How To Install VeraCrypt on Rocky Linux 10

Rocky Linux 10 represents a significant milestone in enterprise-grade Linux distributions, offering robust security features and stability. When it comes to protecting sensitive data on this platform, VeraCrypt stands out as the premier encryption solution. This comprehensive guide walks through every aspect of installing VeraCrypt on Rocky Linux 10, from system preparation to advanced configuration options.
VeraCrypt delivers military-grade encryption capabilities that transform your Rocky Linux 10 system into a fortress of data protection. Whether you’re securing personal documents or enterprise-critical information, this tutorial provides the expertise needed for successful implementation.
What is VeraCrypt?
VeraCrypt emerged as the spiritual successor to TrueCrypt, addressing security vulnerabilities while maintaining the powerful encryption capabilities that made its predecessor popular. This open-source disk encryption software provides on-the-fly encryption that operates seamlessly in the background, protecting data without disrupting workflow.
The software employs multiple industry-standard encryption algorithms, including AES-256, Serpent, and Twofish, ensuring your data remains secure against even the most sophisticated attacks. Cross-platform compatibility allows encrypted volumes created on Rocky Linux 10 to be accessed on Windows and macOS systems, making VeraCrypt ideal for mixed-environment organizations.
VeraCrypt’s hidden volume feature provides plausible deniability, creating concealed encrypted containers within regular encrypted volumes. This advanced capability proves invaluable in situations where users might be compelled to reveal passwords, as the existence of hidden data remains undetectable.
The software’s open-source nature ensures transparency and community oversight, with regular security audits validating its encryption implementations. Performance optimizations allow VeraCrypt to handle large datasets efficiently while maintaining system responsiveness during intensive operations.
Understanding Rocky Linux 10 System Requirements
Rocky Linux 10 introduces significant architectural changes that affect VeraCrypt installation compatibility. The distribution requires x86_64-v3 microarchitecture support, meaning systems must feature Intel Haswell processors from 2013 or newer, or equivalent AMD architectures.
Memory requirements for Rocky Linux 10 vary based on installation type. Minimal installations function with 1GB RAM, while desktop environments require 2GB minimum for optimal performance. VeraCrypt adds minimal memory overhead, typically consuming less than 50MB during active operation.
Storage considerations become crucial when planning VeraCrypt deployments. Rocky Linux 10 needs 10GB minimum disk space, though 20GB proves more practical for systems running encryption software. Additional space requirements depend on encrypted volume sizes and backup strategies.
Network connectivity enables package downloads and security updates essential for maintaining VeraCrypt installations. Display requirements matter primarily for GUI-based VeraCrypt versions, though console alternatives provide full functionality without graphical interfaces.
Prerequisites and System Preparation
System preparation forms the foundation for successful VeraCrypt installation on Rocky Linux 10. Begin by updating your system to ensure all security patches and package repositories reflect current versions. Execute the following commands to refresh your system:
sudo dnf update -y
sudo dnf install epel-release -yVerify your Rocky Linux 10 version and architecture compatibility using system information commands. The uname -a command displays kernel version and architecture details, while cat /etc/rocky-release confirms your specific Rocky Linux version.
Administrative privileges through sudo access prove essential for VeraCrypt installation. Test your sudo permissions by running sudo whoami, which should return “root” if configured correctly. Users without sudo access must contact system administrators for installation assistance.
Network connectivity verification ensures smooth package downloads. Test internet access using ping -c 4 google.com or similar commands. Firewall configurations might require adjustment to allow package manager operations through corporate networks.
Understanding VeraCrypt Installation Options
VeraCrypt offers two primary installation packages: GUI and Console versions, each serving different use cases and system configurations. The GUI version provides intuitive graphical interfaces ideal for desktop environments and users preferring visual interactions with encryption tools.
Console versions deliver identical encryption capabilities through command-line interfaces, making them perfect for server environments or systems without graphical desktop environments. Resource consumption differs significantly, with console versions using approximately 1GB less storage space and minimal memory overhead.
Package selection depends on your specific requirements and system configuration. Desktop users typically prefer GUI versions for ease of use, while system administrators often choose console versions for automated deployment and remote server management scenarios.
Both versions support identical encryption features, including volume creation, mounting operations, and security configurations. The choice primarily affects user interaction methods rather than underlying encryption capabilities or security levels.
Method 1: Installing VeraCrypt Using RPM Package
Downloading the VeraCrypt RPM Package
RPM installation represents the most straightforward approach for deploying VeraCrypt on Rocky Linux 10. Navigate to the official VeraCrypt downloads page and locate the CentOS 8 RPM package, which maintains compatibility with Rocky Linux 10’s architecture and dependencies.
Download the appropriate package using wget commands that fetch files directly from official sources:
wget https://launchpad.net/veracrypt/trunk/1.25.9/+download/veracrypt-1.25.9-CentOS-8-x86_64.rpmPackage verification ensures download integrity and authenticity before installation. While VeraCrypt provides PGP signatures for verification, basic file size checks help identify incomplete downloads. Compare downloaded file sizes with specifications listed on the official website.
Understanding package naming conventions helps select appropriate versions. The filename structure includes version numbers, target distribution, and architecture specifications. Rocky Linux 10 systems require x86_64 packages matching your system architecture.
Installing the RPM Package
DNF package manager handles VeraCrypt installation with automatic dependency resolution. Execute the installation command with appropriate privileges:
sudo dnf install veracrypt-1.25.9-CentOS-8-x86_64.rpmThe installation process displays dependency information and required confirmations. DNF automatically resolves library dependencies, downloading additional packages as needed. Common dependencies include FUSE libraries and GTK components for GUI functionality.
Monitor installation progress through terminal output, which displays package extraction and file placement operations. Successful installations conclude with confirmation messages and return control to the command prompt without error indicators.
Post-installation verification confirms proper VeraCrypt deployment. Check installation success using version queries:
veracrypt --versionThis command should display installed VeraCrypt version information, confirming successful package integration with your Rocky Linux 10 system.
Method 2: Installing VeraCrypt Console Version
Console-only installations provide lightweight alternatives for server environments or systems prioritizing minimal resource usage. Download the console-specific RPM package using dedicated URLs:
wget https://launchpad.net/veracrypt/trunk/1.25.9/+download/veracrypt-console-1.25.9-CentOS-8-x86_64.rpmInstallation procedures mirror GUI package methods, utilizing DNF package manager capabilities:
sudo dnf install veracrypt-console-1.25.9-CentOS-8-x86_64.rpmResource utilization differences become apparent during installation, with console versions requiring approximately 19MB installed space compared to 23MB for GUI versions. Memory usage during operation remains consistently lower for console installations.
Console versions excel in automated deployment scenarios where graphical interfaces prove unnecessary. System administrators managing multiple servers often prefer console installations for consistency across headless systems and remote management capabilities.
Verification processes remain identical regardless of installation type. Console installations respond to version queries and provide complete encryption functionality through command-line interfaces, making them suitable for scripted operations and enterprise deployments.
Verifying VeraCrypt Installation
Installation verification ensures VeraCrypt operates correctly within your Rocky Linux 10 environment. Multiple verification methods provide comprehensive confirmation of successful deployment and functionality.
Command-line verification offers the most reliable installation confirmation. Execute version queries to display installed VeraCrypt information:
veracrypt --versionSuccessful installations display version numbers, build information, and compilation details. Error messages or command-not-found responses indicate installation problems requiring troubleshooting.
GUI verification applies to graphical installations, testing interface launching capabilities. Desktop environments should display VeraCrypt entries in application menus under System Tools or Security categories. Manual launching through terminal commands provides additional verification:
veracrypt &This command launches VeraCrypt in background mode, allowing terminal access while testing interface functionality.
System integration verification examines file associations and desktop integration. Properly installed VeraCrypt instances register file handlers for encrypted volume formats and provide context menu integration in file managers.
Initial VeraCrypt Configuration and Setup
Launching VeraCrypt for First Time
First-time VeraCrypt launches require initial configuration steps that establish default settings and security parameters. Desktop users access VeraCrypt through application menus or direct command execution, while console users rely on terminal interfaces.
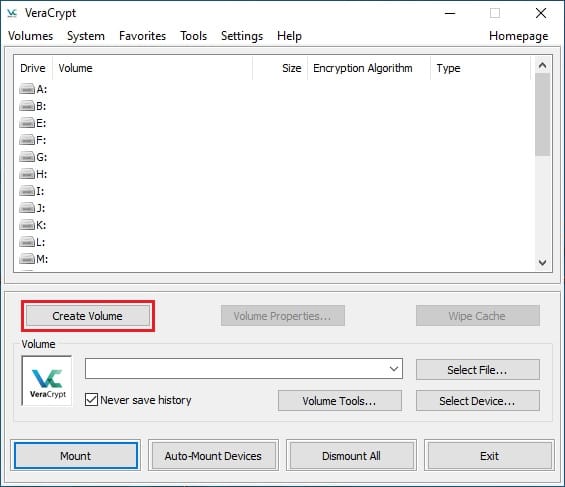
The main interface presents volume management options, encryption tools, and security settings. Familiarize yourself with primary functions including volume creation, mounting operations, and preference configurations. Interface layouts vary between GUI and console versions but provide identical functionality.
System permissions might require adjustment for optimal VeraCrypt operation. Some distributions require users to belong to specific groups for FUSE filesystem access. Add your user to the fuse group if mounting operations fail:
sudo usermod -a -G fuse $USERSecurity prompts during initial launches establish baseline protection levels. VeraCrypt may request administrative privileges for low-level disk operations or kernel module loading, depending on planned usage scenarios.
Basic Configuration Settings
Default algorithm selection influences encryption strength and performance characteristics. Access preferences through the Settings menu and configure encryption algorithms based on your security requirements. AES provides excellent performance, while Serpent offers maximum security.
Keyfile preferences establish additional authentication layers beyond passwords. Configure keyfile directories and specify preferred file formats for enhanced security. Multiple keyfiles can be combined for increased protection complexity.
Interface customization options adapt VeraCrypt behavior to match workflow preferences. Configure automatic dismount timers, system tray behavior, and confirmation dialog settings according to your usage patterns.
PIM (Personal Iterations Multiplier) settings provide additional security through increased key derivation iterations. Higher PIM values improve resistance to brute-force attacks while increasing mount times. Balance security requirements against performance needs.
Creating Your First Encrypted Volume
Volume Creation Wizard
VeraCrypt’s volume creation wizard guides users through encrypted container setup with step-by-step instructions. Launch the wizard from the main interface and select appropriate volume types based on security requirements and usage scenarios.
Standard volumes provide straightforward encryption for most use cases, creating encrypted containers that store files and directories securely. Hidden volumes offer enhanced protection through plausible deniability, concealing encrypted data within apparently legitimate containers.
Volume size selection impacts performance and storage requirements. Smaller volumes mount faster and require less system resources, while larger volumes accommodate more data but increase processing overhead. Consider future storage needs when specifying container sizes.
File container versus device encryption presents fundamental architectural choices. File containers offer portability and easy backup, while device encryption provides higher performance and seamless integration with existing storage infrastructure.
Encryption Algorithm Selection
Algorithm selection determines encryption strength, performance characteristics, and compatibility requirements. VeraCrypt supports multiple symmetric encryption algorithms, each offering different security and performance profiles.
AES-256 provides excellent balance between security and performance, offering fast encryption speeds with proven cryptographic strength. Serpent delivers maximum security through larger key sizes and conservative design, while Twofish offers good performance with strong security characteristics.
Cascading encryption combines multiple algorithms for enhanced protection against cryptographic attacks. While providing additional security layers, cascaded encryption reduces performance and increases computational overhead.
Hash algorithm selection affects key derivation security and performance. SHA-256 provides good balance, SHA-512 offers enhanced security, and Whirlpool delivers maximum protection with increased processing requirements.
Password and Security Setup
Strong password creation forms the cornerstone of VeraCrypt security. Generate passwords combining uppercase and lowercase letters, numbers, and special characters. Minimum lengths of 20 characters provide adequate protection against brute-force attacks.
Keyfile integration adds authentication layers beyond password protection. Create keyfiles using random data generators or select existing files with sufficient entropy. Multiple keyfiles can be combined for increased security complexity.
PIM configuration customizes key derivation iterations for enhanced security. Higher PIM values increase resistance to password attacks while extending mount times. Balance security requirements against usability concerns.
Volume testing verifies password accuracy and security configuration. Test mount operations using created credentials to ensure proper setup before storing critical data within encrypted containers.
Advanced VeraCrypt Features and Usage
Hidden Volumes and Plausible Deniability
Hidden volumes represent VeraCrypt’s most sophisticated security feature, creating concealed encrypted containers within standard encrypted volumes. This technology provides plausible deniability when users face coercion to reveal encryption passwords.
Hidden volume creation requires careful planning to avoid data corruption between outer and inner containers. The two-password system allows users to reveal outer volume passwords while protecting hidden data through separate authentication credentials.
Plausible deniability scenarios benefit journalists, activists, and security professionals operating in restrictive environments. Hidden volumes remain undetectable through forensic analysis, providing protection when physical device access is compromised.
Best practices for hidden volume management include regular backup procedures, careful size planning, and strict separation of outer and inner volume data. Never store critical information in outer volumes that might be revealed under duress.
System Encryption Capabilities
Full disk encryption transforms entire storage devices into encrypted containers, protecting operating systems and all stored data. VeraCrypt system encryption supports both system partition and full drive encryption scenarios.
Pre-boot authentication establishes security before operating system loading, preventing unauthorized access to encrypted systems. Recovery considerations become crucial, as forgotten passwords or corrupted authentication data can render systems unbootable.
System partition encryption provides targeted protection for operating system components while allowing separate encryption policies for data partitions. Full drive encryption offers comprehensive protection but increases complexity for system recovery procedures.
Backup strategies for system encryption require careful planning, including recovery disk creation and secure credential storage. Test recovery procedures before deploying system encryption in production environments.
Security Best Practices and Recommendations
Password strength directly correlates with encryption security effectiveness. Generate passwords using random character combinations exceeding 20 characters. Avoid dictionary words, personal information, and predictable patterns that facilitate brute-force attacks.
Keyfile management requires secure storage and backup procedures. Store keyfiles on separate media from encrypted volumes and maintain multiple copies in secure locations. USB drives provide convenient keyfile storage while enabling portable security.
Regular security updates maintain protection against emerging threats. Monitor VeraCrypt release announcements and apply security patches promptly. Automated update procedures help maintain current security postures.
Multi-factor authentication implementation combines passwords, keyfiles, and biometric data for enhanced security. Avoid single-factor authentication for critical data protection, especially in high-risk environments.
Troubleshooting Common Installation Issues
Package Installation Problems
Dependency conflicts during RPM installation typically involve missing libraries or version incompatibilities. Resolve conflicts by installing required packages manually before attempting VeraCrypt installation:
sudo dnf install fuse-libs wxGTK3Architecture mismatches cause installation failures on systems using incorrect package versions. Verify system architecture using uname -m and ensure downloaded packages match your hardware configuration.
Network connectivity problems prevent package downloads during installation. Test internet access and configure proxy settings if operating behind corporate firewalls. DNS resolution issues can cause download failures even with working network connections.
Permission-related errors indicate insufficient administrative privileges for system modification. Ensure your user account has sudo access and verify sudo configuration allows package installation operations.
Runtime and Functionality Issues
GUI launching problems often result from missing desktop environment components or display configuration issues. Console versions provide alternative access when graphical interfaces fail to operate correctly.
Volume mounting errors typically indicate permission problems or missing FUSE kernel modules. Install FUSE support packages and add users to appropriate groups for filesystem access:
sudo dnf install fuse
sudo modprobe fusePerformance issues with large encrypted volumes suggest hardware limitations or suboptimal algorithm selection. Monitor system resource usage during encryption operations and adjust algorithms for better performance.
Compatibility problems with specific Rocky Linux 10 configurations require alternative installation methods or source compilation. Consider generic installer options when RPM packages fail to integrate properly.
Performance Optimization and System Impact
Encryption overhead varies significantly based on algorithm selection, hardware capabilities, and volume sizes. AES encryption provides optimal performance on modern processors supporting AES-NI instruction sets, while other algorithms impose higher computational costs.
CPU usage patterns during encryption operations reflect algorithm complexity and data throughput requirements. Monitor system performance using top or htop commands during intensive encryption tasks to identify bottlenecks.
Memory requirements scale with active encrypted volume counts and data access patterns. Large volumes or multiple simultaneous mounts increase memory consumption, potentially impacting system responsiveness on resource-constrained systems.
Storage performance impact depends on underlying hardware and encryption algorithms. SSD storage maintains better performance under encryption loads compared to traditional hard drives, while RAID configurations can offset encryption overhead.
Maintenance and Updates
VeraCrypt updates address security vulnerabilities and provide feature enhancements essential for maintaining protection levels. Monitor official announcements through VeraCrypt websites and security mailing lists for update notifications.
Update procedures for RPM installations utilize DNF package manager capabilities when newer packages become available. Manual updates require downloading and installing updated RPM packages using identical procedures.
Backup strategies before updates protect against update failures or compatibility issues. Create encrypted volume backups and document security configurations before applying VeraCrypt updates, especially major version changes.
Version compatibility considerations affect existing encrypted volumes during updates. While VeraCrypt maintains backward compatibility, test volume access after updates to verify continued functionality.
Congratulations! You have successfully installed VeraCrypt. Thanks for using this tutorial for installing VeraCrypt free open-source disk encryption software on your Rocky Linux 10 system. For additional help or useful information, we recommend you check the official VeraCrypt website.