How To Install OwnCloud on AlmaLinux 10

Self-hosted cloud storage has become essential for organizations and individuals seeking complete control over their data. OwnCloud stands out as a powerful, open-source file sharing and collaboration platform that offers enterprise-grade features without the privacy concerns of third-party cloud providers. AlmaLinux 10, with its enterprise-level stability and long-term support, provides the perfect foundation for hosting OwnCloud in production environments.
This comprehensive guide walks through every step of installing and configuring OwnCloud on AlmaLinux 10 using Nginx, PHP 8, and MariaDB. From initial system preparation to SSL certificate implementation and security hardening, this tutorial covers everything needed to deploy a fully functional, secure cloud storage server. Whether setting up personal file storage or deploying a solution for team collaboration, this guide provides the detailed instructions required for a successful implementation.
What is OwnCloud?
OwnCloud is a self-hosted file synchronization and sharing platform that gives users complete control over their data. Unlike commercial cloud storage solutions such as Dropbox or Google Drive, OwnCloud runs on private servers, ensuring data privacy and eliminating subscription costs. The platform supports file sync and share capabilities, calendar integration, contacts management, document collaboration, and extensive customization through its app ecosystem.
Three editions are available: Community Edition (free and open-source), Standard Edition, and Enterprise Edition. The Community Edition provides all core functionality needed for most deployment scenarios. OwnCloud emphasizes security, offering features like file encryption at rest, secure external sharing, and comprehensive access controls. Organizations worldwide trust OwnCloud for managing sensitive data while maintaining compliance with data protection regulations.
While similar to Nextcloud, OwnCloud focuses more heavily on enterprise file collaboration and maintains a more conservative approach to feature development, prioritizing stability and reliability. This makes it particularly suitable for production environments where consistent performance matters most.
Why Choose AlmaLinux 10 for OwnCloud?
AlmaLinux 10 represents a major milestone in community-driven enterprise Linux distributions. As a 1:1 binary compatible fork of Red Hat Enterprise Linux (RHEL), AlmaLinux delivers enterprise-grade stability without licensing costs. The distribution provides long-term support, predictable release cycles, and extensive security updates—all critical factors for hosting production services like OwnCloud.
AlmaLinux 10 introduces significant improvements including frame pointers for better performance analysis, extended x86-64-v2 architecture support, and enhanced security features. The operating system benefits from rigorous testing and a strong community backing, ensuring both reliability and prompt security patches. For system administrators familiar with RHEL or CentOS, AlmaLinux offers a seamless migration path with familiar tools and package management.
The combination of AlmaLinux’s rock-solid foundation with OwnCloud’s mature codebase creates an ideal environment for organizations requiring dependable, self-hosted cloud storage. Both projects prioritize stability over bleeding-edge features, making them perfect companions for business-critical deployments.
Prerequisites and System Requirements
Server Requirements
A minimum hardware configuration of 2 CPU cores and 4GB RAM provides adequate performance for small deployments with 5-10 users. Production environments with 50+ users should provision at least 4 CPU cores and 8GB RAM. Storage requirements vary based on usage, but allocating at least 20GB for the operating system and OwnCloud installation is recommended, with additional storage for user data mounted separately.
Virtual machines work perfectly for OwnCloud deployments. Cloud providers like DigitalOcean, Linode, or AWS EC2 offer suitable instances. Physical servers provide better I/O performance for installations with heavy file access patterns.
Software Requirements
Begin with a fresh AlmaLinux 10 installation with root or sudo administrative access. OwnCloud has specific software dependencies that must be met: PHP 8 (critically important—newer versions are not yet fully supported), MariaDB 10.11 or MySQL 8.0+, and either Nginx or Apache web server. This guide focuses on Nginx for its superior performance and resource efficiency.
PHP extensions required include bz2, ctype, curl, fpm, gd, intl, json, fileinfo, libxml, mbstring, mysqlnd, openssl, posix, session, simplexml, xmlreader, xmlwriter, zip, and zlib. These extensions enable OwnCloud’s core functionality including image thumbnails, database connectivity, file compression, and internationalization support.
Network Requirements
A registered domain name or subdomain pointed to the server IP address improves accessibility and enables SSL certificate installation. While optional for testing, production deployments should always use proper domain names. Firewall configuration must allow inbound traffic on ports 80 (HTTP), 443 (HTTPS), and 22 (SSH for administration).
Static IP addresses prevent connection disruptions and simplify DNS management. Most hosting providers offer static IPs by default, but verify this before beginning installation.
Step 1: Update AlmaLinux 10 System
Keeping the system updated prevents conflicts, ensures security patches are applied, and provides the latest package versions. Start by connecting to the server via SSH and switching to the root user or using sudo for all commands.
Update all installed packages:
sudo dnf update -yThis command refreshes package repositories and upgrades all outdated software. The -y flag automatically confirms update prompts. The process typically takes 2-5 minutes depending on connection speed and the number of updates available.
Check if a reboot is required:
sudo needs-restarting -rIf kernel updates were installed, reboot the system:
sudo rebootAfter rebooting, verify the AlmaLinux version:
cat /etc/almalinux-releaseStarting with a fully updated system establishes a stable foundation and prevents dependency conflicts during OwnCloud installation.
Step 2: Install Required Dependencies
Several basic utilities are needed for downloading and extracting the OwnCloud package. While many AlmaLinux installations include these tools by default, explicitly installing them ensures availability.
Install wget, tar, and bzip2:
sudo dnf install wget tar bzip2 -yThese utilities serve specific purposes: wget downloads files from URLs, tar handles archive extraction, and bzip2 manages .bz2 compressed files. OwnCloud distributes its software as a tar.bz2 archive, making all three tools necessary.
Verify installation:
wget --version
tar --versionThese lightweight packages consume minimal system resources and provide essential functionality for the remaining installation steps.
Step 3: Install and Configure PHP 8
Understanding PHP Version Requirements
OwnCloud requires PHP 7.4 specifically due to compatibility and stability considerations. Newer PHP versions introduce breaking changes that OwnCloud has not yet fully adopted. AlmaLinux 10 ships with PHP 8.3 by default, necessitating the use of third-party repositories to install PHP 7.4.
Adding Remi Repository
The Remi repository provides current versions of PHP and extensions for Enterprise Linux distributions. Install the repository configuration:
sudo dnf install https://rpms.remirepo.net/enterprise/remi-release-10.rpm -yUpdate DNF metadata:
sudo dnf update -yList available PHP modules:
sudo dnf module list phpThis displays all PHP versions available from configured repositories.
Installing PHP 7.4
Reset the PHP module to clear any defaults:
sudo dnf module reset php -yEnable PHP 7.4 from Remi repository:
sudo dnf module enable php:remi-7.4 -yInstall PHP 7.4 with all required extensions:
sudo dnf install php php-cli php-fpm php-mysqlnd php-curl php-gd php-mbstring php-xml php-zip php-intl php-json php-bz2 php-opcache -yEach extension serves important functions: php-curl enables HTTP requests, php-gd processes images for thumbnails, php-intl provides internationalization support, php-json handles data interchange, php-mbstring manages multibyte character encoding, php-mysqlnd connects to MySQL/MariaDB databases, php-xml parses XML configurations, and php-zip compresses and extracts archives.
Configuring PHP-FPM
Start and enable PHP-FPM to run on boot:
sudo systemctl start php-fpm
sudo systemctl enable php-fpmVerify PHP version:
php -vThe output should display PHP 7.4.x. PHP-FPM (FastCGI Process Manager) efficiently handles PHP requests, processing multiple concurrent requests with minimal resource consumption.
Check PHP-FPM status:
sudo systemctl status php-fpmAn “active (running)” status indicates successful configuration.
Step 4: Install and Configure Nginx Web Server
Installing Nginx
Nginx provides exceptional performance for serving OwnCloud, handling both static files and PHP processing efficiently. Install Nginx from AlmaLinux repositories:
sudo dnf install nginx -yStart and enable Nginx:
sudo systemctl start nginx
sudo systemctl enable nginxVerify Nginx is running:
sudo systemctl status nginxTest web server accessibility by visiting http://your-server-ip in a browser. The default Nginx welcome page confirms successful installation.
Creating Virtual Host Configuration
Navigate to the Nginx configuration directory:
cd /etc/nginx/conf.dCreate a dedicated configuration file for OwnCloud:
sudo nano owncloud.confAdd the following configuration, replacing yourdomain.com with your actual domain:
upstream php-handler {
server unix:/run/php-fpm/www.sock;
}
server {
listen 80;
server_name yourdomain.com www.yourdomain.com;
root /var/www/html/yourdomain.com;
index index.php index.html;
client_max_body_size 512M;
fastcgi_buffers 64 4K;
gzip on;
gzip_vary on;
gzip_comp_level 4;
gzip_min_length 256;
gzip_types application/atom+xml application/javascript application/json text/css text/plain text/xml;
location = /robots.txt {
allow all;
log_not_found off;
access_log off;
}
location = /.well-known/carddav {
return 301 $scheme://$host/remote.php/dav;
}
location = /.well-known/caldav {
return 301 $scheme://$host/remote.php/dav;
}
location / {
try_files $uri $uri/ /index.php?$query_string;
}
location ~ ^/(?:build|tests|config|lib|3rdparty|templates|data)/ {
deny all;
}
location ~ ^/(?:\.|autotest|occ|issue|indie|db_|console) {
deny all;
}
location ~ \.php(?:$|/) {
fastcgi_split_path_info ^(.+\.php)(/.+)$;
include fastcgi_params;
fastcgi_param SCRIPT_FILENAME $document_root$fastcgi_script_name;
fastcgi_param PATH_INFO $fastcgi_path_info;
fastcgi_param HTTPS on;
fastcgi_param modHeadersAvailable true;
fastcgi_param front_controller_active true;
fastcgi_pass php-handler;
fastcgi_intercept_errors on;
fastcgi_request_buffering off;
}
location ~* \.(?:css|js|woff2?|svg|gif|map)$ {
try_files $uri /index.php$request_uri;
add_header Cache-Control "public, max-age=15778463";
access_log off;
}
error_log /var/log/nginx/owncloud_error.log;
access_log /var/log/nginx/owncloud_access.log;
}This configuration includes several critical elements. The upstream block defines PHP-FPM’s Unix socket for processing PHP files. The client_max_body_size directive allows file uploads up to 512MB. Gzip compression reduces bandwidth usage and improves page load times.
Security directives block access to sensitive directories like config, data, and lib. The PHP location block properly handles PHP file execution through PHP-FPM. Static file caching improves performance for frequently accessed resources.
Test Nginx configuration syntax:
sudo nginx -tA successful test shows “syntax is ok” and “test is successful.” Restart Nginx to apply changes:
sudo systemctl restart nginxStep 5: Install and Configure MariaDB Database
Installing MariaDB Server
OwnCloud supports multiple database backends including MySQL, MariaDB, PostgreSQL, and Oracle. MariaDB offers excellent performance, proven stability, and strong compatibility with OwnCloud. SQLite is available but not recommended for production due to performance limitations.
Install MariaDB 10.11:
sudo dnf install mariadb-server -yStart and enable MariaDB:
sudo systemctl start mariadb
sudo systemctl enable mariadbVerify MariaDB status:
sudo systemctl status mariadbSecuring MariaDB Installation
Run the security script to harden the installation:
sudo mysql_secure_installationFollow the prompts:
- Enter current root password (press Enter if none set)
- Set root password (choose a strong password)
- Remove anonymous users (Y)
- Disallow root login remotely (Y)
- Remove test database (Y)
- Reload privilege tables (Y)
These security measures prevent unauthorized access and eliminate unnecessary test accounts.
Creating OwnCloud Database
Log into MariaDB as root:
sudo mysql -u root -pEnter the root password when prompted. Create a dedicated database:
CREATE DATABASE owncloud_db;Create a database user with a strong password:
CREATE USER 'owncloud_user'@'localhost' IDENTIFIED BY 'your_strong_password_here';Replace your_strong_password_here with a complex password containing uppercase, lowercase, numbers, and special characters. Grant all privileges:
GRANT ALL PRIVILEGES ON owncloud_db.* TO 'owncloud_user'@'localhost';Flush privileges to ensure changes take effect:
FLUSH PRIVILEGES;Exit the database shell:
EXIT;Database credentials will be needed during OwnCloud’s web-based installation. Document these securely: database name (owncloud_db), username (owncloud_user), password, and host (localhost).
Step 6: Download and Extract OwnCloud
Create the document root directory:
sudo mkdir -p /var/www/html/yourdomain.comNavigate to the parent directory:
cd /var/www/htmlDownload the latest stable OwnCloud release:
sudo wget https://download.owncloud.com/server/stable/owncloud-complete-latest.tar.bz2This downloads the complete OwnCloud package including all dependencies. The file size is approximately 50-60MB depending on the version.
Extract the archive directly into the document root:
sudo tar -xjf owncloud-complete-latest.tar.bz2 -C yourdomain.com --strip-components=1The --strip-components=1 flag removes the top-level directory from the archive, extracting files directly into the target directory. Set proper ownership:
sudo chown -R nginx:nginx /var/www/html/yourdomain.comIf using Apache instead of Nginx, replace nginx:nginx with apache:apache. Configure directory permissions:
sudo chmod -R 755 /var/www/html/yourdomain.comThese permissions allow the web server to read and execute files while preventing unauthorized modifications. The data directory will require write permissions, which OwnCloud handles during installation.
Remove the downloaded archive:
sudo rm owncloud-complete-latest.tar.bz2Step 7: Configure Firewall Rules
AlmaLinux 10 uses firewalld by default for firewall management. Web access requires opening HTTP and HTTPS ports.
Check firewalld status:
sudo systemctl status firewalldIf inactive, start and enable it:
sudo systemctl start firewalld
sudo systemctl enable firewalldAdd HTTP and HTTPS services permanently:
sudo firewall-cmd --permanent --add-service=http
sudo firewall-cmd --permanent --add-service=httpsReload firewall to apply rules:
sudo firewall-cmd --reloadVerify active rules:
sudo firewall-cmd --list-allThe output should show http and https in the services list. These rules allow inbound connections on ports 80 and 443, enabling web browser access to OwnCloud.
For enhanced security, consider restricting SSH access to specific IP addresses or implementing fail2ban to prevent brute force attacks. Production environments should implement network-level security through cloud provider security groups or hardware firewalls.
Step 8: Configure SELinux (Security-Enhanced Linux)
SELinux provides mandatory access control, adding an additional security layer beyond standard permissions. AlmaLinux enables SELinux by default in enforcing mode.
Check SELinux status:
sestatusRecommended Approach: Configure SELinux
Rather than disabling SELinux, configure it to allow required OwnCloud operations. Set the httpd_unified boolean:
sudo setsebool -P httpd_unified 1This allows httpd (web server processes) to read and write to all directories labeled as httpd content. Set the correct SELinux context for OwnCloud directories:
sudo semanage fcontext -a -t httpd_sys_rw_content_t "/var/www/html/yourdomain.com/data(/.*)?"
sudo semanage fcontext -a -t httpd_sys_rw_content_t "/var/www/html/yourdomain.com/config(/.*)?"
sudo semanage fcontext -a -t httpd_sys_rw_content_t "/var/www/html/yourdomain.com/apps(/.*)?"
sudo restorecon -Rv /var/www/html/yourdomain.comThese commands grant write permissions to critical directories while maintaining SELinux protection.
Alternative Approach: Disable SELinux (Not Recommended)
For testing environments only, SELinux can be temporarily disabled:
sudo setenforce 0To permanently disable SELinux, edit the configuration file:
sudo nano /etc/selinux/configChange SELINUX=enforcing to SELINUX=disabled, then reboot. Production environments should never disable SELinux as it significantly reduces security.
Step 9: Complete Web-Based Installation
Access OwnCloud through a web browser by navigating to http://yourdomain.com or http://your-server-ip. The installation wizard appears automatically on first access.
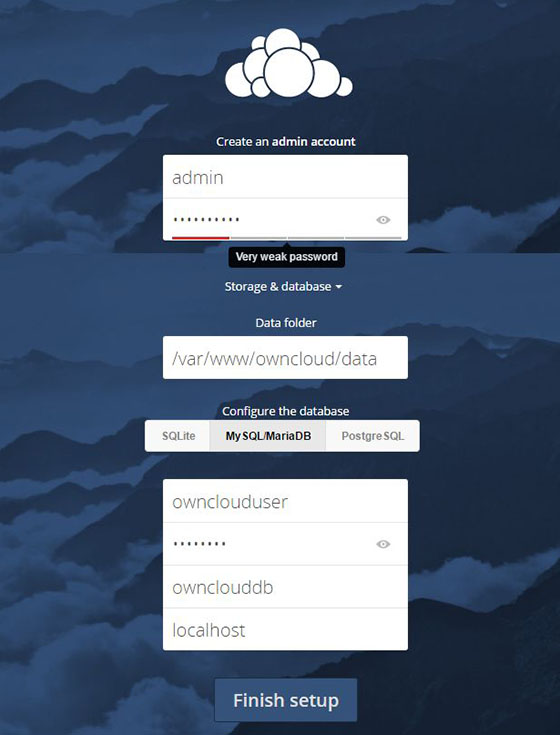
Creating Admin Account
Enter the desired administrative username and password in the top section. Avoid common usernames like “admin” or “administrator” for improved security. Create a strong password containing at least 12 characters with mixed case, numbers, and special characters.
The admin account has full system privileges including user management, app installation, and system configuration. Protect these credentials carefully.
Configuring Storage and Database
Click “Storage & Database” to expand the database configuration section. The default SQLite option works for testing but production deployments require MySQL/MariaDB for better performance and concurrent user support.
Select MySQL/MariaDB from the database options. Enter the database credentials created earlier:
- Database user: owncloud_user
- Database password: (the password set in Step 5)
- Database name: owncloud_db
- Database host: localhost
Leave the database host as “localhost” since MariaDB runs on the same server. External database servers require the appropriate hostname or IP address.
The data folder determines where user files are stored. The default location inside the web root works but storing data outside the web directory improves security. For now, accept the default.
Finishing Setup
Click “Finish Setup” to begin installation. The process takes 1-2 minutes while OwnCloud:
- Creates database tables
- Configures initial settings
- Sets up the admin account
- Prepares the file system
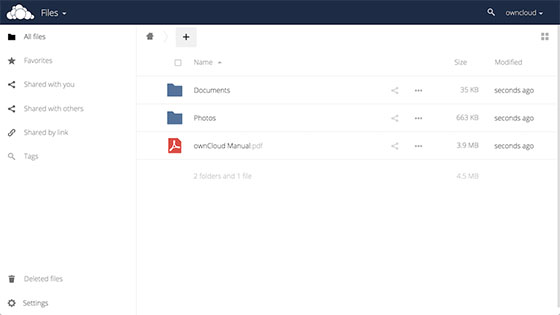
After completion, the login screen appears. Enter admin credentials to access the OwnCloud dashboard. The interface displays the main file management area, navigation menu, and user settings.
First login may show tips and welcome messages. Explore the interface to familiarize yourself with file operations, sharing options, and settings panels.
Step 10: Secure OwnCloud with SSL/TLS Certificate
HTTPS encryption is mandatory for production OwnCloud deployments. Unencrypted HTTP transmits passwords, files, and session cookies in plain text, exposing them to interception.
Option 1: Using Let’s Encrypt (Recommended)
Let’s Encrypt provides free, automated SSL certificates trusted by all major browsers. Install Certbot:
sudo dnf install certbot python3-certbot-nginx -yObtain and install a certificate:
sudo certbot --nginx -d yourdomain.com -d www.yourdomain.comCertbot prompts for an email address and agreement to terms of service. Choose whether to redirect HTTP to HTTPS (recommended: select redirect).
Certbot automatically:
- Validates domain ownership
- Obtains the SSL certificate
- Modifies Nginx configuration
- Configures HTTPS
Test automatic renewal:
sudo certbot renew --dry-runLet’s Encrypt certificates expire after 90 days. Certbot installs a systemd timer that automatically renews certificates before expiration.
Option 2: Self-Signed Certificate
Self-signed certificates work for testing or internal networks but generate browser warnings. Create a self-signed certificate:
sudo mkdir /etc/nginx/ssl
sudo openssl req -x509 -nodes -days 365 -newkey rsa:2048 -keyout /etc/nginx/ssl/owncloud.key -out /etc/nginx/ssl/owncloud.crtAnswer the prompts with appropriate information. Edit the Nginx configuration to enable SSL:
sudo nano /etc/nginx/conf.d/owncloud.confAdd an SSL server block:
server {
listen 443 ssl http2;
server_name yourdomain.com;
ssl_certificate /etc/nginx/ssl/owncloud.crt;
ssl_certificate_key /etc/nginx/ssl/owncloud.key;
# ... (rest of configuration from Step 4)
}Add HTTP to HTTPS redirect:
server {
listen 80;
server_name yourdomain.com;
return 301 https://$server_name$request_uri;
}Restart Nginx:
sudo systemctl restart nginxEnforcing HTTPS
Update OwnCloud’s config.php to force HTTPS:
sudo nano /var/www/html/yourdomain.com/config/config.phpAdd this line inside the array:
'forcessl' => true,This redirects all HTTP requests to HTTPS at the application level, ensuring encrypted connections.
Step 11: Post-Installation Configuration and Optimization
Adjusting PHP Settings
Optimize PHP for better OwnCloud performance. Edit php.ini:
sudo nano /etc/php.iniModify these directives:
memory_limit = 512M
upload_max_filesize = 512M
post_max_size = 512M
max_execution_time = 300
max_input_time = 300
date.timezone = Asia/JakartaAdjust the timezone to match your location. These settings accommodate large file uploads and complex operations.
Restart PHP-FPM:
sudo systemctl restart php-fpmConfiguring OwnCloud Settings
Edit OwnCloud’s configuration file:
sudo nano /var/www/html/yourdomain.com/config/config.phpAdd trusted domains:
'trusted_domains' =>
array (
0 => 'localhost',
1 => 'yourdomain.com',
2 => 'www.yourdomain.com',
3 => '123.45.67.89',
),Replace the IP address with your server’s actual IP. This prevents host header poisoning attacks.
Setting Up Cron Jobs
Background jobs handle maintenance tasks like file scanning and notification delivery. OwnCloud supports three methods: AJAX (default), Webcron, and Cron. Cron provides the best performance.
Add a crontab entry for the nginx user:
sudo crontab -u nginx -eAdd this line:
*/5 * * * * php -f /var/www/html/yourdomain.com/cron.phpThis executes cron.php every 5 minutes. In OwnCloud admin settings (Settings > Admin > Basic settings), select “Cron” as the background jobs method.
Performance Optimization
Enable OPcache by verifying it’s active:
php -i | grep opcacheFor additional performance, install Redis for memory caching:
sudo dnf install redis php-redis -y
sudo systemctl start redis
sudo systemctl enable redisConfigure OwnCloud to use Redis by adding to config.php:
'memcache.local' => '\OC\Memcache\Redis',
'memcache.locking' => '\OC\Memcache\Redis',
'redis' => [
'host' => 'localhost',
'port' => 6379,
],Redis dramatically improves performance for installations with multiple concurrent users.
Backup Strategy
Implement regular backups to prevent data loss. Critical items to backup:
- Data directory:
/var/www/html/yourdomain.com/data - Configuration:
/var/www/html/yourdomain.com/config/config.php - Database: Use mysqldump for MariaDB backups
Create a simple backup script:
#!/bin/bash
BACKUP_DIR="/backup/owncloud"
DATE=$(date +%Y%m%d)
mysqldump -u root -p owncloud_db > $BACKUP_DIR/db-$DATE.sql
tar -czf $BACKUP_DIR/data-$DATE.tar.gz /var/www/html/yourdomain.com/dataSchedule this script via cron for automatic daily backups.
Step 12: Testing OwnCloud Installation
Basic Functionality Tests
Log into OwnCloud and test core features. Upload files of various types—documents, images, videos—to verify upload functionality. Create folders to organize files and test the drag-and-drop interface.
Test file sharing by creating a share link for a test file. Open the link in an incognito browser window to verify public access works correctly. Test password-protected shares and expiration dates.
Download files to confirm download functionality operates properly. Check that file previews generate correctly for images and documents.
User Management Testing
Navigate to Settings > Admin > Users to create additional user accounts. Add a test user with specific storage quota limits. Log out from the admin account and log in as the test user to verify quota enforcement and permission restrictions.
Confirm that regular users cannot access administrative functions. Test group creation and assignment for managing permissions across multiple users.
Mobile and Desktop Client Testing
OwnCloud provides desktop synchronization clients for Windows, macOS, and Linux. Mobile applications are available for iOS and Android. Download the appropriate client from OwnCloud’s website or app stores.
Configure the desktop client by entering the server URL and user credentials. Select folders for synchronization and verify that files sync bidirectionally between the server and client. Test that changes made on the server appear on the client and vice versa.
Mobile clients enable file access, uploads, and automatic photo backups. Test uploading photos from a mobile device to ensure mobile connectivity works correctly.
Performance Verification
Monitor server resource usage during typical operations. Use htop or top to observe CPU and memory consumption. Normal operations should maintain CPU usage below 30% and memory usage below 70% of available resources.
Check page load times—the interface should load within 2-3 seconds on reasonably fast connections. Slow performance may indicate insufficient resources, misconfiguration, or missing optimization settings.
Review log files for errors or warnings:
sudo tail -f /var/www/html/yourdomain.com/data/owncloud.logLogs help identify issues before they impact users.
Troubleshooting Common Issues
Permission Errors
Symptoms include “Permission denied” errors when uploading files or “Cannot write to data directory” messages. Verify ownership of OwnCloud directories:
sudo chown -R nginx:nginx /var/www/html/yourdomain.comCheck directory permissions:
sudo chmod -R 755 /var/www/html/yourdomain.com
sudo chmod -R 770 /var/www/html/yourdomain.com/dataIf SELinux is enabled, verify correct contexts:
sudo restorecon -Rv /var/www/html/yourdomain.comDatabase Connection Errors
“Failed to connect to database” errors indicate database credential problems. Verify credentials in config.php match those created during database setup. Confirm MariaDB is running:
sudo systemctl status mariadbTest database connectivity:
mysql -u owncloud_user -p owncloud_dbIf connection fails, verify user privileges:
SHOW GRANTS FOR 'owncloud_user'@'localhost';The user needs all privileges on the OwnCloud database.
PHP Version Conflicts
OwnCloud reports “PHP version not supported” if the wrong PHP version is active. Verify PHP 7.4 is installed and active:
php -vIf the wrong version appears, ensure the PHP 7.4 module is enabled:
sudo dnf module list php
sudo dnf module enable php:remi-7.4 -yCheck that all required PHP extensions are present:
php -mMissing extensions cause various errors. Install any missing packages and restart PHP-FPM.
File Upload Issues
Large file uploads fail when PHP or Nginx limits are too restrictive. Increase limits in php.ini (see Step 11) and verify the Nginx configuration includes:
client_max_body_size 512M;Restart both services after changes. Check available disk space:
df -hInsufficient disk space prevents uploads regardless of configuration settings.
SSL/HTTPS Problems
Browser certificate warnings occur with self-signed certificates or expired Let’s Encrypt certificates. Verify certificate validity:
sudo certbot certificatesRenew certificates if expired:
sudo certbot renewCheck that Nginx SSL configuration includes valid certificate paths. Test HTTPS configuration:
sudo nginx -tEnsure port 443 is open in the firewall and not blocked by network security groups.
Security Best Practices
Implement two-factor authentication through OwnCloud’s app store. Navigate to Settings > Admin > Apps, enable the Two-Factor TOTP app, and require 2FA for admin accounts minimally.
Configure automatic security updates for AlmaLinux:
sudo dnf install dnf-automatic -y
sudo systemctl enable --now dnf-automatic.timerEdit /etc/dnf/automatic.conf and set apply_updates = yes to automatically install security patches.
Enforce strong password policies through OwnCloud admin settings. Require minimum password lengths, complexity requirements, and regular password changes for sensitive environments.
Restrict administrative access by IP address when possible. Edit Nginx configuration to add IP restrictions to sensitive paths:
location /settings/admin {
allow 123.45.67.89;
deny all;
}Enable OwnCloud’s built-in security features including file encryption at rest and brute force protection. Configure these in admin settings under Security sections.
Implement regular log monitoring. Set up automated alerts for suspicious activities like multiple failed login attempts, unusual file access patterns, or configuration changes.
Keep OwnCloud updated to the latest stable version. Subscribe to OwnCloud’s security mailing list to receive notifications about vulnerabilities and patches. Apply updates promptly after testing in non-production environments.
Implement comprehensive backup procedures covering both data and configuration files. Test restoration procedures regularly to ensure backups are valid and complete. Store backups off-site or in separate cloud storage for disaster recovery.
Configure fail2ban to prevent brute force attacks against OwnCloud’s login interface. Create custom filters matching OwnCloud’s log format and ban IPs after repeated failed attempts.
Use dedicated domains or subdomains for OwnCloud rather than sharing domains with other applications. This isolation limits the impact of potential vulnerabilities in other software.
Harden the database by disabling remote access if the database runs on the same server. Remove unnecessary database users and limit privileges to only what OwnCloud requires.
Review and disable dangerous PHP functions in php.ini:
disable_functions = exec,passthru,shell_exec,system,proc_open,popenBalance security with functionality—some OwnCloud features may require specific PHP functions.
Congratulations! You have successfully installed OwnCloud. Thanks for using this tutorial for installing OwnCloud open-source software platform for self-hosted on your AlmaLinux OS 10 system. For additional help or useful information, we recommend you check the official OwnCloud website.