How To Install SpiderFoot on Debian 13

Open-source intelligence gathering has become essential for cybersecurity professionals, penetration testers, and security researchers worldwide. SpiderFoot stands out as one of the most comprehensive OSINT automation tools available, offering over 200 modules that collect data from countless sources across the internet. This guide walks through the complete installation process of SpiderFoot on Debian 13 “Trixie,” covering everything from initial system preparation to running your first reconnaissance scan. Whether you’re conducting security assessments, mapping attack surfaces, or performing threat intelligence research, this tutorial provides the foundation for leveraging SpiderFoot’s powerful capabilities on Debian’s latest stable release.
Understanding SpiderFoot
SpiderFoot is an open-source intelligence (OSINT) automation framework designed to streamline the process of gathering information from publicly available sources. The tool integrates with more than 200 data sources, making it invaluable for security professionals who need to quickly assess digital footprints, identify potential vulnerabilities, or investigate suspicious domains and IP addresses.
What makes SpiderFoot particularly powerful is its ability to automatically correlate data from multiple sources. The tool can scan IP addresses, domain names, email addresses, phone numbers, usernames, and even Bitcoin addresses. It then aggregates this information into a comprehensive report that reveals relationships and patterns that might otherwise go unnoticed.
SpiderFoot offers both a web-based user interface and a command-line interface, providing flexibility for different workflows. The web UI features intuitive dashboards with real-time scan progress monitoring, while the CLI mode enables automation and integration with other security tools. Results can be exported in multiple formats including CSV, JSON, and GEXF for network graph visualization.
The tool stores all collected data in an SQLite database, allowing users to perform custom queries and extract specific information as needed. Advanced features include TOR integration for anonymous scanning, dark web intelligence gathering, and correlation engines that identify connections between different data points. Common use cases span penetration testing, vulnerability assessments, digital footprint analysis, threat intelligence gathering, and incident response investigations.
Prerequisites and System Requirements
Hardware Requirements
Before installing SpiderFoot on Debian 13, ensure your system meets the minimum specifications. A processor with at least 1 GHz single-core capability is required, though a 2 GHz dual-core processor delivers significantly better performance during intensive scans. Memory allocation is crucial—2 GB RAM represents the bare minimum, but 4-8 GB is recommended for smooth operation when running multiple modules simultaneously.
Storage considerations depend on your intended usage. The SpiderFoot application itself is lightweight, but scan results and databases can grow quickly. Allocate at least 25 GB of disk space, with 50 GB on an SSD being the optimal configuration for faster database operations and quicker result retrieval. A stable internet connection is essential since SpiderFoot continuously queries external APIs and data sources during scans.
Software Requirements
Debian 13 “Trixie” comes with Python 3.13 pre-installed, which is perfect since SpiderFoot requires Python 3.7 or higher. You’ll also need the Git version control system for cloning the repository and pip3 for managing Python packages. Root or sudo access is mandatory for installing system packages and dependencies.
Basic command-line proficiency helps navigate the installation process smoothly. A modern web browser—Firefox, Chrome, or any Chromium-based browser—is necessary for accessing SpiderFoot’s web interface. Optional tools like wget or curl can simplify package downloads, though they’re not strictly required for the installation process.
Step 1: Update System Packages
Keeping your Debian 13 system updated is the first critical step. Outdated packages can cause compatibility issues, security vulnerabilities, or installation failures. Connect to your Debian server via SSH if you’re working remotely, or open a terminal if you’re on a local machine.
Execute the following command to refresh the package repository listings:
sudo apt updateThis command contacts Debian’s repositories and downloads the latest package information. Next, upgrade all installed packages to their newest versions:
sudo apt upgrade -yThe -y flag automatically confirms the upgrade prompts, streamlining the process. This operation may take several minutes depending on how many packages require updates. If kernel updates are applied, consider rebooting your system to ensure all changes take effect properly.
Verify your Debian version to confirm you’re running version 13:
lsb_release -aYou should see output indicating Debian 13 “Trixie.” This confirmation ensures you’re following the correct installation procedures for your distribution version.
Step 2: Install Required Dependencies
Install Python 3 and pip
Debian 13 includes Python 3.13 by default, but verification is always wise. Check your Python version with:
python3 --versionThe output should display Python 3.13.x. If Python isn’t installed or you’re running an older version, install it alongside pip:
sudo apt install python3 python3-pip -yUpgrade pip to the latest version for compatibility with modern Python packages:
pip3 install --upgrade pipVerify pip installation:
pip3 --versionDebian 13 implements PEP 668, which creates “externally managed environments” to prevent conflicts between system packages and pip-installed packages. This protection mechanism is crucial for system stability and will be addressed in later steps when installing SpiderFoot’s dependencies.
Install Git and Additional Tools
Git is essential for cloning the SpiderFoot repository and maintaining updates. Install Git along with useful auxiliary tools:
sudo apt install git unzip wget curl -yOptionally, install build-essential if you anticipate compiling any Python packages from source:
sudo apt install build-essential -yVerify Git installation:
git --versionThese tools form the foundation for downloading, extracting, and managing SpiderFoot throughout its lifecycle on your system.
Step 3: Download SpiderFoot from GitHub
Choose Installation Directory
Select an appropriate location for SpiderFoot installation. The /opt directory is conventional for third-party applications and maintains system organization:
cd /optAlternatively, install in your home directory for user-specific access without requiring elevated privileges:
cd ~/System-wide installations in /opt require sudo privileges for most operations, while home directory installations offer easier management for single-user scenarios.
Clone from GitHub Repository
Clone the official SpiderFoot repository from GitHub:
sudo git clone https://github.com/smicallef/spiderfoot.gitThis command downloads the latest stable release, including all modules, documentation, and configuration files. The process typically completes within a minute, depending on your internet connection speed.
Navigate into the newly created SpiderFoot directory:
cd spiderfootFor users who prefer specific versions, you can download a particular release as a tarball:
wget https://github.com/smicallef/spiderfoot/archive/v4.0.tar.gz
tar zxvf v4.0.tar.gz
cd spiderfoot-4.0The development branch receives frequent updates with new features but may contain unstable code. Stick with the master branch for production environments.
Verify Download
List the directory contents to confirm successful download:
ls -laKey files should include sf.py (the main SpiderFoot script), requirements.txt (Python dependencies), README.md (documentation), and various directories containing modules and configurations. If any files are missing, re-clone the repository.
Step 4: Install Python Dependencies
Understanding requirements.txt
SpiderFoot relies on numerous Python libraries that handle everything from web requests to data parsing. The requirements.txt file lists all necessary dependencies including CherryPy for the web server, BeautifulSoup and lxml for HTML parsing, requests for HTTP operations, and dnspython for DNS queries.
These libraries enable SpiderFoot’s core functionality—without them, the tool cannot communicate with external APIs, parse responses, or present results through the web interface.
Install Dependencies
Due to Debian 13’s externally managed environment protection, the recommended approach is using a Python virtual environment. This isolates SpiderFoot’s dependencies from system packages, preventing conflicts and maintaining system integrity.
Create a virtual environment in the SpiderFoot directory:
python3 -m venv spiderfoot-envActivate the virtual environment:
source spiderfoot-env/bin/activateYour command prompt should now display (spiderfoot-env) indicating the virtual environment is active. Install all required dependencies:
pip3 install -r requirements.txtThis installation process downloads and compiles dozens of Python packages, which may take 5-10 minutes. Watch for error messages indicating missing system libraries or compilation failures. Most installations complete without issues on Debian 13.
If you encounter errors related to specific packages, ensure build-essential is installed. Some Python packages require compilation and need development headers. Once installation completes successfully, you’ll see confirmation messages for each package.
Step 5: Configure SpiderFoot
Set Up Authentication
Security should never be an afterthought. SpiderFoot’s default configuration allows unauthenticated access, which is dangerous if your system is network-accessible. Create a password file to enable authentication:
echo "admin:YourSecurePassword123!" > passwdReplace YourSecurePassword123! with a strong password containing uppercase letters, lowercase letters, numbers, and special characters. This simple authentication mechanism prevents unauthorized access to your SpiderFoot instance and protects sensitive scan data.
For multiple users, add additional lines to the passwd file:
echo "analyst:AnotherPassword456@" >> passwdStore this file securely and restrict permissions:
chmod 600 passwdOptional Configuration
SpiderFoot includes a configuration file named spiderfoot.cfg that controls various operational parameters. Review default settings before running your first scan. While most defaults work well, you may want to customize timeout values, database locations, or logging verbosity.
The default listening port is 5001, but you can modify this in the configuration file or specify it at runtime. For production deployments, consider implementing SSL/TLS certificates to encrypt communication between your browser and the SpiderFoot web server, though this is optional for local-only installations.
Step 6: Launch SpiderFoot
Start Web Interface
From within the SpiderFoot directory with your virtual environment activated, start the web server:
python3 sf.py -l 127.0.0.1:5001This command binds SpiderFoot to localhost on port 5001, restricting access to the local machine only. For remote access, bind to all interfaces:
python3 sf.py -l 0.0.0.0:5001Be cautious with the 0.0.0.0 binding—it exposes SpiderFoot to your entire network. Always use authentication when allowing remote connections.
You’ll see startup messages indicating database verification and web server initialization. The output confirms SpiderFoot is listening and ready for connections. Keep this terminal window open; closing it stops the SpiderFoot service.
Command-Line Options
SpiderFoot offers numerous command-line parameters. View all available options:
python3 sf.py --helpKey options include specifying custom ports, enabling CLI-only mode for automation, setting database locations, and configuring log files. Understanding these parameters enables advanced deployments and integration with other security tools.
For persistent operation without maintaining an open terminal, use screen or tmux:
screen -S spiderfoot
python3 sf.py -l 127.0.0.1:5001Press Ctrl+A then D to detach from the screen session. Reattach anytime with screen -r spiderfoot.
Step 7: Access SpiderFoot Web Interface
Access via Browser
Open your preferred web browser and navigate to:
http://localhost:5001If accessing remotely, replace localhost with your server’s IP address:
http://192.168.1.100:5001If you configured authentication, SpiderFoot prompts for credentials. Enter the username and password from your passwd file. Upon successful login, you’ll see the SpiderFoot dashboard—a clean interface displaying scan history, settings access, and the prominent “New Scan” button.
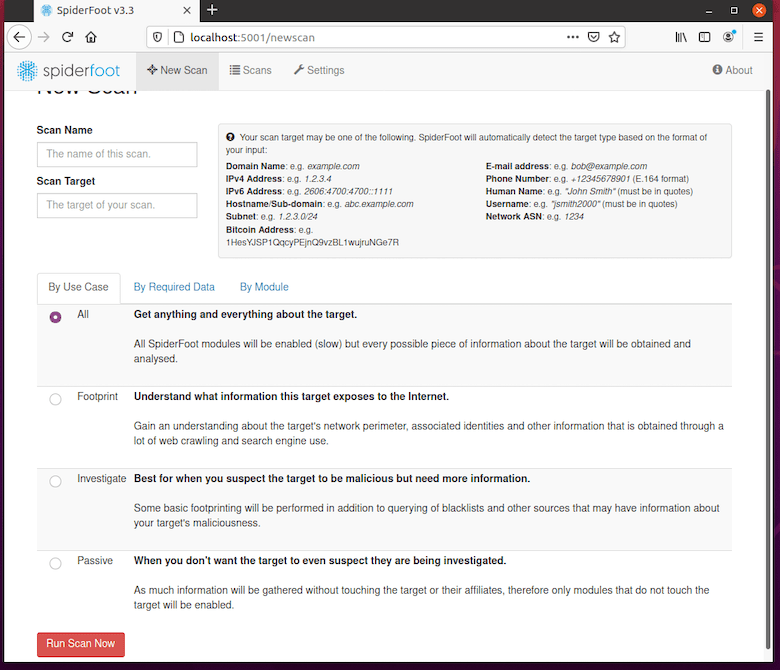
The dashboard provides at-a-glance information about previous scans, system status, and quick navigation to all major features. First-time users will see an empty scan history, which is perfectly normal.
Web Interface Overview
The main navigation menu spans the top of the interface. The “Scans” tab lists all historical and active scans with filtering and sorting capabilities. “Settings” contains module configuration, API key management, and system preferences. The “Documentation” section provides inline help and module descriptions.
Individual scan pages display real-time progress bars, collected data organized by module, relationship graphs showing connections between discovered information, and export options for generating reports. The interface updates automatically as scans progress, eliminating the need for manual refreshing.
Step 8: Configure API Keys and Modules
Understanding SpiderFoot Modules
SpiderFoot’s power lies in its 200+ modules, each designed to query specific data sources. Some modules work without any configuration, pulling data from public sources like DNS records, WHOIS databases, and search engines. Other modules require API keys to access commercial or rate-limited services.
Modules fall into several categories: threat intelligence platforms, DNS and IP intelligence, social media investigation, company and domain intelligence, dark web monitoring, and vulnerability databases. Free modules provide substantial capabilities, while premium API integrations unlock advanced features for comprehensive investigations.
Configure API Keys
Navigate to Settings from the main menu, then select Module Configuration. You’ll see a comprehensive list of all available modules with their current status. Modules requiring API keys display configuration fields where you can paste your credentials.
SpiderFoot allows exporting your current configuration for backup purposes. Click Export under Settings to save your API key configuration as a file. This is useful when migrating to new installations or creating backup configurations.
Edit the spiderfoot.cfg file directly for bulk API key updates:
nano spiderfoot.cfgAdd API keys in the format specified for each service. Save the file and restart SpiderFoot for changes to take effect.
Recommended free API services include Shodan (limited free tier for IP intelligence), VirusTotal (free API for malware and URL scanning), Have I Been Pwned (breach detection), and AlienVault OTX (threat intelligence). Obtain API keys by registering on each service’s website and following their API documentation.
Step 9: Run Your First Scan
Create New Scan
Click “New Scan” from the dashboard to begin your first reconnaissance operation. The scan configuration page presents several fields requiring attention. Enter a descriptive scan name for easy identification later—something like “Example.com Initial Footprint” works well.
In the target field, specify what you want to investigate. SpiderFoot accepts various input types: domain names (example.com), IP addresses (192.0.2.1), email addresses (user@example.com), phone numbers, usernames, and more. Start with a domain name for your initial test.
Select a scan type based on your objectives. “Footprint” mode maps publicly available information without triggering alerts. “Investigate” mode includes threat intelligence checks alongside footprinting. “Passive” mode avoids any direct contact with the target, using only third-party sources. “All” mode runs every configured module but takes significantly longer.
Choose which modules to enable for this particular scan. For beginners, stick with the preset scan types rather than manually selecting individual modules. Advanced users can customize module selection for targeted investigations.
Monitor Scan Progress
After clicking “Run Scan,” SpiderFoot immediately begins data collection. The scan status page displays real-time progress with several key metrics. A progress bar shows overall completion percentage, though this estimate may fluctuate as SpiderFoot discovers additional targets to investigate.
Individual modules report their status—running, completed, or failed. Failed modules typically indicate API rate limits, network timeouts, or configuration issues. These don’t stop the overall scan from proceeding.
Scan duration varies dramatically based on target size, enabled modules, and network speed. Simple domain scans might complete in 10-15 minutes, while comprehensive investigations of large organizations can run for hours. You can pause or stop scans at any time without losing collected data.
Preliminary results appear as data is collected, allowing you to review findings before the scan completes. This immediate feedback helps identify interesting leads that warrant deeper investigation.
Step 10: Review and Export Results
Analyze Scan Results
Navigate to the completed scan from your scan history. SpiderFoot organizes results by data type, module, and relationship. The default view presents a chronological list of all discovered information with timestamps and source modules.
Use the filtering and search capabilities to narrow results. Filter by data type to see only email addresses, IP addresses, or specific information categories. The search function helps locate particular strings within your results.
SpiderFoot’s correlation engine identifies relationships between discovered data points. The graph view visualizes these connections, showing how different pieces of information relate. This visual representation often reveals patterns and relationships that aren’t obvious from raw data alone.
Risk assessment indicators highlight potentially concerning findings like exposed credentials, vulnerable services, or data breaches. Pay special attention to these flagged items during security assessments.
Export Data
SpiderFoot supports multiple export formats for different use cases. CSV exports work well for spreadsheet analysis and reporting. JSON exports enable integration with other security tools and custom processing scripts. GEXF format creates network graphs viewable in tools like Gephi for advanced visualization.
Click the “Export” button on any scan page and select your preferred format. The download begins immediately, containing all collected data in structured format.
For advanced users, SpiderFoot’s SQLite database can be queried directly using SQL commands. The database file resides in the SpiderFoot directory and contains complete scan histories with full relational structure for complex queries.
Setting Up SpiderFoot as a System Service
Create Systemd Service File
Running SpiderFoot as a system service provides automatic startup on boot, easier management, and better integration with Debian’s system architecture. Create a systemd service file:
sudo nano /etc/systemd/system/spiderfoot.serviceAdd the following configuration, adjusting paths to match your installation:
[Unit]
Description=SpiderFoot OSINT Tool
After=network.target
[Service]
Type=simple
User=your-username
WorkingDirectory=/opt/spiderfoot
Environment="PATH=/opt/spiderfoot/spiderfoot-env/bin"
ExecStart=/opt/spiderfoot/spiderfoot-env/bin/python3 /opt/spiderfoot/sf.py -l 0.0.0.0:5001
Restart=on-failure
[Install]
WantedBy=multi-user.targetReplace your-username with your actual username and adjust paths if you installed SpiderFoot elsewhere.
Enable and Start Service
Reload the systemd daemon to recognize the new service:
sudo systemctl daemon-reloadEnable SpiderFoot to start automatically on boot:
sudo systemctl enable spiderfootStart the service immediately:
sudo systemctl start spiderfootCheck service status to confirm it’s running:
sudo systemctl status spiderfootYou should see “active (running)” in green text. View service logs if troubleshooting is needed:
sudo journalctl -u spiderfoot -fThe service now runs continuously in the background, automatically restarting after failures and launching on system boot.
Security Best Practices
Implementing robust security measures protects both your SpiderFoot installation and the data it collects. Always enable authentication with strong, unique passwords. Never use default credentials or simple passwords like “password123.”
Configure firewall rules to restrict network access. If SpiderFoot only needs local access, block external connections using UFW:
sudo ufw deny 5001
sudo ufw allow from 192.168.1.0/24 to any port 5001This configuration blocks all external access while allowing connections from your local network. For internet-exposed installations, implement SSL/TLS encryption using reverse proxies like Nginx or Apache with Let’s Encrypt certificates.
Update SpiderFoot regularly by pulling the latest code from GitHub. Security vulnerabilities are patched frequently in active open-source projects. Navigate to your SpiderFoot directory and run:
git pull origin masterAPI keys represent sensitive credentials that grant access to external services. Store them securely with restricted file permissions. Rotate API keys periodically and limit permissions to only required functions.
Consider legal and ethical implications before scanning targets. Always obtain proper authorization before conducting security assessments on systems you don’t own. Unauthorized reconnaissance can violate computer fraud laws in many jurisdictions. Data privacy regulations like GDPR impose obligations on how personal information is collected and stored.
Troubleshooting Common Issues
Installation Problems
The “externally managed environment” error is common on Debian 13 when attempting pip installations outside virtual environments. The solution is always using virtual environments as described earlier. If you bypassed the virtual environment setup, return to Step 4 and create one properly.
Missing dependencies cause module import errors at startup. Reinstall requirements.txt carefully, watching for error messages indicating failed installations. Some packages require system libraries—install build-essential and python3-dev to resolve compilation issues.
Permission denied errors typically indicate incorrect file ownership or insufficient user privileges. If SpiderFoot is installed in /opt, ensure your user has read access or run with appropriate sudo privileges. For home directory installations, verify file ownership matches your username.
Port conflicts occur when another service is already using port 5001. Change SpiderFoot’s listening port using the -l parameter with an alternative port number like 8080 or 8000.
Runtime Issues
SpiderFoot failing to start usually indicates Python version incompatibility or missing dependencies. Verify Python 3.7+ is installed and all requirements are met. Check startup logs for specific error messages pointing to the problem.
Module errors during scans often result from incorrect API key configuration. Verify API keys are entered correctly without extra spaces or characters. Test each API key directly on the provider’s website to confirm validity.
Database errors can occur if the SQLite database becomes corrupted. Back up your existing database, then delete the spiderfoot.db file. SpiderFoot recreates a fresh database on next startup, though you’ll lose historical scan data.
Memory issues manifest as slow performance or crashes during large scans. Increase system RAM, reduce the number of concurrent modules, or scan smaller target sets. Monitor resource usage with htop to identify bottlenecks.
Network and Access Issues
Firewall configurations block access to SpiderFoot’s web interface. Verify firewall rules allow connections on your chosen port. Temporarily disable the firewall for testing, then re-enable it with proper rules once you’ve confirmed the issue.
Slow scan performance typically indicates network latency, API rate limiting, or insufficient system resources. Review enabled modules and disable those providing low-value data. Adjust timeout values in the configuration file to prevent hanging on unresponsive sources.
Authentication problems arise from malformed passwd files. Recreate the passwd file following the exact format: username:password with one entry per line. Ensure no extra spaces or special characters unless part of the password itself.
Performance Optimization Tips
Optimize SpiderFoot’s performance by carefully selecting modules relevant to your investigation goals. Running all 200+ modules provides comprehensive coverage but takes significantly longer and generates overwhelming data volumes. Focus on modules that address your specific intelligence requirements.
Configure scan depth and timeout values appropriately. Shallow scans complete quickly but may miss valuable information. Deep scans are thorough but resource-intensive. Balance depth based on time constraints and information needs.
SpiderFoot caches certain queries to reduce redundant API calls. Ensure caching is enabled in configuration settings to speed up subsequent scans of previously investigated targets.
Schedule large scans during off-peak hours to minimize impact on network bandwidth and system resources. Overnight scans let you wake up to completed results without impacting daytime productivity.
Database maintenance improves query performance over time. Periodically archive old scan data and run SQLite optimization commands to compact the database and rebuild indexes.
Updating SpiderFoot
Maintaining current software versions ensures access to new modules, bug fixes, and security patches. SpiderFoot’s development team releases updates frequently with meaningful improvements.
Navigate to your SpiderFoot installation directory:
cd /opt/spiderfootDeactivate the virtual environment if it’s active, then pull the latest updates:
git pull origin masterReactivate the virtual environment and update Python dependencies:
source spiderfoot-env/bin/activate
pip3 install --upgrade -r requirements.txtReview the changelog on GitHub to understand what changed. Major updates occasionally introduce breaking changes requiring configuration adjustments. Test SpiderFoot after updates to verify everything works correctly.
If you configured SpiderFoot as a systemd service, restart it to apply updates:
sudo systemctl restart spiderfootBackup your configuration files and database before major version upgrades to prevent data loss if issues arise.
Congratulations! You have successfully installed SpiderFoot. Thanks for using this tutorial for installing SpiderFoot open-source intelligence on your Debian 13 “Trixie” system. For additional help or useful information, we recommend you check the official SpiderFoot website.