How To Install Uptime Kuma on openSUSE

Uptime Kuma has emerged as the go-to self-hosted monitoring solution for system administrators and developers worldwide. This comprehensive monitoring tool offers robust website, API, and server monitoring capabilities without the recurring costs of cloud-based alternatives. In this detailed guide, you’ll learn how to install Uptime Kuma on openSUSE through multiple methods, configure it for optimal performance, and implement best practices for production environments.
Whether you’re managing a single website or an entire server infrastructure, Uptime Kuma provides the reliability and flexibility needed for effective uptime monitoring. Let’s dive into the complete installation process on openSUSE.
Understanding Uptime Kuma
What is Uptime Kuma?
Uptime Kuma is a free, open-source monitoring solution designed for self-hosted environments. This powerful tool enables continuous monitoring of websites, APIs, servers, and various services with real-time alerts and customizable notifications. Unlike traditional monitoring services, Uptime Kuma gives you complete control over your monitoring infrastructure while eliminating monthly subscription fees.
The platform supports multiple monitor types including HTTP(s) websites, TCP ports, ping checks, DNS records, and webhook monitoring. Its intuitive web interface makes configuration straightforward, while advanced features like status pages and multi-language support enhance its enterprise readiness.
Key Features and Benefits
Uptime Kuma offers comprehensive monitoring capabilities including real-time status tracking, customizable alert thresholds, and beautiful status pages for public or private use. The tool supports over 90 notification providers including email, Slack, Discord, Telegram, and webhook integrations.
Additional features include certificate expiration monitoring, keyword detection in HTTP responses, response time tracking, and detailed uptime statistics. The self-hosted nature ensures data privacy while providing unlimited monitors without usage restrictions.
System Requirements and Prerequisites
Before installing Uptime Kuma on openSUSE, ensure your system meets the minimum requirements. You’ll need Node.js version 14 or higher, at least 512MB RAM, and 1GB available disk space. Network access on port 3001 (default) is required for web interface access.
For optimal performance in production environments, consider allocating 1GB+ RAM and ensuring adequate CPU resources based on your monitoring frequency and number of targets.
Pre-Installation Preparation
System Updates and Package Management
Begin by updating your openSUSE system to ensure all packages are current and security patches are applied. Open a terminal session and execute the following commands:
sudo zypper refresh
sudo zypper update -yInstall essential development tools and dependencies required for Uptime Kuma installation:
sudo zypper install -y curl wget git make gcc-c++ python3Configure the system firewall to allow HTTP traffic on the default Uptime Kuma port. Use the following commands to open port 3001:
sudo firewall-cmd --permanent --add-port=3001/tcp
sudo firewall-cmd --reloadInstalling Node.js and npm
Uptime Kuma requires Node.js version 14 or higher for proper functionality. Install Node.js using the NodeSource repository for the latest stable version:
curl -fsSL https://rpm.nodesource.com/setup_lts.x | sudo bash -
sudo zypper install -y nodejsVerify the installation by checking the Node.js and npm versions:
node --version
npm --versionThe output should display Node.js version 14+ and npm version 6+. If you encounter permission issues with npm, configure npm to use a different directory for global packages:
mkdir ~/.npm-global
npm config set prefix '~/.npm-global'
echo 'export PATH=~/.npm-global/bin:$PATH' >> ~/.bashrc
source ~/.bashrcGit Installation and Configuration
Install Git for repository cloning capabilities:
sudo zypper install -y gitConfigure Git with your information for future development or troubleshooting purposes:
git config --global user.name "Your Name"
git config --global user.email "your.email@example.com"User Account Setup
Create a dedicated system user for running Uptime Kuma to enhance security. This approach follows the principle of least privilege:
sudo useradd -r -s /bin/false -m -d /opt/uptime-kuma uptimekumaCreate the application directory with appropriate permissions:
sudo mkdir -p /opt/uptime-kuma
sudo chown uptimekuma:uptimekuma /opt/uptime-kumaMethod 1: Native Installation from Source
Cloning the Repository
Switch to the dedicated user account and clone the Uptime Kuma repository:
sudo -u uptimekuma bash
cd /opt/uptime-kuma
git clone https://github.com/louislam/uptime-kuma.git .Verify the repository contents and check the latest release version:
ls -la
git describe --tags --abbrev=0Installing Dependencies
Install production dependencies using npm. This process may take several minutes depending on your internet connection:
npm ci --production --no-optionalThe npm ci command ensures a clean installation based on the package-lock.json file, providing better reliability than npm install for production environments.
Configuration Setup
Uptime Kuma uses SQLite as the default database, requiring minimal configuration. Create the data directory for database storage:
mkdir -p dataFor production environments, consider configuring environment variables. Create a .env file if custom configuration is needed:
cat > .env << EOF
# Port configuration
PORT=3001
# Database configuration (optional)
DATABASE_PATH=./data/kuma.db
# SSL configuration (if using HTTPS)
# SSL_CERT=/path/to/cert.pem
# SSL_KEY=/path/to/key.pem
EOFBuilding and Initial Setup
Run the setup script to prepare the application:
npm run setupThis command installs additional dependencies and builds the frontend application. The process typically takes 2-5 minutes on modern hardware.
First Run and Testing
Start Uptime Kuma manually to verify proper installation:
node server/server.jsThe application should start and display startup messages including the listening port. Access the web interface by opening a browser and navigating to http://your-server-ip:3001.
Create your initial administrator account by filling in the setup form. Choose a strong password and store the credentials securely.
Troubleshooting Common Issues
Port conflicts: If port 3001 is already in use, modify the PORT environment variable or use netstat to identify conflicting processes:
sudo netstat -tlnp | grep 3001Permission problems: Ensure the uptimekuma user owns all application files:
sudo chown -R uptimekuma:uptimekuma /opt/uptime-kumaNode.js version issues: Verify Node.js compatibility and upgrade if necessary. Uptime Kuma requires specific Node.js versions for optimal performance.
Method 2: Docker Installation
Docker Prerequisites
Install Docker on openSUSE using the official repository:
sudo zypper install -y docker
sudo systemctl enable docker
sudo systemctl start dockerAdd your user to the docker group to run commands without sudo:
sudo usermod -aG docker $USER
newgrp dockerVerify Docker installation:
docker --version
docker run hello-worldPull and Run Uptime Kuma Container
Pull the official Uptime Kuma Docker image:
docker pull louislam/uptime-kuma:1Create a directory for persistent data storage:
mkdir -p ~/uptime-kuma-dataRun the Uptime Kuma container with proper volume mounting:
docker run -d \
--name uptime-kuma \
--restart=always \
-p 3001:3001 \
-v ~/uptime-kuma-data:/app/data \
louislam/uptime-kuma:1Docker Compose Setup (Alternative)
Create a docker-compose.yml file for easier management:
version: '3.8'
services:
uptime-kuma:
image: louislam/uptime-kuma:1
container_name: uptime-kuma
restart: always
ports:
- "3001:3001"
volumes:
- ./uptime-kuma-data:/app/data
environment:
- PORT=3001Start the service using Docker Compose:
docker-compose up -dContainer Management
Monitor container status and logs:
docker ps
docker logs uptime-kumaStop and start the container as needed:
docker stop uptime-kuma
docker start uptime-kumaUpdate the container by pulling the latest image and recreating the container:
docker pull louislam/uptime-kuma:1
docker stop uptime-kuma
docker rm uptime-kuma
# Re-run the docker run command with the same parametersSetting Up Uptime Kuma as a System Service
Creating Service Scripts
Create a systemd service file for automatic startup and process management:
sudo nano /etc/systemd/system/uptime-kuma.serviceAdd the following configuration:
[Unit]
Description=Uptime Kuma
Documentation=https://github.com/louislam/uptime-kuma
After=network.target
[Service]
Type=simple
User=uptimekuma
WorkingDirectory=/opt/uptime-kuma
ExecStart=/usr/bin/node server/server.js
Restart=on-failure
RestartSec=5s
TimeoutStopSec=20s
KillMode=process
# Security settings
NoNewPrivileges=yes
ProtectSystem=strict
ProtectHome=yes
ReadWritePaths=/opt/uptime-kuma/data
[Install]
WantedBy=multi-user.targetService Installation and Configuration
Reload systemd configuration and enable the service:
sudo systemctl daemon-reload
sudo systemctl enable uptime-kuma
sudo systemctl start uptime-kumaVerify service status:
sudo systemctl status uptime-kumaThe service should show as active (running). Check logs if there are any issues:
sudo journalctl -u uptime-kuma -fProcess Management with PM2 (Alternative)
Install PM2 globally for advanced process management:
npm install -g pm2Create a PM2 ecosystem file:
sudo -u uptimekuma bash
cd /opt/uptime-kuma
cat > ecosystem.config.js << EOF
module.exports = {
apps: [{
name: 'uptime-kuma',
script: 'server/server.js',
instances: 1,
autorestart: true,
watch: false,
max_memory_restart: '1G',
env: {
NODE_ENV: 'production'
}
}]
}
EOFStart Uptime Kuma with PM2:
pm2 start ecosystem.config.js
pm2 save
pm2 startupInitial Configuration and Setup
Web Interface Access
Navigate to http://your-server-ip:3001 to access the Uptime Kuma dashboard. The initial setup wizard will guide you through account creation.
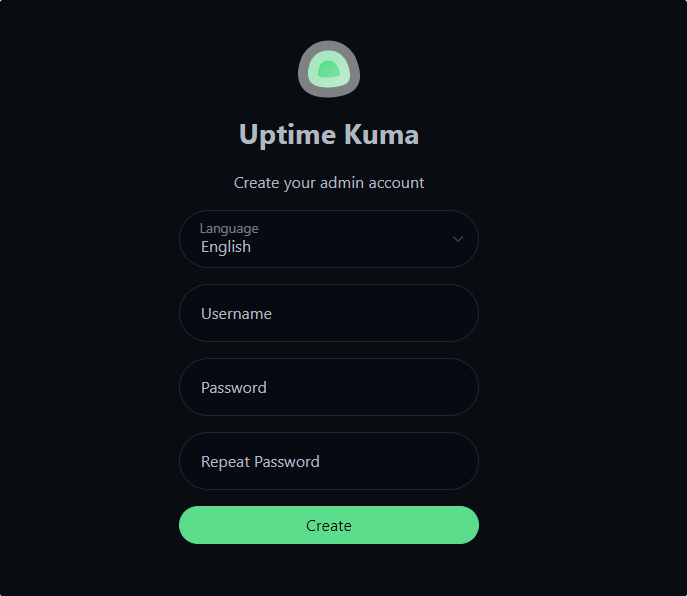
Select your preferred language and create an administrator account with a strong password. This account will have full access to all monitoring functions and settings.
Basic Configuration Options
Configure general settings including:
- Time zone: Set your local time zone for accurate timestamps
- Default notification settings: Configure fallback notification methods
- Security settings: Enable two-factor authentication if desired
- Theme preferences: Choose between light and dark themes
Navigate to Settings > General to access these options. Save changes and restart the service if required.
Creating Your First Monitor
Add a website monitor by clicking “Add New Monitor” and configuring:
- Monitor Type: Select HTTP(s) for websites
- Friendly Name: Choose a descriptive name
- URL: Enter the complete URL to monitor
- Heartbeat Interval: Set check frequency (30 seconds to 24 hours)
- Timeout: Configure request timeout (default: 48 seconds)
Advanced options include keyword monitoring, certificate expiration tracking, and custom HTTP headers.
Dashboard Customization
Organize monitors using tags and groups for better management. Create status pages for public display of service availability. Customize notification rules and escalation policies based on monitor criticality.
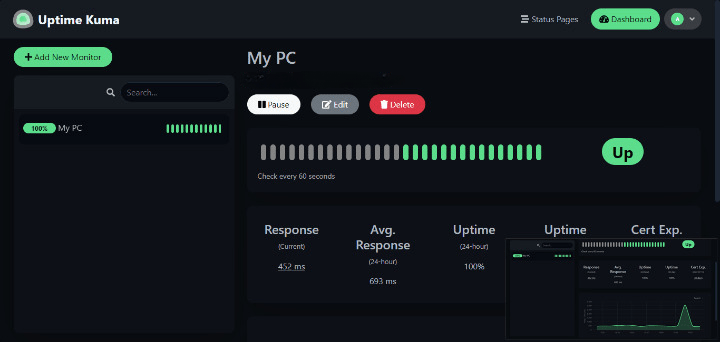
Configure maintenance windows to suppress alerts during planned downtime. Set up monitor dependencies to avoid cascade alerts when upstream services fail.
Advanced Configuration and Optimization
Database Optimization
For high-volume monitoring, consider migrating from SQLite to PostgreSQL. Create a PostgreSQL database and configure the connection string:
# Install PostgreSQL
sudo zypper install -y postgresql postgresql-server
# Configure PostgreSQL
sudo systemctl enable postgresql
sudo systemctl start postgresql
sudo -u postgres createdb uptime_kumaUpdate the DATABASE_URL environment variable in your service configuration.
Reverse Proxy Setup
Configure Nginx as a reverse proxy for SSL termination and domain access:
sudo zypper install -y nginxCreate an Nginx configuration file:
server {
listen 80;
server_name your-domain.com;
location / {
proxy_pass http://localhost:3001;
proxy_http_version 1.1;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection 'upgrade';
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_cache_bypass $http_upgrade;
}
}Enable SSL using Let’s Encrypt for secure access:
sudo zypper install -y certbot python3-certbot-nginx
sudo certbot --nginx -d your-domain.comNotification Channels
Configure multiple notification methods for redundancy:
- Email SMTP: Set up email notifications with authentication
- Slack/Discord: Create webhook URLs for team notifications
- Mobile apps: Configure push notifications for critical alerts
- SMS providers: Set up SMS alerts for urgent failures
Test each notification channel to ensure proper delivery. Configure notification rules based on monitor priority and team responsibilities.
Performance Monitoring and Scaling
Monitor Uptime Kuma resource usage:
# Check memory usage
ps aux | grep node
# Monitor system resources
htop
# Check disk usage
df -h /opt/uptime-kumaFor large deployments, consider load balancing multiple Uptime Kuma instances or implementing database clustering for high availability.
Maintenance and Troubleshooting
Regular Maintenance Tasks
Perform weekly maintenance including:
- System updates: Keep openSUSE packages current
- Application updates: Check for new Uptime Kuma releases
- Database maintenance: Optimize and clean old data
- Log rotation: Manage log file sizes
Update Uptime Kuma by pulling the latest code and restarting:
sudo systemctl stop uptime-kuma
sudo -u uptimekuma bash
cd /opt/uptime-kuma
git pull
npm ci --production
sudo systemctl start uptime-kumaBackup and Restore Procedures
Backup the SQLite database regularly:
sudo -u uptimekuma cp /opt/uptime-kuma/data/kuma.db /backup/location/kuma-backup-$(date +%Y%m%d).dbFor PostgreSQL, use pg_dump:
sudo -u postgres pg_dump uptime_kuma > /backup/location/uptime-kuma-backup-$(date +%Y%m%d).sqlAutomate backups using cron jobs and test restore procedures regularly.
Common Issues and Solutions
High memory usage: Optimize monitor intervals and reduce concurrent checks. Consider upgrading server resources for large deployments.
Database locks: Restart the service and check for filesystem issues. SQLite can experience locks under high concurrent load.
Network connectivity: Verify DNS resolution and network routing. Check firewall rules and proxy configurations.
Service startup failures: Review systemd logs and verify file permissions. Ensure Node.js path is correct in service files.
Performance Optimization
Optimize check intervals based on service criticality. Critical services may need 30-second checks, while less important monitors can use 5-minute intervals.
Implement monitor grouping and dependencies to reduce unnecessary alerts. Configure intelligent notification schedules to avoid alert fatigue.
Consider implementing caching for external DNS lookups and connection pooling for database operations in high-volume environments.
Best Practices and Tips
Monitoring Strategy
Design an effective monitoring strategy by categorizing services based on business impact. Critical services require immediate attention with multiple notification channels, while informational monitors can use delayed notifications.
Implement cascading monitors to track service dependencies. Monitor external services that your applications depend on, including DNS providers, CDN services, and third-party APIs.
Operational Excellence
Document all monitoring configurations and maintain runbooks for common issues. Establish clear escalation procedures and ensure team members understand their responsibilities during incidents.
Regular testing of monitoring accuracy helps maintain system reliability. Simulate failures to verify alert delivery and response procedures.
Cost Optimization
Optimize resource usage by adjusting check frequencies based on service requirements. Balance monitoring thoroughness with system resources to maintain cost-effectiveness.
Implement automated maintenance scripts to reduce manual intervention. Use monitoring data to identify trends and proactively address potential issues.
Consider monitor consolidation for similar services and implement intelligent grouping to reduce management overhead while maintaining comprehensive coverage.
Congratulations! You have successfully installed Uptime Kuma. Thanks for using this tutorial to install the latest version of the Uptime Kuma monitoring tool on openSUSE Linux. For additional help or useful information, we recommend you check the official Uptime Kuma website.