating Rocky Linux 10
System updates ensure the latest security patches and software versions before ISPConfig installation begins. The DNF package manager handles all package operations on Rocky Linux 10 systems. Execute the following command to update all installed packages:
sudo dnf update -yThis command downloads and installs all available updates automatically. The -y flag confirms all prompts without user intervention. Major kernel updates may require system reboot to activate new kernel versions. Check for required reboots using:
needs-restarting -rVerify the update process completed successfully by checking the DNF history:
sudo dnf historyUpdated systems provide better compatibility with ISPConfig packages and reduce security vulnerabilities. Allow adequate time for updates to complete, especially on slower internet connections.
Network Configuration
Proper network configuration ensures ISPConfig services function correctly across the network infrastructure. Rocky Linux 10 provides multiple tools for network interface management. The nmtui command launches a text-based graphical interface for network configuration:
sudo nmtuiConfigure static IP addresses for production servers to ensure consistent network accessibility. Set appropriate subnet masks, gateway addresses, and DNS servers for your network environment. Alternative command-line configuration uses nmcli commands:
sudo nmcli connection modify "connection-name" ipv4.addresses "192.168.1.100/24"
sudo nmcli connection modify "connection-name" ipv4.gateway "192.168.1.1"
sudo nmcli connection modify "connection-name" ipv4.dns "8.8.8.8,8.8.4.4"
sudo nmcli connection modify "connection-name" ipv4.method manual
sudo nmcli connection up "connection-name"Network configuration affects ISPConfig’s multi-service architecture, particularly email and DNS services requiring reliable connectivity. Test network connectivity after configuration changes to ensure proper functionality.
Hostname and FQDN Setup
Hostname and Fully Qualified Domain Name (FQDN) configuration is critical for ISPConfig functionality. Many services depend on proper hostname resolution, including email delivery and SSL certificate generation. Set the system hostname using the hostnamectl command:
sudo hostnamectl set-hostname server.example.comReplace server.example.com with your actual FQDN. Edit the /etc/hosts file to include proper hostname resolution:
sudo nano /etc/hostsAdd the following line with your actual IP address and hostname:
192.168.1.100 server.example.com serverVerify hostname configuration using:
hostnamectl status
hostname -fBoth commands should return your configured FQDN. Incorrect hostname configuration causes various ISPConfig service failures, particularly with email functionality and SSL certificate operations.
Installing LAMP Stack Components
Apache Web Server Installation
Apache HTTP Server forms the foundation of the web hosting environment. Rocky Linux 10 repositories include current Apache versions optimized for enterprise use. Install Apache using the DNF package manager:
sudo dnf install httpd -yThis command installs Apache and required dependencies automatically. Enable Apache to start automatically at boot time:
sudo systemctl enable httpdStart the Apache service immediately:
sudo systemctl start httpdConfigure firewall rules to allow HTTP and HTTPS traffic:
sudo firewall-cmd --permanent --add-service=http
sudo firewall-cmd --permanent --add-service=https
sudo firewall-cmd --reloadVerify Apache installation by accessing your server’s IP address through a web browser. The default Apache test page confirms successful installation. Check Apache service status using:
sudo systemctl status httpdMariaDB Database Server Setup
MariaDB provides robust database services for ISPConfig configuration storage and client website databases. Install MariaDB server and client packages:
sudo dnf install mariadb-server mariadb -yEnable MariaDB to start automatically at system boot:
sudo systemctl enable mariadbStart the MariaDB service:
sudo systemctl start mariadbSecure the MariaDB installation using the security script:
sudo mysql_secure_installationThis interactive script prompts for several security configurations. Set a strong root password when prompted. Answer “Y” to remove anonymous users, disallow root login remotely, remove the test database, and reload privilege tables.
Test MariaDB connectivity:
mysql -u root -pEnter the root password you configured during the security installation. ISPConfig requires specific database privileges and supports both traditional mysql_native_password and newer authentication methods.
PHP Installation and Configuration
PHP provides server-side scripting capabilities for ISPConfig and hosted websites. Install PHP along with essential modules required by ISPConfig:
sudo dnf install php php-mysql php-gd php-curl php-mbstring php-xml php-zip php-opcache php-json php-intl php-ldap php-imap -yEach PHP module serves specific ISPConfig functionality. The php-mysql module enables database connectivity. Graphics functions require php-gd for image manipulation. Network operations use php-curl for HTTP requests. Text processing relies on php-mbstring for multi-byte string handling.
Configure PHP settings for optimal ISPConfig performance. Edit the main PHP configuration file:
sudo nano /etc/php.iniLocate and modify these settings:
memory_limit = 256M
upload_max_filesize = 64M
post_max_size = 64M
max_execution_time = 300ISPConfig benefits from PHP-FPM for improved performance with multiple websites. Install PHP-FPM:
sudo dnf install php-fpm -y
sudo systemctl enable php-fpm
sudo systemctl start php-fpmRestart Apache to load PHP modules:
sudo systemctl restart httpdCreate a PHP test file to verify installation:
echo "" | sudo tee /var/www/html/info.phpAccess http://your-server-ip/info.php to view PHP configuration details.
Additional Services Installation
Complete ISPConfig functionality requires several additional services for email, file transfer, and DNS management. Install Postfix mail server for email delivery:
sudo dnf install postfix -y
sudo systemctl enable postfix
sudo systemctl start postfixInstall Dovecot for IMAP/POP3 email retrieval services:
sudo dnf install dovecot -y
sudo systemctl enable dovecotPure-FTPD provides secure file transfer capabilities:
sudo dnf install pure-ftpd -y
sudo systemctl enable pure-ftpdBIND DNS server handles domain name resolution and DNS record management:
sudo dnf install bind bind-utils -y
sudo systemctl enable namedAdditional useful packages for ISPConfig include:
sudo dnf install mailx awstats webalizer fail2ban rkhunter -yThese packages provide log analysis, security monitoring, and system maintenance capabilities that integrate with ISPConfig’s management interface.
ISPConfig Download and Installation
Obtaining ISPConfig Files
ISPConfig installation begins with downloading the latest stable version from official sources. Always use official download locations to ensure file integrity and security. Navigate to a temporary directory for the download:
cd /tmpDownload the latest ISPConfig stable version using wget:
wget https://www.ispconfig.org/downloads/ISPConfig-3-stable.tar.gzExtract the downloaded archive:
tar -xzf ISPConfig-3-stable.tar.gzNavigate to the extracted ISPConfig directory:
cd ispconfig3_install/install/The installation directory contains the PHP installation script and various configuration templates. List directory contents to verify extraction:
ls -laFor automated installations, ISPConfig provides a streamlined installer script:
wget -O - https://get.ispconfig.org | sh -This command downloads and executes the automated installer, which handles dependency installation and basic configuration automatically.
Running the Installation Script
Execute the ISPConfig installation script with PHP interpreter:
sudo php -q install.phpThe installation script presents an interactive configuration process. Select “Standard” installation for most hosting scenarios when prompted. This option configures ISPConfig for single-server environments with integrated services.
Web server selection appears early in the installation. Choose Apache when prompted unless specific requirements demand Nginx. Apache integration provides broader compatibility and established configuration templates.
SSL certificate configuration offers several options. Select “yes” for SSL certificate generation to enable secure HTTPS access to the ISPConfig control panel. Self-signed certificates work for testing environments, while production systems benefit from proper SSL certificates.
Database configuration requires the MySQL root password configured during MariaDB setup. The installer creates necessary databases and user accounts automatically. Secure passwords protect ISPConfig database access.
Optional components like Roundcube webmail provide additional functionality. Enable webmail installation for integrated email access through the control panel. SpamAssassin and ClamAV enhance email security through spam filtering and antivirus scanning.
The installation process typically completes within 10-15 minutes depending on system performance and selected options. Monitor installation progress and address any error messages immediately.
Installation Configuration Options
ISPConfig presents numerous configuration choices during installation affecting final system behavior. Server configuration determines ISPConfig’s operational mode. Single-server installations integrate all services on one machine. Multi-server setups distribute services across multiple servers for scalability.
Expert mode enables advanced configuration options for experienced administrators. Standard mode provides suitable defaults for most installations. Expert mode allows custom port configurations, service selections, and integration options.
SSL certificate configuration impacts security and browser compatibility. Let’s Encrypt integration provides automated certificate management for production domains. Self-signed certificates suffice for internal testing but trigger browser security warnings.
Database options include MySQL/MariaDB selection and authentication method configuration. ISPConfig supports both traditional and newer authentication mechanisms. Root database access enables complete ISPConfig database management.
Email configuration determines mail server integration and security features. Enable SpamAssassin for spam filtering and ClamAV for antivirus protection. Amavisd integration provides comprehensive email security management.
Installation logs capture detailed progress information and error messages. Monitor logs during installation to identify potential issues early. Log files remain available for troubleshooting post-installation problems.
Post-Installation Configuration
Accessing ISPConfig Control Panel
After successful installation, access the ISPConfig web interface through your web browser. The standard URL format uses port 8080:
https://your-server-ip:8080Replace your-server-ip with your server’s actual IP address or configured domain name. Browser security warnings appear when accessing self-signed SSL certificates. Click “Advanced” and proceed to the site despite warnings for testing environments.
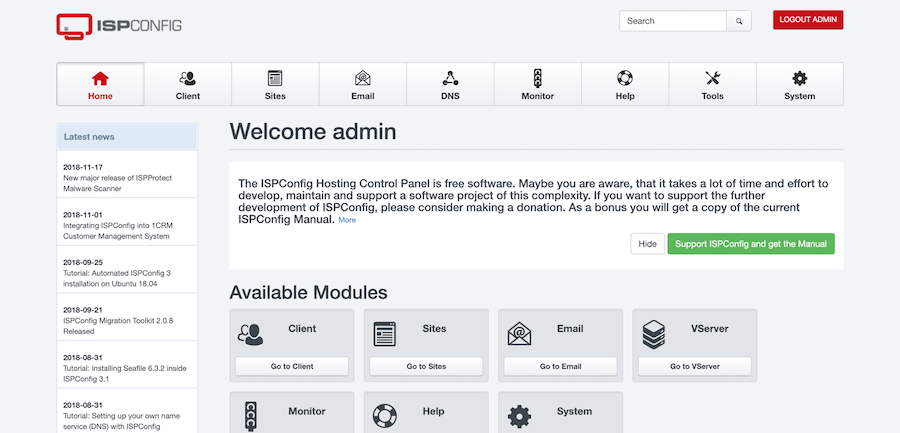
Default login credentials use username “admin” and password “admin”. These credentials provide full administrative access to the ISPConfig control panel. Change these credentials immediately after first login to prevent unauthorized access.
Firewall configuration must allow port 8080 access:
sudo firewall-cmd --permanent --add-port=8080/tcp
sudo firewall-cmd --reloadCommon access issues include firewall blocking, incorrect SSL configuration, or service startup problems. Verify Apache and ISPConfig services are running:
sudo systemctl status httpd
sudo systemctl status mysqlNetwork connectivity tests help identify access problems:
netstat -tlnp | grep :8080Initial Setup and Security Configuration
First-time ISPConfig access requires immediate security configuration. Change the default administrator password through the System > CP Users menu. Select a strong password containing uppercase letters, lowercase letters, numbers, and special characters.
Configure essential server settings through the System menu. Set appropriate timezone for log entries and scheduled tasks. Configure administrative email addresses for system notifications and alerts. Update interface language preferences if needed.
Review server configuration settings before adding clients or websites. Verify Apache, PHP, and database configurations match your requirements. SSL certificate configuration affects website security options. DNS server settings impact domain management capabilities.
User interface familiarization improves administrative efficiency. The main navigation includes Sites, Email, DNS, Client, and System sections. Each section contains relevant management tools and configuration options. Context-sensitive help provides guidance for specific features.
Security hardening extends beyond password changes. Enable session timeouts for automatic logout after inactivity. Configure IP address restrictions for administrative access when possible. Regular security updates maintain protection against emerging threats.
Creating First Client and Website
ISPConfig operates on a client-website hierarchy system. Clients represent customers or organizational units. Websites belong to specific clients and inherit permissions and resource limitations. Create the first client account through the Client > Add Client menu.
Client configuration includes contact information, resource limits, and service permissions. Set appropriate limits for disk space, traffic, email accounts, and databases based on hosting plans. Enable or disable services like FTP access, SSH access, and DNS management per client requirements.
Website creation follows client establishment. Navigate to Sites > Add Website and select the appropriate client. Configure the domain name, document root path, and basic web server settings. Enable PHP and select appropriate PHP versions for website requirements.
DNS configuration accompanies website creation for proper domain resolution. ISPConfig can manage DNS records automatically or integrate with external DNS providers. Configure A records, MX records, and other DNS entries as needed for complete domain functionality.
FTP user creation enables file management capabilities. Create FTP accounts through the Sites > FTP User menu. Associate FTP users with specific websites for isolated access. SSH access provides command-line file management for advanced users.
Website testing verifies proper functionality. Upload test files through FTP and verify web browser access. Check PHP functionality with simple test scripts. Monitor error logs for any configuration issues requiring attention.
Security Configuration and Hardening
Firewall Configuration
Rocky Linux 10’s firewalld service provides robust network security through rule-based traffic filtering. ISPConfig requires specific ports open for proper operation across all integrated services. Configure essential port access using firewall-cmd commands:
sudo firewall-cmd --permanent --add-service=http
sudo firewall-cmd --permanent --add-service=https
sudo firewall-cmd --permanent --add-port=8080/tcp
sudo firewall-cmd --permanent --add-service=ssh
sudo firewall-cmd --permanent --add-service=smtp
sudo firewall-cmd --permanent --add-service=smtp-submission
sudo firewall-cmd --permanent --add-service=imap
sudo firewall-cmd --permanent --add-service=imaps
sudo firewall-cmd --permanent --add-service=pop3
sudo firewall-cmd --permanent --add-service=pop3s
sudo firewall-cmd --permanent --add-service=ftp
sudo firewall-cmd --permanent --add-service=dnsReload firewall configuration to activate changes:
sudo firewall-cmd --reloadVerify open ports and active rules:
sudo firewall-cmd --list-allAdvanced firewall configurations include rate limiting and fail2ban integration for enhanced security. Configure rate limiting for SSH access:
sudo firewall-cmd --permanent --add-rich-rule="rule service name=ssh limit value=3/m accept"Balance security requirements with service functionality. Overly restrictive rules may prevent legitimate access while inadequate protection exposes services to attacks.
SSL/TLS Certificate Setup
SSL/TLS encryption secures communications between clients and servers. ISPConfig supports multiple SSL certificate sources including Let’s Encrypt automated certificates and commercial certificate authorities. Install Certbot for Let’s Encrypt integration:
sudo dnf install certbot python3-certbot-apache -yGenerate SSL certificates for your domain:
sudo certbot --apacheCertbot automatically configures Apache virtual hosts for SSL termination and creates automatic renewal cron jobs. Verify certificate installation:
sudo certbot certificatesISPConfig’s SSL management interface enables certificate configuration for individual websites. Navigate to Sites > Select Website > Options tab for SSL configuration options. Enable SSL and redirect HTTP traffic to HTTPS for enhanced security.
Monitor SSL certificate expiration dates and renewal processes. Certbot includes automatic renewal through systemd timers:
sudo systemctl status certbot.timerTest renewal process manually to verify functionality:
sudo certbot renew --dry-runISPConfig 3.4 introduces improved Certbot account management and multiple account handling capabilities for enhanced certificate management.
Additional Security Best Practices
Comprehensive security extends beyond firewall and SSL configuration. Regular system updates maintain current security patches for Rocky Linux 10, ISPConfig, and all installed components. Automate updates where appropriate while maintaining change control procedures.
SSH security hardening significantly improves remote access security. Disable root login through SSH by editing /etc/ssh/sshd_config:
sudo nano /etc/ssh/sshd_configModify or add these configurations:
PermitRootLogin no
PasswordAuthentication no
PubkeyAuthentication yes
Port 2222Change the default SSH port from 22 to a non-standard port like 2222. Configure key-based authentication and disable password authentication for enhanced security.
Log monitoring identifies suspicious activity and security breaches. Install and configure logwatch for automated log analysis:
sudo dnf install logwatch -yConfigure logwatch to send daily reports via email. Monitor authentication logs, web server logs, and mail server logs for unusual activity patterns.
Backup procedures protect against data loss and enable rapid recovery from security incidents. ISPConfig 3.3 introduces automatic nightly backup features simplifying backup management. Implement off-site backup storage for comprehensive protection.
Intrusion detection systems like fail2ban automatically respond to suspicious activity:
sudo dnf install fail2ban -y
sudo systemctl enable fail2ban
sudo systemctl start fail2banConfigure fail2ban rules for SSH, HTTP, and email services to prevent brute force attacks.
Troubleshooting Common Issues
Installation Error Resolution
ISPConfig installation problems typically stem from dependency issues, insufficient system resources, or configuration conflicts. Identify installation errors through detailed log analysis. ISPConfig creates installation logs in the /tmp directory during setup.
Missing package dependencies cause installation failures. Verify all required packages are installed:
sudo dnf groupinstall "Development Tools"
sudo dnf install wget curl unzipPHP module dependencies affect ISPConfig functionality. Verify essential PHP modules are loaded:
php -m | grep -E "(mysql|gd|curl|mbstring|xml|zip)"Database connection problems prevent ISPConfig installation. Test MySQL/MariaDB connectivity and verify root password accuracy:
mysql -u root -p -e "SHOW DATABASES;"Memory and disk space constraints cause installation timeouts and failures. Monitor system resources during installation:
free -h
df -hClean installation procedures resolve persistent installation problems. Remove partial installations and clear temporary files before retry attempts:
sudo rm -rf /usr/local/ispconfig
sudo rm -rf /tmp/ispconfig*Service Configuration Problems
Post-installation service issues affect ISPConfig functionality across integrated components. Apache configuration problems prevent website access. Verify Apache syntax and configuration:
sudo httpd -t
sudo systemctl status httpdReview Apache error logs for specific problem identification:
sudo tail -f /var/log/httpd/error_logEmail delivery problems affect client communication and system notifications. Test Postfix configuration and connectivity:
sudo postfix check
sudo systemctl status postfixDNS resolution issues impact website and email functionality. Verify BIND configuration and test DNS queries:
sudo named-checkconf
dig @localhost example.comService conflicts occur when multiple applications compete for resources or ports. Identify port conflicts using netstat:
sudo netstat -tlnp | grep :80
sudo netstat -tlnp | grep :25Configuration file validation prevents service startup failures. Most services include syntax checking commands:
sudo nginx -t # For Nginx configurations
sudo postfix check # For Postfix configurationsPerformance Optimization Tips
ISPConfig performance optimization enhances user experience and system efficiency. PHP configuration adjustments improve website response times and resource utilization. Enable OPCache for compiled PHP bytecode caching:
sudo nano /etc/php.iniConfigure OPCache settings:
opcache.enable=1
opcache.memory_consumption=256
opcache.max_accelerated_files=4000
opcache.revalidate_freq=60MariaDB performance tuning optimizes database operations and query execution. Configure query cache and buffer sizes:
sudo nano /etc/my.cnf.d/server.cnfAdd performance optimization settings:
[mysqld]
query_cache_type=1
query_cache_size=64M
innodb_buffer_pool_size=256MApache performance improvements handle increased concurrent connections efficiently. Configure worker modules and connection limits:
sudo nano /etc/httpd/conf.modules.d/00-mpm.confSystem monitoring identifies performance bottlenecks and resource constraints. Install monitoring tools:
sudo dnf install htop iotop sysstat -yISPConfig 3.3 introduces real-time performance monitoring with graphical system resource displays. These tools provide immediate feedback on system performance and resource utilization.
Caching mechanisms reduce server load and improve response times. Configure browser caching through Apache modules:
sudo dnf install mod_expires mod_deflate -yMaintenance and Updates
Keeping ISPConfig Updated
Regular ISPConfig updates maintain security patches, bug fixes, and new feature availability. ISPConfig follows a structured release schedule with stable versions, release candidates, and development builds. Download the latest stable version from official sources for production systems.
Update preparation includes complete system backups covering ISPConfig configuration, client data, and database contents. Verify backup integrity before proceeding with updates. Document current ISPConfig version and installed components for rollback procedures if needed.
Download and extract the latest ISPConfig version:
cd /tmp
wget https://www.ispconfig.org/downloads/ISPConfig-3-stable.tar.gz
tar -xzf ISPConfig-3-stable.tar.gz
cd ispconfig3_install/install/Execute the update script:
sudo php -q update.phpThe update script preserves existing configuration settings and client data while upgrading ISPConfig components. Review update documentation for version-specific changes or requirements before applying updates.
Monitor system functionality after updates to identify any issues requiring attention. Test critical features including website access, email delivery, and control panel functionality. Update logs provide detailed information about applied changes and potential issues.
ISPConfig 3.3 and 3.4 releases introduce significant new features including PostgreSQL support, Docker integration, and WordPress management tools. Plan update schedules around these major releases to take advantage of enhanced capabilities.
System Maintenance Tasks
Comprehensive maintenance schedules ensure optimal ISPConfig performance and reliability. Rocky Linux 10 system updates provide security patches and software improvements through the DNF package manager:
sudo dnf update -y
sudo dnf autoremove -ySchedule regular system updates through cron jobs for automated maintenance. Consider reboot requirements after kernel updates and plan maintenance windows accordingly.
Log file management prevents disk space exhaustion and maintains system performance. Configure log rotation for ISPConfig, Apache, and system logs:
sudo nano /etc/logrotate.d/ispconfigDatabase maintenance optimizes ISPConfig and client database performance. Schedule regular database optimization and backup verification:
mysqlcheck -u root -p --optimize --all-databasesDisk usage monitoring prevents storage capacity issues affecting system operation. Monitor disk usage and implement cleanup procedures:
df -h
du -sh /var/www/*Service uptime monitoring ensures ISPConfig components remain operational. Implement monitoring solutions for Apache, MariaDB, Postfix, and other critical services. Configure automated alerts for service failures or performance degradation.
ISPConfig 3.3 introduces automatic nightly backup functionality simplifying backup management and reducing administrative overhead. Configure backup retention policies and off-site storage for comprehensive data protection.
Congratulations! You have successfully installed ISPConfig. Thanks for using this tutorial for installing the ISPConfig on your Rocky Linux 10 system. For additional help or useful information, we recommend you check the official ISPConfig website.